Have you ever searched online for a free version of that expensive software you need? We’ve all been there, but what if that tempting download turns your computer from a productivity tool into a hacker’s playground? This article discussed the dark side of YouTube videos offering cracked software, revealing how cybercriminals exploit our desire for freebies to spread malware.
Keep reading as we discuss the malware threat on YouTube, how hackers infiltrate YouTube accounts, the tactics they use, and the impact these infections can have, even if they seem less sophisticated than other cyberattacks.
How Does YouTube Serve as an Attack Vector?
YouTube’s massive user base and open platform make it an attractive target for cybercriminals seeking to spread malware. Here’s how attackers exploit the platform:
Account Compromise:
- Hackers gain access to legitimate YouTube accounts, often through phishing or credential stuffing.
- Compromised accounts, especially those with established followings, lend credibility to malicious content.
Deceptive Content Creation:
- Attackers create videos promising popular cracked software, game cheats, or exclusive content.
- AI-generated videos are sometimes used to quickly produce convincing, yet fraudulent, content.
- Video titles and descriptions are optimized with trending keywords to appear in search results.
Malicious Link Distribution:
- Video descriptions contain links to external websites hosting malware.
- These links are often disguised as download pages for the promised software.
- URL shorteners may be used to obscure the true destination of these links.
Social Engineering Tactics:
- Videos often create a sense of urgency or exclusivity to encourage clicks.
- Comments sections are filled with fake positive reviews to boost credibility.
- Attackers may interact with potential victims, offering personalized “support.”
Exploiting YouTube’s Recommendation Algorithm:
Malicious videos can appear in users’ recommended feeds by using trending tags and generating high engagement (often through bot networks).
Bypassing Content Moderation:
- Attackers frequently update video content and descriptions to evade automated detection systems.
- Some use private or unlisted videos shared in targeted communities to avoid broader scrutiny.
Leveraging YouTube Ads:
In some cases, cybercriminals create malicious ads that appear before or during legitimate videos.
Cross-Platform Amplification:
Links to malicious YouTube videos are shared across other social media platforms, expanding the potential victim pool.
How the Attack Unfolds?
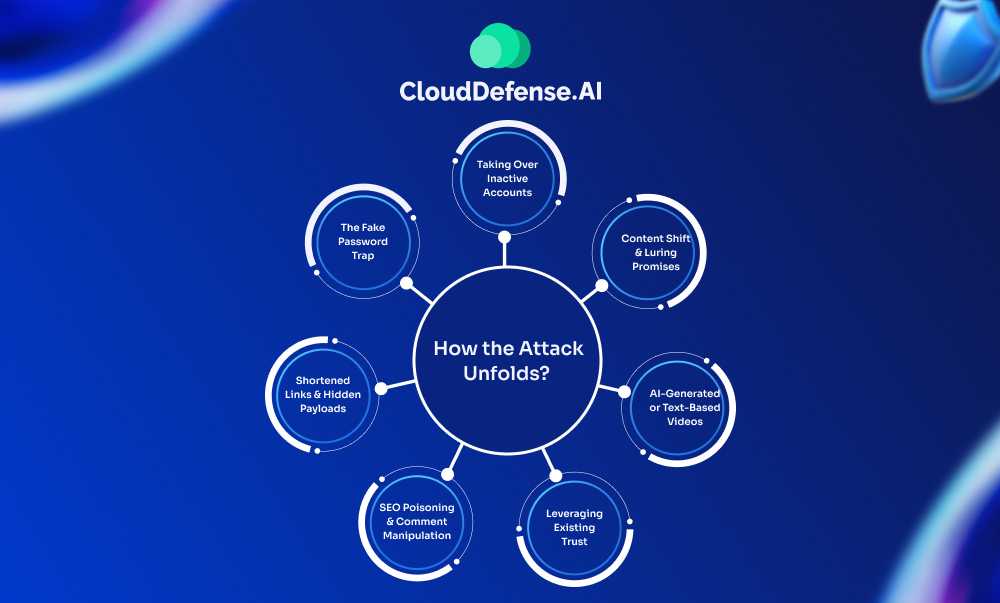
Taking Over Inactive Accounts
Attackers target old YouTube channels that haven’t been used in years. These are often vulnerable because the owners might have forgotten their login details or used weak passwords. Data breaches can also expose such credentials, making them easy targets.
Content Shift & Luring Promises
Once in control, attackers upload new videos that drastically differ from the channel’s past content. These new videos typically have one goal: lure you in with the promise of free, cracked versions of popular software. They might even target channels with existing audiences to appear more trustworthy.
AI-Generated or Text-Based Videos
The videos themselves may not be high-production. Attackers sometimes use AI-generated voices or simply text overlays on animations to keep costs low. But the message remains clear: download the “free” software through the provided link.
Leveraging Existing Trust
The attackers might target channels with established audiences, from a few subscribers to over a hundred thousand. These accounts hold more weight as trusted sources, making them more likely to trick viewers into clicking the malicious link.
SEO Poisoning & Comment Manipulation
To get their videos seen, attackers resort to various tactics. They might:
- Stuff the video with keywords: This makes the video appear in searches for cracked software, ensuring it reaches people actively looking for such content.
- Target specific regions: By using keywords in local languages, attackers can focus their campaigns on specific regions.
- Fake positive comments: They might use compromised accounts to leave positive comments about the “free software,” creating a false sense of security. Disabling comments altogether can also be a tactic to prevent victims from warning others.
Shortened Links & Hidden Payloads
The video description will likely include a shortened link (e.g., Bitly) that supposedly leads to the download page. Clicking it actually downloads malware disguised as the desired software. File-sharing platforms or compromised websites often host these malicious files.
The Fake Password Trap
The description might also provide a password to “unlock” the download. This adds another layer of deception, making the victim believe they have a legitimate software installer with password protection.
Types of Potential Malware
The investigation of YouTube-based malware distribution identified a clear trend towards using commodity loaders and infostealers. These types of malware offer cybercriminals a cost-effective yet potent arsenal for compromising user systems. Let’s examine the primary culprits:
RedLine
RedLine emerged as the most prevalent malware in our study. This versatile info stealer primarily targets browser data and stored credentials on infected machines. However, its functionality extends beyond mere data theft; RedLine can also serve as a downloader and backdoor, providing attackers with a robust toolkit for system exploitation.
Despite its comprehensive capabilities, RedLine is surprisingly affordable for cybercriminals. The standalone binary can be acquired for approximately $150, while a monthly subscription service (Malware-as-a-Service or MaaS) is available for around $100. This low barrier to entry likely contributes to its widespread use in these campaigns.
RaccoonStealer
Another frequently observed threat is RaccoonStealer. Like RedLine, this infostealer specializes in credential and data theft from infected systems. RaccoonStealer is offered at an even lower price point, with weekly access available for about $75 or monthly subscriptions for $200, again as a MaaS offering.
Other Malware
While RedLine and RaccoonStealer dominated our findings, it’s important to note that this distribution vector is well-suited for a variety of other malicious software. We’ve seen evidence of other infostealers and loaders such as Vidar, Smokeloader, and Privateloader being disseminated through similar tactics in past campaigns involving fraudulent cracked software. These have all been spotted in previous “cracked software” scams.
The bottom line? These cybercriminals are using cheap, readily available malware to cast a wide net. They’re not after specific targets – they’re hoping to catch as many unsuspecting users as possible.
How to Detect and Prevent Malware Attacks
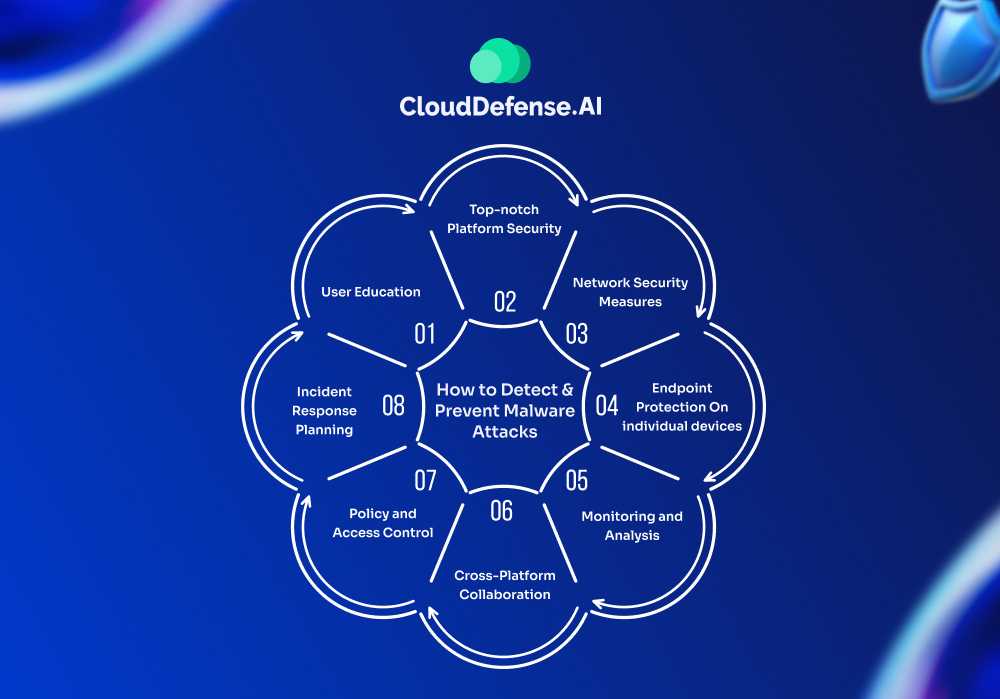
As the landscape of cyber threats continues to evolve, it’s crucial to stay ahead of the curve. Here are some key strategies for detecting and preventing these malware attacks:
User Education
The first line of defense is always an informed user base. Organizations should:
- Conduct regular cybersecurity awareness training
- Emphasize the risks of downloading ‘cracked’ software
- Teach employees to recognize signs of compromised or suspicious accounts
Top-notch Platform Security
Video sharing platforms like YouTube should:
- Implement more robust account takeover protection measures
- Develop AI-driven content analysis to flag suspicious video uploads
- Improve automated detection of malicious links in video descriptions
Network Security Measures
IT departments can:
- Deploy advanced firewalls and intrusion detection systems
- Implement URL filtering to block known malicious domains
- Use sandboxing technologies to safely analyze suspicious downloads
Endpoint Protection On individual devices:
- Install and regularly update reputable antivirus software
- Use browser extensions that warn against potentially harmful websites
- Enable automatic software updates to patch known vulnerabilities
Monitoring and Analysis
Security teams should:
- Continuously monitor for new IoCs across various platforms
- Utilize threat intelligence feeds to stay updated on emerging attack vectors
- Perform regular security audits and penetration testing
- Consider using cloud and application security solutions to add an extra layer of defense. These solutions can help identify and block malicious activity within cloud storage platforms and applications you use, providing a broader safety net.
Cross-Platform Collaboration
To combat the spread across multiple sites:
- Encourage information sharing between platform operators
- Participate in industry-wide threat intelligence networks
- Cooperate with law enforcement to track and disrupt cybercriminal operations
Policy and Access Control
Organizations can:
- Implement strict software installation policies
- Use application whitelisting to prevent unauthorized software execution
- Employ the principle of least privilege for user accounts
Incident Response Planning
Be prepared by:
- Developing and regularly updating an incident response plan
- Conducting tabletop exercises to test the plan’s effectiveness
- Establishing clear communication channels for reporting suspicious activity
Final Words
Attackers are adept at exploiting our desire for free software by compromising YouTube accounts and using deceptive tactics. While some videos are flagged quickly, others remain undetected for months.
Social media platforms fight this battle, but the ultimate responsibility lies with us. Employing strong passwords, skepticism towards too-good-to-be-true offers, and reliable security software, we can defend ourselves against these ever-evolving online threats.







