While assessing the cybersecurity requirements, it can get confusing for organizations to choose between an endpoint protection platform (EPP) and endpoint detection and response (EDR).
Both EPP and EDR serve as vital components of modern cybersecurity, where each component plays a critical role in safeguarding an organization’s endpoint devices. The main motive of EPP is to provide protection against security threats, whereas EDR is designed to detect and respond to incidents that other security measures can’t detect.
Although both the components are similar in various aspects, they are quite different, and each of them plays a distinct role. To help you strategize your endpoint security, we have created this guide that will provide you with a detailed comparison of the EPP vs EDR difference.
Understanding Endpoint Protection Platform (EPP)
What is an Endpoint Protection Platform (EPP)?
An endpoint protection platform or EPP is an endpoint security solution that comprises a set of security technologies, and its main aim is to detect and prevent security threats on the endpoint device.
According to Gartner, EPP is a solution implemented on an endpoint device to prevent security attacks, identify malicious activities, and deliver investigation and remediation proficiency required for responding to various cybersecurity incidents.
The main aim of EPP is to safeguard the endpoints from all kinds of security threats like file-less attacks, malware, zero-day vulnerability, and others. An effective EPP collects massive amounts of data and leverages the best tools, including AI, to anticipate the next attack vector.
Many EPP solutions come equipped with various cloud-based detection techniques that utilize cloud data to identify threat vectors. Some EPPs also leverage machine learning and behavioral analysis to identify suspicious activities at the endpoints. In some cases, EPP solutions come equipped with EDR, but in traditional EPP solutions, the EDR is kept optional.
Key Features of an EPP Solution
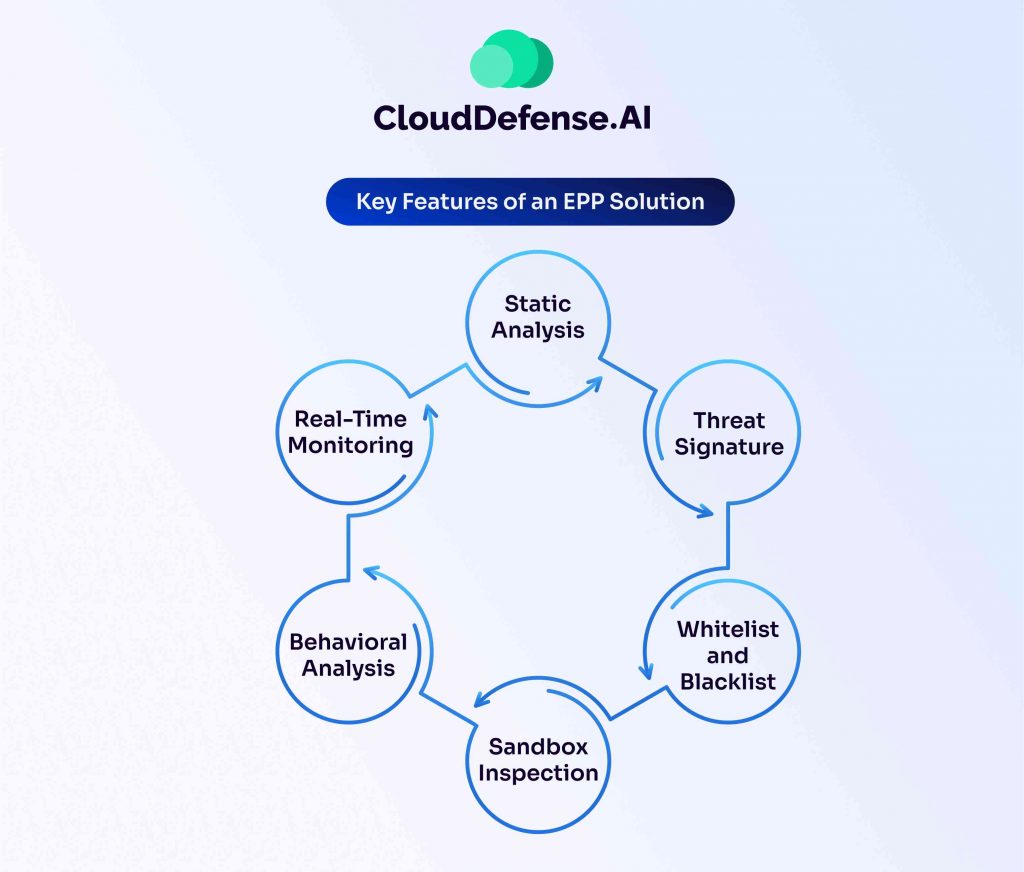
An EPP solution is a comprehensive security tool that delivers many valuable features for safeguarding the endpoint. These features are:
Static Analysis
Every EPP solution is equipped with static analysis capability, where it leverages machine learning to evaluate malicious binary files and identity components that can lead to vulnerabilities.
Threat Signature
It is a prime feature of the EPP solution, which enables it to detect incoming security threats by matching them with a database of malware signatures. This feature allows security teams to find malware and file-based threats.
Whitelist and Blacklist
The whitelist and blacklist feature of the EPP solution blocks access to all the malicious URLs, applications, and IP addresses.
Sandbox Inspection
A feature that makes EPP solutions highly effective is its sandbox feature. It assesses various files for malicious behavior by running them in a virtual environment and then executing them at the endpoint device.
Behavioral Analysis
By leveraging the behavioral analysis, EPP can also evaluate the behavior pattern in the endpoint and identify any malicious activity that can lead to security threats. The behavioral analysis works effectively even in the absence of a threat signature.
Real-Time Monitoring
Every EPP platform offers a real-time monitoring feature that constantly monitors all the endpoint activities and reports upon detection of any security incident.
Benefits of Endpoint Protection Platform (EPP)
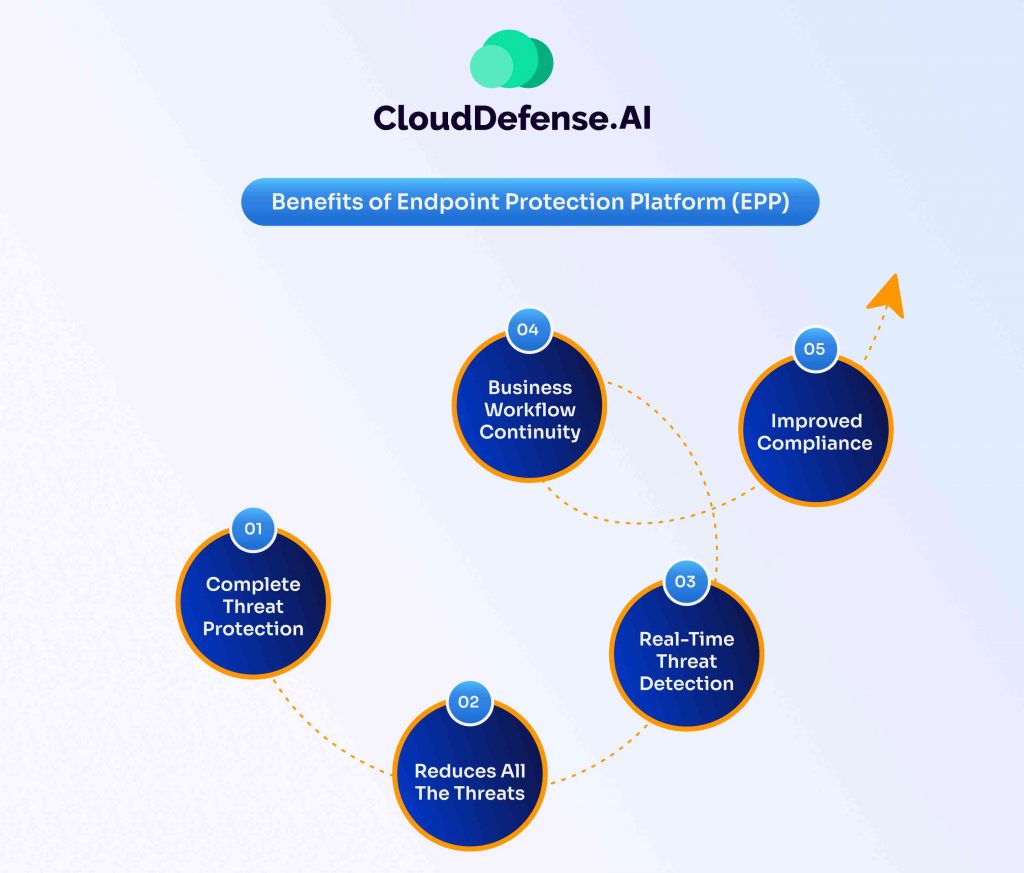
An Endpoint protection platform offers a range of benefits to every organization seeking to safeguard their endpoint devices:
Complete Threat Protection
Leveraging numerous capabilities, EPP provides comprehensive threat protection to all an organization’s endpoints and prevents attacks like malware, file-based attacks, phishing, and others.
Reduces All The Threats
One of the most significant benefits of EPP is its ability to curb threats before they can impact the endpoint devices. Since it utilizes AI threat intelligence and machine learning, it not only prevents malicious attacks but also prevents data breaches and identity theft.
Real-Time Threat Detection
EPP continuously monitors the endpoint activities in real-time to detect suspicious behavior that can lead to costly data breaches. It promptly responds to the threat and mitigates it to curb any impact.
Business Workflow Continuity
Endpoint protection platform benefits every organization by maintaining their business workflow continuity. Protecting the endpoints ensures the business workflow doesn’t get interrupted in the occasion of any potential threat.
Improved Compliance
Almost every regulatory framework requires organizations to implement robust security measures to protect endpoints. EPP helps organizations create a robust security strategy and cater to all the requirements needed to stay compliant with all the necessary regulatory frameworks.
How does EPP Work?
The endpoint protection platform works as an advanced security component; it is tasked with discovering threats and attackers who bypass normal endpoint security. It employs numerous technologies and security measures that work together to provide comprehensive protection.
By leveraging complex security stacks, EPP can gain a lot of insight and enhance data sharing that, ultimately, helps it detect malicious behavior in a better fashion. EPP utilizes a single agent to monitor all the endpoints of an organization and gain insight into the approaches of attackers. EPP also globally shares these data so it can be utilized to improve the behavioral detection capability of EPP solutions.
Understanding Endpoint Detection and Response (EDR)
What is Endpoint Detection and Response (EDR)?
Endpoint detection and response serve as a security solution that continuously monitors the activities of end-user devices and workloads to get complete visibility in real-time. By providing comprehensive visibility, it enables the team to identify and respond to all cybersecurity issues quickly.
Gartner defined EDR as a new type of technology that records endpoint behavior, identifies suspicious behavior at endpoints, provides quick information about attacks, prevents suspicious activity, and delivers restoration suggestions at the end.
It basically monitors and records all the endpoint data, which is then used by security teams for analyzing the endpoint data to proactively prevent threats like malware, file-less attacks, APTs, and ransomware.
When dealing with advanced attacks, EDR is compulsory as EPP solutions can’t alone remediate those security threats. What makes EDR more valuable is that it provides security teams with improved identification, investigation, and mitigation capabilities.
Moreover, the solution enables the security team to effectively respond to attacks by blocking malicious activities, quarantining endpoints, or deploying IR playbooks automatically.
Key Features of an EDR Solution
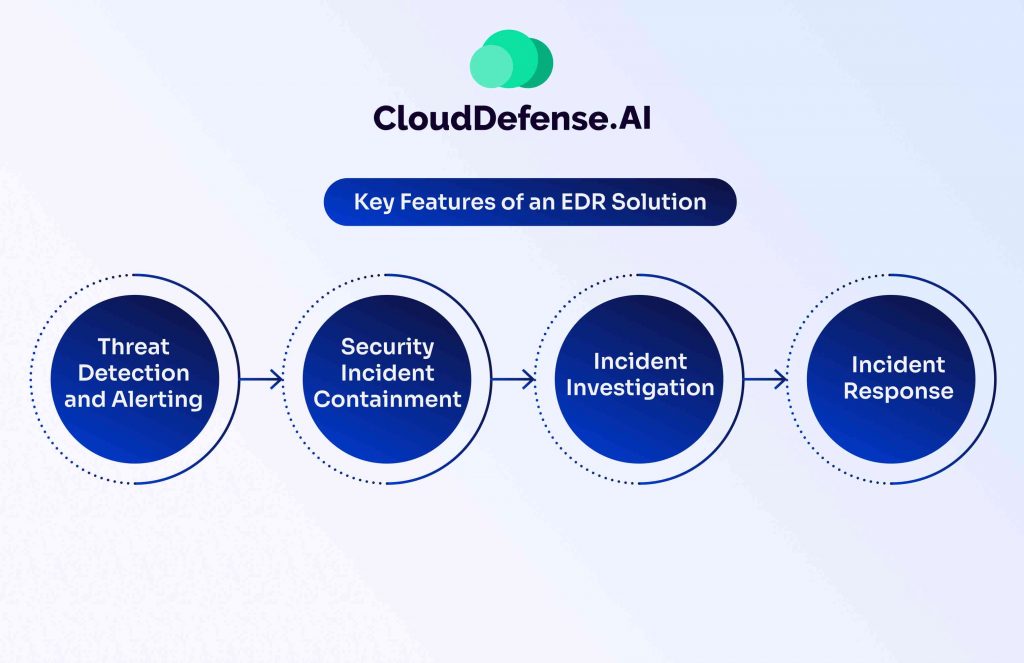
An EDR solution comes equipped with many key features that make it an effective EDR solution for safeguarding an organization’s endpoints. These features include:
Threat Detection and Alerting
One of the defining features of the EDR solution is its threat detection and alerting feature. Through continuous monitoring, it identifies malicious behavior and suspicious processes at the endpoint and alerts them to the security team.
Security Incident Containment
EDR solution has the capability to block all security incidents from making any impact and automatically contain the endpoint where a security incident has been reported. Through incident containment, it also prevents all the security threats from spreading to every part of the system.
Incident Investigation
When it comes to investigating a security incident in the endpoint, EDR also helps security through forensic investigation, where they create a central repository for collecting endpoint events and data. Using these data, the security performs analysis of malicious activities.
Incident Response
Another handy feature of EDR is that it provides an effective incident response, enabling security teams to perform prioritized action on endpoints. Whether reimaging an infected endpoint or changing passwords, incident response helps teams respond to activities quickly.
Benefits of Endpoint Detection and Response (EDR)
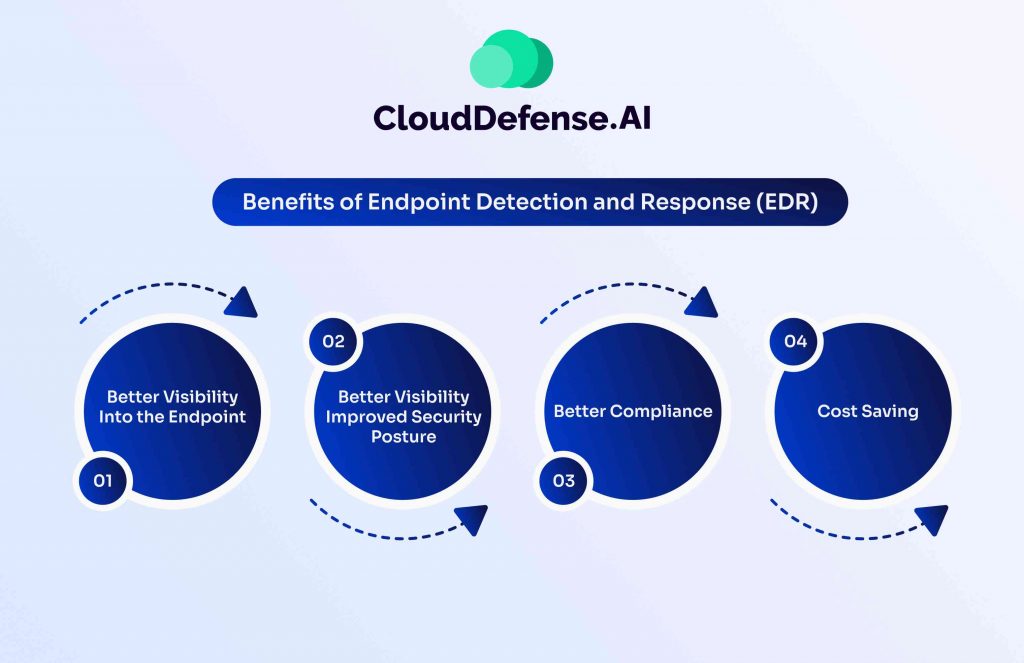
The number of benefits of an EDR solution is enormous, and this is the reason it is widely considered when it comes to building a robust endpoint security strategy. These benefits are:
Better Visibility Into the Endpoint
EDR solution benefits every organization by providing them better visibility into the endpoints through continuous monitoring and enables the team to detect and respond to threats. It includes detailed information about the endpoints in real-time and enables the security to detect malicious activities like malware.
Improved Security Posture
Implementation of EDR solutions enables organizations to enhance their cybersecurity strategy by responding to security threats in real time. It provides an additional layer against all types of cyberattacks by detecting them using various technologies.
Better Compliance
With EDR solutions in place, organizations won’t have problems staying compliant with strict industry regulatory frameworks like GDPR, HIPAA, and PCI DSS. It constantly monitors endpoints for suspicious activity and investigates the source to prevent any potential threat, ultimately eliminating the chance of any data theft.
Cost Saving
When an organization leverages an EDR solution for safeguarding their endpoints, it helps them to save a lot of money by curbing the cost associated with various security incidents. Using EDR, organizations can quickly detect and respond to security threats in real time and mitigate the issue before it can make any impact.
How Does EDR Work?
An effective endpoint detection and response solution works in a simple manner, and it often works alongside an endpoint protection platform to ensure optimum endpoint security.
At first, detect the security incident through analysis, contain the incident at the specific endpoint, contextualize it, and, in the end, provide all the necessary suggestions regarding the remediation process.
EDR continuously monitors all the activities at the endpoint and records all of them in a central repository for analysis. Since it records all the file modifications, network traffic, registry modifications, and other changes, EDR provides excellent threat visibility and allows organizations to respond to threats proactively.
EPP vs EDR: What is the Difference Between EPP and EDR?
Even though EPP and EDR have similar ultimate goals of preventing threats at endpoints, there are specific differences between them. However, on many occasions, vendors merge EDR with an EPP solution. Let’s take a look at those differences:
| EPP | EDR | |
| Main Focus | The primary focus of EPP is to prevent traditional cyber threats from impacting the endpoints. It basically acts as a first line of defense in safeguarding the endpoint devices and resources. | The main focus of EDR is to identify, investigate, and respond to security threats at the endpoint. This solution considers the threat that has appeared, so it investigates the activities and contains them. |
| Threat Prevention | EPP only prevents traditional threats like zero-day vulnerability, ransomware, and fileless attacks. It often prevents certain unknown threats. | EDR, on the other hand, responds to all types of security threats, including the ones that EPP can’t detect. It also provides remediation suggestions to security teams. |
| Approach | EPP takes a passive threat prevention approach. It conducts minimal supervision after installation and configuration. | EDR takes an active threat-prevention approach, where it actively investigates security threats and isolates them. |
| Visibility | EPP only offers comprehensive visibility into some of the activities in the endpoint. | EDR continuously monitors all the activities in the endpoint and records all the data at the endpoint for investigation. |
| Protection | EPP is tasked with the protection of each endpoint through isolation. | EDR, by collecting data and security events, allows security teams to analyze them and identify attacks spanning across different endpoints. |
| Detection Techniques | Signature matching, blacklisting and whitelisting, behavioral analysis and sandboxing. | Behavioral analysis, threat intelligence, and data analysis. |
| Automation | Leverage automation for the prevention of security threats. | It utilizes automation to respond to security incidents upon detection quickly. |
| Scalable | It is completely scalable to adapt to the increasing number of endpoints in an organization. | It can scale to accommodate increasing endpoints and data volume for investigation. |
3 Common Misconceptions About EPP and EDR
Here are three common misconceptions associated with EPP and EDR, and they often confuse security teams:
EPP is only about passive prevention
Many consider EPP to take a passive approach to threat prevention, but in reality, EPP is not only about passive form. Instead, it takes different forms to protect endpoints from security incidents. EPP also includes threat intelligence, vulnerability management, detection, and other techniques for mitigating any security threats at the endpoint.
Only EDR is sufficient against modern cyberattacks
EDR serves robust endpoint security as it helps the security team analyze activities across the endpoints and identify security threats to remediate them. However, an EDR solution is not sufficient enough to safeguard the endpoints against modern cyber threats. An organization must involve various other security capabilities in its strategy to protect the endpoints and ultimately prevent security breaches.
Organizations have to choose either EPP or EDR
Since EPP and EDR take a distinct approach toward threat prevention at the endpoint, many organizations consider choosing between EPP and EDR. However, one doesn’t have to choose between EPP and EDR as they offer limited capabilities without each other. Most of the vendors offer EDR along with EPP to help organizations protect endpoints against a broad spectrum of attacks.
EPP vs EDR: Which Should You Choose?
According to most analysts, it is always best for organizations to choose the combination of EPP and EDR to ensure optimum protection of endpoints.
Most vendors combine pure EPP along with EDR features to help organization safeguard their endpoints against modern cyberattacks. Organizations must understand that EPP acts as a first line of defense while EDR ensures that your organization can successfully respond to all security incidents.
EPP solution, by combining different technologies, creates a “safety net” that prevents hackers from breaching the endpoints. EPP doesn’t perform regular monitoring and utilizes fewer resources when it is hosted in the cloud.
EDR, on the other hand, enables security teams to respond to all attacks that are able to bypass EPP and also advanced attacks like APTs. It also enables the team to accurately identify the endpoint attack and contain them before they can make any significant impact.
So you can’t choose between the two as you will need both of them to ensure optimum endpoint security. The absence of any one of them will make the other useless and make the endpoints vulnerable to attackers.
FAQs
Is EDR part of EPP?
EDR serves as a foundational component of an EPP, and together, they provide comprehensive security to the endpoint. Even though they are distinct components, they are related in certain aspects, and without each, they won’t be able to mitigate cyberattacks in the endpoint.
Can EPP and EDR prevent all types of cyber threats?
EPP and EDR are vital endpoint security solutions that safeguard the endpoint from a variety of attacks. The EPP solution mostly prevents traditional cyber attacks from impacting the endpoint.
In comparison, EDR provides detection and response to all types of attacks on the endpoint. So, together, EPP and EDR can prevent all types of cyber threats and ensure complete protection.
How do EPP and EDR work together?
Many vendors integrate EDR solutions with pure EPP tools to provide comprehensive security to endpoints. EPP solutions act as a first line of defense where they create a safety net against traditional security threats.
When an attacker is able to breach the first line of defense. EDR comes into play when it identifies and contains unknown and advanced cyber threats in real time. Both EPP and EDR complement each other and work together to provide complete protection.
Conclusion
We can conclude this article by mentioning that both EPP and EDR solutions serve as essential tools for endpoint security. Together, they provide the comprehensive approach every organization requires to ensure robust endpoint security.
EPP and EDR are futile without each other, so it is better to go for a vendor that offers both while providing an endpoint security solution. In this guide, we have provided all the details you need to understand EPP and EDR and how they are different from each other.







