In 2023 alone, over 26,000 software vulnerabilities were discovered – that’s more than 70 new vulnerabilities every single day. In an increasingly interconnected world, where our reliance on software extends from our personal devices to critical infrastructure, the security of our code has never been more important.
Think about it – major companies with vast resources and elite talent still get caught in this software insecurity vortex. If tech giants deploying cutting-edge security practices still struggle, what chance does the average developer have? The hard truth is we’re all caught in the vulnerability vortex to some degree.
But it doesn’t have to be this way. While we may never eradicate vulnerabilities completely, there are concrete steps we can take to significantly improve software security from the start. By rethinking our coding practices and development lifecycles, we can minimize that sinking feeling of playing whack-a-mole with security holes.
The path forward begins with understanding what goes wrong and why the vulnerability vortex perpetuates in the first place. Only then can we chart a new course helping developers break free from insecure coding patterns once and for all.
Understanding the Vulnerability Vortex
Software vulnerabilities are like cracks in a dam – they may seem small at first, but they can grow into major security breaches. These weaknesses arise from a combination of factors:
Here’s a breakdown of some common causes:
- Coding Errors: Simple mistakes like typos or logical errors can create vulnerabilities.
- Improper Input Validation: If code doesn’t properly check user input (like data entered in a form), attackers can inject malicious code and manipulate the application.
- Weak Authentication: Inadequate user login procedures or password storage can allow unauthorized access.
- Outdated Libraries and Frameworks: Using outdated code components with known vulnerabilities creates easy access points for attackers.
- Insecure Design: The fundamental architecture of the software might have inherent weaknesses that leave it vulnerable.
So, why does software remain vulnerable despite these known risks? Here are some contributing factors:
- Development Speed vs. Security: The pressure to release software quickly can lead to security being overlooked in favor of faster development cycles.
- Lack of Security Expertise: Developers may not have the necessary training or resources to identify and address security vulnerabilities effectively.
- Legacy Systems: Maintaining and securing older software built without modern security practices can be challenging.
- Evolving Threats: Attackers are constantly developing new methods to exploit vulnerabilities, keeping developers on the defensive.
The Cycle of Insecurity: A Breeding Ground for Breaches
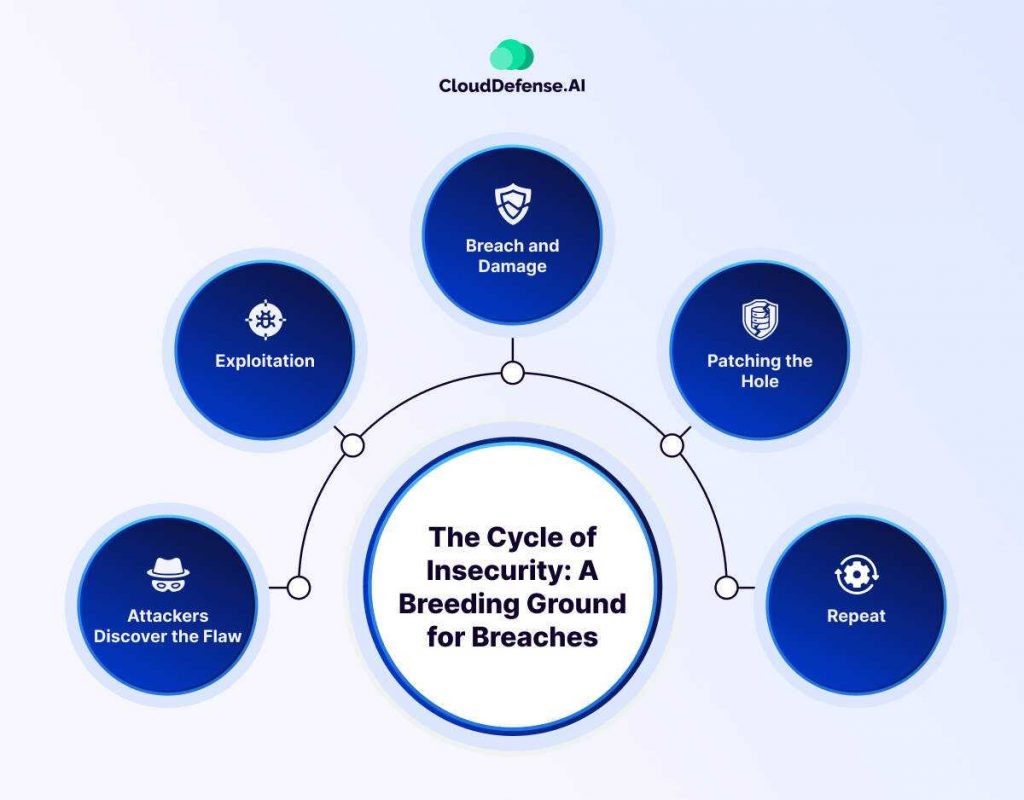
Unpatched vulnerabilities create a vicious cycle of insecurity within software and applications. It all starts with a false sense of security, often fueled by the belief that “it won’t happen to us” or that existing security measures are sufficient. This complacency breeds a dangerous lack of vigilance, allowing vulnerabilities to fester in the code.
These vulnerabilities become ticking time bombs, waiting to be exploited by malicious actors. Here’s how a single unaddressed vulnerability can trigger a cascade of security issues:
- Attackers Discover the Flaw: Through various techniques like automated scanning or targeted research, attackers identify the vulnerability in the software.
- Exploitation: They develop an exploit, a piece of code specifically designed to take advantage of the vulnerability.
- Breach and Damage: Once the exploit is launched, attackers can gain unauthorized access to systems, steal sensitive data, or disrupt critical operations.
- Patching the Hole: After a breach occurs, the developers scramble to release a patch that fixes the vulnerability.
- Repeat: Unfortunately, the cycle doesn’t end there. Attackers are constantly searching for new vulnerabilities, and the process begins again.
This cycle is tragically evident in real-world security incidents. Here are a couple of chilling examples:
Equifax Breach (2017): A vulnerability in a web server allowed attackers to access the personal information of over 147 million Americans. This breach could have been prevented if Equifax had addressed a known vulnerability in Apache Struts software used on their website.
SolarWinds Supply Chain Attack (2020): Hackers compromised a widely used network monitoring software, SolarWinds Orion. This compromise allowed them to gain access to numerous downstream targets, demonstrating how a single vulnerability in a critical piece of software can have a cascading effect.
Colonial Pipeline Ransomware Attack (2021): A legacy system with unaddressed vulnerabilities allowed attackers to disrupt operations of a major US fuel pipeline, showcasing the real-world impact of insecure software on critical infrastructure.
These examples illustrate how the cycle of insecurity can have devastating consequences. But is there a way out of this cycle? Is it even possible to achieve truly secure software?
These questions lead us to the next section, where we’ll explore strategies for breaking free from the vulnerability vortex and building a more secure digital future.
Breaking Free: Proactive Security with CloudDefense.AI
While patching vulnerabilities remains crucial, reactive measures alone are not enough in today’s constantly growing threat front. The key to escaping the vulnerability vortex lies in proactive security measures implemented throughout the development lifecycle. This is where tools like CloudDefense.AI come into play.
CloudDefense.AI empowers developers and security teams to achieve this by offering a comprehensive suite of tools for mitigating vulnerabilities during the development process. Here’s how CloudDefense.AI helps:
Continuous Agentless Assessment: Unlike traditional vulnerability scanners, CloudDefense.AI works without installing agents on your systems. This lightweight approach enables continuous assessment without impacting performance, allowing you to identify and address vulnerabilities early in the development cycle.
AI-Powered Remediation: CloudDefense.AI leverages the power of Artificial Intelligence to not only identify vulnerabilities but also suggest potential remediation strategies. This streamlines the process and frees up developer time.
Key Features of CloudDefense.AI:
Detailed Inventory Discovery: Gain a complete view of your cloud environment, including libraries, frameworks, and containers. This comprehensive inventory ensures no potential vulnerability goes undetected.
Context-Driven Prioritization: CloudDefense.AI goes beyond just identifying vulnerabilities. It analyzes the context of your cloud assets and prioritizes threats based on their potential impact. This allows your team to focus on the issues that matter most.
Attack Path Analysis and Visual Graphs: Move beyond a simple list of vulnerabilities. CloudDefense.AI utilizes attack path analysis to identify interconnected vulnerabilities and visualize them through clear, informative graphs. This empowers your team to understand the bigger picture and take comprehensive mitigation steps.
CI/CD Integration and Automated Detection: Seamlessly integrate CloudDefense.AI into your CI/CD pipeline to automatically identify and eliminate vulnerabilities before deployment. This proactive approach significantly reduces the risk of vulnerabilities reaching production.
Compliance Management: Ensure adherence to critical security standards like GDPR, PCI, and HIPAA with CloudDefense.AI’s compliance management features. It streamlines the compliance process and helps maintain a secure development environment.
By implementing these proactive measures throughout the development process, CloudDefense.AI helps organizations escape the vulnerability vortex and build applications with security embedded from the ground up. This is not just about staying ahead of threats; it’s about building a more secure digital future for everyone. Ready to see CloudDefense.AI in action? Book a free demo today and discover how it can help you escape the vulnerability vortex!







