As the number, complexity, and sophistication of cyber threats continue to grow in recent times, organizations undergo a perpetual quest to reinforce their security measures. Amidst this multitude of threats–each bearing its own unique vulnerability–the question arises: how can they ensure the security of their systems? Well, this is precisely where two key acronyms come into play: MITRE ATT&CK and NIST CSF.
Now, what do these frameworks actually accomplish, and how specifically do they enhance the security of our digital lives? In this blog, let’s dive deeper into the intricacies of MITRE ATT&CK vs. NIST CSF to uncover the answer to these questions.
Understanding the MITRE ATT&CK Framework
What is MITRE ATT&CK?
Pronounced as “miter attack,” MITRE ATT&CK represents a framework that serves us in understanding and categorizing the methods cyber adversaries employ for their attacks. Essentially, it’s like having a cheat sheet on how cybercriminals operate.
It was created by MITRE, a not-for-profit organization that works on cybersecurity research and development. The acronym “ATT&CK” stands for “Adversarial Tactics, Techniques, and Common Knowledge,” and it’s like a treasure trove of information for both cybersecurity experts and those interested in understanding how cyberattacks happen.
Components of MITRE ATT&CK:
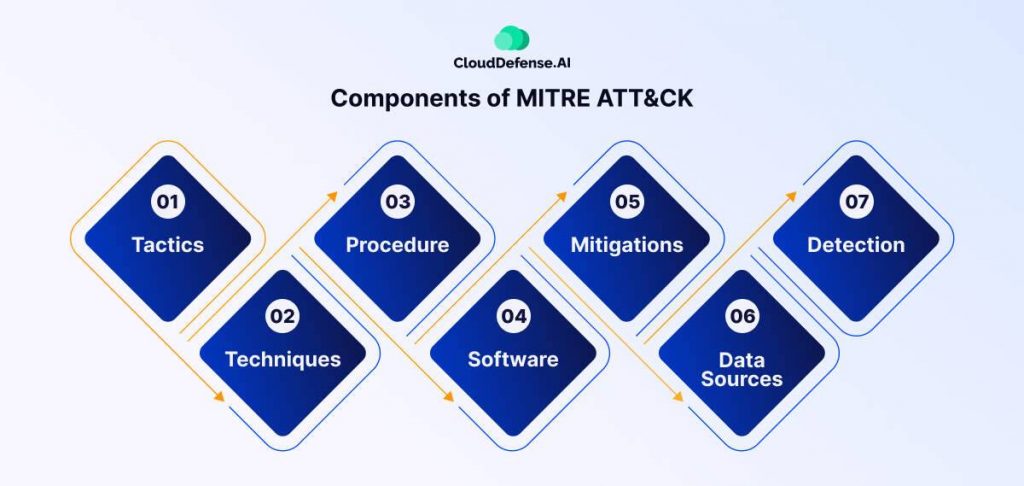
MITRE ATT&CK framework is organized into several components:
Tactics: Tactics can be likened to the overarching objectives pursued by cyber attackers. They serve as the high-level goals of a cyberattack, essentially the big-picture targets. MITRE ATT&CK characterizes tactics with various facets, such as “Initial Access” (pertaining to the means by which attackers infiltrate a system), “Execution” (involving the execution of malicious code), and “Exfiltration” (focusing on the extraction of data).
Techniques: Techniques are the specific maneuvers or actions that attackers employ to fulfill the tactical objectives that we discussed above. Think of techniques as the detailed steps or tools found within an attacker’s toolkit. For example, a technique aligned with gaining initial access could be “Phishing,” which entails the art of deceiving a user into clicking on a malicious link.
Procedure: This is a more detailed description of a specific technique. It’s the nitty-gritty of how the technique is put into practice. For instance, a procedure related to the phishing technique might intricately outline the exact steps an attacker takes to craft a convincing phishing email.
Software: This component lists the specific malware, tools, or software that attackers commonly use in their techniques. It’s like knowing what weapons an attacker might carry. For example, “Emotet” is a known malware often associated with phishing attacks.
Mitigations: This is where the good things come in. They are the strategies and actions that organizations can employ to defend against the techniques and tactics described in ATT&CK. Think of mitigations as the countermeasures that bolster defenses against cyber threats. For instance, implementing two-factor authentication can act as a mitigation strategy to reduce the risk of credentials being stolen through techniques like “Credential Access.”
Data Sources: Data sources serve as valuable breadcrumbs left behind by attackers, indicating the kinds of logs and information organizations can gather to detect and investigate cyberattacks. These are the digital footprints that help in uncovering malicious activities. For instance, to detect the execution tactic, one might scrutinize Windows event logs or network traffic data.
Detection: The art of detection in cybersecurity is akin to detective work. It entails the methods used to identify signs of malicious activity within the data sources. For instance, spotting the use of PowerShell in an atypical manner for your organization could be a telltale sign of malicious execution.
Understanding the NIST CSF Framework
What is NIST CSF?
The NIST CSF, or National Institute of Standards and Technology Cybersecurity Framework, is a voluntary, risk-based framework developed by the U.S. government to help organizations manage and improve their cybersecurity posture. The framework finds widespread use across diverse industries – not limited to just the borders of the United States.
Essentially, it is a navigational tool for enterprises and corporations to adhere to, in order to safeguard against cyber perils. It enables them to comprehend, regulate, and diminish their cyber defense vulnerabilities. The NIST CSF is not a one-size-fits-all thing. It’s flexible and can be adapted to fit the specific needs and risks of different organizations. It’s like giving them a toolbox full of tools and telling them, “Use these in the way that makes the most sense for you.”
NIST CSF Core Functions
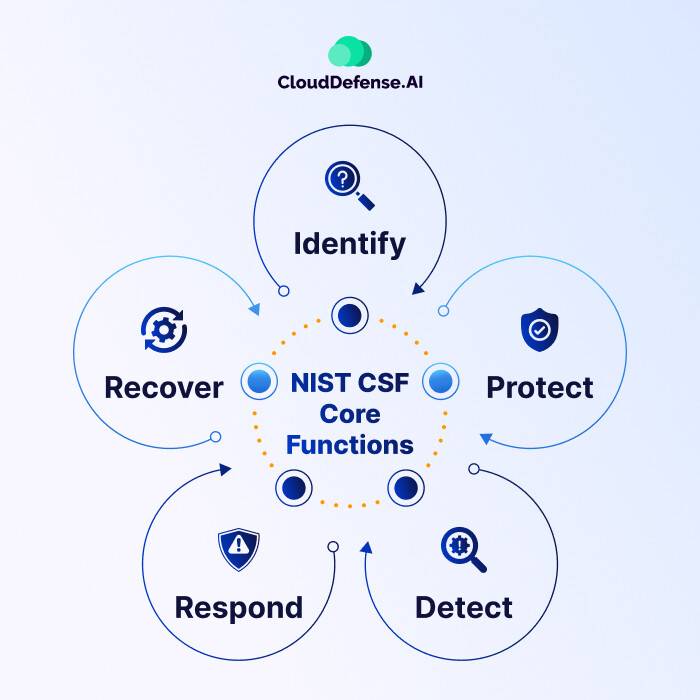
The NIST CSF breaks things down into five main functions:
Identify: This function is all about knowing and spotting what you actually need to protect. It’s like making a comprehensive list that helps you figure out what data, systems, and assets are important to your organization. This step helps you know what you have and what needs protection.
Protect: Now that you know what’s important, you can put safeguards in place. You formulate security policies, enforce access controls, and undertake measures such as data encryption. The goal is to make it as hard as possible for bad actors to get in.
Detect: With this function, you actively monitor your systems for any potential indicators of trouble; your aim is to swiftly identify and address unusual activities such as suspicious logins or abnormal network traffic. Early detection can help you respond faster.
Respond: When you detect a cybersecurity incident, you need to have a plan for what to do next. This function is all about taking action. You’ll have procedures in place for containing the incident, mitigating the damage, and recovering from it.
Recover: Once a cybersecurity attack has been handled, the process of restoration aims to return things to their usual state. This may involve data retrieval, system reconstruction, and utilizing insights from the event to enhance security measures. It’s like fixing your house after a storm so that it’s even stronger and more resilient for the next one.
Why should the MITRE ATT&CK and NIST CSF be used together?
NIST CSF is like the foundation and framework for an organization’s cybersecurity governance, while MITRE ATT&CK provides detailed blueprints and guidance on how to defend against cyber threats effectively.
With its five governance areas—protect, identify, detect, respond, and recover—NIST CSF gives organizations a high-level structure to manage their cybersecurity efforts. It sets the stage, defining what needs to be done in broad strokes. It doesn’t, however, delve into the nitty-gritty of specific cyberattack tactics, techniques, and procedures (TTPs). It’s like a blueprint for a house, but it doesn’t specify the individual materials and methods used to construct it.
On the other hand, the MITRE ATT&CK matrix is all about those practical details about a situation. It provides an exhaustive matrix of known attack techniques and procedures, categorizing them by threat actors and platforms. It’s like an encyclopedia of cyber threats, showing organizations exactly how attackers might breach their defenses. This is invaluable for security practitioners, but if used in isolation, it lacks the broader organizational context that NIST CSF offers.
Now, here’s where the magic happens: When you combine NIST CSF and MITRE ATT&CK, you get the best of both worlds. NIST CSF lays out the governance structure, telling you what aspects of cybersecurity to focus on. It’s the “what” and “why.” MITRE ATT&CK, on the other hand, provides the “how” and “what to look out for” in exquisite detail.
In fact, you can create a comprehensive cybersecurity plan by matching the precise tactics and procedures of MITRE ATT&CK with the high-level aims of NIST CSF. NIST CSF tells you that you need a security camera in your house, and MITRE ATT&CK tells you how to position it, what to look for in the footage, and what to do if you spot something suspicious.
So, in essence, you need both to have a well-rounded cybersecurity program. You could possess all the technical know-how but lack the strategic direction if NIST CSF is missing. Similarly, without MITRE ATT&CK, you might have the strategy but not know how to practically defend against real-world threats.
When paired together, they produce a powerful synergy that improves an organization’s cybersecurity posture in operational technology (OT) and traditional IT contexts. It’s like having the blueprint and the skilled craftsmen to build a robust security fortress.
Key Differences: MITRE ATT&CK vs. NIST CSF
| Aspect | MITRE ATT&CK | NIST CSF |
| Purpose | Threat intelligence framework | Cybersecurity risk management framework |
| Primary Focus | Specific adversary tactics and techniques | Holistic cybersecurity risk management |
| Scope | Detailed TTPs used by threat actors | Broad framework covering risk management |
| Framework Type | Threat intelligence framework | Risk management framework |
| Tactical vs. Strategic | Tactical (focuses on specific techniques) | Strategic (focuses on overall risk) |
| Detailed Threat Information | Provides extensive adversary behavior data | Offers high-level guidance |
| Components | Tactics, techniques, procedures, groups, etc. | Identify, Protect, Detect, Respond, Recover |
| Prescriptive Controls | Not prescriptive; offers observations | Includes prescriptive security controls |
| Specificity | Highly specific, covers known threat behavior | General, adaptable to various industries |
| Adversary-Centric | Adversary-centric; focuses on adversary actions | Organization-centric; covers risk factors |
| Incident Response Focus | Specific techniques for incident response | Provides a broader incident response plan |
| Common Language | A common language for describing threats | A common language for managing cybersecurity |
| Integrating Threat Intel | Provides threat intelligence for risk assessment | Can integrate threat intelligence sources |
| Continuous Improvement | Emphasizes ongoing monitoring of threat landscape | Promotes continuous security program improvement |
| Industry Applicability | Relevant for organizations with a focus on threat intelligence | Applicable across various industries for risk management |
| Customization | Customizable for specific threats and environments | Customizable for organization-specific risk profiles |
FAQ
Which framework is more technical, MITRE ATT&CK or NIST CSF?
MITRE ATT&CK is the more technical of the two frameworks. It offers a comprehensive and in-depth matrix of established cyberattack methods, strategies, and protocols (TTPs). It is mostly intended for technical cybersecurity practitioners who must comprehend the particular techniques that attackers may employ to infiltrate networks.
In contrast, NIST CSF provides a higher-level, strategic framework for managing cybersecurity initiatives within an organization while being less technical.
How does NIST CSF help with regulatory compliance?
NIST CSF can be a valuable tool for achieving regulatory compliance. Many regulatory bodies and standards organizations, such as the GDPR, HIPAA, and NIST itself, reference or recommend using the NIST CSF as a cybersecurity framework.
Aligning your organization’s practices with the NIST CSF not only demonstrates a structured approach toward managing and enhancing cybersecurity but also presents concrete evidence to both regulators and auditors.
Is MITRE ATT&CK suitable for non-technical staff?
MITRE ATT&CK is primarily designed for technical cybersecurity professionals, so it may not be the best fit for non-technical staff who lack a deep understanding of cybersecurity concepts. Its complexity can overwhelm employees without technical backgrounds. However, it can be used as an applicable source for reference and information in security awareness training.
Conclusion
After examining the comparisons between MITRE ATT&CK vs. NIST CSF, a common question arises: which framework is the best? However, there is no direct answer to this question. Both have their strengths. NIST provides a straightforward way to assess security, while MITRE’s ATT&CK offers a more detailed and diverse set of tactics and techniques.
So, here’s what we recommend to level up your network security: Combine the best of both. First, take a close look at the specific risks your organization is up against using NIST. It’s like setting the stage. Then, put your knowledge into action by testing out tactics, techniques, and procedures laid out in ATT&CK. It’s like the practical application phase.
Taking the pros of both frameworks, you can develop proactive and reactive cybersecurity strategies that are relevant to the risks your organization faces. This way, you’ll be better equipped to protect your network and data.







