Software applications have become an integral part of our day-to-day digital life. Every aspect of our daily chores is somehow connected to an application that helps streamline our tasks. Our reliance on applications, no matter how beneficial they are, might backfire as they render us exposed to hackers. Critical concerns are raised regarding software development companies’ stance on software security.
This is exactly where software security testing tools such as SCA, SAST, and DAST play a big role in ensuring the security and integrity of applications. Are you wondering what these terms are? Don’t worry because this blog has got you covered.
A quick read of this article will get you acquainted with these three security testing tools. We will look into their benefits and discuss the differences between SAST vs DAST vs SCA.
Let’s get started with your software security testing journey!
What is SAST?
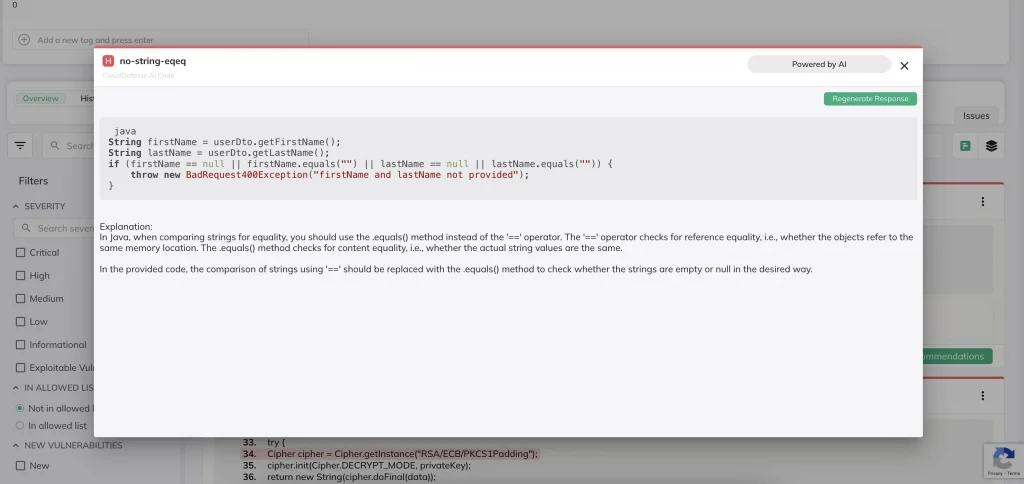
SAST (Static Application Security Testing) is the automated analysis of written code (compiled or uncompiled) for security vulnerabilities. SAST products parse your code into different pieces that it can further analyze in order to find vulnerabilities that are many layers deep in regard to functions and subroutines.
SAST products are able to follow recursion many steps deeper than a human mind is capable;
And therefore they are able to find many more types of vulnerabilities than a human being (without using automated tools for assistance). SAST products are often slow, full of false positives, and require a trained expert to use at their full potential. That said, they are also able to find many more types of vulnerabilities that could have been missed without their analysis.
Memory leaks, endless loops, falling into unknown states, unhandled errors and other exceptions, and so many more potential serious security vulnerabilities are easily found with SAST products. One of the greatest strengths of SAST tools is that they are able to get complete code coverage, meaning they are able to analyze every single line of code within your application.
That said, studies have shown that a non-trivial percentage of the source code within modern applications is executed when our apps are in production or being used by end-users. This raises the question as to if complete code coverage is actually necessary to ensure that the applications you are creating are secure.
SAST tools are able to analyze binaries (byte code/compiled code) and (raw/uncompiled) source code.
What are the benefits of SAST?
These are some of the benefits that SAST provides you with:
Continuous Integration into SDLC: SAST seamlessly integrates into the software development lifecycle (SDLC), allowing for continuous security analysis from the early stages to project completion.
Precise Vulnerability Identification: SAST provides developers with detailed insights, such as the exact file name and line number where a vulnerability exists, enabling swift and targeted remediation.
Timely Remediation: Identification of vulnerabilities shortly after the code is written enables prompt remediation. The sooner issues are addressed, the more economic costs are saved, enhancing overall software security.
Cost Savings: Early remediation translates into significant cost savings. Addressing security issues in the initial stages of development requires fewer resources and effort compared to tackling them later in the SDLC.
Combination of Manual and Automated Analysis: When combined with manual inspection, SAST tools yield results with low rates of false positives and false negatives. This dual approach ensures a reliable and accurate security assessment.
What is DAST?
DAST (Dynamic Application Security Testing) is interaction with your running application with the purpose of finding and managing vulnerabilities it may have. In order to find vulnerabilities using a DAST tool, your application must be installed on a web server, a virtual machine, or a container, and it must be running during the analysis.
The DAST tool must proxy your web application’s communications, putting itself between the browser (front end) and server (backend). DAST tools then analyze the requests and responses to learn about your application as it is used. Once it has seen all of the pages of your application (including the parts after authentication and authorization), the automation can begin.
DAST tools generally have a crawling feature to try to find any missed pages, and then they start to perform fuzzing and dynamic analysis.
What are the benefits of DAST?
Here is how DAST benefits you throughout the software development lifecycle.
Continuous Integration into SDLC: DAST integrates into the SDLC just like SAST, facilitating continuous security testing from the early stages to the completion of a project.
Identification of Interaction-Induced Vulnerabilities: DAST is an expert at identifying vulnerabilities resulting from the interaction with the application. By simulating real-world
scenarios, it helps pinpoint weaknesses that may not be visible in static analysis alone.
Simulation of Malicious Attacks: DAST allows for the simulation of attacks by malicious hackers. This approach helps organizations understand and address potential security loopholes before they can be exploited in a real-world scenario.
Manual and Automated Customized Attacks: When combined with manual testing, DAST tools enable the creation of custom-made and clever attacks. This dual approach results in assessments with low rates of false positives and false negatives, enhancing the precision and reliability of the security testing process.
What is Fuzzing?
Fuzzing is submitting malformed input to an application to verify that it fails gracefully. It is important to ensure that our applications never fall into an unknown state or crash. To do so use fuzzing tests by adding bad input into every possible field within the application.
Fuzzing also generally tests bound limits to ensure that there are no overflow vulnerabilities within our applications if our languages are not memory-safe. The bad input used for fuzzing is a combination of random, special characters, shell code, and anything else the fuzzer’s creators think may find problems.
After this, the DAST tool performs more targeted, automated testing, often referred to as “active testing” or “attack”. It uses the information found during the crawling and fuzzing phases to create scripts that it can use to attack the application.
DAST Testing
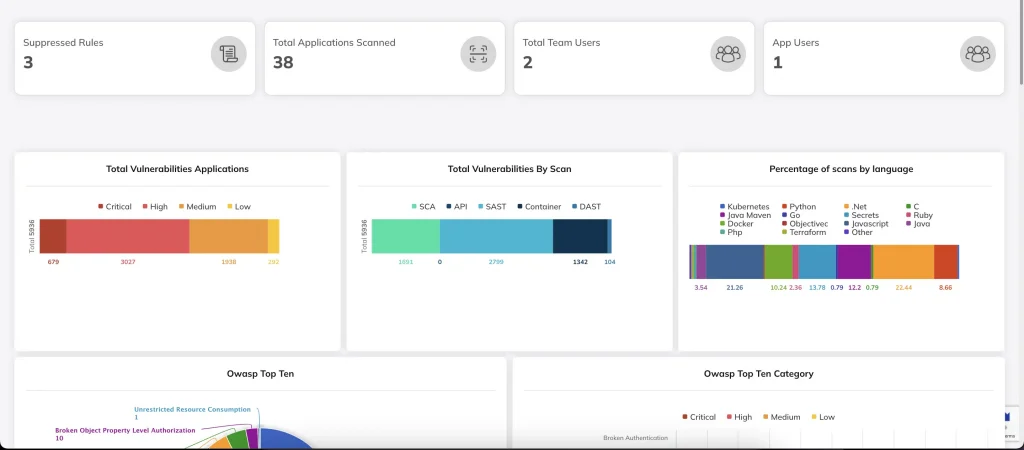
DAST testing is partially an attempt to find business logic problems but also to find implementation problems (security bugs/code problems). A DAST tool can find several types of problems quickly and effectively, although it misses many types. Automated DAST tools are also not able to guarantee complete code coverage.
DAST Tools is also not able to promise that they will be able to find and evaluate every page or feature within your application, it is necessary to manually ensure that they have seen every single part of your application for complete coverage.
DAST tools are quick and effective wins for security. They are able to find some things reliably, and very quickly, which means that even unadvanced attackers would be able to also find those vulnerabilities.
It is important that if you easily find dangerous vulnerabilities using an automated DAST tool, you fix them to avoid falling prey to unadvanced malicious actors.
Top Tip
DAST tools are often used by Penetration Testers or Security Assessors in conjunction with other security tooling. DAST tools often contain features for performing manual security testing, which can then yield significantly more accurate results when used by trained professionals.
What is SCA?
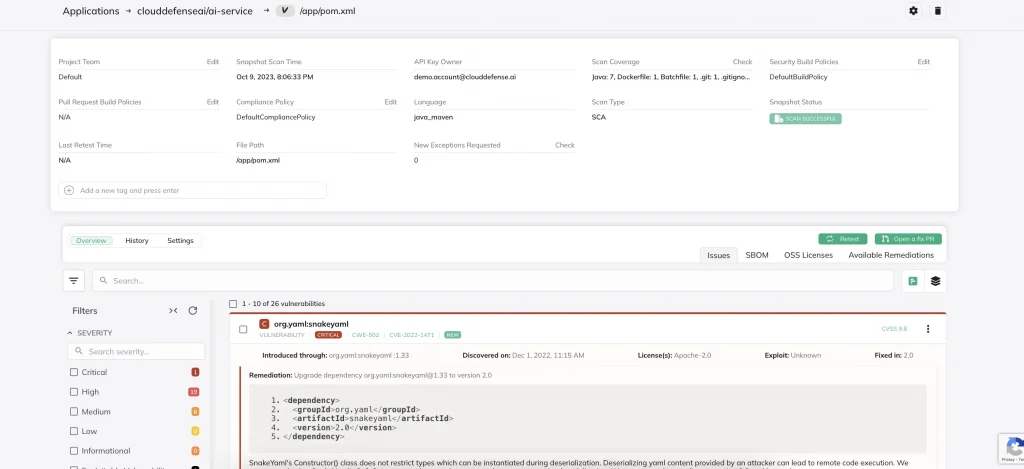
Software Composition Analysis (SCA) is the verification of the third-party libraries, frameworks and components used within your application; all of the code that you and your team did not write is considered by SCA tools.
Although SCA is often partially covered as part of SAST tools, it is not necessarily complete or exhaustive when compared to a standalone SCA tool.
The vulnerabilities that SCA tools found in third-party components come from numerous places.
Common Vulnerability Enumeration
The CVE (Common Vulnerability Enumeration) database, exploit DB, independent security researchers, research that the vendor has performed themselves, and information released by the frameworks or third-party component creators.
SCA tools do not perform static or dynamic analysis of the code within the third-party components themselves, they report based on the pre-created lists from the sources listed above.
SCA tools therefore do not evaluate the security of the components within your application while they run; instead, they analyze your list of dependencies, cross reference them against their list of known-vulnerable dependencies, and then report the matching dependencies are their findings.
This results in very fast reporting, and generally fairly accurate results when compared to SAST or DAST. SCA is generally considered a very valuable tool for finding vulnerabilities in code and protecting your software supply chain.
What are the benefits of SCA?
These are some of the benefits that SCA provides you with
Continuous Integration into SDLC: SCA integrates into the SDLC just like SAST and DAST, allowing for continuous examination of software components from the early stages to project completion.
Production of Software Bill of Materials (SBOM): SCA enables the creation of an SBOM, a document detailing the software dependencies being utilized in a project. This transparency aids in better understanding and managing the software supply chain.
Identification of Supply Chain Risks: SCA plays a big role in identifying software supply chain risks by assessing component quality factors such as licenses, versions, and vulnerabilities. This helps in reducing potential issues related to the software supply chain.
Manual and Automated Analysis Combination: When employed manually in conjunction with SCA tools, the results exhibit low rates of false positives and false negatives. This synergistic approach ensures a more accurate assessment, by making use of both human expertise and automated analysis.
SAST vs SCA vs DAST: Key Differences
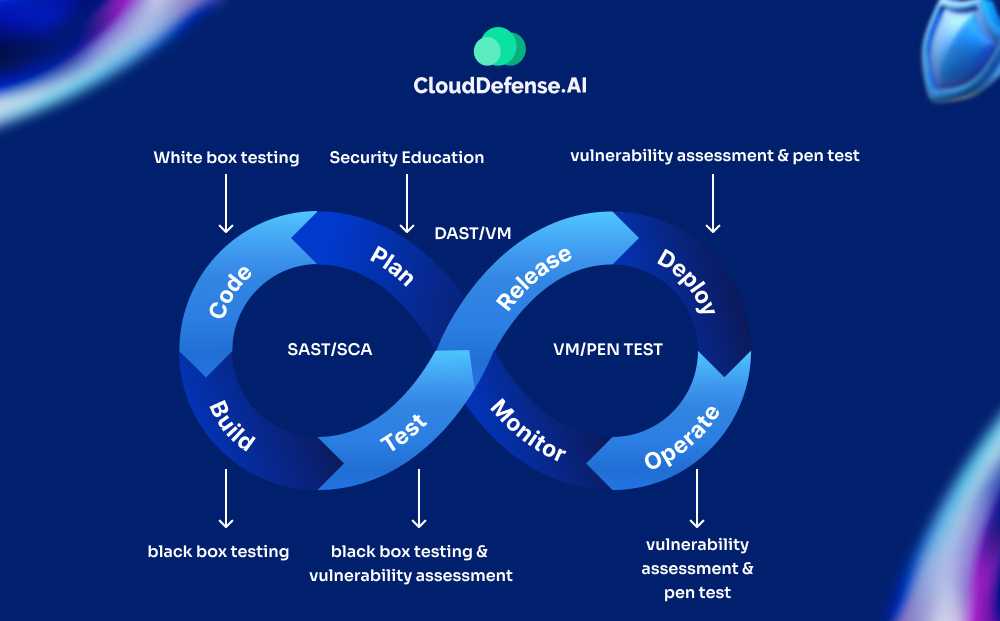
SAST vs SCA or SAST vs DAST are not valid debates since all three of the security testing tools have different scopes. All three of these testing tools can be used to complement one another in a software development environment.
| Metrics | SAST | SCA | DAST |
| Complexity of Implementation | Moderate complexity, customization is required to avoid any false positives in the system. | Very low, as the tool can start with a list of dependencies only. | Between moderate to low complexity. The tool doesn’t require any prior knowledge of the target’s ecosystem. |
| Time taken for operation | Moderate impact on the SDLC time, as the tool analyzes each line of code. | Between moderate to low impact on the SDLC time, depending on the level of evaluation the tool provides. | Since the attack simulation is independent, it has zero impact on the operation time. |
| False Positives/ Noise | Moderate noise, since the tool relies on static code analysis. | Very low, as the tool uses a database of known vulnerabilities to detect any vulnerabilities. | Moderate noise due to reliance on attack simulation. |
| False Negatives | Moderate false negatives, as the tool is unable to detect vulnerabilities that are introduced from third-party dependencies or during runtime. | Moderate to high amount of false negatives, as the tool relies on a CVE database and a lot of the dependency names match the tools pattern. | Moderate negatives, as the tools relies on attack simulation which is not enough to uncover all vulnerabilities. |
Quality of Results
Automated tools are far from perfect; they will not only miss things, but they will also report issues that don’t exist. Using multiple tools, having a skilled professional tune your tools and remove false positives, compiling your results from all tools,
And then evaluating application risk based on your business is necessary in order to gauge your software threat landscape. It is advantageous to combine all tool results after validation, as well as any manual testing results, in order to direct your defense efforts effectively.
You will never have time to act on every result; thus prioritization is critical.
Comprehensive Security
As previously stated, just one of these tools alone is not enough to find everything wrong with your application or often even to make it “safe enough” for the Internet. Being able to protect your software supply chain and find vulnerabilities in both written and running code are fundamental for a complete application security program.
FAQ
Is SCA white-box testing?
No, SCA is not typically considered white-box testing. SCA focuses on identifying and managing open-source components and dependencies in applications, without direct examination of the application’s internal code.
Which are valid features of an SCA tool?
Valid features of a SCA tool include dependency tracking, vulnerability detection in third-party components, license compliance monitoring, and integration into the development lifecycle for continuous monitoring of open-source components.
Is SAST more expensive than DAST?
The cost comparison between SAST and DAST can vary based on factors like tools used, implementation complexity, and organization size. Generally, SAST may involve higher upfront costs due to its integration into the development process, but ongoing DAST testing may incur additional expenses over time. The cost-effectiveness depends on specific project needs and security requirements.
What is SCA dependency?
In the context of SCA, a dependency refers to an external software component or library that a given software project relies on to function properly. SCA tools analyze and track these dependencies to identify potential security vulnerabilities, licensing issues, or other risks associated with third-party components.
Choose CloudDefense.AI as your Security Testing Partner
At CloudDefense.AI, we provide a comprehensive security testing solution by offering SAST, DAST, SCA throughout the entire software development lifecycle. We seamlessly integrate SAST, DAST, and SCA into a single solution, providing you with a unified testing approach that covers the complete SDLC.
Our advanced security testing tools are combined with the expertise of our highly certified security researchers. This unique approach ensures the detection of a wide range of vulnerabilities in the assessed systems.
Take the first step in securing your systems by exploring our platform. Click here to learn more about our free demo. Experience the benefits of our automated security testing, or inquire about our other state-of-the-art security tools. For further information, feel free to contact us today!







