If you’re getting used to the maze of modern infrastructure, you’ve probably come across the terms IaC and CaC and thought, “Are these just acronyms for doing the same thing?” Not quite. The difference between IaC and CaC goes beyond mere semantics. It’s all about how you manage your infrastructure and its inner workings.
Keep reading as we’re going to break down the real-world difference between these two approaches to configuration management without overloading you with unnecessary complexity.
What is IaC?
IaC or Infrastructure as Code is a modern approach to building and managing your cloud infrastructure using code, rather than manual configurations. Instead of clicking through endless menus and settings, you describe your desired infrastructure state in human-readable files like JSON or YAML.
These files serve as blueprints or a source of truth, allowing you to provision, configure, and manage your entire infrastructure with just a few clicks or script executions.
Key Benefits of IaC
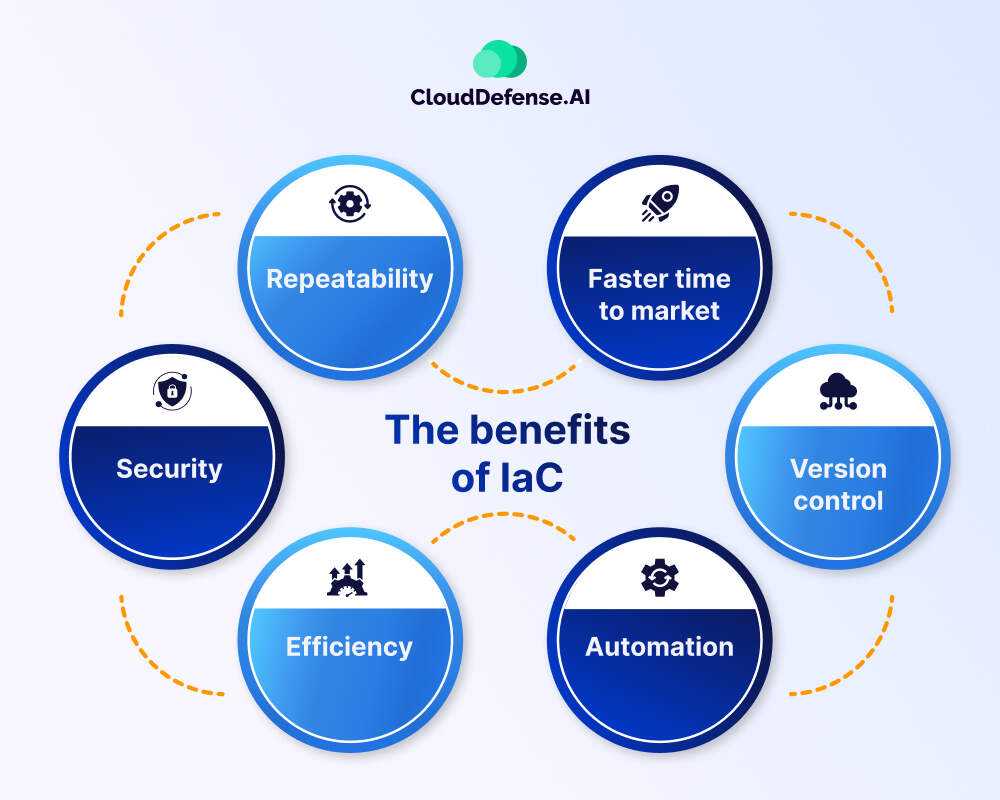
- Repeatability: With IaC, you can create identical environments consistently, reducing human error and eliminating configuration drift.
- Faster time to market: By automating infrastructure provisioning, IaC accelerates application deployment and updates.
- Version control: Just like software code, IaC enables you to track changes, roll back mistakes, and manage infrastructure with precision.
- Automation: Seamlessly integrate IaC into your development pipeline, simplifying deployments and infrastructure changes.
- Efficiency: By automating repetitive tasks, IaC frees up your IT team to focus on more strategic work.
- Security: Codify best practices for compliance and governance, ensuring that your infrastructure is both secure and scalable.
| Read More: Want to learn how to secure your IaC setup? Check out our in-depth article on IaC scanning! |
What is CaC?
While IaC sets up the basic framework of your infrastructure, Configuration as Code (CaC) steps in to fine-tune what’s inside. CaC defines how each server, operating system, and application is configured, ensuring that everything works exactly as intended.
Instead of manually adjusting settings or installing software one-by-one, CaC automates these tasks using tools like Chef, Puppet, or Ansible. Think of it as a set of pre-written instructions or configuration files that tell each system which software to install, what configurations to apply, and how to enforce security policies—all through code.
Key Benefits of CaC:
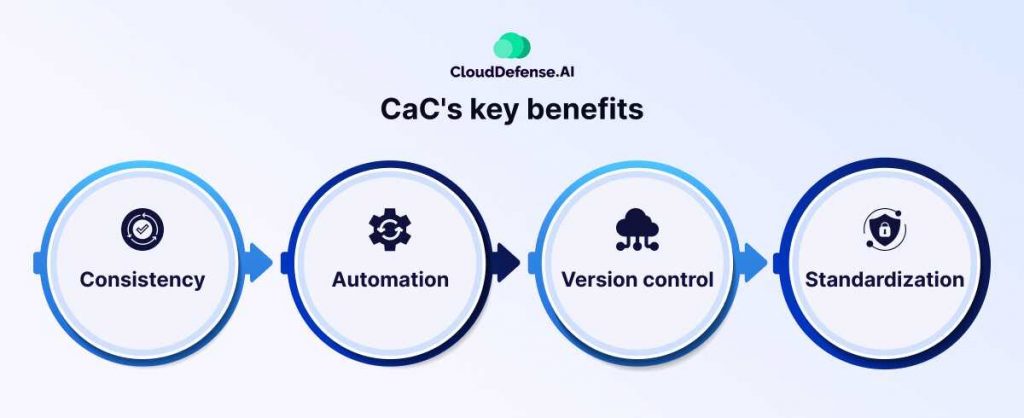
- Consistency: CaC ensures that configuration files remain uniform across all systems, reducing the risk of errors or security gaps.
- Automation: By automating configuration management, CaC eliminates the need for manual tweaks, saving both time and resources.
- Version control: Just like with IaC, CaC allows you to track configuration changes, roll back mistakes, and simplify compliance audits.
- Standardization: With CaC, you can enforce consistent configurations across your infrastructure, minimizing human error and increasing security.
Evolution of Infrastructure as Code (IaC) and Configuration as Code (CaC)
The Early Days: Manual Configurations
Remember when IT teams had to configure each server manually? It was a slow, painstaking process that often led to inconsistencies and human errors. Back then, managing infrastructure involved logging into individual machines and tweaking settings by hand. It worked when you had just a few servers, but as systems grew, this approach quickly fell apart.
Evolution of Cloud Computing
Fast forward to the early 2000s. With the rise of cloud services like AWS, the need for a more scalable and reliable way to manage complex infrastructure became critical. Spinning up servers on demand was great, but how could you manage hundreds, even thousands, of them without losing your mind?
The Birth of IaC
This is where Infrastructure as Code (IaC) comes in. Around the early 2010s, tools like AWS CloudFormation and later Terraform hit the scene. They let teams define their entire infrastructure in code. Instead of manually setting up servers and networks, you could write scripts to do it for you. It was a game-changer, allowing developers to deploy environments in minutes rather than hours or days. IaC became a cornerstone of modern configuration management, making infrastructure scalable, repeatable, and easy to manage.
The Rise of CaC
While IaC was great for building infrastructure, there was still the question of how to ensure everything inside those servers was configured correctly. That’s where Configuration as Code (CaC) steps in.
Tools like Puppet (which launched in 2005) and Chef (2009) allowed you to automate the configuration of software, security policies, and system settings across every machine in your environment. Instead of logging into each machine to manually apply settings, CaC let you define these configurations in source code and push them out across the board.
Why It Mattered
IaC and CaC didn’t just save time—they solved real problems. Teams no longer had to worry about “configuration drift,” where systems slowly became out-of-sync with one another. Everything could be kept consistent and version-controlled. Plus, with automation, it meant fewer late-night emergency fixes because things had gone off the rails.
What We Have Today
Now, IaC and CaC are the backbone of DevOps and cloud strategies. Companies deploy application code, spin up environments, and configure servers faster than ever before. What once took weeks now takes minutes, thanks to the automation brought by IaC and CaC. They’ve become essential in managing modern infrastructure at scale, ensuring not just speed but security and consistency too.
Key Differences Between IaC and CaC
When you start digging into Infrastructure as Code (IaC) and Configuration as Code (CaC), it’s easy to think they’re just two sides of the same coin. Sure, they both automate things, but they have different roles in the world of IT.
Let’s break down what makes each one unique, and why understanding the differences matters.
Purpose
- IaC: Imagine IaC as the blueprint for your entire infrastructure. It’s all about setting up and managing the foundational elements that your applications need—like servers, databases, and networks. IaC’s goal is to create that infrastructure quickly and consistently, so you’re not stuck configuring things by hand.
- CaC: Now, CaC is where the fine-tuning happens. Once your infrastructure is up and running, CaC comes in to make sure each individual piece—servers, applications, and services—is set up just right. Think of it as making sure everything inside your systems is configured properly, from software installations to security settings.
Level of Abstraction
- IaC: IaC operates at a higher level. You can define your infrastructure using code without worrying about all the tiny details. You write scripts that describe what you want, and the IaC tool handles the how. It’s like drawing a map; you don’t need to know every little road, just the main routes.
- CaC: On the flip side, CaC gets into the nitty-gritty. It focuses on the specifics of how each system behaves. With CaC, you’re managing the configurations that control your software and services. It’s essential for keeping everything consistent across different environments.
Tools and Languages
- IaC: When it comes to tools, IaC has some heavy hitters like AWS CloudFormation and Terraform. These tools usually use declarative languages, letting you state what you want your infrastructure to look like without diving into how to get there.
- CaC: For CaC, you’re looking at tools like Chef, Puppet, and Ansible. These often use imperative languages, which means you’ll lay out the exact steps needed to configure a system. This gives you detailed control over the installation and configuration processes.
Workflow Integration
- IaC: IaC typically fits right into the development workflow. Developers can provision environments alongside their application code, making it easy to spin up new setups for testing and deployment. It’s all about speed and efficiency.
- CaC: CaC usually steps in once the infrastructure is established. It ensures that configurations are applied correctly and consistently across all systems, making it a crucial part of ongoing maintenance.
Version Control
Both IaC and CaC leverage version control systems, which allow teams to track changes over time. With IaC, you can easily manage infrastructure changes and roll back if needed. Similarly, CaC enables you to track configuration changes, ensuring compliance and making audits simpler. This version control capability is crucial for maintaining consistency and stability across your environments.
Here’s the table that break down the key differences for you:
| Aspect | Infrastructure as Code (IaC) | Configuration as Code (CaC) |
| Purpose | Acts as the blueprint for your infrastructure, setting up foundational elements like servers and networks. | Focuses on the specifics of software configuration within those systems. Ensures everything runs as it should. |
| Level of Abstraction | Operates at a higher level, allowing you to define your infrastructure without getting bogged down in details. | CaC dives into specifics, focusing on the finer points of how each application or server should behave. |
| Tools and Languages | You’ll see tools like AWS CloudFormation and Terraform here. They let you describe your infrastructure in plain language. | For CaC, think Chef, Puppet, and Ansible. These tools get into the step-by-step process of setting up your systems, making sure everything is just right. |
| Workflow Integration | IaC plays nicely with your development process, allowing you to create new environments quickly and efficiently alongside your code. | CaC usually steps in after the infrastructure is set up, ensuring all configurations are consistently applied across the board. |
| Use Cases | Perfect for managing scalable, repeatable cloud environments, such as spinning up staging environments for testing. | Ideal for precise software component configuration, ensuring consistent setups across development, testing, and production. |
| Focus on Change | Emphasizes infrastructure changes, making it easy to create, modify, and tear down entire environments. | Concentrates on configuration changes, allowing teams to track and roll back settings easily. |
| Consistency | Aims for consistency across the infrastructure, ensuring all resources are set up similarly. | Ensures that configurations remain identical across all environments, reducing errors and discrepancies. |
| Version Control | Leverages version control for infrastructure code, making it easy to track changes and roll back if needed. | Supports version control for configurations, simplifying audits and ensuring compliance with standards. |
| Scalability | Designed for scalability, enabling the rapid creation and management of large environments. | Scales well in terms of configuration management, allowing for consistent application setups across many servers. |
| Human Error Reduction | Reduces human error by automating infrastructure provisioning, eliminating tedious manual setups. | Minimizes human error in configurations, standardizing setups to avoid “it works on my machine” problems. |
Use Cases of IaC and CaC
When you’re stepping into the world of IaC vs CaC, it’s natural to wonder: Which one do I need for my project? The truth is, the choice often depends on your specific goals and the technologies you’re using.
So let’s explore some real-world scenarios together to understand the difference between IaC and CaC, and help you decide which approach fits your needs best.
IaC Use Cases
Let’s say you’re in a modern DevOps environment where you’re working with serverless architectures or containerized applications. Does that sound familiar? If so, IaC might just be the answer you’re looking for. Here are a few situations where IaC really shines:
- Building New Cloud Environments: Have you ever had to spin up cloud infrastructure from scratch? With IaC, you can do this in a snap, using pre-defined configurations to ensure everything is set up consistently. No more manual setup headaches!
- Automating Infrastructure Provisioning: What if you could eliminate the tedious process of manually configuring servers? That’s exactly what IaC can do for you. It speeds up deployments and minimizes the risk of errors, allowing your team to focus on what really matters—delivering value.
- Managing Large-Scale Infrastructure: Are you juggling multiple environments? IaC makes it easy to manage complex deployments, ensuring everything remains consistent across the board. Think of it as your safety net for large-scale operations.
Tools to Consider: If you’re ready to dive into IaC, look into Terraform, AWS CloudFormation, or Azure Resource Manager. Which tool resonates with your project?
CaC Use Cases
Now, let’s shift gears and talk about Configuration as Code (CaC). If you’re focusing on the nitty-gritty details of hardware provisioning and software configurations, CaC might be what you need. Here are some scenarios where CaC comes into play:
- Managing Server Configurations: How do you ensure that every server in your fleet is set up correctly? With CaC, you can define and enforce consistent configurations across all your systems, whether they are physical servers or virtual machines, boosting security and stability.
- Automating Configuration Changes: Have you ever had to roll back a configuration change because it didn’t work as planned? CaC allows you to standardize these changes, making rollbacks smooth and reducing the likelihood of errors.
- Enforcing Security Policies: Are you concerned about security vulnerabilities in your systems? CaC helps you apply security policies consistently, enhancing your overall security posture.
Recommended Tools: If this sounds like the right fit, consider exploring Configuration as code tools like Chef, Puppet, or Ansible. Which one do you think would integrate well with your existing setup?
Combined Use Cases
But wait, why not have the best of both worlds? Many DevOps teams find that using both IaC and CaC together creates a more comprehensive automation strategy. Does this sound appealing to you?
In scenarios where you need to manage both the “hardware” side of things (IaC) and the “software” configurations (CaC), this combined approach ensures everything runs smoothly. Imagine IaC orchestrating your infrastructure while CaC handles the detailed setups of operating systems and applications—talk about a power duo!
How Can CloudDefense.AI Help?
Having explored the different between IaC and CaC in infrastructure automation, let’s talk about something equally important: security. While these tools make your life easier, they can also introduce vulnerabilities if not managed properly.
This is where CloudDefense.AI steps in, providing a comprehensive IaC scanning solution to empower you on your secure infrastructure journey.
So, how does CloudDefense.AI empower you in this critical area? Let’s break it down:
Multi-layered protection
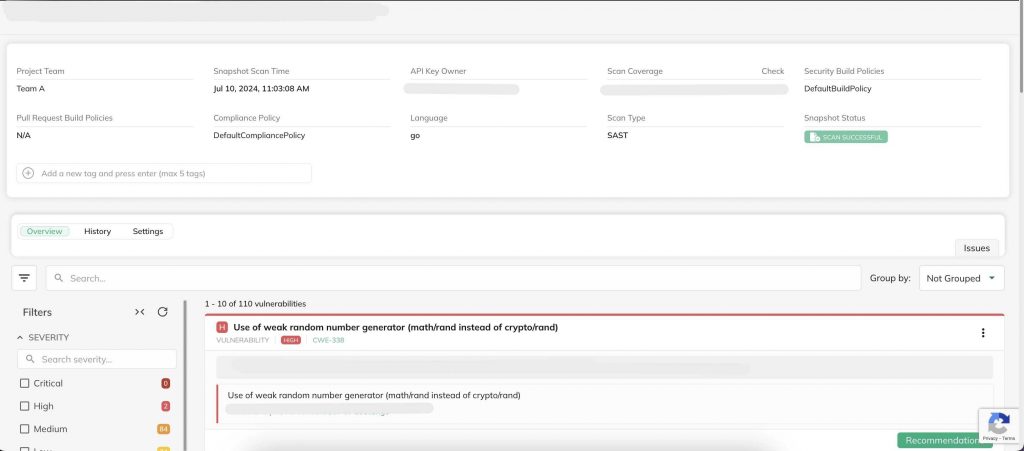
CloudDefense.AI identifies known vulnerabilities within your IaC templates, actively scanning for vulnerabilities, secrets exposed in source code, and misconfigurations that could compromise your infrastructure.
User-Friendly Interface
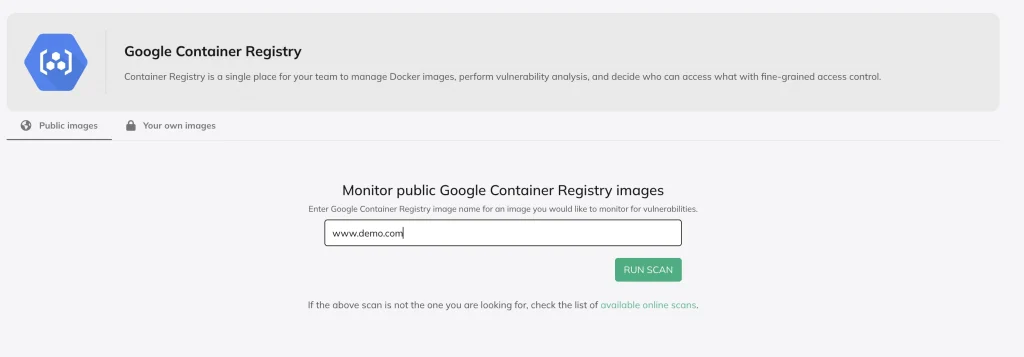
CloudDefense.AI provides a simple, intuitive interface for monitoring vulnerabilities across multiple container registries, including Google Container Registry, Amazon ECR, and Docker Hub. As shown, you just enter the image name and click “Run Scan”—no complex setup required. This user-friendly design empowers all team members, regardless of security expertise, to easily assess and manage vulnerabilities, making security accessible and streamlined for everyone.
Policy enforcement
Ever had a moment where you wished you had a way to enforce security policies across your code? CloudDefense.AI allows you to define and enforce these policies seamlessly. It automatically flags any code that doesn’t comply, helping you prevent potential security risks before they sneak into your production environment.
Risk Prioritization
Not every vulnerability is a crisis. Some can wait, but others can’t. CloudDefense.AI doesn’t just identify issues; it prioritizes them based on the actual risk they pose to your infrastructure. No more wasted energy on low-level concerns when your time is better spent fixing critical flaws. This means you can focus your resources and energy on what truly matters—improving security without running around like a headless chicken.
Compliance made easy
Let’s face it: compliance can be a headache. But with CloudDefense.AI, it doesn’t have to be. The platform helps ensure that your infrastructure adheres to important industry standards like PCI DSS and SOC 2. This means you can streamline compliance audits and reduce risk, making your life a whole lot easier. Who wouldn’t want that?
Unmatched efficiency and accuracy
Managing development speed and security has always been a challenge for developers. CloudDefense.AI’s advanced scanning capabilities allow you to identify and address security issues quickly and accurately. This efficiency not only keeps your projects on track but also ensures that your infrastructure remains secure.
Streamlined workflows
Integrating security into your development process can feel daunting, but CloudDefense.AI makes it seamless. By automating security checks and integrating them into your development pipeline, you can maintain a smooth workflow without sacrificing security. Think about how much more streamlined your processes could be with this kind of support!
Remediation guidance
Finding vulnerabilities is just the first step; knowing how to fix them is crucial. CloudDefense.AI provides clear, actionable instructions on how to remediate any identified issues or misconfigurations. This guidance enables your team to respond quickly and effectively, keeping your infrastructure secure and up to date. How empowering would that be for your developers?
Conclusion
To wrap things up, grasping the difference between IaC and CaC is crucial for anyone looking to enhance their infrastructure and configuration management. While both play vital roles in automation, they can introduce security risks if not handled properly.
That’s why CloudDefense.AI is here to help. With our comprehensive scanning solutions, policy enforcement, and compliance support, you can protect your infrastructure effectively. Curious to see how it all works? Book a free demo today and take the first step toward securing your infrastructure!







