Proactively securing networks and systems from cyber threats is like playing an intense game of digital cat-and-mouse. On one side, you’ve got the hackers constantly prowling, looking for vulnerabilities to exploit.
On the other, you need robust security measures to stay one step ahead. Two critical players in this high-stakes game are Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). But what exactly differentiates these systems, and which one is right for your needs?
Keep reading as this article explores the functionalities, response mechanisms, and advantages of both IDS and IPS, empowering you to make an informed decision for your network’s security posture.
What is an Intrusion Detection System (IDS)
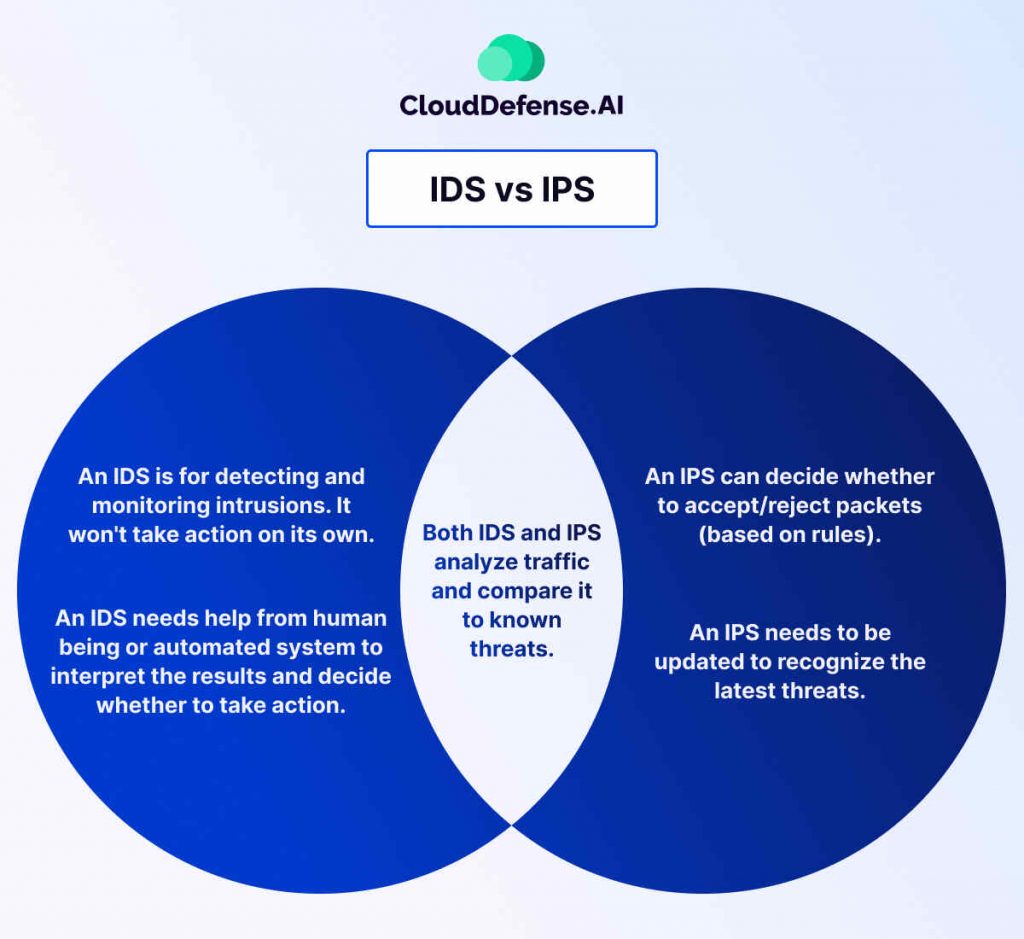
An Intrusion Detection System (IDS) acts as a vigilant security guard for your network. An ideal IDS doesn’t just mindlessly monitor traffic. Nah, it’s way smarter than that. It analyzes data packets, logs, and system activities, using predefined rules or intelligent algorithms to identify patterns that could indicate a potential threat.
There are a couple of different types when it comes to IDS:
Signature-based: This approach resembles checking passports at a border. The IDS maintains a database of digital fingerprints, or signatures, of known malicious activities and malware. It meticulously compares incoming network traffic against these signatures. If a match is found, it raises a red flag, indicating a potential threat.
Anomaly-based: Anomaly-based detection functions in a way that it precisely establishes a baseline of what constitutes “normal” activity on your network. Any significant deviations from this norm, such as a sudden surge in traffic or unauthorized access attempts, trigger an alert.
Deployment Modes of IDS:
IDS can be deployed in two main configurations, offering strategic advantages depending on your needs:
Network-based IDS (NIDS): NIDS acts as a digital traffic cop, stationed at a strategic point within your network. It examines all incoming and outgoing traffic, scanning data packets for suspicious activity or patterns that might indicate an attack.
Host-based IDS (HIDS): HIDS functions as a local vigilant, residing directly on individual devices like servers or workstations. It monitors system activity, file changes, and log files for signs of intrusion attempts or malware execution.
By leveraging these detection methods and deployment modes, an IDS offers several advantages:
- 24/7 Monitoring – The IDS never sleeps, constantly surveilling
- Early Threat Detection – Identifies incidents before major damage occurs
- Comprehensive Logging – Provides valuable forensic data for analysis
- Notification Alerts – Immediately notifies admins of potential breaches
- Compliance Support – Helps meet regulatory requirements
What is an Intrusion Prevention System (IPS)
In the previous section, we have seen that IDS provides invaluable insight into potential threats, but what if you could actively prevent those threats from infiltrating your network in the first place? That’s where Intrusion Prevention Systems (IPS) come in. IPS functions as the network’s bouncer, rigorously screening traffic and taking immediate action to block anything suspicious.
Unlike IDS, which focuses solely on detection and alerting, IPS integrates seamlessly with your network infrastructure. It acts as an in-line device, positioned directly in the flow of network traffic. This strategic placement allows the IPS to examine every data packet in real-time, scrutinizing it for malicious activity based on predefined security policies and known attack signatures.
Here’s how IPS achieves its proactive defense:
Signature-based Detection: Similar to IDS, IPS maintains a database of malicious activity signatures. However, instead of simply raising an alert, IPS actively blocks traffic that matches these signatures. This prevents malware, exploits, and other known threats from reaching your network.
Anomaly-based Detection: Building upon the anomaly detection capabilities of IDS, IPS can also analyze traffic patterns and identify deviations from established baselines. If the IPS detects suspicious activity that doesn’t necessarily match a known signature, it can take pre-configured actions such as blocking the traffic, resetting the connection, or sending an alert for further investigation.
Deployment Modes of IPS:
Similar to IDS, IPS can be deployed in various configurations to cater to diverse network security needs:
Inline Mode: This is the most common deployment mode for IPS. The IPS device is inserted directly into the data path of your network, typically between a switch and a firewall. This placement allows the IPS to examine all incoming and outgoing traffic and take immediate action against threats.
Passive Mode: In passive mode, the IPS functions as a monitoring device, positioned on a separate network segment. It monitors traffic using a network tap or SPAN (Switch Port Analyzer) port, analyzing data packets for suspicious activity without directly interfering with network traffic flow. While it cannot directly block threats in passive mode, it can still generate alerts and provide valuable insights into potential security risks.
Response Mechanisms of IPS:
When encountering suspicious activity, IPS can take various actions depending on the severity of the threat and the pre-defined security policies:
Blocking Traffic: This is the most common response. The IPS intercepts and discards malicious data packets, effectively stopping the attack in its tracks.
Resetting Connections: In some cases, the IPS might choose to reset the connection between the source and destination, disrupting the attacker’s attempt and allowing legitimate traffic to resume.
Generating Alerts: Even with its blocking capabilities, IPS can still generate alerts for security personnel to investigate potential threats that require further analysis.
Employing these detection methods, response mechanisms, and deployment modes, IPS offers significant advantages:
Enhanced Network Security: The ability to actively block threats in real-time drastically reduces the risk of successful attacks and data breaches.
Reduced Response Time: IPS eliminates the need for manual intervention by security personnel, automatically taking action against identified threats.
Improved Efficiency: By blocking malicious traffic at the network level, IPS relieves the burden on other security solutions, allowing them to function more efficiently.
Yet, it’s important to understand that IPS also has limitations. Overly aggressive IPS configurations can lead to false positives, blocking legitimate traffic. Additionally, similar to IDS, signature-based detection in IPS can be vulnerable to zero-day attacks.
IDS and IPS: A Teamwork Approach
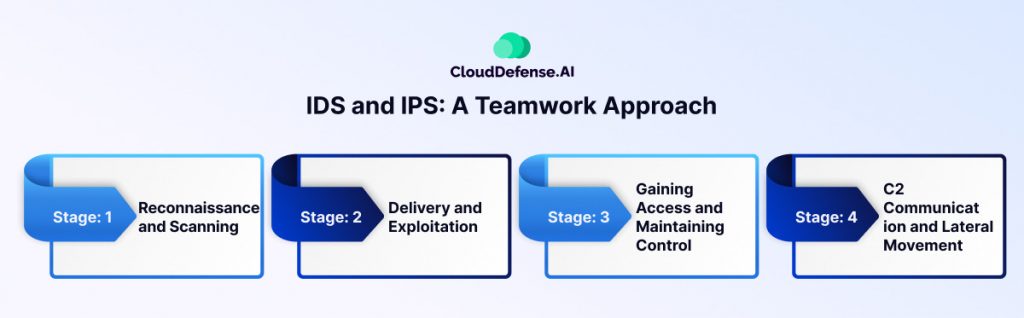
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are fundamental tools in the fight against cyberattacks. While they differ in their approach, their combined functionality creates a robust defense against ever-evolving threats. Here’s how they work together in an attack scenario:
Stage 1: Reconnaissance and Scanning
An attacker initiates a reconnaissance phase, probing your network for vulnerabilities. The IDS meticulously analyzes this traffic, searching for patterns that deviate from established baselines. For instance, a sudden surge in port scans or unusual traffic patterns could trigger an alert.
Stage 2: Delivery and Exploitation
The attacker attempts to deliver malware or exploit vulnerabilities. The IDS continues to monitor traffic, identifying suspicious data packets containing known malware signatures or exploit attempts. It raises an alert, notifying security personnel of the potential threat.
Stage 3: Gaining Access and Maintaining Control
If the attacker bypasses initial defenses, they might try to establish persistent access or escalate privileges. The IDS remains vigilant, detecting anomalous activity such as unauthorized access attempts or suspicious file modifications. It continues to generate alerts, providing valuable information for security personnel to investigate.
Stage 4: C2 Communication and Lateral Movement
The attacker might establish communication channels with compromised systems (Command and Control) or attempt to move laterally across the network to other devices. The IDS monitors network traffic for signs of unauthorized communication or unusual network activity between devices. This can help identify compromised systems and prevent lateral movement.
Where IPS Takes Action:
While IDS excels at detection and alerting, IPS functions as a proactive shield. It leverages the same detection methods as IDS but can take immediate action to block threats. Here’s how:
Signature-based Blocking: If the IPS identifies traffic matching a known malware signature, it can block the malicious data packets, preventing them from reaching your systems.
Anomaly-based Blocking: When the IPS detects suspicious activity that deviates from established baselines, it can block the traffic as a precautionary measure, giving security personnel time to investigate.
These combined efforts of IDS and IPS offer significant advantages:
Multi-layered Defense: They provide a layered security approach, offering early detection through IDS and real-time prevention through IPS.
Faster Response Times: IDS alerts allow for quicker response and mitigation of threats.
Reduced Risk of Breaches: IPS actively blocks attacks, significantly reducing the risk of successful intrusions.
IDS vs IPS: Key Difference
| Parameter | Intrusion Detection System (IDS) | Intrusion Prevention System (IPS) |
| Primary Function | Detection and Alerting | Prevention and Blocking |
| Response Mechanism | Generates alerts for security personnel | Actively blocks or disrupts suspicious traffic |
| Focus | Identifying potential threats | Preventing threats from reaching your network |
| Impact on Network Performance | Lower impact, as it only monitors traffic | Potentially higher impact, as it can block legitimate traffic (false positives) if not configured correctly |
| Deployment Strategy | More flexible, can be deployed in network-based or host-based configurations | Often deployed in-line within the network flow for faster response |
| Cost | Generally less expensive than IPS | Can be more expensive due to the complexity of real-time analysis and blocking capabilities |
| Suitability for Zero-Day Attacks | Limited effectiveness against entirely new attacks | Can still offer some protection by blocking suspicious activity, even if the specific attack signature is unknown |
| Alert Fatigue | Can generate a high volume of alerts, requiring effective filtering and prioritization | Less likely to generate alerts, but improper configuration could lead to missed threats |
Additional Considerations:
Response Time: IDS relies on manual intervention by security personnel, leading to slower response times. IPS offers faster response times by automatically blocking threats.
Security Posture: While IDS provides valuable insights, IPS offers a more proactive approach to network security.
False Positives: Both IDS and IPS can generate false positives, but misconfigurations in IPS can have a more significant impact on network performance.
Bottom Line
As discussed, intrusion detection and prevention systems offer distinct yet complementary functionalities. Understanding their strengths and differences can create a layered security strategy that effectively deters and mitigates cyberattacks.
Moving forward will require sustained effort and a long-term commitment, but the potential benefits make it well worth striving towards. Whether you choose to deploy IDS, IPS, or a combination of both, remember – a well-fortified network is a secure network.







