Considering the attack-prone digital world we live in, keeping our computers and networks safe is not an easy thing. For years, we’ve relied on good old antivirus software to catch those viruses and malware. But today’s cyberattacks? They’ve leveled up big time – way more sophisticated and sneaky than ever.
That’s where Endpoint Detection and Response (EDR) solutions come in to save the day. But what exactly is EDR, and how does it differ from your trusty antivirus?
Here, we’ll break down the key distinctions between EDR and antivirus, helping you decide which security solution best equips you for the evolving threat front.
What is Antivirus?
Antivirus software has long been the first line of defense for our digital lives. It works by identifying and blocking malicious software (malware) like viruses, worms, and Trojans. Antivirus software relies on a database of known malware signatures, constantly updated to recognize new threats.
The way traditional antivirus works is by scanning files against a database of known malware signatures. If a file matches one of the signatures, the antivirus will quarantine or remove it from your system. Antivirus also monitors real-time activity looking for suspicious behavior that could indicate an infection.
While effective at catching known malware strains, antivirus has some key limitations:
- It can’t detect new, previously unseen malware strains until their signatures are identified and updated.
- It focuses primarily on malware pattern matching rather than analyzing deeper behaviors and attacks.
- It lacks visibility into activity happening across the entire network of endpoints.
- Its response is limited to cleaning up after infections rather than active threat hunting.
These shortcomings leave organizations vulnerable to more advanced and stealthy attack vectors like fileless malware, zero-day exploits, and multi-staged attacks that can easily slip under the radar.
This sets the stage for a new generation of security approaches – Endpoint Detection and Response!
What is EDR?
If antivirus is the first line of defense, EDR (Endpoint Detection and Response) is like having a team of security experts watching your back 24/7. EDR goes beyond simple malware detection. It actively hunts down threats, investigates suspicious activity, and responds to incidents in real time.
Unlike traditional antivirus, which mostly reacts to known threats, EDR is proactive. It’s designed to spot emerging, unknown threats by monitoring behaviors and patterns across all devices in your network. If anything looks off, EDR steps in—either by containing the threat or alerting security teams to investigate further.
Let’s look at a quick breakdown of what EDR means:
- The “Endpoint Detection” part of EDR refers to its ability to detect malicious activity in real-time by analyzing event data, user behavior, and other telemetry from laptops, servers, mobile devices and other endpoints on the network.
- The “Response” component allows security teams to quickly investigate and respond to threats detected on endpoints. This could include containing potentially compromised devices, gathering forensic data, identifying root causes, and surgically remediating issues – all from a centralized management console.
| Read More: If you’re curious about how EDR compares to MDR and XDR, check out our detailed guide on the EDR vs MDR vs XDR. Discover which solution best fits your organization’s needs and how they can strengthen your cybersecurity defense even further. |
Key Benefits of EDR:
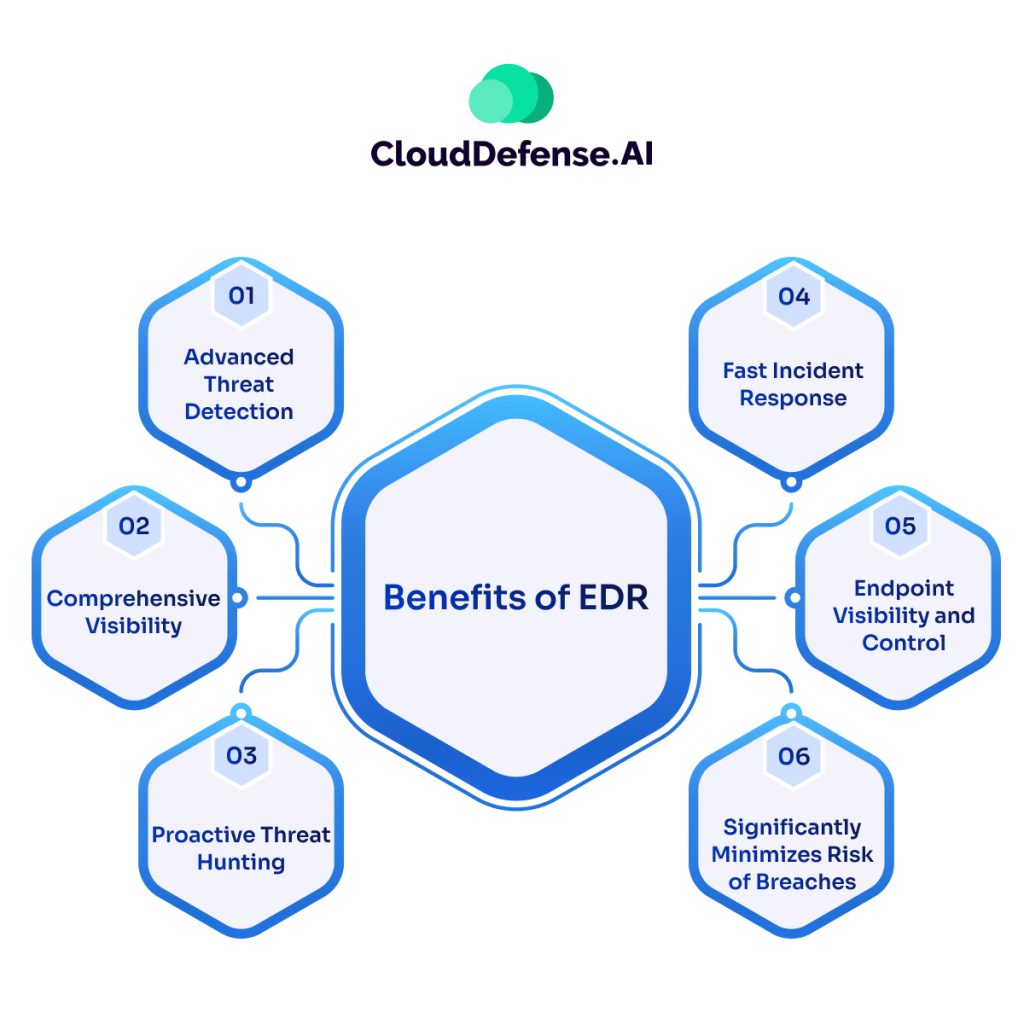
So why should you consider EDR? It’s all about being proactive and staying ahead of threats. Here’s why EDR stands out:
1. Proactive Threat Hunting: EDR isn’t just about reacting to problems—it’s about finding them before they cause harm. It gives your team the tools to actively hunt for threats, preventing attacks from ever happening.
2. Real-Time Threat Detection: EDR doesn’t wait for malware to cause damage. It continuously monitors endpoints, so threats are spotted as soon as they show up—before they can do serious harm.
3. Immediate Action: Unlike traditional antivirus, which just alerts you after the fact, EDR can take action on its own. If something suspicious is detected, it can isolate the device or block the threat immediately.
4. Advanced Threat Detection: EDR can catch more than just the obvious malware. It’s designed to spot complex, sophisticated attacks like ransomware or fileless malware that would slip past traditional antivirus.
5. Better Visibility Across Your Network: EDR doesn’t just protect individual devices. It gives you visibility into the entire network of endpoints, making it easier to track down threats and understand how they spread.
6. Faster Incident Response: With real-time data and automated actions, EDR speeds up response times, helping your security team handle potential breaches faster and with more precision.
How do both methods support cybersecurity defense?
Both antivirus and EDR play important roles in keeping your systems safe, but they each tackle security from different angles.
Traditional Antivirus Software:
- Provides a baseline of protection by scanning for and preventing known malware infections on endpoints based on signature databases.
- Helps stop the spread of widespread viruses, worms, and other commodity malware strains.
- Complements other security controls as part of a defense-in-depth strategy.
- Cleans up systems after malware infections occur through quarantine and removal.
While limited, antivirus continues to play a role in cybersecurity as one preventative layer against common malware threats. However, it lacks advanced detection and response capabilities.
Endpoint Detection and Response (EDR):
- Takes a proactive security approach through continuous monitoring and data collection across all endpoints.
- Uses advanced analytics and machine learning to detect attack behaviors and unknown threat patterns.
- Provides deep visibility into activities across the entire endpoint environment.
Allows for rapid threat prioritization, investigation, containment and surgical remediation.
- Enables threat hunting to proactively identify and respond to stealthy threats or existing compromises.
Together, they’re a powerful combo. Antivirus gives you solid protection against known threats, while EDR provides the extra layer of defense for those harder-to-detect, next-level attacks. Think of antivirus as the shield and EDR as the sword—you need both to really stay ahead of today’s evolving cyber threats
Antivirus vs. EDR: Key Differences
When it comes down to it, antivirus and EDR are two different tools for protecting your devices, and each has its own strengths. Here’s how they stack up against each other:
1. Scope of Protection
Antivirus is mainly focused on preventing and removing known malware—viruses, worms, Trojans, and such. It’s great at catching common threats but doesn’t look much deeper than that.
EDR, however, is more like an all-seeing eye. It monitors everything happening on your devices, from file changes to suspicious activity. It’s built to spot threats that don’t match a signature, like ransomware or advanced malware, which antivirus might miss.
2. Threat Detection
Antivirus relies heavily on a database of known malware signatures. If it finds a match, it takes action. The downside is it can’t detect new or evolving threats until they’re added to that database.
EDR, on the other hand, doesn’t rely solely on signatures. It looks for behavior patterns that indicate malicious activity, even if the threat is brand new or unfamiliar. That means EDR is always hunting for the latest threats.
3. Response to Threats
Antivirus typically reacts to threats after they’ve been detected. It’s great at stopping things like viruses before they can cause damage, but once the damage is done, it’s more about cleaning up.
EDR takes things a step further with real-time action. If it detects something unusual, it can immediately quarantine the affected device or block malicious activity to stop the attack in its tracks.
4. Visibility and Coverage
Antivirus tends to focus on individual devices—your laptop, phone, or desktop—so it’s limited in scope.
EDR provides broader visibility across all your endpoints and network, giving you a more comprehensive view of what’s going on across your organization. This makes it easier to spot and stop attacks that are spreading.
5. Use Cases
Antivirus:
- Ideal for personal devices or small businesses.
- Best for protecting against common, known malware like viruses and Trojans.
- Suitable for users who need basic, straightforward protection without complex configurations.
- Great for everyday consumers who aren’t dealing with advanced or targeted attacks.
EDR:
- Best suited for medium to large organizations or enterprises.
- Perfect for businesses with sensitive data that need comprehensive protection against sophisticated attacks (e.g., ransomware, zero-day exploits).
- Essential for environments with high-value targets or those in regulated industries (finance, healthcare).
- Ideal for proactive, real-time threat hunting and immediate threat response.
- Works well in organizations with distributed endpoints or remote workers, ensuring coverage across all devices.
Here’s the quick summary of the key differences between Antivirus Vs EDR
| Feature | Antivirus | EDR (Endpoint Detection and Response) |
| Primary Function | Block known malware threats | Detect and respond to ALL suspicious activity |
| Detection Method | Signature-based detection | Behavior analysis, anomaly detection |
| Scope | Primarily focused on files and applications | Monitors all endpoint activity (files, network, processes) |
| Threat Focus | Known malware strains | Zero-day attacks, unknown threats, advanced malware |
| Response | Quarantine or remove detected threats | Investigate, contain, and remediate threats |
| Visibility | Limited to scanned files and applications | Comprehensive view of all endpoint activity |
| Alerting | Alerts on detected malware signatures | May generate more alerts due to behavior analysis |
| Management | Typically standalone software | Can integrate with antivirus for centralized management |
| Approach | Reactive – waits for threats to appear | Proactive – hunts for threats |
| Ideal for | Home users, basic network security | Businesses with sensitive data, complex networks |
Cost vs. Value Analysis
Let’s break it down. Antivirus and EDR aren’t just different in what they do—they’re completely different when it comes to cost and value. One’s cheap but limited. The other’s an investment but gives you real protection.
Antivirus: Lower Cost, Basic Protection
- Cost: Antivirus solutions typically follow a subscription-based pricing model, ranging from $20 to $100 per user per year, depending on the features and vendor.
- Value: The value lies in its ability to block common threats like viruses, worms, and Trojans. It’s a cost-effective choice for personal devices, small businesses, or organizations with low-risk environments.
- Limitations: While affordable, antivirus lacks the advanced threat detection, real-time monitoring, and incident response capabilities necessary to combat sophisticated cyberattacks.
EDR: Higher Cost, Comprehensive Defense
- Cost: EDR solutions usually cost between $40 and $150 per endpoint annually, depending on the vendor, features, and deployment scale. Some enterprise-grade platforms may also include additional fees for management, integration, and advanced analytics.
- Value: EDR offers far more than basic malware protection. It continuously monitors endpoints, detects complex attack patterns, and enables rapid incident response. The value lies in its ability to prevent costly data breaches, minimize downtime, and protect sensitive information.
- Long-Term ROI: While the upfront investment is higher, EDR reduces the financial impact of security incidents, making it a more cost-effective solution for businesses with critical data or complex infrastructures.
Which Delivers Better Value?
- For individual users or small businesses with minimal security needs, antivirus provides sufficient protection at a low cost.
- For enterprises, regulated industries, or organizations handling sensitive data, EDR delivers superior value by preventing advanced threats and reducing the risk of costly breaches.
Which One Should You Choose?
Now that you know the key differences, it’s time to think: Which one is right for you?
1. Are you running a small business or just need basic protection for personal devices?
Antivirus might be all you need. It’s simple, effective, and can protect you from the most common malware threats. It’s perfect for individuals or businesses that don’t have a lot of complex security needs.
2. But what if you’re in a larger organization or you deal with sensitive data?
That’s where EDR comes in. If your business is at risk of more advanced threats, like ransomware, insider attacks, or complex, multi-stage breaches, you’ll need something more powerful than antivirus. EDR gives you deeper protection, proactive threat hunting, and the ability to respond to threats in real-time.
3. Are you someone who values peace of mind, knowing you’re one step ahead of attackers?
EDR is designed for that. It’s not just about reacting to threats—it’s about preventing them before they even have a chance to cause damage. If you’re in a highly regulated industry or managing a distributed team, EDR can keep you covered, no matter where you are.
4. Do you need visibility across your entire network of devices?
If your answer is yes, then EDR is your solution. While antivirus works on individual devices, EDR provides a more holistic view, helping you see everything that’s happening across your endpoints and network.
5. Are you trying to stop threats in real-time, rather than waiting for them to happen?
EDR’s ability to act instantly can make all the difference in stopping an attack before it spreads. If you need real-time responses and rapid remediation, EDR is the better choice.
6. Do you have the resources to manage complex security systems?
EDR often requires more expertise and effort to manage compared to antivirus. If you have the team to handle it, EDR offers a higher level of protection. If not, antivirus can still provide solid defense with less overhead.
Conclusion
At the end of the day, the cybersecurity game is getting tougher, and relying solely on traditional antivirus just won’t cut it anymore. Those traditional solutions are still good for basic protection, but we’re facing way more sophisticated threats now.
EDR offers deeper visibility, real-time monitoring, and the ability to investigate suspicious activity – empowering you to be a cyber-detective within your own systems.
So, which solution is right for you? It depends on your specific needs. Antivirus provides a solid base, while EDR offers a powerful upgrade. For many, a combination of both approaches is the most effective strategy.
No matter your choice, CloudDefense.AI is here to bolster your cybersecurity. We specialize in innovative application and cloud security solutions that seamlessly integrate with your existing defenses. Ready to see how CloudDefense.AI can take your cybersecurity to the next level? Request a free demo today and discover how we can help you build a watertight defense against the ever-evolving threats of the digital age.







