Every organization running a website on the internet needs to understand about the OpenSSL vulnerability. OpenSSL is a cryptographic library that helps in encrypting communication by the websites on the internet.
In modern times, OpenSSL has transformed from being optional to a necessity for most websites on the internet as it ensures a secure connection. However, the biggest roadblock to a secure connection is the OpenSSL vulnerability, which has had many severe impacts on various websites.
Over the years, OpenSSL has encountered several vulnerabilities that have put the system at severe risk and enabled malicious actors to exploit the system. In this blog, we are going to discuss the OpenSSL vulnerability and all the other associated aspects you need to know for your websites.
Let’s dive right in!
What is OpenSSL?
OpenSSL can be defined as an open-source cryptographic library that is universally utilized to secure the communication of a website on the internet. Almost every website, especially HTTPS websites, widely uses them, and it is generally denoted as “https://” with a lock icon on the browser address section.
By securing a connection, OpenSSL ensures data exchange between the client and server is completely protected and can’t be interpreted by malicious actors. It is widely leveraged by system administrators and developers to encrypt websites.
In general, OpenSSL comes equipped with three core components, and they are the libssl library, the libcrypto library, and a command line utility. With this cryptographic library, users have the liberty to perform various SSL-related tasks, including private key generation, SSL certificate installation, and CSR generation.
Nowadays, it is estimated that over 2.4 million sites from all over the world utilize OpenSSL to secure their communication over the internet. OpenSSL is available for both Windows and Linux, due to which most enterprises are adopting it to counter modern cyber threats.
How Does OpenSSL Work?
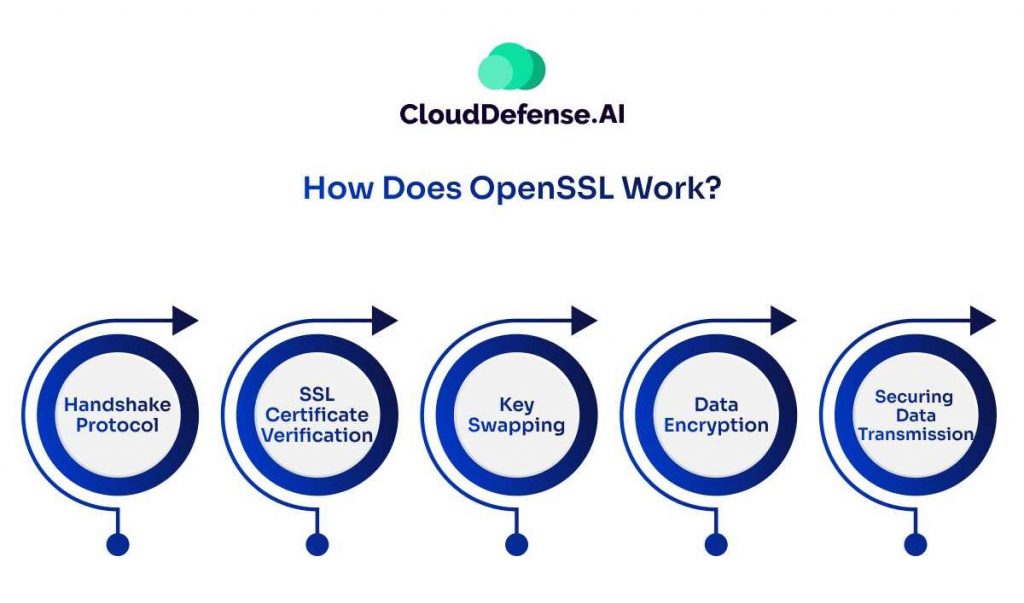
OpenSSL is an open-source software that provides cryptographic functions and tools to secure website communication with the network server. Importantly, it implements the Socket Layer (SSL) and Transport Layer Security (TLS) protocol, which ultimately helps create a secure connection between the client and server.
Besides web servers, OpenSSL is also used by VPNs, emails, and other applications to deliver cryptographic functions like digital signatures, verification, encryption, and decryption.
Basically it works by encrypting and securing the data transmission over the network in the internet and ensuring all the sensitive information remains confidential from unauthorized access. Here’s a detailed overview of how OpenSSL works:
Handshake Protocol
Through the handshake protocol, SSL creates a secure connection between the browser and server while negotiating the parameters that will create a secure connection. The parameters to secure the connection include session keys, SSL version, and encryption algorithm.
SSL Certificate Verification
During the handshake process, the server provides an SSL certificate to the client that usually contains public key and other vital information such as domain name. Then, the web browser(client) verifies the certificate by assessing the digital signature and ensuring they have been supplied by a Certificate Authority.
Key Swapping
When the web browser verifies the SSL certificate, it performs key swapping with the server to create a shared secret key that will be used for encryption and decryption. So when an OpenSSL commences, this secret key is utilized to transmit data.
Data Encryption
Once the shared secret key is established, it is time for the web browser and the server to encrypt and decrypt the data. It is usually done through a symmetric encryption algorithm, and it makes sure all the transmitted data are completely unaffected by interception.
Securing Data Transmission
After everything has been established, along with data encryption, web browsers, and servers can now securely communicate over the internet. All the transmission including response, HTTP request and other are properly encrypted, ensuring no one can manipulate the transmitted data.
What is OpenSSL Vulnerability?
OpenSSL vulnerability highlights the security flaw found in OpenSSL that can be exploited by malicious actors. It allows the attackers to infiltrate the security firewall and interpret the communicated data.
OpenSSL vulnerabilities are mostly found in the OpenSSL library, which is used to apply cryptographic functions to different systems. The most common vulnerability is the cryptographic weakness in the security, and this vulnerability allows the malicious actor to decrypt data, launch cyber attacks, or eavesdrop communication.
The other forms of OpenSSL vulnerability that have plagued many systems are buffer overflow, certification validation issues, DoS, and information leaks. Over the years, many severe vulnerabilities have impacted numerous systems.
Heartbleed, POODLE, BEAST, and DROWN are some of the severe vulnerabilities that allow attackers to steal data. The recent OpenSSL vulnerability that had a major impact are CVE-2022-3602 and CVE-2022-3786. These vulnerabilities had a huge impact on OpenSSL version 3.0 and above, along with applications using the OpenSSL library.
What is the Security Bug Behind these Vulnerabilities?
The security bug behind the above-mentioned vulnerabilities varies, and there is no single particular bug that led to the security flaw. When the web browser and TLS server run on the affected OpenSSL version, it enables the attacker to utilize Remote Code Execution.
The major security bug behind the recent vulnerability, 4-byte CVE-2022-3602 and variable length CVE-2022-3786 is the issue in the OpenSSL X.509 certificate version process. The bug was discovered in the punycode decoder component that lies in the OpenSSL libcrypto library.
Are Both TLS Clients and Servers Impacted by These Vulnerabilities?
Yes, both TLS clients and servers are impacted when these vulnerabilities come into effect. When an OpenSSL 3.0 application confirms an X.509 certificate after receiving it from untrusted sources, it will be affected by the vulnerability. The TLS server and clients are also affected because they are configured with the TLS client authentication.
Under What Conditions Are These Vulnerabilities Exploitable?
In the TLS servers, the vulnerabilities get exploited when they are configured to get manipulated certificates and request client authentication from the attacker. Basically, the server that utilizes mutual TLS would get affected as they authenticate the client’s identity by verifying it with the certificate sent by the client.
However, for the TLS clients, the vulnerabilities will be exploitable when the client gets connected to an attacker-controlled server.
This connection is established when a user is tricked into clicking a phishing link or affected by a man-in-the-middle attack leading to the redirection of traffic. Automated clients like bots or web crawlers might be utilized by attackers to trick users into connecting to a malicious server.
Are Public Exploits Available For These Vulnerabilities?
Yes, there are public exploits that have been made available for the above-mentioned vulnerabilities. Public proof of concept is the most common exploit that is available designed to disrupt a vulnerable system. Besides, there are many advanced public proof of concepts coming along with better effectiveness.
Understanding Major OpenSSL Vulnerabilities Over the Years
OpenSSL has been successful in establishing secure connections on the internet, but over the years, there are many vulnerabilities in OpenSSL that have made the system open to exploitation. Here are some major OpenSSL vulnerabilities that have made an impact:
Heartbleed
Happened back in 2014, Heartbleed was a crucial bug that was discovered in the heartbeat extension of OpenSSL’s implementation.
This major bug enabled attackers to interpret the memory of numerous web browsers(clients) and servers and it ultimately impacted over half a million encrypted websites. The bug was resolved after patching OpenSSL 1.0.1 through the 1.0.1f version.
POODLE
POODLE is a serious bag that impacted thousands of websites in 2014, and it originated due to a major flaw in the SSL 3.0 protocol. POODLE signifies Padding Oracle on Downgraded Legacy Encryption, which enabled malicious actors to decrypt and intercept various HTTPS connections in 2014. After the discovery, organizations were able to mitigate it by disabling SSL 3.0 protocol support in servers and web browsers.
Temporarily, organizations had to configure the server settings and browsers to disable SSL 3.0 and prevent attackers from exploiting it. However, a long-term solution came into effect by enforcing TLS_FALLBACK_SCSV mechanisms, which prevent clients and servers from falling back to less secure SSL versions.
DROWN
Another serious issue that occurred in OpenSSL in the year 2016 is DROWN, which stands for “Decrypting RSA with Obsolete and Weakened Encryption.” The attackers were able to exploit the loopholes in the SSLv2 protocol that enabled them to compromise the secured connection and steal all the sensitive information.
The initial fix was to disable SSLv2 on the web browser and server. However, later, server operators came with two major fixes. The first fix was to make sure the server didn’t initiate SSLv2 cypher suites, and the second fix was to make the server’s private key completely unique.
The server operator also made sure the private key wasn’t utilized by applications like web servers and email servers or server software having SSLv2 connection.
2022 Critical Vulnerability
After 2014’s Heartbleed highly severe OpenSSL vulnerability, it was in 2022 that another such vulnerability came into the limelight. The vulnerability was split into two CVEs where it was named CVE-2022-37786 and CVE-2022-3602 and they made the X.509 digital certificate verification vulnerable, especially the name constraint checking.
The CVE-2022-37786 vulnerability is X.509 email address variable length buffer overflow, whereas the CVE-2022-3602 is X.509 email address 4-byte buffer overflow. Since the OpenSSL version was limited between 3.0 and 3.6, it led to buffer overflow, and this caused potential system crashes, giving attackers the opportunity to launch DDoS attacks.
Examining The Risks: Which Systems are Impacted?
In modern times, OpenSSL vulnerability has become a serious issue, and it is best to examine whether your system is impacted by any of the vulnerabilities. To examine the risk, you will have to first identify which system has been associated with the OpenSSL.
In an organization, systems like email servers, VPN servers, firewalls, routers, web servers, and load balancers utilize OpenSSL, and you will have to assess these systems. You need to utilize a vulnerability scanner that can scan the network to make a list of all the systems that have been affected.
If there is any outdated system lying in your network, it is best to upgrade them because they also pose a huge threat. It is vital to quickly identify the systems because they affect not only the communicating server but also the client.
Through the scanner, you also need to assess the system that acts as a TLS client. Proper examination of the system helps you to establish an OpenSSL vulnerability mitigation strategy in your system.
Best Practices for Mitigating OpenSSL Vulnerabilities
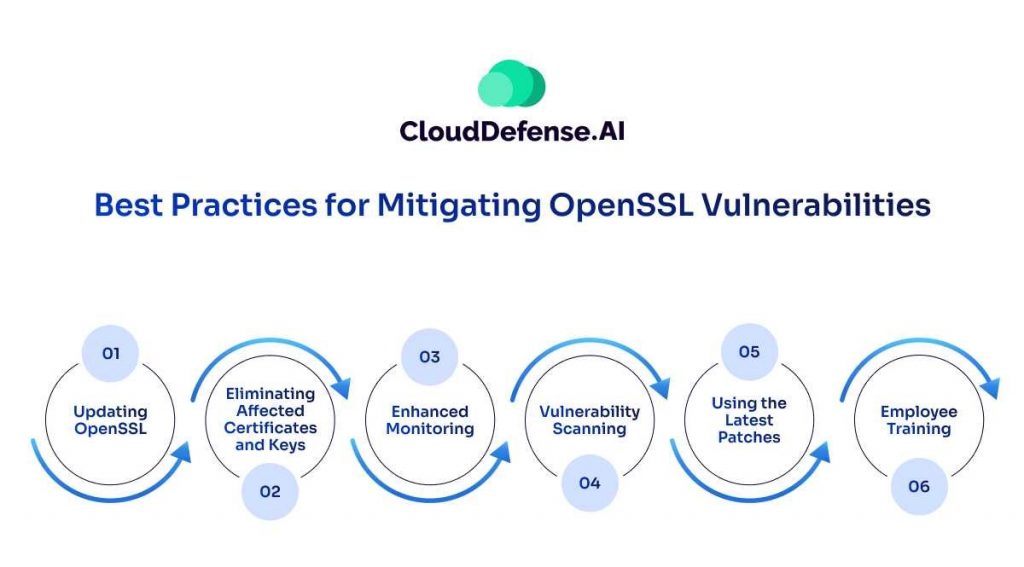
When it comes to mitigating OpenSSL vulnerability, there are some best practices you need to implement. After identifying all the vulnerabilities, you need to apply the following practices that will help in eliminating all the risks:
Updating OpenSSL
One of the best practices you can follow to mitigate OpenSSL vulnerability is updating it to the latest version, which will help eliminate the vulnerabilities present in the system. In addition, all the associated systems, such as the email server, web server, and web browser, should be updated along with version upgrades.
Eliminating Affected Certificates and Keys
Another best practice you can follow when your private key gets exposed is eliminating or replacing them. You should generate a new key and ask your certificate authority to provide your new certificate as a replacement.
Enhanced Monitoring
To efficiently identify and mitigate vulnerabilities, you will have to enhance monitoring of all the systems through OpenSSL. While monitoring, you will have to track any kind of malicious activity and identify the vulnerabilities. You should also proactively review all the logs and alerts which will help you in mitigating vulnerabilities quickly.
Vulnerability Scanning
Performing vulnerability scanning at regular intervals using OpenSSL will help you discover weak spots. Scanning the system through specialized tools will help you to mitigate the vulnerabilities and ensure a proactive approach.
Using the Latest Patches
As a system administrator or developer, it is important to keep the OpenSSL updated with the latest patches released by the OpenSSL and OS vendors to prevent potential threats. You should follow up on the patch release dates and install new patches whenever they come out.
Employee Training
To mitigate vulnerabilities, you will also need the support of your team. You need to train your employees, especially system administrators and developers, to understand vulnerabilities, how they can spot them, and take corrective measures to prevent them. The training should be conducted at regular intervals to create awareness.
Final Words
OpenSSL vulnerabilities are a serious issue that should be prioritized by every organization across the industries operating on the web. These vulnerabilities will not only compromise your secured connection but also enable attackers to steal data and get access to your system.
In this article, we have mentioned various OpenSSL vulnerabilities that have affected the system and how these vulnerabilities affect the system. We have also come up with all the best practices your organization can follow to prevent the vulnerabilities affecting your system.







