Organizations have a variety of options when it comes to cloud deployments, each with its own unique capabilities and security considerations. This article works as the primary guide that you will need to secure five prominent cloud environments. The cloud environments that we will be covering are:
1. Public cloud
2. Private cloud
3. Hybrid cloud
4. Multi-cloud
5. Multi-tenant cloud.
This blog will help you understand the key characteristics and security challenges associated with each type of cloud deployment. Keep reading as we explore the best practices for securing diverse cloud environments in detail.
1. Public Cloud Environments
A public cloud environment is a service provided by third-party vendors that offers scalable and cost-efficient resources to users globally. These shared infrastructures enable businesses to access virtual machines, applications, and storage over the Internet.
While providers manage infrastructure security, users share responsibility for access, application security, and data management. This shared responsibility model highlights the need for users to stay vigilant in protecting their cloud environments.
Public Cloud Security Risks
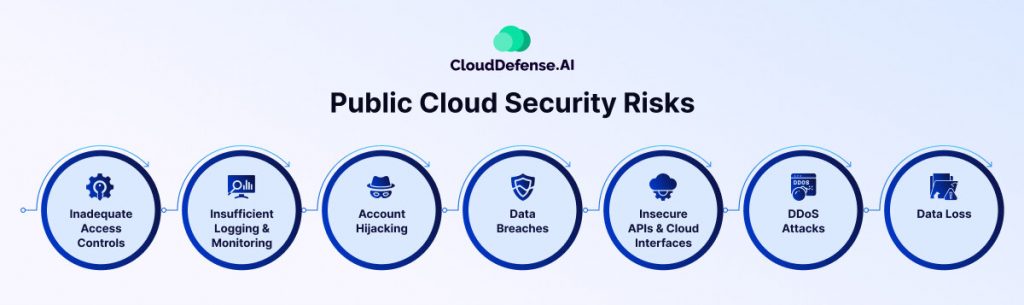
Public cloud environments come with inherent security risks. Understanding these risks and implementing effective prevention measures is crucial for maintaining data integrity and protecting sensitive information. Here’s an overview of common public cloud security risks, how they occur, and strategies to mitigate them
Inadequate Access Controls
- How they occur: Improperly configured permissions lead to unauthorized access.
- Prevention: Apply the concept of least privilege, conduct frequent access audits, and use IAM tools.
Insufficient Logging & Monitoring
- How it occurs: Lack of real-time detection due to inadequate logging and monitoring.
- Prevention: Activate cloud logging, use SIEM systems for continuous monitoring, and establish incident response protocols.
Account Hijacking
- How it occurs: Attackers gain unauthorized access using stolen credentials.
- Prevention: Requires MFA, educating users on password security, and monitoring accounts for suspicious activities.
Data Breaches
- How they occur: Unauthorized access to sensitive data due to vulnerabilities or misconfigurations.
- Prevention: Implement strong encryption, access restrictions, data categorization, secure connections, and an incident response strategy.
Insecure APIs & Cloud Interfaces
- How they occur: Vulnerable APIs and inadequately protected cloud interfaces.
- Prevention: Implement API security practices, perform regular vulnerability testing, and enforce strict access controls.
DDoS Attacks
- How they occur: Overloading cloud and network systems with malicious traffic.
- Prevention: Deploy DDoS protection services, traffic filtering, and content delivery networks (CDNs) to handle extra traffic.
Data Loss
- How it occurs: Inadvertent data deletion, corruption, or theft.
- Prevention: Regularly back up data, implement data classification and retention policies, use versioning features, employ Data Loss Prevention (DLP) tools, and educate employees on data management best practices.
How To Secure Public Cloud Environments?
Securing public cloud environments requires a well-calculated approach aimed at addressing various potential vulnerabilities. Here are some effective methods for increasing security in a public cloud setting:
- Use Strong Authentication: Implement multi-factor authentication (MFA) to enhance user login security, adding an extra layer of verification to prevent unauthorized access.
- Regular Updates and Patching: Ensure the ongoing protection of your cloud environment by regularly updating and patching software and applications to mitigate known vulnerabilities and maintain system integrity.
- Continuous Monitoring: Implement continuous monitoring mechanisms to oversee cloud resources in real time, enabling prompt detection and response to suspicious activities or security breaches.
- Security Guidelines and Procedures: Develop and enforce comprehensive security policies and procedures tailored to your organization’s cloud usage. These guidelines ensure consistency and compliance with industry standards, bolstering overall security posture.
- Data Categorization: Classify data based on its sensitivity and importance, and apply appropriate security measures accordingly. This approach ensures that data is adequately protected in accordance with its significance, minimizing the risk of unauthorized access or breaches.
- Staff Education: Educate employees on cloud security best practices and potential risks associated with cloud usage. A well-informed workforce serves as the first line of defense against security threats, empowering individuals to recognize and mitigate risks effectively.
2. Private Cloud Environments
A private cloud environment is customized to the needs of a single organization, providing unparalleled control, privacy, and security over its resources. Unlike public clouds, private clouds ensure that data, applications, and assets remain isolated within a dedicated environment, offering added assurance of protection. Similar to other cloud environments, private cloud security requires the implementation of strong security measures to protect against potential threats.
Private Cloud Security Risks
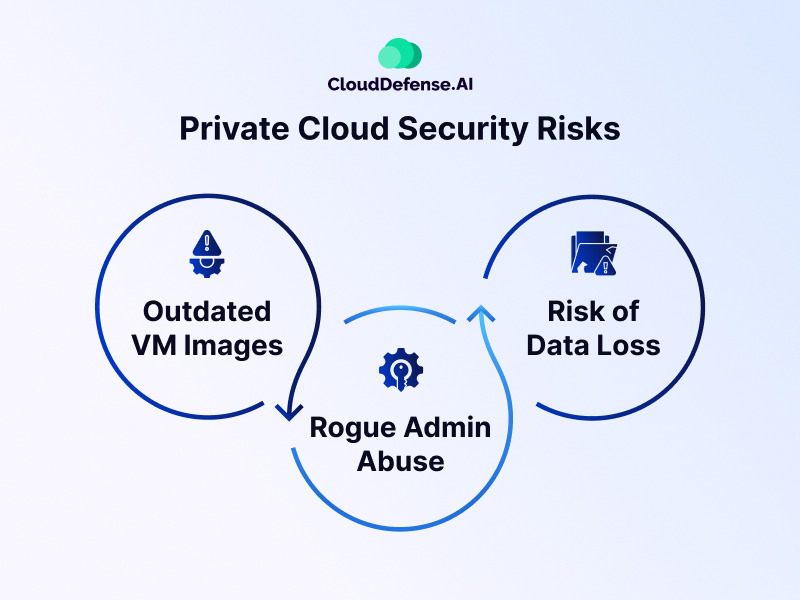
Private cloud environments offer numerous benefits but also come with inherent security risks that must be addressed to ensure data protection and integrity. Here are some key security risks associated with private cloud environments, along with preventive measures:
Outdated VM Images
- How they occur: Outdated VM images pose a significant security risk as they may contain vulnerabilities that can be exploited by attackers.
- Prevention: Admins should regularly update VM templates to include the latest patches and adhere to security best practices. They should also ensure that VM templates rigidly adhere to the organization’s security requirements.
Rogue Admin Abuse
- How they occur: Insider abuse by rogue admins within the IT department can lead to unauthorized access to sensitive tenant resources.
- Prevention: Implement role-based access control to limit the scope of administrative access and compartmentalize resources. Enable audit logging and restrict access to logs to prevent cover-up attempts. Use VM shielding to encrypt VMs and prevent unauthorized copying.
Risk of Data Loss
- How they occur: Tenant data loss without proper backups can occur if tenants assume the IT department backs up their resources.
- Prevention: Admins should ensure means for recovering tenant VMs exist by implementing cloud backup solutions that provide file sync, share, backup, and recovery management capabilities.
How To Secure Private Cloud Environments?
Securing private cloud environments requires a comprehensive approach that addresses various aspects of security. Here are some ways you can secure private cloud environments:
- Optimize Access Control and Identity Management: Implement strong IAM practices to ensure that users only access resources necessary for their roles. Enforce multi-factor authentication to enhance user verification.
- Encrypt Data: Encrypt both static and in-transit data to prevent unauthorized access. Data encryption renders information unreadable without the encryption key, providing an additional layer of security.
- Address Physical Security: Implement physical security measures such as surveillance cameras, security personnel, and fire protection to protect private cloud infrastructures from unauthorized access and hazards.
- Enhance Data Privacy and Protection: Adhere to data privacy regulations and best practices by regularly backing up data, encrypting sensitive information, and implementing zero-trust principles like least privilege.
- Use Security Tools and Technologies: Utilize consolidated security tools such as cloud detection and response, security posture management, and workload protection platforms to identify and remediate vulnerabilities effectively.
- Implement Two-Factor Authentication: Strengthen authentication mechanisms by implementing two-factor authentication, requiring users to verify their identity using two different authentication criteria or credentials.
- Ensure Comprehensive Monitoring and Logging: Continuously monitor and log security measures, risks, and remediation actions toidentify and address security threats in private cloud environments.
3. Hybrid Cloud Environments
A hybrid cloud environment combines on-premises data centers with public cloud services, allowing smooth data and application sharing. This setup offers flexibility and scalability, catering to diverse workload requirements. Organizations benefit from optimized resource utilization while maintaining control over sensitive data. With hybrid cloud computing becoming prevalent, it provides an agile and efficient solution for businesses’ IT needs.
Hybrid Cloud Security Risks
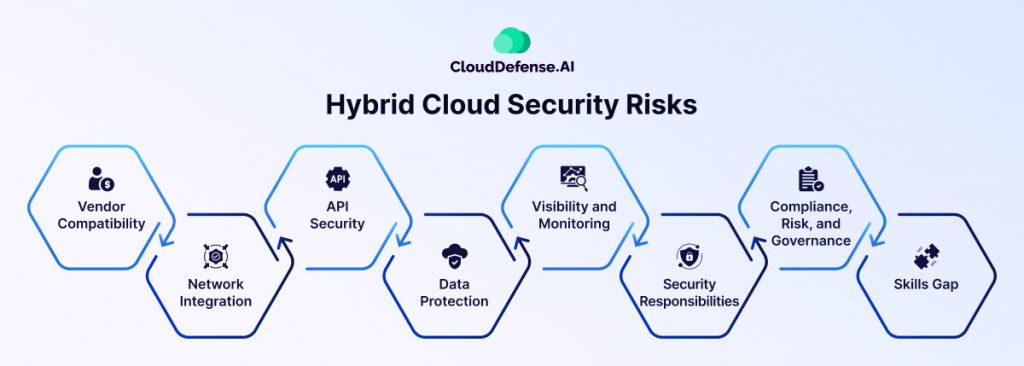
Hybrid cloud environments introduce unique security risks that organizations must address to safeguard their data and infrastructure. Here’s a breakdown of these risks and strategies to minimize them:
Vendor Compatibility
- How they occur: Juggling multiple cloud providers increases complexity and security vulnerabilities.
- Prevention: Establish a centralized security architecture and governance framework to manage diverse cloud environments efficiently. Choose reputable cloud providers and services that align with your organization’s security requirements.
Network Integration
- How they occur: Integrating existing systems with cloud environments can lead to compatibility issues and vulnerabilities.
- Prevention: Address network security concerns proactively during the migration process. Implement native firewall services and logging tools for enhanced security.
API Security
- How they occur: Poorly configured APIs pose a significant security threat, exposing sensitive data and back-end logic.
- Prevention: Conduct regular security assessments of APIs and implement strong authentication mechanisms. Adhere to industry best practices outlined by organizations like OWASP.
Data Protection
- How they occur: Ensuring the security and privacy of sensitive data across hybrid cloud environments is essential for regulatory compliance.
- Prevention: Encrypt data in transit and at rest, implement access controls based on least privilege principles, and maintain data residency compliance. Regularly audit data flows to identify vulnerabilities and ensure compliance.
Visibility and Monitoring
- How they occur: Limited visibility into hybrid cloud environments makes it difficult to detect and respond to security threats effectively.
- Prevention: Implement comprehensive monitoring solutions to track all resource activities and access attempts. Use native security tools provided by cloud service providers and integrate with SIEM platforms for centralized threat detection and response.
Security Responsibilities
- How they occur: Shared responsibility models in hybrid cloud environments require clear delineation of security responsibilities between organizations and service providers.
- Prevention: Document security responsibilities in contractual agreements and establish clear lines of communication with service providers. Conduct regular security assessments to ensure compliance with established security policies.
Compliance, Risk, and Governance
- How they occur: Meeting regulatory requirements and industry standards in hybrid cloud environments requires cross-functional coordination and alignment.
- Prevention: Align security standards and frameworks with overall business objectives and cybersecurity strategies. Implement strong risk management and governance practices to ensure compliance with regulatory requirements.
Skills Gap
- How they occur: A shortage of skilled cybersecurity professionals hinders organizations’ ability to address evolving security challenges in hybrid cloud environments.
- Prevention: Invest in training and development programs to bridge the skills gap within security teams. Use external resources such as cybersecurity certifications and managed security services to augment internal capabilities.
How To Secure Hybrid Cloud Environments
Securing hybrid cloud environments involves several key factors that we have mentioned below:
- Standardize Processes: Ensure consistent security measures and procedures across both public and private clouds to prevent errors and gaps.
- Encrypt Data Consistently: Apply encryption uniformly to data in transit and at rest across all cloud environments.
- Configure Secure Tools: Implement automated security workflows, such as DevSecOps pipelines, to reduce human error and ensure secure code deployment.
- Establish Business Continuity: Develop backup and disaster recovery plans to maintain operations during emergencies.
- Manage Access: Implement Identity and Access Management (IAM) to control resource access and enforce least-privileged access principles.
- Use CWPP: Use CWPP for visibility, risk assessment, and remediation of vulnerabilities.
- Isolate Critical Infrastructure: Segment critical systems and limit access to authorized users to enhance security.
- Use CSPM: Utilize CSPM for automated assessment and resolution of security issues.
4. Multi-Cloud Environments
A multi-cloud environment refers to the strategic use of cloud computing services from multiple cloud providers simultaneously. This approach allows organizations to leverage a combination of public and private cloud resources, tailoring their computing environment to suit the unique requirements of each workload. By utilizing services from multiple vendors, businesses gain flexibility, resilience, and the ability to avoid vendor lock-in.
Multi-Cloud Security Risks
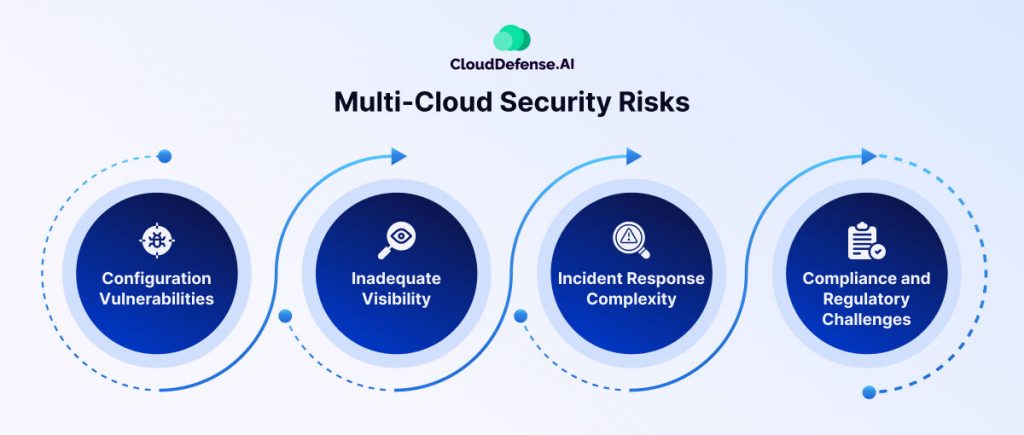
Multi-cloud environments may introduce a wide range of security challenges to IT infrastructures. Here are a few common risks that you need to be aware of.
Configuration Vulnerabilities
- How They Occur: The complexity of managing configurations across multiple cloud environments increases the likelihood of misconfigurations. Outdated components, exposure of storage nodes to the internet, and misaligned access management policies are common issues.
- Prevention: Implement robust configuration management practices, regularly update server and container components, restrict access to storage nodes, and ensure proper alignment of identity and access management policies.
Inadequate Visibility
- How They Occur: Challenges in logging and monitoring across multiple clouds lead to difficulties in detecting and responding to security events. Coordinating monitoring playbooks and contextualizing alerts becomes complex.
- Prevention: Implement centralized logging and monitoring solutions to gain consistent visibility across all cloud environments. Develop standardized playbooks for monitoring and alerting, ensuring they are tailored to each service environment.
Incident Response Complexity
- How They Occur: Incident detection and response are hindered by the need for the preparation of tools and workflows in each cloud environment. Hybrid architectures further complicate incident response efforts.
- Prevention: Prepare incident response tools and workflows in advance for each cloud environment. Provide training to incident response teams on responding to incidents in diverse cloud environments.
Compliance and Regulatory Challenges
- How they occur: Meeting compliance requirements across multiple cloud environments poses challenges, especially in regulated industries. While cloud providers offer compliance reports, organizations must still ensure their own controls and reporting align with regulatory standards.
- Prevention: Regularly review and update compliance measures to align with regulatory requirements. Ensure proper documentation and reporting of customer controls status in each cloud environment.
How To Secure Multi-Cloud Environments?
Securing multi-cloud environments requires a comprehensive approach that uses industry best practices and specialized security tools and processes:
- Adopt CSPM: Utilize CSPM platforms to monitor and report on configuration and vulnerability statuses across all cloud deployments. CSPM platforms help ensure compliance with regulatory requirements and provide insights into security posture across multiple clouds.
- Deploy Cloud-Native SIEM: Implement cloud-native Security Information and Event Management (SIEM) systems to enhance visibility and detection capabilities. Integrate cloud logs and event data into SIEM platforms for centralized monitoring, alerting, and threat detection across multi-cloud environments.
- Implement Cloud-Native Guardrails: Use security services and tools offered by leading CSPs such as Google Cloud Security Command Center, Microsoft Azure Security Center, and Amazon GuardDuty. These native tools enhance security monitoring, threat detection, and provide additional controls to safeguard multi-cloud deployments.
- Utilize Multi-Cloud Compatible Tools: Choose security tools that can seamlessly operate across multiple cloud providers, including endpoint detection and response (EDR), extended detection and response (XDR), and cloud-native application protection platforms.
5. Multi-Tenant Cloud Environments
A multi-tenancy cloud refers to a cloud computing model where a single instance and infrastructure are designed to serve multiple customers, known as tenants simultaneously. In this architecture, tenants share computing resources such as servers, storage, and networking infrastructure, but their data and applications are kept separate and isolated from one another. This allows for efficient resource utilization and scalability, making it a fundamental aspect of cloud computing, particularly in SaaS offerings.
Multi-Tenant Security Risks
Multi-tenant cloud environments might seem lucrative in the first look but they are known to introduce some major security risks. Here are some of the risks that you need to be aware of.
Data Breach Risks
- How they occur: Multi-cloud environments often involve shared infrastructure where multiple tenants’ data coexists. If one tenant’s data is breached, it can potentially compromise the privacy and security of other tenants’ data within the shared environment.
- Prevention: Implement robust access controls, encryption mechanisms, and data isolation techniques to ensure that each tenant’s data remains separate and protected. Conduct regular security audits and penetration testing to identify and address vulnerabilities proactively.
High Downtime Risks
- How they occur: Inadequate resource allocation and scalability can lead to overutilization of resources by tenants, resulting in system shutdowns and downtime.
- Prevention: Employ dynamic resource allocation strategies and auto-scaling capabilities to ensure that resources are allocated efficiently based on demand. Monitor resource usage patterns in real-time and invest in scalable infrastructure to accommodate fluctuating workloads effectively.
Configuration Change & Management Risks
- How they occur: Configuration changes or upgrades made by one tenant may inadvertently impact the environment of other tenants, leading to misconfigurations and potential disruptions.
- Prevention: Establish rigorous change management processes to assess the impact of configuration changes before implementation. Utilize automation tools for consistent and controlled configuration management across the multi-cloud environment. Implement segmentation techniques to isolate tenants’ environments and minimize the impact of changes on others.
Inadequate Visibility and Monitoring
- How they occur: Limited visibility and monitoring across multiple cloud environments make detecting and responding to security threats challenging.
- Prevention: Deploy cloud-native security monitoring and analytics tools that provide centralized visibility into all cloud environments. Implement robust logging and auditing mechanisms to track user activities and detect suspicious behavior. Leverage cloud-native security services and platforms to automate threat detection and response processes.
How To Secure Multi-Tenant Environments
Securing multi-cloud environments requires a combination of robust practices and tools to protect sensitive data and maintain system integrity. Here are ten best practices to enhance security in multi-cloud architectures:
- Access Control: Implement role-based access control (RBAC) to manage permissions effectively, ensuring that users have appropriate access based on their roles. Regularly review and adjust access limits to reflect organizational changes and minimize the risk of unauthorized access.
- Audit Trails: Utilize logging systems to maintain detailed audit trails of user actions and system events. Centralized log management solutions like SIEM systems enable efficient storage and analysis of logs, facilitating the detection of suspicious activities.
- Compliance Management: Choose cloud services with built-in compliance features and ensure adherence to relevant standards and regulations such as GDPR, HIPAA, or ISO 27001. Regularly assess compliance status and update processes accordingly.
- Data Encryption: Employ strong encryption techniques to protect data both at rest and in transit. Utilize encryption tools provided by cloud providers and implement robust key management practices to safeguard encryption keys.
- Data Loss Prevention (DLP): Deploy DLP solutions to monitor data movement and enforce policies to prevent unauthorized data transfers. Configure DLP rules to identify and mitigate potential data leaks proactively.
- Incident Response Plan: Develop a comprehensive incident response plan outlining roles and responsibilities in the event of a security breach. Conduct regular exercises and simulations to ensure an effective and timely response to security incidents.
- Regular Patching: Establish a patch management strategy to keep the software, operating systems, and security tools up to date. Monitor vendor security bulletins and promptly apply patches to address reported vulnerabilities and minimize the risk of exploitation.
- Tenant Isolation: Enhance isolation in multi-tenant environments using virtualization technologies such as VPCs and cloud network segmentation. Isolating tenants helps mitigate the impact of security incidents and unauthorized access.
- Use Cloud Security Tools: Use a variety of cloud security tools such as CNAPPs, CASBs, and firewalls as a service to enhance security posture and meet shared security model responsibilities effectively.
Conclusion
Securing the diverse cloud environment types- public, private, hybrid, multi-cloud, and multi-tenant-demands customized strategies. While cloud providers excel in security, businesses must apply best practices. Prioritizing data protection and compliance ensures business continuity amid evolving risks. By embracing security measures, organizations confidently harness the benefits of cloud computing.







