In cloud security, risk assessment and risk mitigation are vital processes for protecting environments from threats. Risk assessment identifies, analyzes, and prioritizes security vulnerabilities, while risk mitigation implements controls and fixes to eliminate risks.
A successful cloud security strategy needs continuous assessment for weaknesses and proactive mitigation to prevent exploits. This blog explores the differences between risk assessment and mitigation, their respective roles in cloud security, and how CloudDefense.AI integrates both for comprehensive protection.
What is Risk Assessment in Cloud Security?
Risk assessment is the process of identifying, evaluating, and prioritizing security risks that could impact cloud environments.
This includes analyzing potential threats, vulnerabilities, and misconfigurations that may expose an organization to cyberattacks, data breaches, or compliance failures.
Common security risks assessed in cloud environments include:
- Misconfigurations: Improperly configured cloud resources, such as publicly exposed storage buckets or overly permissive access controls.
- Vulnerabilities: Security flaws in cloud applications, containers, and virtual machines that attackers could exploit.
- Insecure Access Controls: Weak identity and access management (IAM) policies that allow unauthorized access to critical cloud resources.
- Data Exposures: Unprotected sensitive information, such as personally identifiable information (PII) or intellectual property, that is at risk of being leaked or stolen.
Why is Risk Assessment Critical?
Cloud environments present unique security challenges due to their dynamic nature, shared responsibility model, and diverse infrastructure configurations. Key challenges include:
- Dynamic Scaling: Cloud resources are frequently created, modified, and decommissioned, increasing the risk of misconfigurations.
- Multi-Cloud Complexity: Organizations using multiple cloud providers (AWS, Azure, GCP) must manage security policies and configurations across different platforms.
- Cloud-Native Application Security: Microservices, containers, and serverless functions introduce new security risks that traditional security tools may not effectively address.
Continuous risk assessment is essential to maintain visibility, enforce security best practices, and detect vulnerabilities before they can be exploited. By implementing automated security assessments, organizations can proactively reduce their exposure to threats and ensure compliance with security standards.
Key Risk Assessment Features
To effectively assess risks in cloud environments, organizations leverage security tools with automated scanning, real-time monitoring, and compliance enforcement. Some key features include:
- Automated Vulnerability Scanning: Identifies security weaknesses in cloud workloads, containers, and applications by scanning for known vulnerabilities and misconfigurations.
- Misconfiguration Detection: Continuously monitors cloud infrastructure for insecure configurations, such as open ports, unrestricted permissions, or unencrypted data storage.
- Compliance Monitoring: This evaluates cloud environments against industry security frameworks (e.g., GDPR, SOC 2, HIPAA, ISO 27001) to ensure compliance with regulatory requirements.
Organizations can enhance their security posture, mitigate risks, and protect their cloud environments from new threats by integrating these features. In the next section, we will understand risk mitigation.
What is Risk Mitigation in Cloud Security?
Risk mitigation refers to the process of reducing or eliminating identified risks by implementing security controls, automated fixes, and best practices.
While risk assessment identifies potential vulnerabilities and misconfigurations, risk mitigation focuses on taking corrective actions to prevent these risks from being exploited.
Risk mitigation strategies can include:
- Automated remediation: Fixing misconfigurations, patching vulnerabilities, or enforcing security policies automatically.
- Access control enhancements: Strengthening identity and access management (IAM) policies to prevent unauthorized access.
- Encryption and data protection: Securing sensitive data at rest and in transit to prevent leaks or breaches.
- Incident response planning: Preparing for potential security incidents with predefined action plans and monitoring systems.
By actively mitigating risks, organizations can minimize security threats, reduce attack surfaces, and improve their overall cloud security posture.
Why is Risk Mitigation Important?
Cloud environments are constantly evolving, making it crucial for organizations to address security risks rather than react after a breach occurs. Key reasons why risk mitigation is essential include:
- Rapid Threat Evolution: Cyber threats continue to evolve, and new vulnerabilities are discovered regularly. Without mitigation, cloud systems remain exposed.
- Automated Attacks: Attackers use automation to scan for and exploit misconfigurations, requiring organizations to respond with automated defenses.
- Compliance Requirements: Many industries mandate specific security controls, and failing to mitigate risks can lead to compliance violations and legal consequences.
Organizations can substantially lessen their vulnerability to cyber threats and maintain security in cloud environments by adopting proactive risk mitigation strategies.
Key Risk Mitigation Features
To effectively mitigate risks in cloud security, organizations use tools that provide automated remediation, continuous monitoring, and enforcement of security best practices. Key features include:
- Automated Remediation: Security tools can automatically correct misconfigurations, apply patches, or adjust access controls without manual intervention.
- Policy Enforcement: Security frameworks and policies can be applied across cloud environments to ensure resources remain configured securely.
- Continuous Monitoring and Threat Detection: Real-time security monitoring helps detect suspicious activity and respond to threats before they escalate.
Risk mitigation is a continuous process that requires constant adaptation to new threats and vulnerabilities. Organizations can significantly lower security risks and uphold a solid cloud security posture by implementing automated security solutions and following best practices.
The Role of Risk Assessment and Risk Mitigation in Risk Management
Risk management is a combined approach that involves both risk assessment and risk mitigation. Risk assessment focuses on identifying and evaluating potential threats, while risk mitigation involves implementing strategies to reduce or eliminate these risks. Together, they form a proactive framework to protect sensitive data, systems, and assets from security threats.
For a detailed insight into risk management, read our blog: “What is Risk Management?“
Risk Assessment vs. Risk Mitigation: How CloudDefense.AI Combines Both

In cloud security, risk assessment and risk mitigation are two sides of the same coin—one identifies vulnerabilities, while the other ensures they don’t become security incidents.
Organizations focusing solely on assessment accumulate security issues without action plans. Conversely, those mitigating risks without proper assessment may waste resources on low-priority issues, leaving critical vulnerabilities exposed.
To build a robust cloud security strategy, organizations must integrate both risk assessment and mitigation into a continuous, automated process. Let’s explore why both are essential and how they work together to create a strong, proactive cloud security posture.
Risk Assessment Identifies, Risk Mitigation Reduces
- Risk assessment provides visibility into security weaknesses by detecting vulnerabilities, misconfigurations, and compliance gaps.
- Risk mitigation ensures identified risks are addressed efficiently through security controls, automated fixes, and policy enforcement.
Without mitigation, assessments become passive reports that don’t actively improve security. Without assessment, mitigation lacks direction, leading to inefficient security efforts.
Prioritization is Key to Effective Mitigation
- Not all risks are equally dangerous—some are critical (e.g., an exposed database containing sensitive data), while others are lower priority (e.g., outdated encryption on an internal system).
- A strong risk assessment process categorizes threats based on impact and likelihood, allowing mitigation efforts to focus on what truly matters first.
Organizations that lack proper risk assessment often spend resources fixing minor issues while leaving high-risk vulnerabilities unchecked.
Continuous Risk Assessment Enables Real-Time Mitigation
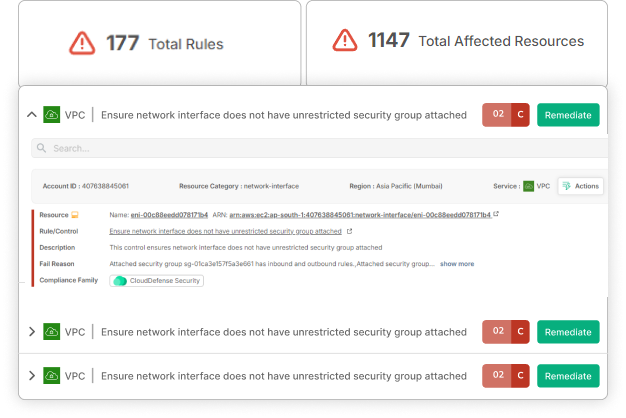
- Cloud environments change constantly. New workloads, user permissions, and configurations are deployed daily, so a one-time risk assessment quickly becomes outdated.
- Continuous monitoring helps detect new security risks in real-time, ensuring mitigation efforts keep pace with evolving threats.
Organizations using automated risk assessment and mitigation can respond to threats instantly rather than waiting for periodic security audits.
Automating Risk Mitigation Reduces Human Error
- Manual security processes are slow and prone to mistakes. For example, a security team may overlook a critical vulnerability or misconfigure a cloud firewall.
- Automating both assessment and mitigation ensures that security best practices are consistently applied and remediations happen instantly when issues are detected.
Example: If a risk assessment detects an overly permissive IAM policy, an automated mitigation system can immediately correct the permissions, preventing unauthorized access.
Compliance Requires Both Assessment and Mitigation
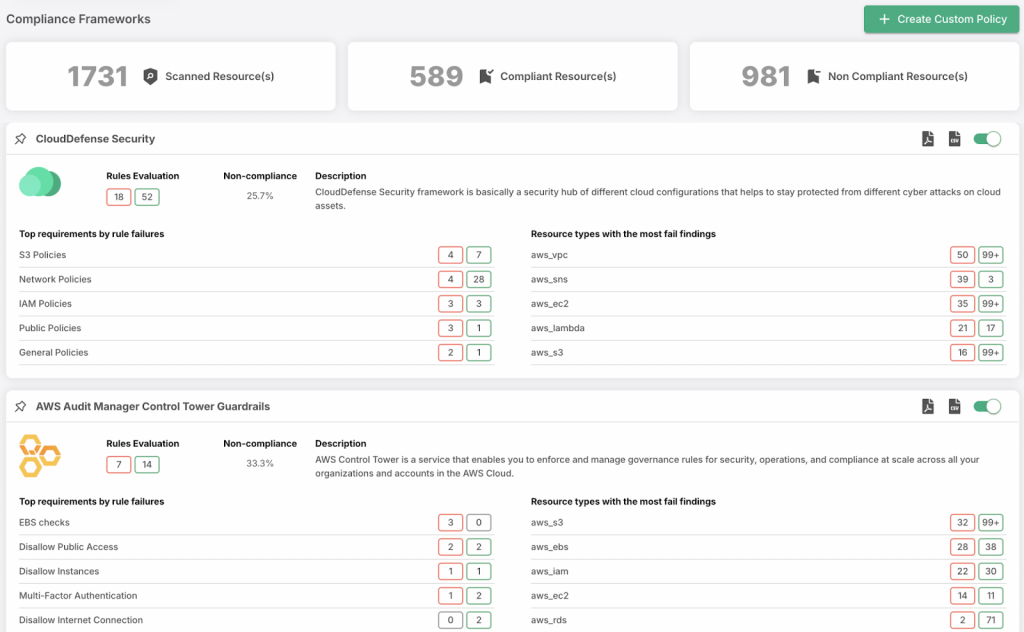
- Security frameworks like GDPR, SOC 2, and HIPAA require both risk assessments and proactive risk mitigation.
- Risk assessments identify compliance violations, while mitigation ensures that organizations stay within regulatory requirements.
Failing to integrate mitigation with assessment can lead to non-compliance penalties and data breaches that could have been prevented.
Benefits of Using CloudDefense.AI for Risk Assessment and Mitigation
Security risks are constantly evolving. Organizations need a solution that not only identifies threats but also mitigates them efficiently. CloudDefense.AI offers a powerful approach to risk assessment and mitigation, ensuring complete protection with minimal manual effort. Here’s how:
Scalability & Automation
Modern cloud environments are dynamic, constantly expanding to meet business demands. CloudDefense.AI seamlessly scales alongside your infrastructure, automating risk assessment and mitigation. This reduces the need for manual security oversight, allowing security teams to focus on strategic initiatives while ensuring continuous protection.
Real-Time Protection
Cyber threats evolve rapidly, making real-time detection and response essential. CloudDefense.AI continuously monitors your cloud environment, detecting vulnerabilities and active threats as they emerge. By addressing risks in real time, organizations can prevent breaches before they cause significant damage.
Proactive Security Posture
Many organizations operate with a reactive security approach—addressing risks only after they become incidents. CloudDefense.AI shifts this paradigm, enabling businesses to adopt a proactive security posture. By identifying vulnerabilities early and implementing preventive measures, CloudDefense.AI helps organizations stay ahead of potential threats.
Improved Compliance & Reduced Risk Exposure
Regulatory compliance is a major concern for businesses operating in the cloud. Failure to meet security standards can lead to penalties, reputational damage, and increased vulnerability to attacks. CloudDefense.AI ensures that cloud environments align with industry best practices and compliance frameworks, reducing the risk of non-compliance and strengthening overall security.
Why CloudDefense.AI is a Comprehensive Solution for Cloud Security Risk Management?
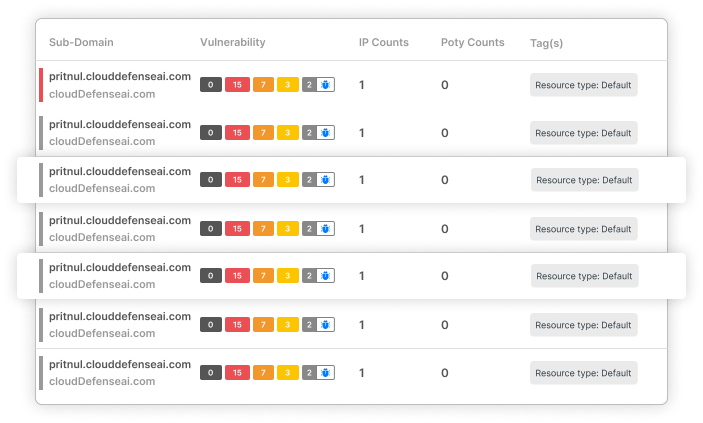
Traditional security methods are outdated—they are reactive, fragmented, and unable to address the swift threats we confront today. CloudDefense.AI employs a modern, proactive strategy, utilizing AI-driven analytics, real-time threat intelligence, and automated risk mitigation to ensure the security of your cloud environment.
- Complete Attack Surface Visibility: No more blind spots. Get full insight into internal, external, and hidden vulnerabilities.
- Predictive Threat Modeling: Understand attack paths before they’re exploited and stop breaches before they happen.
- Smart Risk Prioritization: Focus on high-impact threats that actually matter, not just severity scores.
- Automation & Scalability: Reduce manual effort and ensure security grows with your cloud infrastructure.
- Compliance & Risk Reduction: Stay ahead of industry regulations and minimize security gaps.
CloudDefense.AI is not merely another security tool; it’s a complete risk management platform designed for adapting to cloud security challenges. Schedule a demo today to discover how CloudDefense.AI can enhance your cloud security strategy.







