What if your computer became ground zero for a cyberattack? Imagine this: you settle in at your desk, ready to tackle a busy day. You fire up your computer, only to be met with a chilling message on your screen. A cybercriminal has taken control, encrypting all your files and demanding a hefty ransom to unlock them. Your work, personal documents, and precious memories – all held hostage.
This scenario, unfortunately, isn’t science fiction. Every day, countless devices fall victim to cyberattacks, putting sensitive data and entire networks at risk. But what if there was a way to strengthen your defenses and prevent your computer from becoming ground zero?
Keep reading as we explore the essential endpoint security measures every business should embrace.
What is Endpoint Security?
Think about all the different gadgets you use to connect to your company’s network – your work laptop, your phone, maybe even a tablet. These devices are called “endpoints”, and they act as gateways into your organization’s systems and data. Well, unfortunately, cybercriminals also see them as potential entry points to wreak havoc.
Endpoint security refers to a comprehensive strategy for safeguarding these entry points – or endpoints – of your network. These endpoints encompass all the devices users interact with, including laptops, desktops, tablets, smartphones, and even servers. Essentially, anything that connects to your network and potentially provides an opening for cyberattacks falls under the umbrella of endpoint security.
Traditionally, antivirus software served as the first line of defense, shielding against basic malware threats. However, endpoint security goes far beyond simple antivirus protection. It’s a layered security approach that employs a combination of technologies to proactively prevent, detect, contain, and respond to a wide range of cyber threats.
Common Endpoint Security Risks
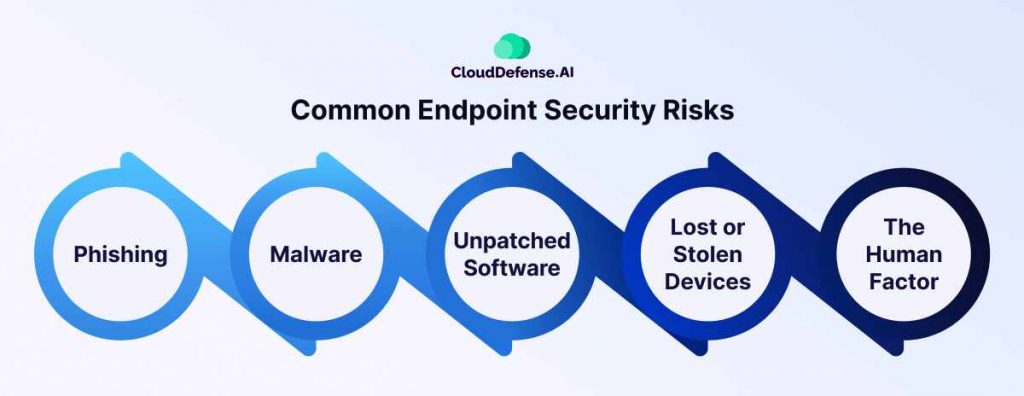
You know that feeling when you misplace your laptop or phone for a few minutes, and panic starts to set in? Yeah, that pit-in-your-stomach sensation is justified because those endpoints are gateways to a world of hurt if they fall into the wrong hands. In the digital world, these vulnerabilities are endpoint security risks – the gaps in your defenses that cybercriminals can exploit to gain access to your device and wreak havoc. Let’s explore some of the most common threats lurking in the shadows:
Phishing: Have you ever received an email that appears to be from your bank, but something just feels off? Phishing emails are cleverly disguised attempts to trick you into revealing sensitive information like passwords or clicking on malicious links that can infect your device.
Malware: From viruses and worms to ransomware and spyware, malware encompasses a range of malicious software designed to steal data, disrupt operations, or hold your files hostage.
Unpatched Software: Those nagging update notifications? They’re not there to annoy you. Software updates often contain critical security patches that fix vulnerabilities hackers can exploit. Ignoring them creates a wide-open door for attacks.
Lost or Stolen Devices: A misplaced laptop or a stolen phone – both pose significant security risks. If your device lacks proper encryption, sensitive information can easily fall into the wrong hands.
The Human Factor: We all make mistakes. Clicking on a suspicious link or downloading an unknown attachment can create a security breach. Uneducated users are a prime target for social engineering attacks that manipulate them into compromising security protocols.
Essential Endpoint Security Best Practices
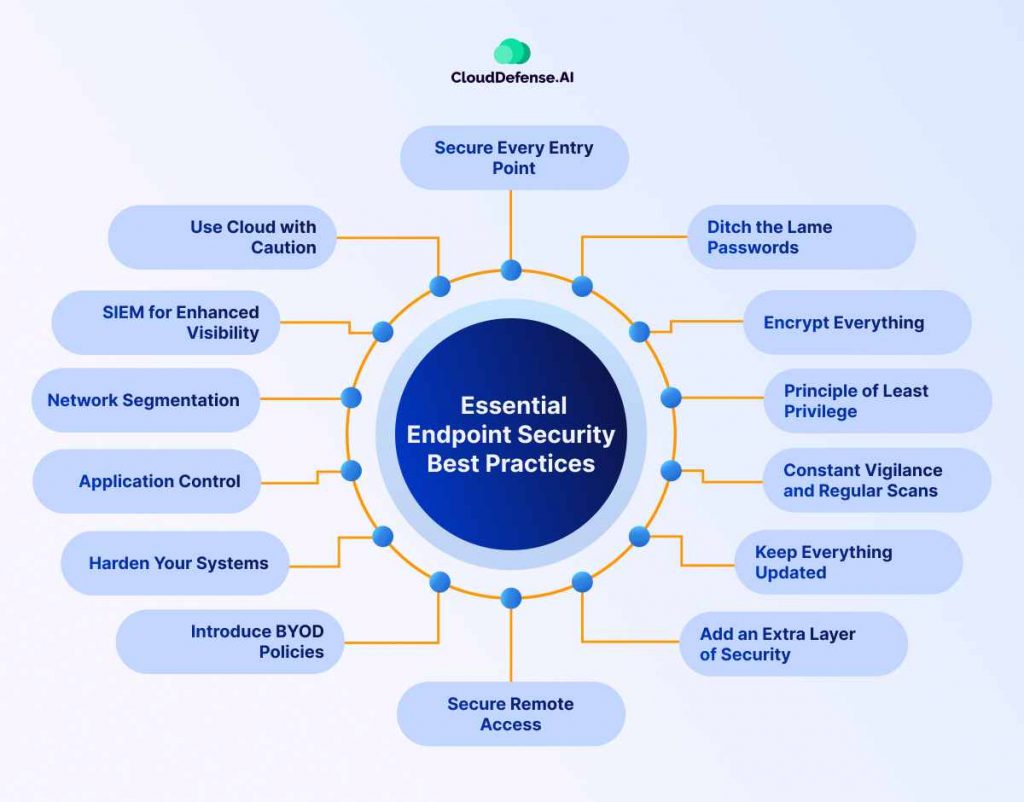
Secure Every Entry Point
Think of all the gadgets connected to your network – laptops, desktops, phones, tablets, even IoT devices. Each one is a potential entry point for cyber attackers. You’ve got to lock them all down with endpoint security software and keep it updated religiously. Cybercriminals love exploiting that one unprotected device you forgot about.
Ditch the Lame Passwords
We all know the struggle of remembering a billion passwords, but using weak ones is the cyber equivalent of leaving your door unlocked. Encourage your team to use strong, unique passwords for every account, combining upper/lowercase letters, numbers, and symbols. And, no more reusing passwords or using dumb ones like “Password123” that a kid could guess.
Encrypt Everything
Data encryption is like wrapping your sensitive info in a cloak of invisibility. Whether it’s sitting on a device, being transmitted, or being stored in the cloud, keep that data encrypted so that even if the wrong person intercepts it, it just looks like an indecipherable thing to them. It’s a must these days.
Principle of Least Privilege
Not everyone needs access to every system or file, so adopt the principle of least privilege access. Only grant employees the bare minimum permissions required to do their jobs. That way, even if someone’s credentials get compromised, the intruder can’t run rampant through your entire infrastructure.
Constant Vigilance and Regular Scans
Schedule regular scans of your endpoints using robust endpoint detection and response (EDR) solutions. These tools can identify and neutralize potential threats before they cause damage.
Keep Everything Updated
Software updates are a real pain, but they’re essential for patching vulnerabilities that cyber jerks love to exploit. Implement automated patch management to ensure every app, operating system, and software component stays current with the latest security fixes and upgrades.
Add an Extra Layer of Security
Logins and passwords alone aren’t enough these days. Enable multi-factor authentication (MFA) to add that critical second or third verification step, making it way harder for bad actors to breach your accounts, even if they manage to swipe some login credentials.
Secure Remote Access
With remote work on the rise, ensure secure connections by implementing a virtual private network (VPN) with strict access controls. This encrypted tunnel prevents people from snooping on your employees’ internet traffic when they’re working remotely.
Introduce BYOD Policies
If you allow personal smartphones, laptops or other devices on the company network through “bring your own device” policies, make sure they meet your organization’s security standards and controls. An infected personal device can put your entire environment at risk.
Harden Your Systems
System hardening is all about reducing your attack surface by disabling unnecessary services, closing unused ports, removing default accounts or passwords, and configuring systems with secure settings.
Application Control
You wouldn’t let a random person wander into your office, so why let any program run willy-nilly on your endpoints? Implement application control (whitelisting/blacklisting) to restrict which apps are allowed to execute, blocking any unapproved or potentially shady software.
Network Segmentation
Instead of having one flat, open network, segment it into smaller zones based on resources, teams or responsibilities. This micro-segmentation approach can contain any breaches and limit lateral movement by hackers looking to spread their attacks.
SIEM for Enhanced Visibility
With so much security data pouring in from all your endpoints, it’s impossible to analyze it all manually. Leverage SIEM (Security Information and Event Management) tools to collect, correlate and make sense of all those logs and events for better threat detection and incident response.
Use Cloud with Caution
While cloud storage and apps are super convenient, don’t get lulled into a false sense of security. Implement tight access controls, audit protections, encryption and other safeguards to prevent data leakage or unauthorized access to your cloud environments. The security is still on you.
Final Words
Implementing robust endpoint security isn’t just another cybersecurity checklist item – it’s an absolute necessity in today’s massively connected world. With more devices accessing your network than ever before, each one represents a potential open door for threats.
By following these endpoint security commandments, you’re basically outfitting every single device with a virtually impenetrable security detail. Advanced malware protection, encryption, access controls, patching, and cloud security—it’s all about creating tight, multi-layered defenses around your exposed endpoints.
Cyber threats are escalating rapidly, and all it takes is one overlooked vulnerability for devastating breaches to occur. Don’t let your organization’s reputation, finances, and data become a cyber road kill. Implement rock-solid endpoint security practices, and you’ll secure your digital assets tighter than Fort Knox. Your business’s survival depends on staying vigilant against the ever-evolving cybercrime landscape.







