Shift-left security refers to integrating security measures early in the software development lifecycle (SDLC). This approach ensures that code and software are evaluated for security vulnerabilities at the earliest stages of development, reducing risks and improving overall security posture.
What is Shift Left Security?
Shift-left security refers to the approach of integrating security testing earlier in the software development lifecycle. In traditional DevOps processes, security checks typically happen after the code is developed and ready for deployment. However, this delayed testing can lead to bottlenecks if vulnerabilities are discovered late.
By shifting security left, organizations incorporate security practices from the planning and coding phases. This early integration involves security modeling, which anticipates potential risks before development progresses.
Shift-left security aligns with DevSecOps principles, encouraging seamless collaboration between development, operations, and security teams to ensure continuous, secure software delivery.
What is Shift Right Security in DevOps?
If shift-left security moves testing earlier in the software development process, shift-right security focuses on monitoring and testing in real-world, production environments. No matter how thorough your testing is during development, real-world usage can reveal issues that weren’t detected before deployment.
Shift-right security involves evaluating an application after it’s live, testing its performance, resilience, and reliability under real conditions. This stage ensures that any lingering vulnerabilities or bugs can be caught and addressed promptly, often through patches or other fixes.
DIfferences between Shift Left Security and Shift Right Security
To illustrate the difference, imagine building a car. Shift-right testing would be like taking the car for a test drive after assembling it to see how it handles on the road. If you notice a problem with the brakes or the steering, you’d need to bring the car back to the workshop to make necessary adjustments.
Shift-left security, on the other hand, would be akin to inspecting the engine and other critical components before fully assembling the car, ensuring that any issues are caught early and worked on immediately. Shift right security might be essential but it is definitely not as cost-effective as shift left security.
If we go back to our car example, not selling faulty cars to your customers is amazing but identifying the faults during production is even better and can help in cutting down costs. That is why we can say that for DevSecOps best practices, it is ideal to use both shift right and shift left security combined together.
Benefits of Shift Left Security
Here’s a closer look at the key benefits of shift-left security:
- Early Detection of Issues: Spotting security issues early on is essential for minimizing risks. By identifying vulnerabilities from the start, teams can address them quickly, reducing the chance of missing critical threats later.
- Cost Savings: Fixing security concerns during the development phase is far more cost-effective than dealing with them post-deployment. Not only does this save money, but it also reduces the overall expense of implementing security measures throughout the project.
- Faster Development: Incorporating security early helps eliminate last-minute roadblocks, ensuring smooth releases and timely deployments. This speeds up the overall development process, preventing delays caused by unexpected security fixes.
- Proactive Risk Management: By embedding top-tier security practices from the beginning, you’re actively mitigating risks. This makes your software more resilient to cyberattacks and vulnerabilities, ensuring a more robust defense against emerging threats.
- Higher Software Quality: When security becomes a foundational element, the overall quality of the software improves. You end up with a product that’s not only secure but also efficient and reliable.
- Increased Flexibility: An agile and flexible security approach allows you to quickly adapt to new threats and incorporate the latest security measures. This keeps your software ahead of the curve, prepared to handle the ever-evolving landscape of digital threats.
- Enhanced Customer Trust: Secure software builds trust. By prioritizing security from the ground up, you’re sending a clear message to your customers that their data and systems are protected, earning their confidence and loyalty.
The Importance of Shift-Left Security
Organizations are realizing the need to integrate security earlier in the SDLC with cyber threats becoming more complex. Shift-left security is a proactive strategy that embeds security into the earliest phases of development. This approach not only improves security outcomes but also offers other significant advantages.
Reducing Remediation Costs
Addressing vulnerabilities during the design or coding stage is far more cost-effective than fixing them after deployment. Early detection and remediation prevent costly fixes, minimize disruptions, and reduce the risk of vulnerabilities making it into production systems.
Accelerating Time to Market
Identifying security flaws late in the development process can lead to major delays, slowing the release of the final product. Shifting security left ensures that vulnerabilities are caught and resolved earlier, allowing the development process to proceed smoothly and reducing time-to-market delays.
Strengthening Security Posture
By embedding security measures into the development pipeline, companies enhance their overall security posture. Automation of security checks, compliance audits, and threat detection ensure that applications are built with security in mind from the very beginning, reducing the likelihood of breaches.
Building Trust with Users
Customers and end-users are more likely to trust organizations that prioritize security from the outset. Shifting security left reduces the risk of data breaches and ensures that sensitive information is protected. For industries like finance and healthcare, maintaining user trust through secure applications is paramount to long-term success.
Types of Shift Left Security Tools and Technologies
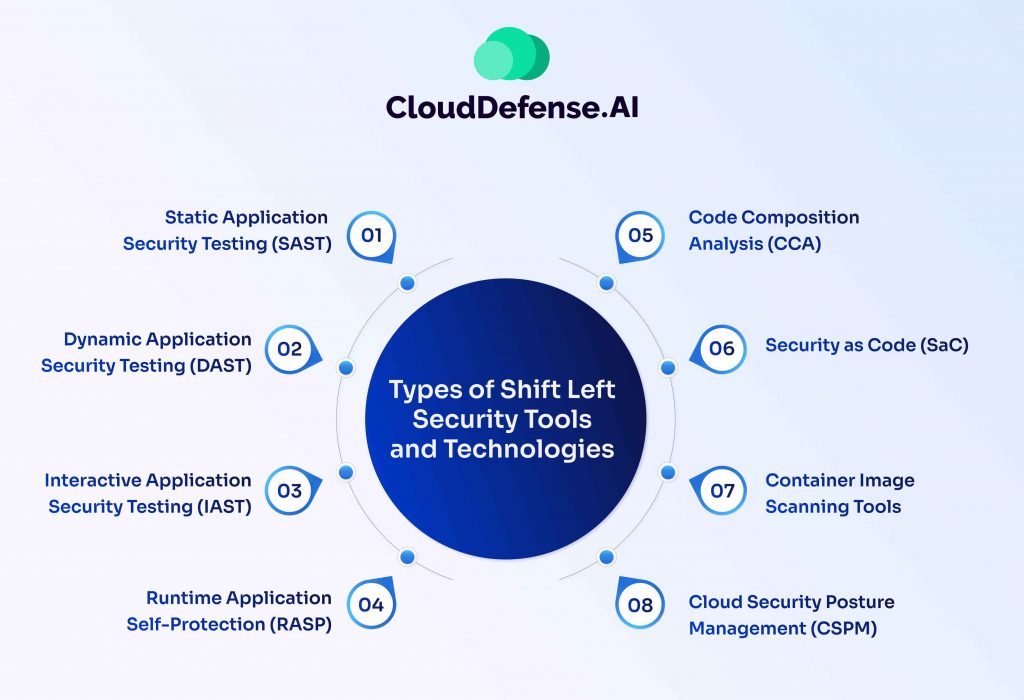
When it comes to embracing a shift-left security approach, a variety of tools and technologies come into play. These tools play a crucial role in shifting security practices earlier in the development cycle, enhancing the overall security posture. Let’s delve into some key types of Shift-Left security tools and technologies:
Static Application Security Testing (SAST)
SAST tools analyze source code, bytecode, or binary code for vulnerabilities without executing the program. By identifying security flaws early in the development process, SAST enables teams to adopt a proactive approach to risk mitigation.
Dynamic Application Security Testing (DAST)
DAST tools examine running applications for security vulnerabilities by simulating external attacks. By integrating DAST into the development lifecycle, organizations can identify vulnerabilities in real-time, ensuring comprehensive threat detection during runtime.
Interactive Application Security Testing (IAST)
IAST combines the capabilities of SAST and DAST by analyzing applications in real-time during runtime. It provides immediate feedback on security issues, enabling continuous monitoring and rapid identification of potential vulnerabilities as the application executes.
Runtime Application Self-Protection (RASP)
RASP operates alongside applications in production environments, monitoring behavior in real-time and detecting anomalous or unauthorized activities. It offers immediate responses to potential security threats, although it may require additional infrastructure considerations.
Code Composition Analysis (CCA)
CCA tools focus on identifying vulnerabilities in third-party dependencies and open-source components within the codebase. By scanning external libraries, CCA tools provide essential insights into potential risks and ensure the integrity of external code.
Security as Code (SaC)
SaC involves embedding security policies and best practices directly into the development process through codified rules. Automation tools ensure consistent application of security standards, creating a standardized and enforceable security framework across the development lifecycle.
Container Image Scanning Tools
Container image scanning tools automatically assess container images within CI/CD pipelines and registries. These tools proactively identify vulnerabilities in containerized environments, offering developers remediation guidance to ensure secure deployments.
Cloud Security Posture Management (CSPM)
CSPM solutions detect and address misconfigurations in cloud infrastructure, providing recommendations or automatic enforcement of security best practices. By aligning cloud environments with organizational security policies and industry standards, CSPM enhances cloud security and reduces potential attack vectors.
Implement Shift Left Security: A Proven Process
Implementing shift-left security is about embedding security practices into the development process from the start. This ensures vulnerabilities are identified early, minimizing risks and reducing costly fixes later. Here’s a streamlined process for effectively integrating shift-left security.
Establish a Shared Vision
Shift-left security requires collaboration across teams. Leaders need to foster a collective mindset by encouraging open discussions about current security challenges and benefits. By setting shared goals and success criteria, teams can ensure a smooth transition to a unified DevSecOps approach.
Comprehend the Software Delivery Path
Understanding the software delivery pipeline is crucial. Organizations must evaluate their tech stack, recognizing that security risks stem from both in-house and third-party developers. By integrating tools and standards that address these risks, you can design a robust DevSecOps strategy.
Automation as the Backbone
Automation drives shift-left security. Integrating tools like CI/CD for automated security testing and vulnerability scanning during the development phase ensures risks are flagged early. Issue tracking tools should notify teams of risks promptly, streamlining remediation and protecting cloud-native workflows.
Empower the Development Teams
Developers are central to the shift-left process. Educating them on secure coding practices and providing the right resources ensures they can identify and fix security gaps early. Continuous education helps build a security-aware development culture, enhancing the overall security posture.
Challenges of Shift Left Security and Testing
Implementing the transformative switch to shift-left security and testing comes with its own set of challenges. One major challenge is shaking off the old mindsets ingrained in traditional development approaches, where security is often considered a standalone step at the end of a project.
Now, bringing security into the picture right from the start requires a bit of a cultural shift. It means teams need to take a fresh look at their usual workflows and how they collaborate. And let’s not forget about the learning curve when it comes to new tools and technologies.
Teams used to the comfort of legacy systems might find themselves slowed down initially. The real trick here is finding the right balance between speed and security. It’s a bit of a balancing act, ensuring we don’t sacrifice one for the other. As we tackle these challenges, the next part dives into some tried-and-true practices that light the way forward.
Shift Left Security Best Practices
Cultivate a Collaborative Spirit
Nurture a culture where development, security, and testing teams openly communicate and collaborate right from the project’s kick-off. Say goodbye to isolated silos, and let everyone share a common understanding of the security goals and testing needs.
Early Learning and Skill Building
Invest in comprehensive training programs for developers, arming them with the knowledge and skills for secure coding practices. Recognize that boosting human capabilities is key to building a strong defense against potential security vulnerabilities.
Choose Tools Wisely
Be savvy in picking tools that seamlessly fit into the development pipeline and support automation. Look for tools that cover a range of security testing, including static and dynamic analysis, continuous integration, and vulnerability scanning.
Keep an Eye on Security
Shift-left security isn’t a one-time thing. Set up continuous monitoring to catch and deal with security issues in real-time, stopping potential threats from escalating throughout the software development journey.
Install Security Checkpoints
Insert security gates at crucial stages in the development process to validate security measures. This ensures that security isn’t just an early consideration but a consistent checkpoint across the entire software delivery pipeline.
Embrace DevSecOps Approach
Fully weave security into the DevOps methodology, creating a holistic approach where security is part and parcel of every stage. Encourage collaboration across functions and shared responsibility for security.
Keep Policies Up-to-Date
Security policies should evolve with the changing threat landscape. Regularly review and update them to align with emerging risks and industry best practices, maintaining a proactive stance against potential vulnerabilities.
Shift Left with CloudDefense.AI
At CloudDefense.AI, we’ve always understood the importance of integrating security smoothly throughout the development lifecycle. With ou platform, your teams can embed security measures directly into their workflows, reducing vulnerabilities and ensuring compliance from the very first line of code.
By using CloudDefense.AI, you can effectively shift security left—catching risks early, simplifying remediation, and accelerating your development process. Here’s how CloudDefense.AI enhances your shift-left security strategy.
- Agentless Security Analysis: Our platform uses industry-leading agentless scanning to examine code repositories, container images, and Infrastructure as Code (IaC) templates, identifying vulnerabilities and compliance gaps long before they can impact production environments.
- Code-to-Cloud: CloudDefense.AI links security issues detected in cloud environments back to the exact code and team responsible, creating accountability and significantly speeding up the remediation process.
- Developer-Centric Integration: CloudDefense.AI integrates smoothly into IDEs and development repositories, allowing developers to address security issues as they code. This direct integration eliminates bottlenecks and reduces the cost and time associated with security fixes down the line.
- Contextualized Security Insights: With prioritized insights and actionable remediation guidance, developers can swiftly address vulnerabilities and misconfigurations. This contextual approach not only simplifies remediation but also improves overall code quality.
- Unified Policy Management: Our unified policy framework spans across the entire CI/CD pipeline, ensuring consistent security controls from the development stage to production deployments. This ensures that security policies remain enforceable and effective across all environments.
By incorporating CloudDefense.AI into your DevSecOps strategy, you not only reduce the risk of vulnerabilities but also optimize workflows for a more secure, efficient, and faster development cycle. Embrace the full potential of automated, integrated security, and take your shift-left approach to the next level with CloudDefense.AI. Book a free demo now!
FAQs
What is the principle of Shift Left?
The Shift Left principle centers on integrating processes like testing and security into the early stages of software development. It stresses the importance of addressing issues and concerns right from the start instead of postponing them to later phases.
How does Shift Left Testing save time and resources?
Shift-left testing saves time and resources by catching and fixing issues early in the development process. Detecting defects from the beginning allows teams to avoid the time-consuming and costly process of dealing with problems in later stages. This way, businesses can boost overall efficiency, reduce the chances of delays, and minimize the resources needed for extensive bug fixing.
Can Shift Left Security be applied to all software projects?
Shift Left Security is a versatile approach applicable to various software projects, regardless of size or complexity. However, the extent to which it can be implemented may vary based on factors such as project requirements, team expertise, and the specific security challenges associated with the project.
What is the main goal of Shift Left Testing?
The primary goal of shift left testing in agile is to ensure the early identification and resolution of defects in the software development process. By moving testing activities to the early stages, the approach aims to enhance software quality, expedite development cycles, and lower the overall cost of addressing issues.
Are there any potential drawbacks to Shift Left Testing?
While Shift Left Testing offers numerous advantages, potential drawbacks may include difficulties in adapting to new tools and processes, initial resistance to cultural shifts, and the need for thorough training. Additionally, if not executed correctly, there is a risk of overlooking certain issues that might surface in later development stages. Addressing these challenges effectively requires careful planning and collaboration.







