Malware has become a serious threat in the world, harming individuals and multi-million dollar companies all over. A whopping 450,000 new strains pop up daily, with each one having the potential to cause grave financial damage. But fear not! Malware detection is here to save the day.
Keep reading as we explore different malware detection techniques and technologies. From traditional signature-based methods to cutting-edge machine learning, we’ll break down how these tools work and their challenges.
Malware Detection Techniques
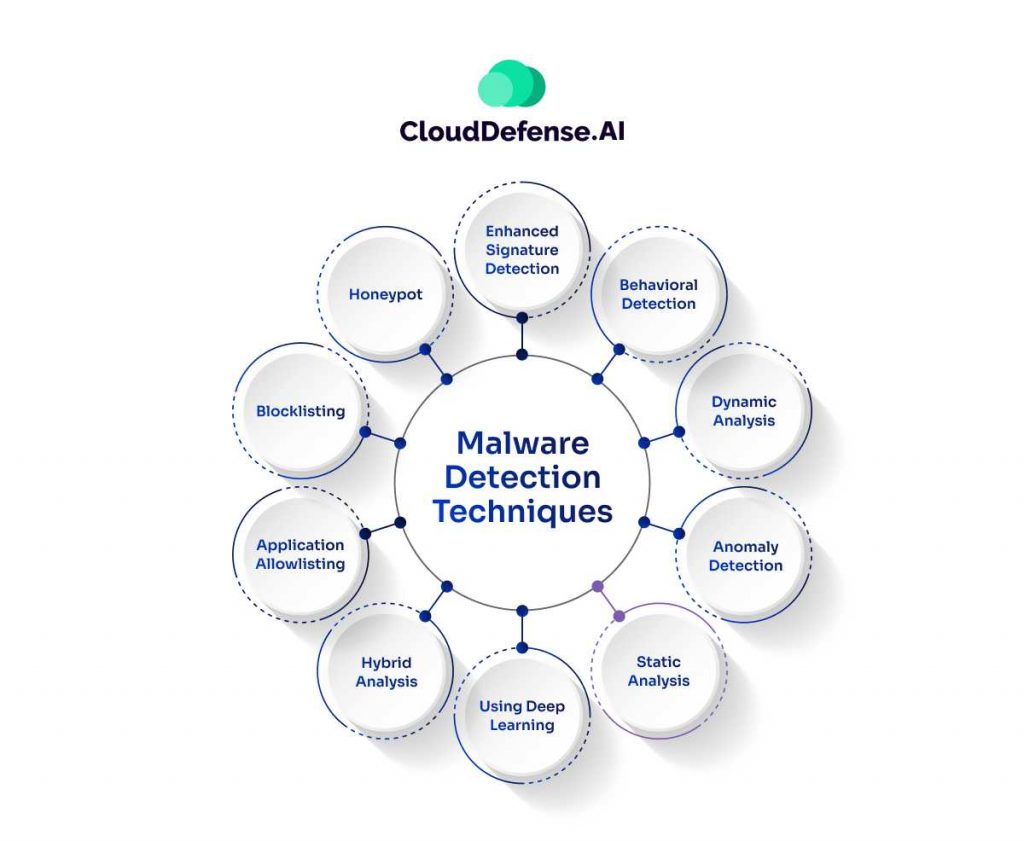
Malware detection techniques have evolved significantly over the years to combat the sophistication of cyber threats. Here’s an overview of various techniques employed in detecting and analyzing malware:
Enhanced Signature Detection
Enhanced signature detection builds upon traditional signature-based methods by incorporating advanced techniques to overcome their limitations. For instance, checksumming, which calculates CRC checksums, provides a more nuanced approach to identifying malware by considering the data’s integrity and position. Moreover, reduced masks, known plaintext cryptanalysis, statistical analysis, and heuristics are employed to detect polymorphic malware, which can alter its code to evade traditional signature-based detection.
Behavioral Detection
Behavioral detection focuses on identifying malware based on its unusual activities or behaviors rather than relying solely on known signatures. This technique observes actions such as file encryption, network communication, or system modifications that deviate from normal behavior. By monitoring these anomalies, security systems can flag and respond to potential threats in real-time.
Dynamic Analysis
Dynamic analysis involves executing suspected malware within a controlled environment, such as a sandbox, to observe its behavior. This technique allows security analysts to study the malware’s actions without risking damage to the actual system. By monitoring the malware’s runtime behavior, analysts can identify malicious activities and patterns, enabling them to develop countermeasures and enhance threat intelligence.
Anomaly Detection
Anomaly detection uses artificial intelligence and machine learning algorithms to establish a baseline of normal system behavior and identify deviations indicative of potential malware infections. By continuously monitoring system activities and comparing them against established norms, anomaly detection techniques can detect previously unseen threats or zero-day attacks.
Static Analysis
Static analysis involves examining the characteristics and structure of suspicious files without executing them. This method assesses file attributes such as file type, size, metadata, and strings to identify potential indicators of compromise. While static analysis provides valuable insights into the nature of malware, it may struggle to detect sophisticated threats that exhibit malicious behavior only upon execution.
Using Deep Learning
Deep learning-based malware detection employs complex neural network models to analyze and classify software as either benign or malicious. By training on extensive datasets of known malware and benign software, these models can identify subtle patterns and features indicative of malware, enabling them to detect previously unseen threats effectively.
Hybrid Analysis
Hybrid analysis combines the strengths of both static and dynamic analysis techniques to provide comprehensive malware detection and analysis. By integrating insights from static file examination with dynamic behavior monitoring, hybrid analysis can accurately identify and characterize malware while minimizing false positives and negatives.
Application Allowlisting
Application allowlisting involves specifying a list of approved applications that are permitted to run on a system while blocking all others. This proactive approach reduces the attack surface by only allowing known and trusted applications to execute, effectively mitigating the risk of malware infections.
Blocklisting
Blocklisting entails specifying certain files, domains, or IP addresses that are known to be malicious or suspicious, preventing them from accessing the system or network. By maintaining a comprehensive blocklist of known threats, organizations can prevent malware infections and unauthorized access attempts.
Honeypot
Honeypots are decoy systems or files designed to attract and deceive attackers or malware. By luring potential threats into a controlled environment, security professionals can gather valuable intelligence about their tactics, techniques, and procedures (TTPs) without exposing real systems to risk. Honeypots enable organizations to study emerging threats and develop effective countermeasures to protect their networks.
Malware Detection Technologies
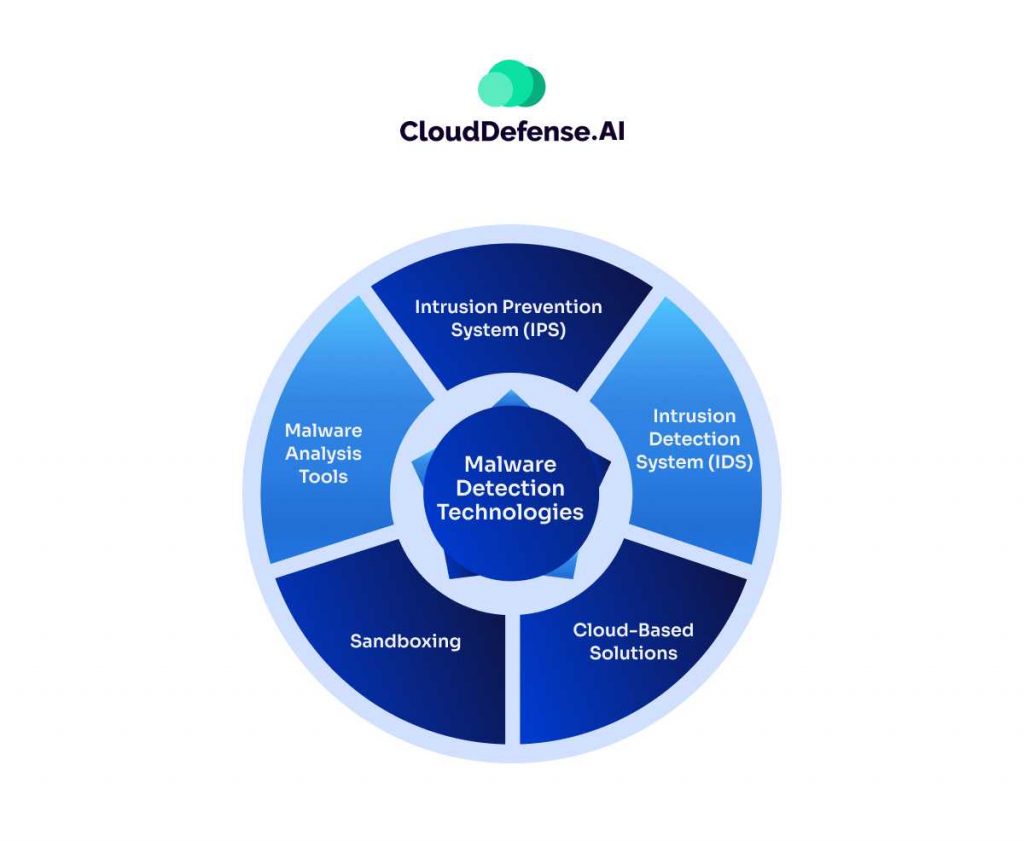
Malware detection technologies protect organizations against malware by employing the many techniques highlighted above. Here’s an overview of key technologies utilized in malware detection:
- Intrusion Prevention System (IPS): An IPS is a network security solution that actively monitors network traffic to detect and prevent malicious activities or attacks. IPS systems operate in real-time, inspecting incoming and outgoing traffic for signs of known malware signatures, anomalous behavior, or suspicious patterns. Upon detection, an IPS can take immediate action to block or quarantine the malicious traffic, thus preventing it from reaching its intended target and mitigating potential damage to the network.
- Intrusion Detection System (IDS): IDS are security solutions that passively monitor network traffic or system activity for signs of unauthorized access, malicious activities, or security policy violations. Unlike IPS, IDS does not actively block or prevent detected threats but instead generates alerts to notify security personnel of potential security incidents. IDS can operate at the network level (NIDS) or the host level (HIDS), providing visibility into potential threats across an organization’s network infrastructure.
- Malware Analysis Tools: Malware analysis tools are essential for analyzing and dissecting malicious software to understand its functionality, behavior, and impact. These tools include a range of techniques, including static analysis, dynamic analysis, and behavioral analysis, to uncover hidden malware characteristics and identify indicators of compromise, or IoCs. Examples of malware analysis tools include disassemblers, debuggers, reverse engineering platforms, and sandboxing environments, which enable security analysts to dissect and analyze malware samples in a controlled and isolated environment.
- Sandboxing: Sandboxing solutions provide a secure and isolated environment for executing and analyzing potentially malicious files or applications without risking harm to the main system. Sandboxes simulate real-world operating environments, allowing security analysts to observe the behavior of malware samples in a controlled setting. By monitoring the actions and interactions of malware within the sandbox, security teams can identify malicious behavior, extract IoCs, and develop countermeasures to protect against future threats. Sandboxing is particularly effective for detecting zero-day exploits and unknown malware variants that evade traditional detection methods.
- Cloud-Based Solutions: Cloud-based malware detection solutions use the scalability and resources of cloud infrastructure to enhance detection capabilities and improve threat intelligence sharing. These solutions utilize cloud-based analytics, machine learning algorithms, and distributed threat intelligence to identify and mitigate malware threats across large-scale networks and diverse environments. Cloud-based solutions offer advantages such as real-time threat updates, centralized management, and automated response capabilities, making them ideal for organizations seeking comprehensive and scalable malware detection solutions.
Final Words
Protection against malware is essential for companies aiming to conduct secure business operations. Employing strong malware detection techniques and advanced technologies is key together with understanding malware types, adopting multi-layered security, and best practices.
CloudDefense.AI offers an all-in-one platform for malware defense. With seamless integration and deep insights into cloud security, it empowers organizations to identify and mitigate threats effectively. By relating security findings and vulnerabilities, CloudDefense.AI provides enhanced security insights, ensuring a secure digital environment.
Book a free demo now to experience the future of cloud security!







