Kubernetes is the backbone of modern cloud-native applications, but its flexibility also makes it a frequent target for cyberattacks. To protect your workloads and maintain compliance, implementing strong security practices in your Kubernetes environment is essential.
Here’s a comprehensive guide to the top Kubernetes security best practices for 2025, covering everything from access control to monitoring and threat prevention.
What is Kubernetes Security?
Kubernetes security is all about making sure your Kubernetes clusters and the apps they manage are super safe. But here’s the thing, even though Kubernetes is super popular, it’s had its fair share of security issues.
Why? Well, mainly because not everyone’s on the same page about security, and there’s a bit of a skill and process gap.
In short, here’s what Kubernetes security aims to do:
- Protect cluster access: Controls access to Kubernetes clusters, limiting who can view, modify, or manage resources.
- Keep secrets safe: From passwords to API keys, sensitive data gets encrypted and protected from prying eyes.
- Block unapproved code: Only authorized workloads can run in your cluster, stopping harmful code in its tracks.
- Watch over your apps in real-time: Constantly monitors active applications to spot and respond to security issues as they happen.
- Ensure compliance: Meets industry standards to keep your organization in the clear on security requirements.
- Act fast against threats: Sets up automated alerts to detect threats quickly, helping you contain issues before they spread.
Hence, the primary objective of Kubernetes security is to tackle these risks by enforcing access controls, network policies, secure image management, and monitoring. These measures ensure the integrity, confidentiality, and availability of your containerized applications while also safeguarding sensitive data from potential threats.
| Read More: Curious about Kubernetes basics? Check out our in-depth guide on Kubernetes and why it’s essential for modern app management. |
Why is Kubernetes Security Important?
Kubernetes security is crucial because your cluster environment is always moving and evolving. As apps move through different phases of application lifecycle—like build, deploy, and runtime—each phase needs its own approach to stay secure and reliable.
Here’s why each stage matters for Kubernetes security:
- In the Build phase: Instead of patching containers like traditional systems, Kubernetes replaces them with new, updated images. This means you have strong version control, and if there’s a problem with the new code, rolling back is quick and easy.
- In the Deploy phase: Security checks ensure that only trusted code and configurations make it into the cluster. Screening images and settings here stops vulnerabilities from reaching your live environment.
- In the Runtime phase: The runtime environment is constantly altering, with pods starting and stopping and API connections adjusting. For IT teams, this can be tricky because you’re protecting a moving target.
With all this constant change, Kubernetes security makes sure your applications and data stay safe, adapting to keep up with the fast-paced cluster environment.
What are the Kubernetes Security Challenges?
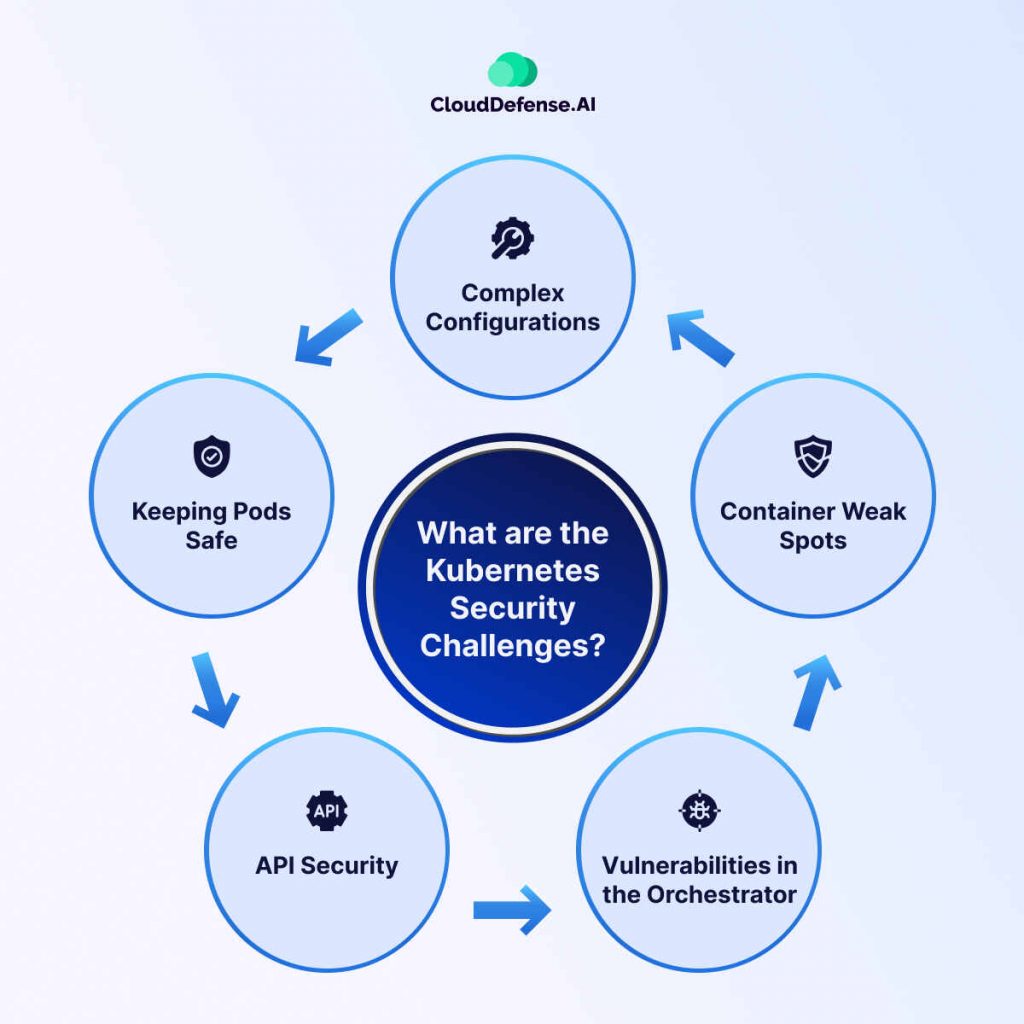
Kubernetes offers powerful flexibility, but it also comes with unique security challenges. These are some of the most common Kubernetes security issues to watch out for:
- Complex Configurations: Kubernetes gives you many options to set up network policies, role-based access control (RBAC), and more. But with so many choices, it’s easy to misconfigure something—like leaving ports open or granting excessive permissions, which can lead to security vulnerabilities.
- Container Vulnerabilities: Containers can have their own security risks. If a vulnerability inside a container is exploited, attackers could escalate privileges, access sensitive data, or cause denial-of-service attacks.
- Kubernetes Orchestrator Risks: The Kubernetes platform itself can have vulnerabilities, and a skilled attacker can exploit these weak points to gain control over your entire cluster.
- API Security Issues: Kubernetes relies on APIs for cluster management. Without proper API security, you risk unauthorized access, data leaks, or even full control of the cluster falling into the wrong hands.
- Pod Security Concerns: Pods are temporary and constantly changing, making them challenging to secure. If a pod is breached, an attacker could move laterally through the cluster. Setting up strict network policies and runtime protections is essential to keep pods safe.
Top 10 Kubernetes Security Best Practices
1. Resource Segregation
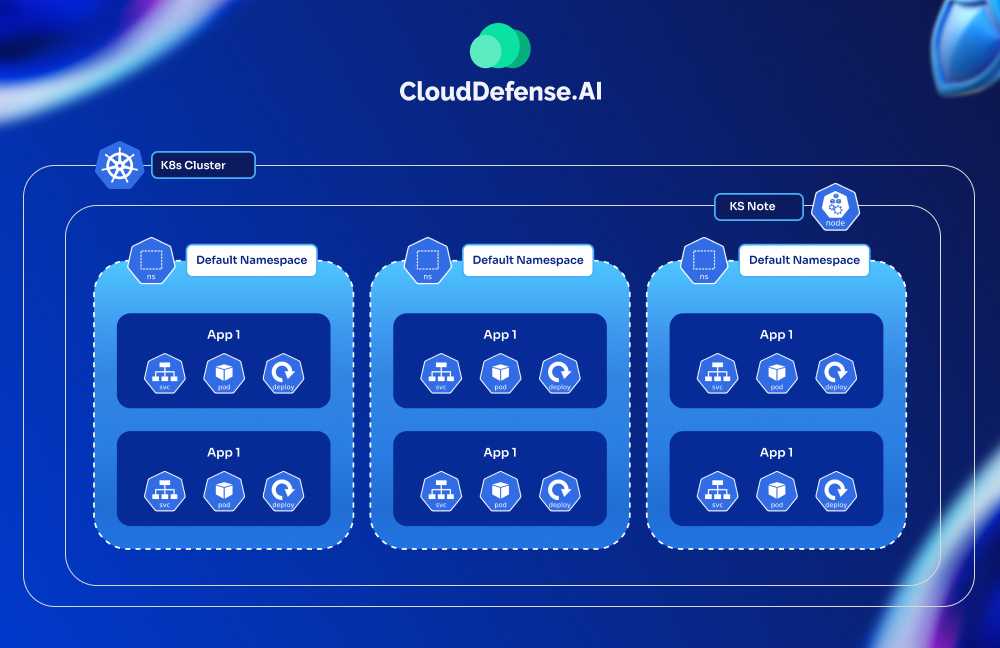
Ask yourself: Are your critical and non-critical workloads sharing the same nodes or namespaces? If yes, it’s time to rethink your segregation strategy to tighten security.
So, how do you ensure that a small glitch in one container doesn’t disrupt your entire Kubernetes cluster? This is where resource segregation comes into play—it’s all about isolating workloads to limit the blast radius of potential security incidents.
When using Kubernetes, it’s critical to segregate resources by:
- Namespaces: Segment different teams, environments (like dev, staging, and production), or applications into separate namespaces to manage access and policies independently.
- Node Pools: Assign workloads to specific node pools based on their sensitivity or resource requirements. For example, public-facing pods can run on isolated nodes to minimize exposure risks.
- Network Policies: Use Kubernetes Network Policies to restrict traffic flow between pods and services. For example, only allow database pods to receive traffic from specific application pods.
This way, if a container or node is compromised, the impact is confined to a small part of the infrastructure. You’re not just avoiding downtime—you’re ensuring that attackers don’t have unrestricted access to everything in your cluster.
2. Role-Based Access Control
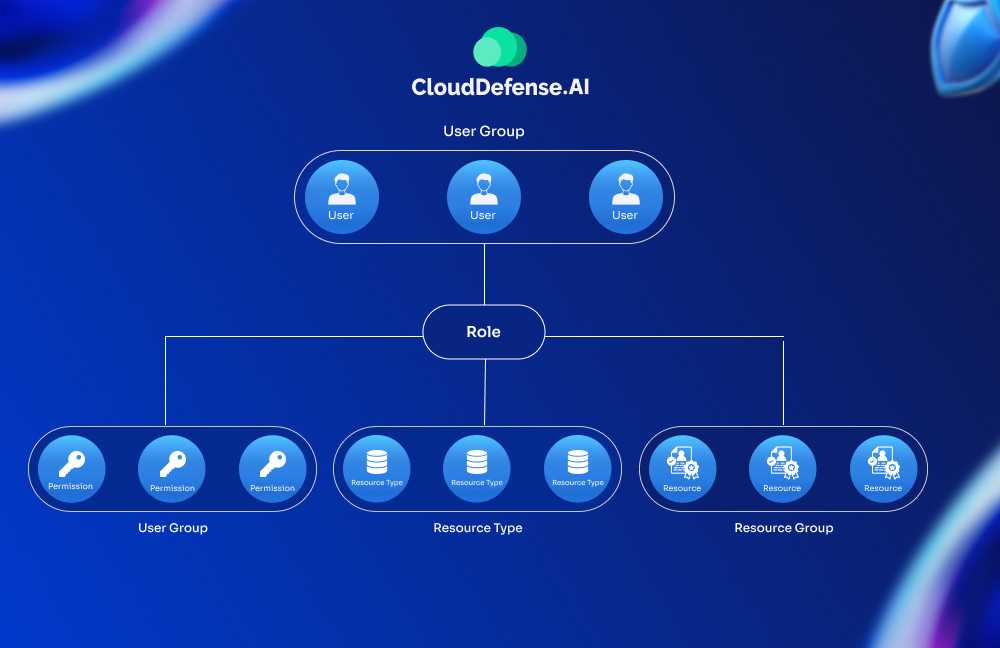
Do all users and services in your Kubernetes cluster need full access to the API? Probably not. This is why you should implement RBAC (Role-Based Access Control)—it lets you define precisely who can do what, ensuring only the right people or services have the right permissions.
Here’s how to implement RBAC effectively:
- Disable ABAC: Make sure the older Attribute-Based Access Control (ABAC) is off to avoid any potential security conflicts.
- Granular Permissions: Set roles and permissions at the namespace level instead of cluster-wide, unless absolutely necessary. This limits exposure if an account or process is compromised.
- Principle of Least Privilege: Avoid granting cluster-admin rights indiscriminately, even when troubleshooting. Stick to minimal permissions for specific tasks. For example, instead of giving blanket admin rights for debugging, create a role that only allows logs access and pod restarts.
- Audit and Rotate Credentials: Regularly review who has access to what and rotate service accounts and tokens to keep things secure.
Are your RBAC policies in line with your team’s workflow and security needs? If not, a regular audit will help catch roles with more privileges than necessary, reducing the chances of a breach.
3. API Security
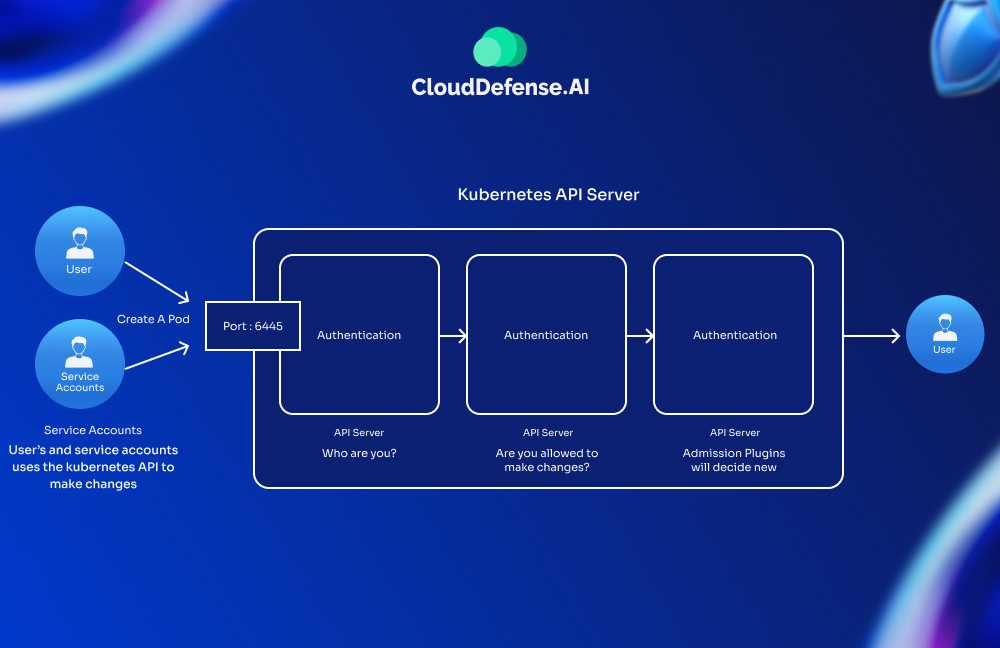
The API server is the gateway to your Kubernetes cluster—if it’s compromised, the entire environment is at risk. So how can you secure it effectively?
Let’s walk through the essential steps:
- Authentication with Certificates: Use TLS certificates to verify the identity of anyone or any component interacting with the API. These certificates ensure that only trusted entities—like authorized admins or system components—get access.
- Authorization Controls: Pair authentication with RBAC policies to define what each user or service can do. It’s not just about who gets in, but what they’re allowed to do once they’re in.
- IP Whitelisting: Restrict access to your API server by allowing requests only from trusted IP addresses. Implementing network policies lets you control what traffic can reach your API endpoints. For example, only your CI/CD systems or internal networks should have API access.
- Audit Logs: Enable API server auditing to track all interactions and detect unusual behavior. Auditing helps you spot unauthorized access attempts or misconfigurations before they escalate.
4. Implement Effective Logging Practices
Logs are most helpful when troubleshooting issues or investigating security incidents. They provide a transparent view of everything happening behind the scenes, helping you track actions, events, and errors in your Kubernetes environment.
Why are logs essential? In the event of a security breach, logs enable you to pinpoint exactly what the attacker did, how they got in, and what needs to be blocked or fixed to prevent future incidents. But to leverage logs effectively, you need to know where and how to find them.
Accessing API Server Logs and Events
- Local Path: Typically, API server logs are located at /var/log/kube-apiserver.log, though this may vary based on your cloud provider.
- AWS: Use CloudTrail to access Kubernetes API logs.
- GKE: Access API logs from the Google Cloud Console under the “Kubernetes Engine” section.
Accessing Node Logs and Events
- Local Logs: Node logs, including kubelet logs, are usually stored in /var/log/. You can view them directly by SSHing into the node and running:
| tail -f /var/log/kubelet.log |
- API Access: From Kubernetes 1.27 onward, you can query node logs using APIs. Example:
| kubectl get –raw “/api/v1/nodes/node-1.example/proxy/logs/?query=kubelet” |
- Accessing Pod Logs and Events: Pod logs are easily accessible with kubectl commands, which help monitor containers in real time:
| kubectl logs -f pod_name -n namespace_name |
Need to troubleshoot? Use the -f flag to follow live logs and keep track of the latest events.
Therefore, by integrating logs from different sources—API server, nodes, and pods—you create a comprehensive view of your cluster’s operations. Regularly reviewing these logs not only helps resolve issues faster but also strengthens your security by catching suspicious activities early.
5. Image Security
Are all your images scanned and verified before deployment? If not, it’s time to tighten up your image security and protect your cluster from unnecessary risks. Also, when it comes to securing your Kubernetes cluster, container image security should be your top priority.
Containers are only as secure as the images they’re built from—any vulnerability in those images could compromise your entire system. Here’s how to stay ahead:
- Use Image Scanning Tools: Integrate container image scanning into your CI/CD pipeline to detect vulnerabilities early. Tools like Trivy, Clair, or Aqua Security can identify known vulnerabilities in images, ensuring only secure images make it to production.
- Restrict Image Sources: Stick to trusted registries like Docker Hub’s verified publishers or your own private registry. Avoid downloading images from unknown sources, as they might contain malicious code. For example, public images that aren’t frequently maintained may carry hidden risks.
- Use Signed Images: Consider using signed images to verify their authenticity. This ensures the image hasn’t been tampered with in transit or pulled from an untrusted source.
- Keep Base Images Updated: Regularly update your base images to avoid relying on outdated components with known vulnerabilities. Automate this process to ensure continuous security improvements.
6. Implement CIS Benchmarks
Kubernetes security is essential for preventing vulnerabilities and leaks, and one of the best ways to achieve this is by following CIS (Center for Internet Security) Benchmarks. These benchmarks provide a set of best practices for securing your cluster and aligning it with industry standards like PCI DSS, HIPAA, and NIST.
Here’s how applying CIS benchmarks helps secure your environment:
- Network Hardening: Recommendations include restricting network access, applying strict firewall rules, and isolating workloads to minimize attack surfaces.
- Access Control: CIS guidelines enforce best practices for authentication and authorization, such as using RBAC (Role-Based Access Control) and multi-factor authentication (MFA) for API access.
- Configuration Management: Ensure secure configurations of Kubernetes components like the API server, etcd, and kubelet. This includes disabling anonymous access and setting strict policies for node configurations.
Most of these controls are applied at the node or agent level to ensure the cluster runs securely at its core. Some tools, like Kube-bench, can automate the process of checking your cluster against CIS benchmarks and reporting compliance gaps.
Following CIS benchmarks not only hardens your cluster but also helps in meeting regulatory requirements. Are you running regular scans and audits to ensure your Kubernetes environment stays aligned with these standards?
7. Facilitate Audit Logging
Are your audit logs turned on and actively monitored? If not, now’s the time to make it happen. The main reason is that, when you set up a Kubernetes cluster, there’s a high chance that audit logging isn’t turned on by default.
You’ll want to make sure it is because audit logs are crucial for tracking what’s happening inside your cluster. And, if possible, send all logs to a central location—it makes life much easier when you need to analyze or correlate events.
Why does this matter? Because, audit logs give you a clear trail of every action—who did what, when, and where. If something goes wrong or there’s a security issue, these logs are your first line of defense. They can tell you if an unauthorized change was made, helping you pinpoint and fix vulnerabilities before they spiral out of control.
Here are a few tips to make the most of audit logging:
- Centralize Logs: Use tools like ELK (Elasticsearch, Logstash, Kibana) or Grafana Loki to gather logs from multiple sources in one place. This way, you get a complete picture of what’s happening across your cluster.
- Set Up Alerts: Configure alerts for unusual activity—like unexpected API calls or unauthorized access attempts—so you can respond quickly.
- Review Logs Regularly: Don’t just collect logs; make it a habit to review them. Even minor anomalies can indicate bigger issues brewing under the surface.
8. Minimization of the Attack Surface
When it comes to securing your Kubernetes cluster, the fewer things that can go wrong, the better. That is where the notion of minimizing the attack surface comes into play. One of the easiest ways to do this is by using lean base container images—only including the bare minimum your app needs to run. The idea is simple: less software = fewer vulnerabilities.
Here are a few practical ways to reduce bloat and boost security:
- Build Minimal Images from Scratch: Use Docker’s FROM scratch directive to create a super-lightweight container image with only the components you need. This way, you have complete control over what goes into your container—nothing extra that attackers could exploit.
- Use Slim or Distroless Images: If you can’t build from scratch, start with a distroless image (like Google’s distroless base) or something lightweight like Alpine Linux. These minimal images strip out unnecessary tools and libraries that traditional Linux distributions include.
- Audit Your Dependencies: Even with slim images, only add the packages your app absolutely needs. Every extra dependency is a potential vulnerability waiting to be discovered.
Keeping your base images as small as possible not only makes your containers more secure but also speeds up deployments and reduces resource consumption. So, next time you build a container, ask yourself: Does it really require all that stuff? If not, strip it down and keep things clean.
9. Secret Management
One of the most common (and dangerous) mistakes when working with Kubernetes is mismanaging secrets—things like API keys, passwords, or database credentials. If these sensitive pieces of information aren’t handled correctly, they can easily fall into the wrong hands.
Here’s how you can manage secrets the right way:
- Use Kubernetes Secrets API: Instead of hardcoding secrets into environment variables or configuration files, store them using Kubernetes Secrets. This API securely holds sensitive data and ensures it isn’t exposed during deployments.
- Encrypt Secrets at Rest: By default, Kubernetes stores secrets as plain base64-encoded data, which isn’t very secure. Make sure encryption at rest is enabled to protect your secrets within the cluster’s etcd storage.
- Control Access with RBAC: Limit who or what can access your secrets by setting RBAC policies. Only the necessary pods or services should have access to specific secrets—no more, no less.
- External Secret Management Tools: Consider integrating with HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault for more advanced secret management. These tools offer better security, rotation policies, and centralized control.
- Rotate Secrets Regularly: Don’t let secrets become stale. Rotate them periodically to reduce the impact if they are compromised. Automating this process can make it easier to keep everything up to date without disrupting services.
10. Leverage Kubernetes Security Posture Management (KSPM) Solutions
Managing security in Kubernetes can feel like juggling a lot of moving parts. That’s where Kubernetes Security Posture Management (KSPM) steps in. Think of KSPM as your security checklist and auditor—it helps you keep track of misconfigurations, compliance gaps, and vulnerabilities across your cluster.
Here’s how KSPM can make your life easier:
- Continuous Monitoring: KSPM tools keep an eye on your Kubernetes environment 24/7, scanning for security issues like open ports, weak access controls, or unpatched components.
- Policy Enforcement: You can define security policies (like ensuring network policies are applied or containers don’t run as root), and KSPM makes sure these rules are consistently followed across all deployments.
- Compliance Reporting: If you need to meet industry standards like PCI DSS, HIPAA, or SOC 2, KSPM can generate detailed reports, showing exactly where you stand and what needs fixing.
- Misconfiguration Alerts: Simple mistakes—like exposing a sensitive service to the internet—can slip through the cracks. KSPM tools catch these issues early and notify you before they turn into bigger problems.
All these features come with Clouddefense.AI’s KSPM solution that tools help you automate security tasks, saving time and reducing the chances of human error. With KSPM, you get a continuous pulse on your cluster’s health, giving you the confidence that everything is secure and compliant.
Conclusion
Securing a Kubernetes cluster is a continuous process that requires attention to every detail—from resource segregation to secret management. Following these Kubernetes security best practices helps you minimize risks, control access, and maintain a secure environment. If you’re serious about locking down your Kubernetes environment, CloudDefense.AI’s KSPM has you covered by offering continuous monitoring, policy enforcement, and actionable risk insights. Book a free demo today and see how it simplifies Kubernetes security for your team!







