Hack-Proof Your Cloud and Apps
Hacker’s View™: Hack-Proof Your Cloud and Apps
Uncover the hacker’s perspective and actively defend your cloud against cyber threats with advanced attack analysis and vulnerability mitigation.
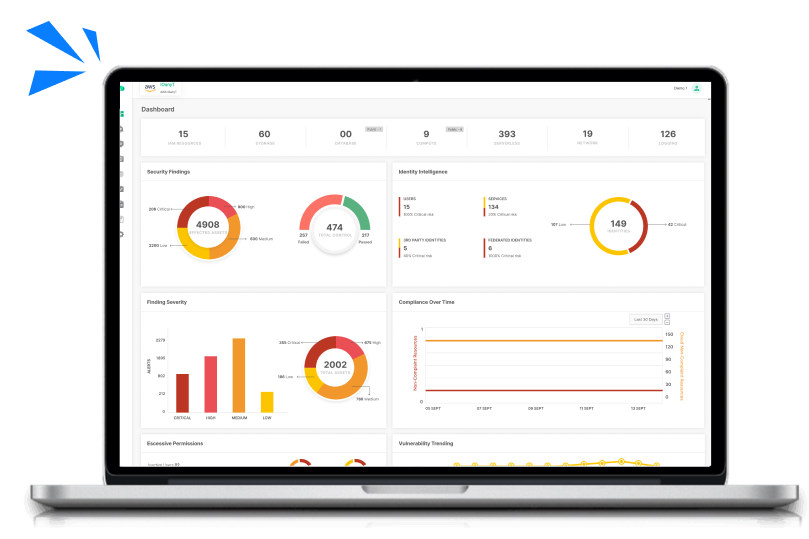
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
Hack-Proof Your Cloud and Apps
See Through the Hacker's Eyes: Spot Vulnerabilities Like a Pro!
View your cloud’s vulnerabilities through a hacker’s lens, revealing insights from surface scans and sensitive data exploration.
Hacker's POV
Get a unique glimpse into your network’s vulnerabilities from the eyes of a hacker. Identify weak points and security gaps effortlessly.
360° Scanning
Attain comprehensive security coverage through our scanning feature, leaving no potential security risks unexamined and ensuring effective mitigation strategies are put in place.
Sensitive Data Exposure
Hacker’s View™ provides an inside look at potential exploits, safeguarding your data with insight into how hackers operate
Defend Like a Pro: Understanding Vulnerabilities the Hacker Way
Discover elusive vulnerabilities and gain a deeper grasp of your organization’s real external threat landscape with our Hacker’s View™ feature
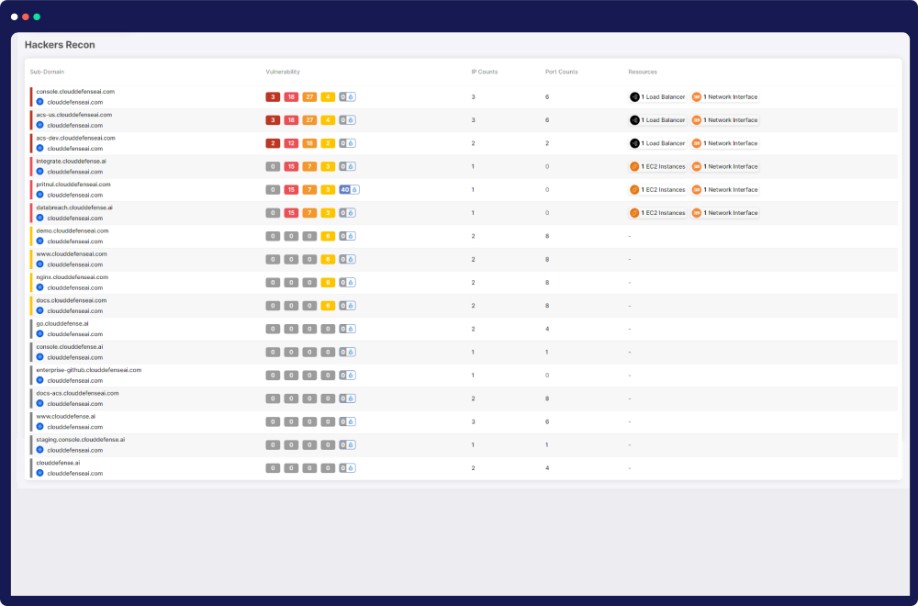
Comprehensive Domain Security Suite
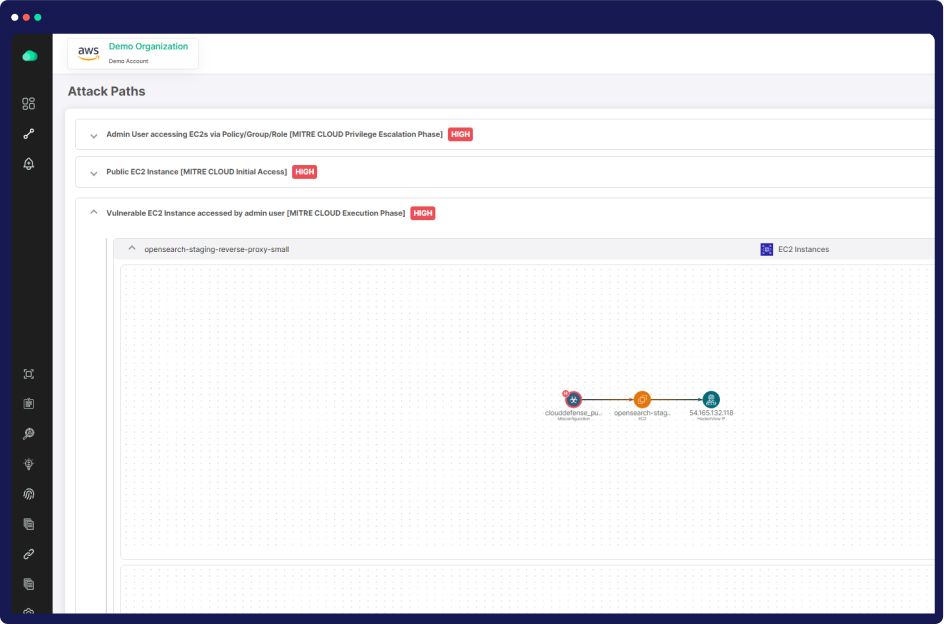
Our advanced feature empowers you to conduct a comprehensive domain survey, subdomain enumeration, IP resolution, vulnerability scans, and port scans. Visualize data with context maps, craft individual attack paths, and reduce noise with organized findings in list view.
Comprehensive Domain Reconnaissance
Hacker’s View™ enables thorough domain analysis, uncovering critical insights for robust security.
Subdomain Enumeration
Discover hidden assets and potential vulnerabilities with our subdomain scanning capabilities.
Port Scans
Evaluate open ports to fortify your network defenses and reduce attack vectors.
Data Visualization
Leverage the power of context maps to gain a holistic view of your security landscape.
Proactive Attack Surface Awareness
At CloudDefense.AI, we empower organizations to proactively safeguard their digital assets. Think like an attacker, continuously assess your external attack surface, and prioritize risk mitigation with our external attack surface management and protection solutions.
Proactive Security Strategy
Follow a proactive approach to security by continuously assessing your entire cloud ecosystem from an external perspective, keeping attackers at bay.
Continuous Risk Assessment
Continuously monitor, detect, and prioritize risks across your entire attack surface to effectively fortify your digital defenses.
Efficient Prioritization
Streamline risk management by prioritizing and remediating vulnerabilities, ensuring you focus on the most critical threats first.
Uncompromising Protection
Prevent attackers from exploiting the path of least resistance with our attack surface protection solutions, safeguarding your high-value digital assets.
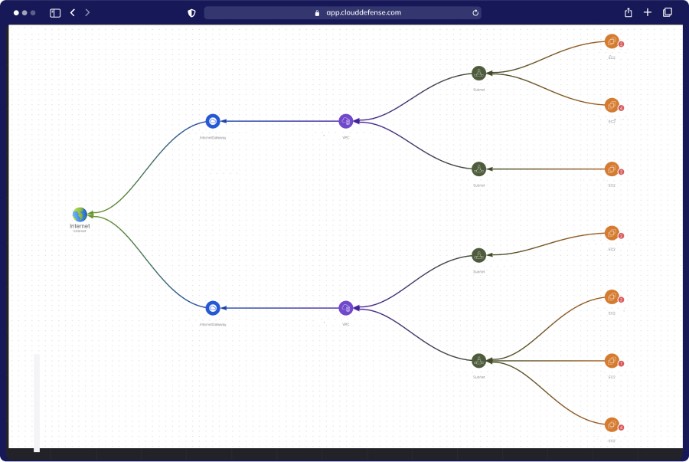
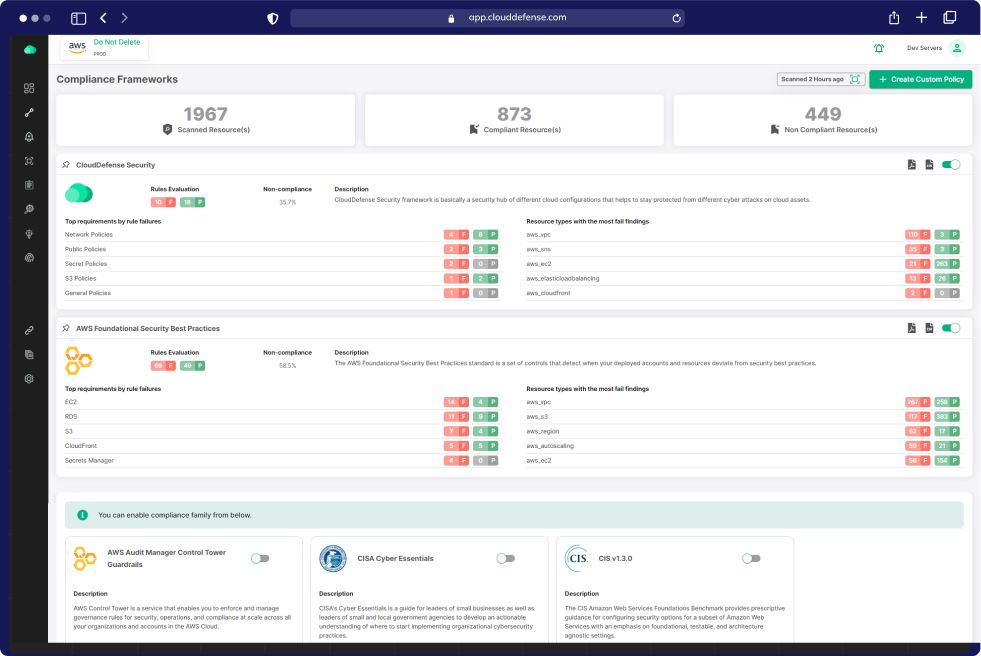
Complete Asset Visibility for Holistic Protection
Experience unmatched visibility with our Hacker’s View™ section on the CloudDefense.AI platform. Explore your scan results from a hacker’s perspective, revealing critical findings, total assets, and scan times, empowering you to secure your assets effectively.
Hacker's Perspective
Gain insights into your system's vulnerabilities through the eyes of a hacker. Identify potential security threats before they can be exploited.
Alerts and Findings
Quickly spot and address security issues with our intuitive interface. Hacker’s View™ provides a comprehensive overview of findings from surface scans.
Attack Surface Visibility
Get comprehensive insights into your organization's assets and attack surface, identifying vulnerabilities and potential entry points that attackers target.
Efficient Scan Times
Monitor scan times in real-time. Hacker’s View™ empowers you to optimize scan schedules for minimal disruption to your operations.
Tailored Insights: Prioritize, Pinpoint, Secure
Our Hacker’s View™ feature offers a unique perspective by allowing you to view surface scan findings from a hacker’s standpoint. You can also tailor your view with filters, effortlessly focusing on severity and instance ID for streamlined cybersecurity insights.
Severity Filter
Easily prioritize and focus on critical issues with our intuitive severity filter by customizing your view to focus on specific threat levels, ranging from Critical and High to Medium and Low, ensuring a thorough threat assessment.
Instance ID Filter
Streamline your workflow by pinpointing specific instances of vulnerabilities, saving you time and effort in remediation.
Efficient Workflow
Seamlessly integrate Severity and Instance ID filters to optimize your security process. Prioritize critical issues and target specific instances for efficient vulnerability management.
Ready to see us in action? Schedule a time
to speak with our team!
Spot unknowns sooner and continuously watch for signs of compromise. Take us on a test drive to see for yourself.




