Falco is a renowned open-source project designed specifically for threat detection on Linux systems. Developed primarily in C and C++, Falco utilizes a combination of kernel modules, eBPF (extended Berkeley Packet Filter), and the newly developed Modern BPF driver to capture a wide range of system events, including syscalls, file and directory operations, and more.
By applying static rules that we create, Falco promptly notifies us of any detected malicious events. Furthermore, Falco can integrate seamlessly with various sources like Kubernetes (K8s), AWS CloudTrail, and OKTA through dedicated plugins, enabling it to capture events from diverse platforms.
For enhanced threat detection, we have the flexibility to write additional rules tailored to specific attack scenarios and even develop new plugins to expand the number of event sources.
What we did using falco:
To gain insight into Falco’s functionality and its ability to detect various attacks, we conducted a Proof of Concept exercise. We wrote attack scripts and emulated them on a Linux system equipped with Falco.
This practical exploration provided us with a comprehensive understanding of Falco’s capabilities and its scope of coverage. However, it became evident that Falco needs to be enhanced in detecting well-known MITRE ATT&CK®.
Despite its effectiveness in certain areas, further analysis revealed potential limitations in this specific domain.
To address this concern, we took proactive steps by carefully selecting the 20 significant MITRE ATT&CKs. We then proceeded to develop attack scripts to simulate these attacks and thoroughly study their impact on the system.
By closely monitoring the system events generated during these attacks, we were able to craft specific rules that successfully captured these MITRE attacks. This approach significantly enhanced Falco’s threat detection capabilities beyond its standard features. Through our efforts, we successfully scaled up Falco’s effectiveness in detecting and mitigating these targeted attacks.
When crafting the rules, we carefully considered several key factors. These included:
- Analyzing the system calls triggered during the execution of specific attacks
- Identifying the process names associated with each attack
- Examining file and directory modifications
- Monitoring network activities, and observing memory read/writes and disk accesses.
These critical elements provided valuable insights that enabled us to develop comprehensive and effective rules for detecting and mitigating the identified attacks.
This approach allows individuals to adopt an attacker’s mindset and explore potential vulnerabilities within a system. By thoroughly analyzing the various possibilities in which threats can emerge, one can develop a proactive approach to safeguarding their systems.
This entails crafting specific rules that target and detect particular threats, enabling effective mitigation measures to be implemented.
Through this process, a proactive and security-focused perspective is fostered, resulting in enhanced system protection.
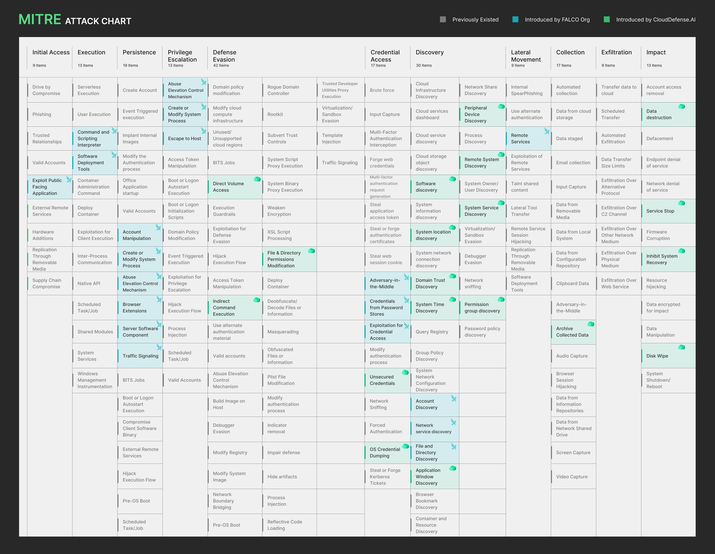
MITRE ATT&CK Rules Covered By Falco:
| # | Mitre Attack Technique | Attack Technique |
|---|---|---|
| 1 | Mitre Execution | Command and Scripting Interpreter |
| 2 | Mitre Execution | Software Deployment Tools |
| 3 | Mitre Persistence | Account Manipulation |
| 4 | Mitre Persistence | Create or Modify System Process |
| 5 | Mitre Persistence | Abuse Elevation Control Mechanism |
| 6 | Mitre Persistence | Browser Extension |
| 7 | Mitre Persistence | Server Software Component |
| 8 | Mitre Persistence | Traffic Signaling |
| 9 | Mitre Privilege Escalation | Abuse Elevation Control Mechanism |
| 10 | Mitre Privilege Escalation | Escape to Host |
| 11 | Mitre Credential Access | Adversary in the Middle |
| 12 | Mitre Credential Access | Credentials from Password Stores |
| 13 | Mitre Credential Access | Exploitation for Credential Access |
| 14 | Mitre Discovery | Account Discovery |
| 15 | Mitre Discovery | Network Service Discovery |
| 16 | Mitre Discovery | File and Directory Discovery |
| 17 | Mitre Lateral Movement | Remote Services |
MITRE ATT&CK Rules Covered By CloudDefense.AI:
Check our open source project here.
| # | MITRE ATT&CK | ATT&CK Technique | Rule Name |
|---|---|---|---|
| 1 | Mitre Impact | Disk Wipe | Suspicious Disk Activity |
| 2 | Mitre Impact | Inhibit System Recovery | Disable Recovery Features |
| 3 | Mitre Impact | Data Destruction for Impact | Detect Data Destruction Activity |
| 4 | Mitre Persistence | Account Manipulation | Account Manipulation in SSH |
| 5 | Mitre Discovery | Remote System Discovery | Suspicious Network Scanning Command |
| 6 | Mitre Discovery | Permission Groups Discovery | Permission and Group Members Discovery |
| 7 | Mitre Discovery | Peripheral Device Discovery | Detect Peripheral Device Enumeration Commands |
| 8 | Mitre Discovery | System Time Discovery | Suspicious Time and Date Command Execution |
| 9 | Mitre Discovery | Domain Trust Discovery | Enumerate Domain Trusts |
| 10 | Mitre Discovery | System Location Discovery | Detect System Location Information Retrieval |
| 11 | Mitre Discovery | Application Window Discovery | Get Information About Open Application Windows |
| 12 | Mitre Discovery | Software Discovery | Suspicious System Information Gathering |
| 13 | Mitre Credential Access | OS credential Dumping | Read Maps File of Process |
| 14 | Mitre Credential Access | Unsecured Credential Access | Attempt to Access Bash History File |
| 15 | Mitre Defense Evasion | File and Directory Permission Modification | Chown or Chmod Operation |
| 16 | Mitre Defense Evasion | Indirect Command Execution | Execute Command Via Utility |
| 17 | Mitre Defense Evasion | Direct Volume Access | Read Disk Block Command |
| 18 | Mitre Collection | Archive Collected Data | Archive and Compression Activity |
| 19 | Mitre Impact | Service Stop | Detect Service Disable Using Systemctl |
| 20 | Mitre Discovery | System Service Discovery | System Service Discovery |
The 20 rules that we have written for Falco cover various aspects of detection and monitoring in a system. Here’s an overview of their use, impact, and rationale:
1. Disk Wipe (Mitre Impact):
This rule detects attempts to perform disk wiping, which can result in the complete destruction of data, making it unrecoverable. Its purpose is to identify malicious actions aimed at data destruction or covering tracks.
2. Inhibit System Recovery (Mitre Impact):
This rule detects actions that hinder or disable system recovery mechanisms, making it difficult for administrators to restore the system to a functional state. Attackers may employ this technique to impede recovery efforts and prolong their presence.
3. Data Destruction for Impact (Mitre Impact):
This rule identifies activities that intentionally destroy or manipulate data to cause disruption or damage. It helps detect actions aimed at data destruction for malicious purposes.
4. Account Manipulation (Mitre Discovery):
This rule detects unauthorized actions related to user accounts, such as the creation, deletion, or modification of user accounts. It helps identify potential misuse or compromise of user credentials.
5. Remote System Discovery (Mitre Discovery):
This rule detects attempts to discover or gather information about remote systems or network resources. Attackers may use this information to plan further actions or identify potential targets.
6. Permission Groups Discovery (Mitre Discovery):
This rule identifies activities related to the discovery of permission groups or security roles within a system. It helps in understanding the adversary’s understanding of the system’s security structure.
7. Peripheral Device Discovery (Mitre Discovery):
This rule detects actions related to the discovery or enumeration of peripheral devices connected to the system. It helps in understanding the adversary’s reconnaissance activities or potential device-based attacks.
8. System Time Discovery (Mitre Discovery):
This rule identifies attempts to gather information about the system’s time settings or synchronization. Attackers may exploit time-related vulnerabilities or use accurate timestamps for their operations.
9. Domain Trust Discovery (Mitre Discovery):
This rule detects actions aimed at discovering or exploring the trust relationships between domains within a network. It helps identify potential lateral movement or privilege escalation attempts.
10. System Location Discovery (Mitre Discovery):
This rule detects activities related to determining the physical or network location of the compromised system. Attackers may use this information to plan further attacks or target specific geographical areas.
11. Application Window Discovery (Mitre Discovery):
This rule identifies actions aimed at discovering or enumerating open application windows on the system. It helps in understanding the adversary’s reconnaissance activities or potential window-based attacks.
12. Software Discovery (Mitre Discovery):
This rule detects activities related to the discovery or enumeration of installed software or applications on the system. It helps identify unauthorized or potentially malicious software.
13. OS Credential Dumping (Mitre Credential Access):
This rule detects attempts to extract or obtain operating system credentials or authentication tokens. Attackers may use this information to escalate privileges or gain unauthorized access.
14. Unsecured Credential Access (Mitre Credential Access):
This rule identifies actions aimed at accessing or extracting unsecured or weakly protected credentials, such as plaintext passwords. It helps identify potential credential-based attacks or weak security practices.
15. File and Directory Permission Modification (Mitre Defense Evasion):
This rule detects modifications to file or directory permissions, which may indicate attempts to evade detection or gain unauthorized access to sensitive resources.
16. Indirect Command Execution (Mitre Defense Evasion):
This rule identifies the use of techniques that obfuscate or indirectly execute commands, making it harder to detect malicious activities. Attackers may employ this method to bypass security controls.
17. Direct Volume Access (Mitre Defense Evasion):
This rule detects actions related to direct access or manipulation of storage volumes or raw disk sectors. It helps identify potential data exfiltration or persistence techniques.
18.Archive Collected Data (Mitre Collection):
This rule identifies attempts to compress or archive collected data, which may indicate exfiltration or preparation for later exfiltration. It helps detect potential data theft or concealment.
19. System Service Discovery (Mitre Discovery):
This rule detects activities related to the discovery or enumeration of system services running on the system. It helps in understanding the adversary’s reconnaissance activities or potential service-based attacks.
20. Service Stop (Mitre Impact):
This rule identifies attempts to stop or disable critical system services. It helps in identifying actions aimed at disrupting system functionality or facilitating further compromise.
These rules collectively enhance the security posture of the system by detecting various suspicious activities, potential attacks, or indicators of compromise. By monitoring and analyzing events based on these rules, organizations can proactively identify and respond to security incidents, minimize the impact of attacks, and protect their systems and data.
Conclusion:
In conclusion, Falco is a powerful open-source host runtime threat detection project designed specifically for Linux systems. It uses kernel module, eBPF and Modern BPF driver to capture system events, and notify users about any malicious activities based on predefined static rules. While Falco’s basic version is capable of detecting various threats, our team conducted POCs and found that it had limitations in detecting the famous MITRE attacks.
To address this issue, we wrote rules to capture these attacks and successfully generated events for each of them. By analyzing system events produced by these attacks, we were able to scale up Falco’s threat detection capabilities beyond its basic version. This approach can be adopted by anyone to analyze system vulnerabilities, think like an attacker, and write rules to safeguard their systems from potential threats.
Credits:
1) The Falco Maintainers
2) www.falco.org







