When it comes to agile software development, ensuring security isn’t just about your in-house code anymore—it’s about the entire software supply chain. Ever found yourself wondering about the myriad dependencies in your project and why they’re there?
That’s where the Software Bill of Materials (SBOM) comes into play – think of it as a comprehensive guide that reveals the contents and origins of your application’s code. There are multiple tools for crafting SBOMs, but in this blog, we will delve into the specifics of leveraging SBOM with GitLab Actions.
What is GitLab?
GitLab serves as a web-centric platform catering to version control, continuous integration, and collaborative efforts in software development. Functioning as an extensive DevOps lifecycle tool, GitLab empowers teams to oversee and monitor source code alterations, thereby building developers’ cooperation. It encompasses functionalities such as issue tracking, code review, and an integrated CI/CD system, streamlining the intricacies of development workflows.
With a consolidated interface, GitLab supports both the hosting of Git repositories and project management, providing a unified solution for code repositories, issue tracking, and CI/CD pipelines. Notably, it has strong security features, encompassing container scanning and vulnerability management, thereby elevating the overall development process.
GitLab’s open-source character and adaptability position it favorably as a go-to option for organizations seeking to optimize their software development lifecycle.
Benefits of Utilizing SBOM with GitLab Actions
Integrating Software Bill of Materials (SBOM) with GitLab Actions offers several strategic advantages:
Transparency and Values Alignment:
Generating accurate SBOMs aligns with GitLab’s core value of transparency. SBOMs provide thorough insights into software components, including origin and vulnerability details, promoting transparency and adherence to open core principles.
Risk Mitigation and Informed Decision-Making:
Lack of visibility into software dependencies is a significant risk. SBOMs empower GitLab to make well-informed decisions rapidly, drawing insights from diverse sources. This robust risk management approach enhances decision-making in the software development lifecycle.
Competitive Differentiation:
Being a frontrunner in the DevSecOps domain, GitLab’s emphasis on SBOMs sets a higher benchmark. Excelling not only in product features but also in customer confidence regarding SBOMs gives GitLab a competitive advantage, positioning it as an industry pacesetter.
Efficiency and Standardization:
Embracing standardized formats such as CycloneDX and VEX simplifies communication. This ensures a clear understanding of software dependencies and vulnerabilities, eradicating ambiguities and boosting operational efficiency for GitLab and its user base.
Regulatory Compliance Readiness:
Anticipating evolving regulatory landscapes, GitLab’s integration with SBOMs positions it ahead of compliance requirements. With references to U.S. federal orders, cybersecurity strategies, and ongoing legislative developments, GitLab is prepared for dynamic regulatory changes in the software supply chain.
Which type of SBOM is used for GitLab?
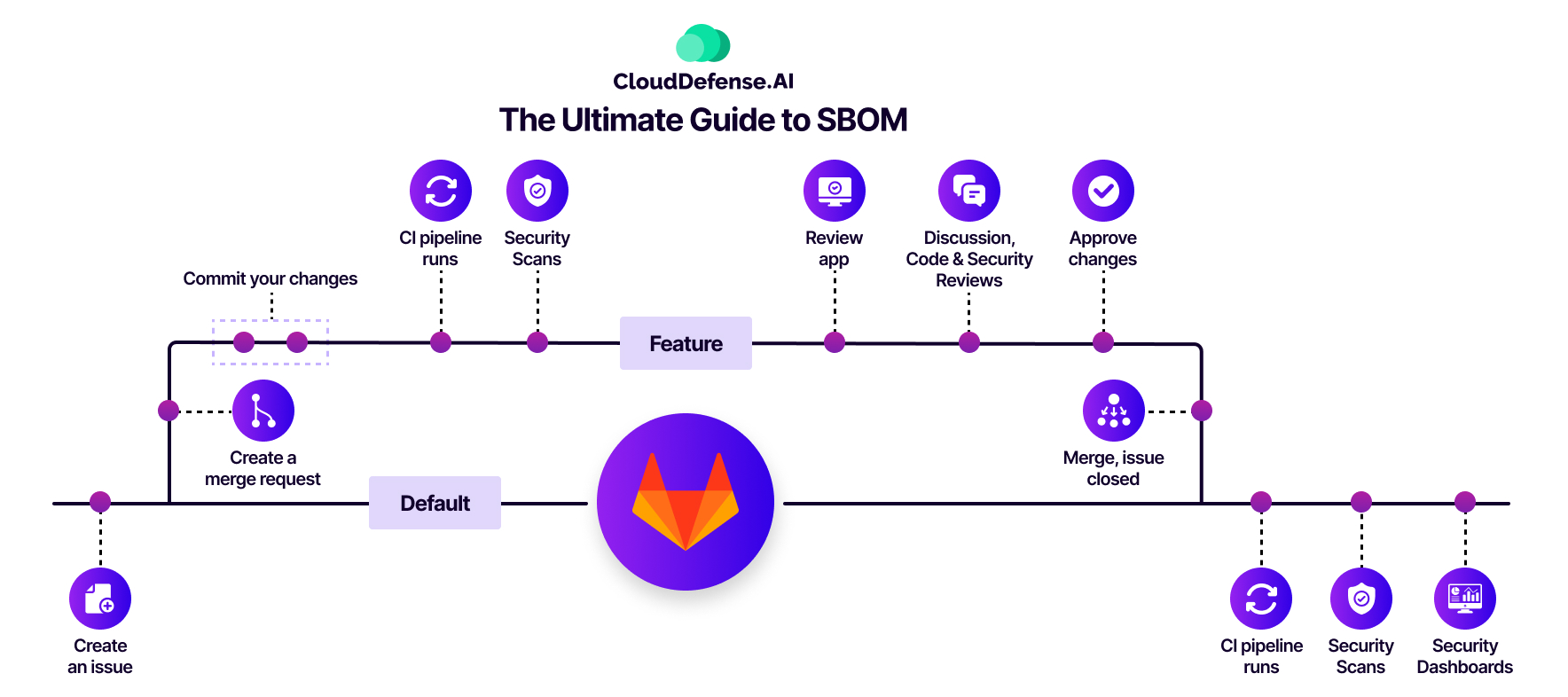
As of version %16.4, GitLab utilizes the CycloneDX format for SBOM within its product features. Within the GitLab ecosystem, several features have been seamlessly incorporated to enhance SBOM-related functionalities:
CycloneDX-Formatted SBOMs: GitLab now possesses the capability to generate SBOMs in the CycloneDX format. This extends to the generation of CycloneDX-formatted SBOMs following both Dependency and Container scans within GitLab.
Dependency List: A pivotal addition is the Dependency List feature embedded in GitLab, consolidating vulnerability and license data from the existing GitLab databases. This empowers users to gain comprehensive insights into dependencies within their projects.
API for Pipeline-Specific CycloneDX SBOM Exports: With version %16.4, GitLab has introduced an Application Programming Interface (API) facilitating the export of CycloneDX SBOMs tailored to specific pipelines. This API introduces a more nuanced and customizable approach to SBOM generation.
Group-Level Dependency Lists: GitLab has expanded dependency management by enabling the creation of group-level dependency lists. This extends the oversight of dependencies to a broader organizational level.
Despite GitLab’s proficiency in generating CycloneDX SBOMs for most projects, it’s essential to note that, as of version %16.4, the company primarily leverages Dependency Lists to access vulnerability information for key projects.
Notably, GitLab does not actively ingest these CycloneDX SBOMs, amalgamate them, produce VEX BOMs (Vulnerability and EXposure), nor readily provide them to customers. This snapshot represents GitLab’s current status as of version %16.4.
Create SBOM Maturity Model with GitLab
To create an SBOM Maturity Model with GitLab, ensuring the comprehensive generation and management of Software Bill of Materials (SBOMs), follow these steps based on the information provided:
1. Automatic SBOM Generation in CycloneDX Format:
- Ensure that GitLab repositories can automatically generate complete and accurate SBOMs in the accepted format, such as CycloneDX.
- Confirm that the generated SBOMs include all of NTIA’s recommended minimum data elements: Supplier Name, Component Name, Version of the Component, Other Unique Identifiers, Dependency Relationship, Author of SBOM Data, and Timestamp.
- Enable fields like Dependency Relationship and Author, if not already available, by submitting a feature request for missing fields.
2. Source SBOM from Development Environment:
- Leverage GitLab’s existing Dependency List feature, which allows creating a “Source SBOM” directly from the development environment, source files, and included dependencies used to build a product artifact.
- Explore the possibility of exporting the Dependency List into CycloneDX format to meet the accepted standard.
3. Analyzed SBOM for Artifacts:
- Utilize GitLab’s existing capability to generate “Analyzed SBOMs” through the analysis of artifacts (e.g., executables, packages, containers, and virtual machine images) after their build.
- Leverage the CycloneDX SBOMs produced in CI pipelines for both Dependency Scanning and Container Scanning.
4. Digital Signing of SBOMs:
As mentioned in GitLab’s planned features under Software Supply Chain Security, ensure future support for digitally signing SBOMs at build or release time. This would contribute to the integrity and authenticity of SBOMs.
Documentation and Communication:
- Document the processes and features within GitLab that support each aspect of the SBOM Maturity Model.
- Communicate the availability and usage of these features to GitLab users and administrators.
By following these steps, you can establish a robust SBOM Maturity Model within GitLab, aligning with industry standards and ensuring transparency and security in the software supply chain. Keep an eye on GitLab’s updates and feature releases to stay aligned with the evolving landscape of SBOM requirements.
The future of SBOM and GitLab
GitLab is gearing up for the future of Software Bill of Materials (SBOM) with a strong dedication to beefing up software supply chain security. As the industry places a spotlight on securing software supply chains, SBOMs are becoming increasingly vital for ensuring transparency, traceability, and effective risk management.
GitLab is fully tuned in to the changing landscape and is tackling key concerns related to SBOMs head-on. Let’s break down what they’re up to:
Constantly Boosting SBOM Capabilities: GitLab has seamlessly woven SBOMs into its software supply chain strategy, highlighting their significance within the DevSecOps platform. They’re committed to continuously tweaking and refining SBOM capabilities, ensuring they stay ahead in the game of top-notch software security practices.
Exciting Features in the Pipeline: GitLab is on the move, actively planning cool new features and functionalities tied to SBOMs. This shows their proactive stance in addressing industry concerns. Among the planned features is the automation of attestation through the Runner, making it easier for users by supporting code signature generation via short-lived keys.
Digital Signing for Build Artifacts: GitLab is all set to introduce the automatic digital signing of build artifacts, giving an extra layer of security and integrity to the software supply chain. This nifty feature will make sure that build artifacts are digitally signed during the build process, adding a trustworthy seal to the entire process.
Support for Externally Generated SBOMs: GitLab is getting ready to embrace externally generated SBOMs, understanding the need for flexibility and interoperability with SBOMs created outside the GitLab world. This is a game-changer for organizations using various tools or platforms for SBOM generation, allowing them to centralize and manage information seamlessly within GitLab.
FAQ
1. Can SBOM with GitLab Actions be used for open-source projects?
Absolutely! You can utilize SBOM in conjunction with GitLab Actions for your open-source projects. GitLab plays a major role in building transparency throughout software development by generating precise SBOMs, complete with details about dependencies and potential vulnerabilities. This functionality proves invaluable for both open-source and proprietary projects, bolstering security measures and effectively managing risks in the software supply chain.
2. What is the purpose of GitLab?
GitLab is like your all-in-one DevOps tool. It’s a comprehensive platform that comes packed with tools and features catering to version control, continuous integration, continuous deployment, collaboration, and more. The whole point? Streamlining the software development lifecycle.
GitLab empowers teams to handle code repositories efficiently, keep tabs on changes, automate testing and deployment, and promote seamless collaboration among team members. Think of it as your go-to for end-to-end DevOps processes – from planning and coding to testing and monitoring, all conveniently housed within a single integrated platform.
Conclusion
In wrapping up, as the need for SBOMs keeps on growing, it’s become a crucial factor for software sellers, federal software developers, and open-source communities. The traditional scenarios of software supply chain security are changing, with government agencies more and more suggesting or requiring SBOM creation. To stay proactive and lead the way in the world of software security, it’s crucial to explore the SBOM with GitLab’s DevSecOps platform.
GitLab not only recognizes how important SBOMs are but has also incorporated strong features to meet these demands. By making the most of GitLab’s capabilities, organizations can ensure that their software development processes are transparent, traceable, and secure, aligning with the best practices in the industry and meeting regulatory expectations.







