What is a Shared Responsibility Model?
The shared responsibility model is a fundamental framework in cloud computing that defines security and operational responsibilities between the cloud service provider (CSP) and the customer. It ensures clarity on who secures what within a cloud environment, minimizing the risk of overlooked vulnerabilities.
CSP’s Role (Security of the Cloud)
Cloud providers are responsible for securing the core infrastructure, including physical data centers, servers, storage, and networking components. Their responsibilities typically include:
- Maintaining the physical security of data centers to prevent unauthorized access.
- Patching and updating the underlying operating systems.
- Ensuring high availability and reliability of cloud services.
For example, a provider like Amazon Web Services (AWS) ensures the security of its cloud infrastructure by protecting it against physical and virtual threats.
Customer’s Role (Security in the Cloud)
Customers are responsible for securing their data, applications, and configurations hosted on the cloud. This includes:
- Configuring secure access controls and permissions.
- Encrypting sensitive data during transmission and while at rest.
- Managing user identities, credentials, and authentication mechanisms.
- Implementing application-level security measures.
For instance, users storing data on AWS S3 are responsible for ensuring proper access control to their buckets and encrypting their sensitive data.
Importance of Shared Responsibility Models
It is essential to understand the shared responsibility model to clearly prevent security gaps. While CSPs deliver a secure foundation, customers must actively secure their assets and applications. Unfortunately, many organizations fail to fully grasp their responsibilities, leading to misconfigurations, data breaches, and compliance issues.
Surprisingly, while 98% of businesses report experiencing cloud data breaches, only 13% are fully aware of their security obligations. Many mistakenly rely solely on CSPs to protect data and applications. Addressing this knowledge gap through education and robust policies is vital to ensuring cloud security.
Different Types of Shared Responsibility Models
The Shared Responsibility Model is a critical framework in cloud computing that outlines the division of security responsibilities between the Cloud Service Provider (CSP) and the customer. While it might seem like a singular concept, it adapts based on the type of cloud service used—software as a Service (SaaS), Platform as a Service (PaaS), or Infrastructure as a Service (IaaS). Each model has unique security dynamics, making it essential to understand how responsibilities vary.
Software as a Service (SaaS): Minimal Customer Responsibility
SaaS is the most hands-off model for customers when it comes to security responsibilities. The CSP takes care of most of the security aspects, ensuring the application, infrastructure, and network are secure. This model is standard in applications like Gmail, Salesforce, or Microsoft Office 365.
CSP Responsibilities
- Securing the software application and underlying infrastructure.
- Managing application-level security.
- Ensuring uptime and system performance.
Customer Responsibilities
- Managing user access (e.g., creating secure passwords and configuring permissions).
- Ensuring data protection and account security.
For example, if you use Salesforce, the CSP ensures that the platform’s underlying architecture is secure. However, it is the customer’s responsibility to configure access controls and protect sensitive data adequately.
Platform as a Service (PaaS): Shared Control and Flexibility
In the PaaS model, CSPs provide a secure platform for customers to build and deploy applications. This model offers more flexibility than SaaS while also requiring more responsibility from the customer. Examples include Google App Engine and Azure App Service.
CSP Responsibilities
- Securing the underlying infrastructure and platform components, including runtime, libraries, and operating systems.
Customer Responsibilities
- Managing application and data security.
- Implementing secure user access controls.
For instance, Microsoft secures the OS and runtime environment when using Azure App Service. However, developers are responsible for ensuring the security of their application code and properly managing data encryption.
Infrastructure as a Service (IaaS): Maximum Flexibility, Maximum Responsibility
IaaS offers customers the highest level of control and flexibility but also comes with the greatest security responsibilities. Examples of IaaS platforms include Amazon EC2 and Microsoft Azure Virtual Machines.
CSP Responsibilities
- Securing the foundational infrastructure, such as virtual machines, storage, and networks.
Customer Responsibilities
- Managing everything built on top of the infrastructure, including Operating systems, Runtime environments, Applications, Data security and protection, User access management.
For example, Amazon secures the EC2 infrastructure, but customers must configure their operating systems, patch vulnerabilities, and secure data stored on their instances.
The Customer’s Cloud Security Responsibilities
Despite the security measures provided by Cloud Service Providers (CSPs), most cloud security incidents occur from customer mistakes.
According to Gartner, by 2025, a staggering 99% of cloud security failures will be attributed to customers.
To thrive within the shared responsibility model, customers must understand and own their security responsibilities. Here’s a breakdown of key customer responsibilities and how to manage them effectively:
| Customer Responsibility | Description |
| Data Protection | Ensuring the confidentiality, integrity, and availability of data is critical. Implement strong encryption, access controls, and backup strategies to secure sensitive information. |
| Application Security | Protect applications by following secure coding practices, conducting regular vulnerability scans, and implementing necessary security controls to mitigate risks. |
| User Access Management | Secure user accounts by enforcing robust permissions, using multi-factor authentication (MFA), and ensuring strong password policies. |
| Compliance and Governance | Stay compliant with industry regulations by implementing proper governance frameworks, maintaining audit trails, and aligning your security measures with applicable standards. |
| Network Controls | Configure firewalls, security groups, VPNs, and other network controls to prevent unauthorized access to cloud resources. Regularly review and update these settings. |
By fully embracing these responsibilities and leveraging best practices, organizations can significantly reduce the likelihood of cloud security failures and maintain a strong security posture.
The CSP’s Typical Cloud Security Responsibilities
CSPs are entrusted with securing the foundational infrastructure that supports cloud services. Their responsibilities primarily involve protecting the core elements necessary for cloud operations. Below are the key areas where CSPs typically handle security:
Physical Security
CSPs are responsible for ensuring the safety of physical access to their data centers. This includes using advanced surveillance systems, securing entry points with restricted access, and implementing environmental controls to prevent damage from external threats.
Network Infrastructure Security
The CSP also manages the security of the cloud’s network infrastructure. This involves safeguarding critical components such as routers, switches, and load balancers. CSPs typically deploy security measures like intrusion detection and prevention systems to monitor and protect the network from unauthorized access or attacks.
Host Infrastructure Security
CSPs ensure the security of the underlying host infrastructure, which includes servers, virtualization layers, and storage systems. They implement essential security protocols such as regular patching, proper configuration, and rigorous controls to maintain the integrity of these resources while ensuring their operational reliability.
Compliance Certifications
To demonstrate adherence to industry standards and regulations, CSPs undergo regular independent audits. These certifications assure customers that the CSP follows best practices in maintaining security and privacy across their services, helping to build trust and meet compliance requirements.
These responsibilities help ensure that the cloud infrastructure remains secure and reliable while customers can focus on managing their own data and applications within the provided environment.
Divided responsibilities
In cloud environments, responsibilities often overlap between you and your provider, depending on the service model (SaaS, PaaS, IaaS). Understanding these shared areas is crucial for smooth security collaboration.
- Operating Systems: Whether you use the provider’s OS or bring your own, securing and patching the OS is your responsibility. Ensure it’s configured securely, and vulnerabilities are managed.
- Native vs. Third-Party Tools: The provider secures the infrastructure, but you’re in charge of securing third-party tools, applications, and data. Make sure these tools align with your security standards.
- Server-Based vs. Serverless Computing: In server-based setups, you manage the OS and security configurations. In serverless environments, the provider secures the infrastructure, but you’re still responsible for your code and deployment.
- Network Controls: Configuring network security, whether using the provider’s or your own firewall, is up to you. Ensure proper rules are set and align with your security policies.
By taking ownership of these shared responsibilities, you ensure better security outcomes and avoid gaps in your cloud security posture.
Examples of Shared Responsibility Model
Leading CSPs, such as Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure, each have their own shared responsibility models, which outline the security duties of both the provider and the customer.
AWS Shared Responsibility Model
AWS is responsible for securing the infrastructure that powers all its services, including hardware, physical data centers, networks, edge locations, and virtualization layers.
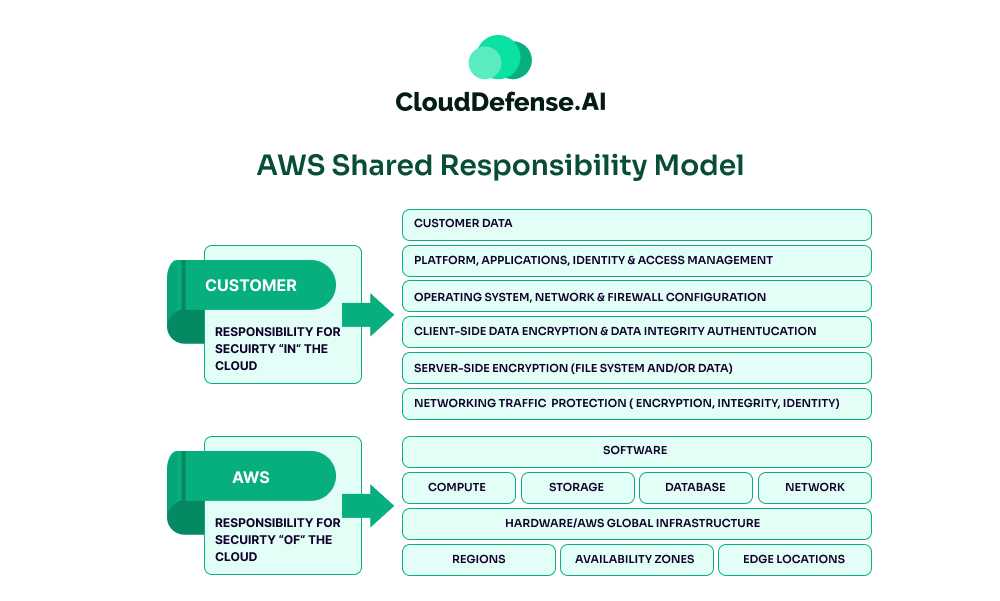
They also secure managed services like AWS DynamoDB, RDS, Redshift, Elastic, and EMR. However, customers must secure their own applications and data and manage access controls and configurations within their AWS accounts.
GCP Shared Responsibility Model
Google Cloud Platform (GCP) follows a shared responsibility and shared fate model, emphasizing the collective responsibility for security.
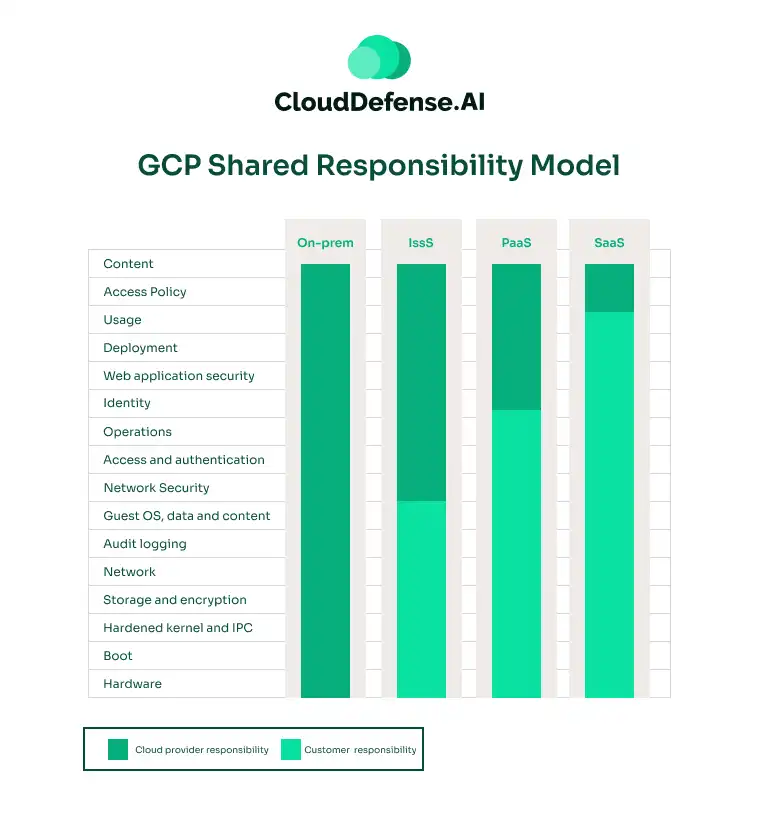
While GCP secures the underlying cloud infrastructure, customers are responsible for securing their applications, data, user access, and security settings within their projects. GCP provides tools to help customers effectively meet these responsibilities.
Azure Shared Responsibility Model
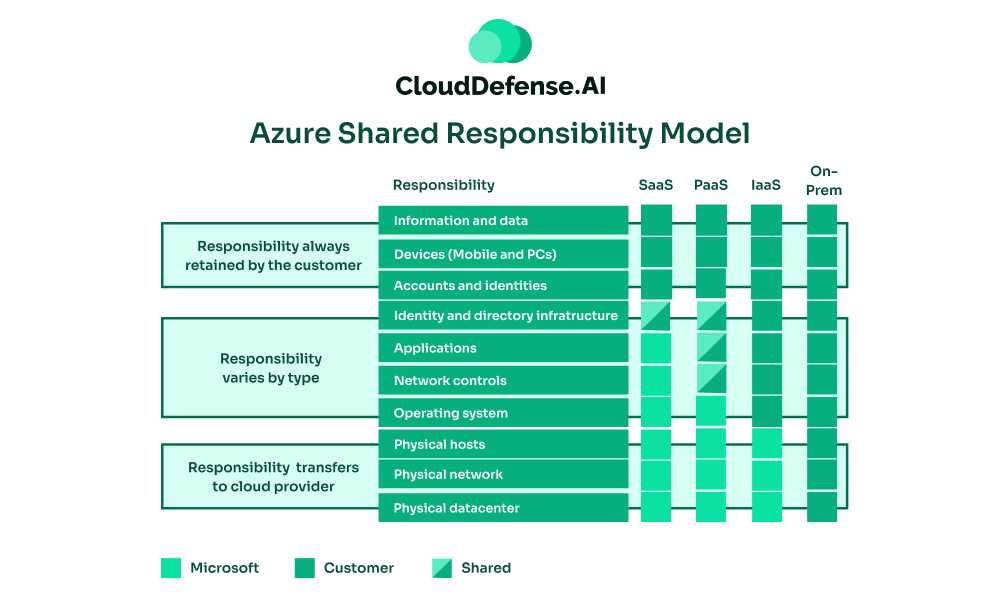
Microsoft Azure’s shared responsibility model is similar to GCP’s. Azure secures its managed services, but customers are responsible for securing the entire stack if running on-premises data centers. They must manage applications, data, and configurations to ensure security within their Azure environments.
Challenges of the Shared Responsibility Model
While the shared responsibility model offers a framework for collaborative cloud security, it’s not without its challenges. Here are some key issues to consider:
- Complexity and Confusion: The model’s nuances can be overwhelming, especially for organizations with limited cloud expertise. Providers use different terminology, adding to the complexity.
- Lack of Visibility and Control: Customers often do not fully understand how providers secure infrastructure, limiting their control over security policies and tools.
- Incident Management and Attribution: In the event of a security breach, determining responsibility can be difficult, causing delays and friction between parties.
- Access Control: Balancing strong access controls with business agility is challenging, especially in multi-tenant environments with shared credentials or third-party tools.
- Misaligned Resources and Incentives: Differences in risk tolerance and security priorities can lead to misaligned investments, with providers promoting tools that may not align with customer needs.
Best Practices for Implementing Shared Responsibility Model
The shared responsibility model in the cloud offers immense opportunity but also harbors potential pitfalls. By following these five best practices, you can navigate the model effectively and achieve a secure cloud environment:
Know Your Service Level Agreement (SLA)
Different cloud providers assign responsibilities differently, so meticulously review your SLA to understand your exact obligations. Don’t hesitate to seek clarification or negotiate terms. If you use multiple providers, do this for each.
Integrate Security Everywhere
Security shouldn’t be an afterthought; it should be woven throughout your development lifecycle. DevSecOps practices—integrating security testing and controls into your development pipeline—help catch vulnerabilities early and streamline processes. Make security everyone’s responsibility, not just security teams.
Prioritize Data Security
Data is your crown jewel, and across all service models (IaaS, PaaS, etc.), it’s always your responsibility. Start by classifying your data based on sensitivity. Build a robust data security strategy from the inside out, enforcing strong perimeter controls and policies. Remember, encryption is your friend!
Open Communication with Your Cloud Provider
Communication is key. Be vigilant about updates from your provider, as service enhancements or changes can impact your security responsibilities. Don’t hesitate to ask questions or seek clarification if anything is ambiguous. Engage your security community – knowledge is power.
Consider Trusted Security Partners
The cloud can feel vast and overwhelming, but you don’t have to overcome it alone. With solutions like CloudDefense.AI, you can simplify your shared responsibility journey. Key offerings include:
- Cloud Infrastructure Entitlement Management (CIEM): Gain complete control over identity and access with CIEM, ensuring the right people have the proper permissions.
- Data Security Posture Management (DSPM): DSPM safeguards your critical data assets and reduce the risk of exposure.
- Cloud Workload Protection: Secure your workloads and applications against evolving threats.
- Cloud Security Posture Management (CSPM): With CSPM, enforce secure configurations across your entire cloud environment for proactive defense.
With the right security partner, cloud security becomes more manageable and effective. Let CloudDefense.AI guide you to safer, more innovative cloud operations.
Conclusion
The cloud offers agility and innovation, but navigating shared responsibility can be complex. While CSPs encourage customers to own their security, CloudDefense.AI simplifies this by smoothly integrating with your CSP, giving you unmatched visibility and control.
Our platform lets you pinpoint vulnerabilities, prioritize risks, and use AI-driven auto-remediation—all in one place. See the difference for yourself. Schedule a FREE demo with CloudDefense.AI today and secure your cloud with confidence.







