Data breaches are turning out to be costly for companies, with the average cost of a data breach standing at USD 4.45 Million in 2023. Smaller enterprises (SMEs) that cannot withstand the financial burden of breaches end up pulling shutters, as 60% of SMEs go out of business in under six months.
Companies scramble to protect themselves from data breaches. Setting up a robust network security system is essential. Prevention is a cure and the best way to protect oneself from facing the repercussions thrown by threat actors.
Keep reading this article to unlock the secrets you need to know to detect and prevent suspicious network activity.
What Is Suspicious Network Activity in Cyber Security?
Suspicious network activity in cybersecurity refers to unusual or abnormal behavior observed within a computer network that may indicate a potential security threat. This can include unauthorized access attempts, unusual data transfers, communication with known malicious IP addresses, or deviations from established patterns of normal network behavior.
Suspicious network activity can be a precursor to various cyber threats, such as malware infections, data breaches, or network intrusions, making it essential for organizations to have robust cybersecurity measures in place to detect and respond to such anomalies effectively.
Security systems and tools, such as intrusion detection systems (IDS) or firewalls, actively monitor network traffic for anomalies and generate alerts when suspicious activity is detected. Promptly investigating and addressing these alerts is important for identifying and mitigating potential security breaches. You can check some of the examples of suspicious activities here below:
Malicious Database Activity
Unauthorized internal or external changes to the database can cause suspicious activities to pop up. You can identify these activities through changes in users, permissions, and content.
Abuse of User Accounts
Privileged account abuse signals potential insider threats. Look for altered audit trails, shared account access, and unauthorized access to sensitive data as key indicators of such security breaches.
Change in User Access
Unusual alterations in user access patterns often indicate external threats, like hackers exploiting user credentials to breach your network. Watch for anomalies such as off-hour or remote logins, repeated login failures, and inconsistencies between a user’s profile and the associated device, as these may signify security risks.
Configuration Changes
File configuration alterations—replacing, modifying, adding, or deleting—are clear indicators of a data breach. These changes suggest unauthorized network access, revealing an attempt to operate discreetly within your system and emphasizing the potential compromise of sensitive information.
Abrupt Network Changes
Unusual external infiltration attempts manifest in atypical traffic origins, targets, protocol breaches, erratic network performance, and unauthorized scans. Watch for these signs to detect potential security threats and safeguard your network against unauthorized access or compromise.
End Users Detecting Changes
In smaller organizations with limited security measures, end users often observe the initial impacts of suspicious activity. Signs may encompass increased pop-ups, unusual antivirus notifications, sluggish device or network performance, and the appearance of unauthorized toolbars. Stay vigilant to empower users in recognizing and reporting potential security threats.
Why Is Suspicious Network Activity Detection Important?
Spotting suspicious network activity is essential to strong cybersecurity measures. It’s like having an early warning system that catches potential threats before they cause big problems. Detecting unusual things on the network—like weird traffic, protocol issues, or unauthorized scans—helps you act quickly to stop cyberattacks.
This early warning system is crucial for protecting important data from things like viruses and hackers. By closely monitoring how our network behaves, we build a strong defense against cyber threats. It’s like having a security guard for our digital inventory, making sure it stays safe and sound.
How Can We Detect and Prevent Suspicious Network Activity?
Detecting and preventing suspicious activity in cloud applications involves implementing security best practices, tools, and monitoring strategies. Here are some general steps you can take.
Know Your Data
To protect your cloud data effectively, start by understanding its nature, storage location, access methods, and ownership. Classify data based on sensitivity, value, and regulatory compliance, implementing tailored security measures for each category. Map data flows, pinpoint dependencies, and identify vulnerabilities within your data architecture. This proactive approach enables you to apply precise security policies, ensuring a strong defense against potential risks.
Monitor Activity
Ensure cloud data security by routinely monitoring activity logs and metrics. Employ tools that collect, aggregate, and analyze data, alerting you to abnormal or suspicious events. Utilize cloud-native or third-party solutions for tracking user authentication, data access, transfers, changes, and anomalies. Regularly review activity reports and dashboards, promptly investigating any incidents or alerts. This vigilant monitoring enhances your ability to detect and respond to potential security threats efficiently.
Implement Security Measures
Secure cloud data by deploying preventive measures. Employ encryption, masking, or tokenization for data protection in transit and at rest. Implement firewalls, network segmentation, and VPNs to secure networks and communication channels. Utilize identity and access management, multi-factor authentication, and role-based access control to regulate user access and privileges, ensuring robust safeguards against unauthorized actions.
Update Policies
Regularly update policies to align with current architecture and needs. Review and revise data governance, quality, security, and privacy policies to meet business objectives, legal obligations, and industry standards. Communicate and enforce policies organization-wide, offering training and awareness programs for staff and stakeholders to promote compliance and understanding.
Audit for Compliance
Periodically audit your cloud data security using internal or external auditors and automated tools. Assess and verify data security and privacy practices, using benchmarks and feedback to enhance maturity and effectiveness. Document and report audit results, showcasing accountability and transparency in aligning with benchmarks, indicators, and recommended improvements.
Make Use of Experience
Adapt to the evolving landscape by learning from experience. Leverage lessons learned, best practices, case studies, and research findings to enhance cloud data security knowledge. Stay aware of emerging technologies and trends to optimize data architecture and security solutions. Implement feedback loops, continuous improvement, and change management to refine and update data security and privacy strategies, ensuring adaptability and effectiveness.
Finding Suspicious User Logins During Incident Response
To find and stop suspicious network activity it’s like solving a big puzzle. Instead of looking at the whole picture, break it down into smaller questions that you can answer with the information you can see. This helps you understand and tackle the issue step by step using your data.
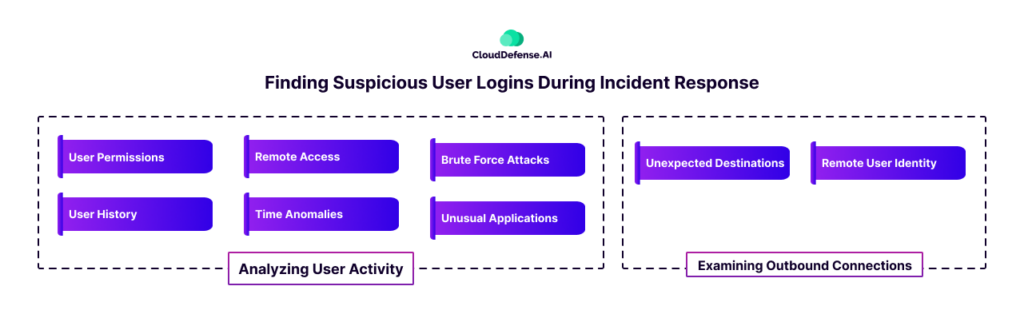
Analyzing User Activity
User Permissions
- Question: Are there users logging in who don’t have a business need to do so?
- Detection: Compare the list of users logging in with those who should have access, identifying potential lateral movement.
User History
- Question: Did a user recently start logging into this system?
- Detection: Determine the first login date for each account, leveraging log files or home directory timestamps.
Remote Access
- Question: Is an expected user remotely logging in from an unexpected system?
- Detection: Understand typical remote login patterns for users and cross-reference with login data to identify anomalies.
Time Anomalies
- Question: Is an expected user logging in at an unexpected time?
- Detection: Analyze historical data to establish normal user behavior and identify deviations, indicating potential account compromise.
Brute Force Attacks
- Question: Are there signs of excessive failed logins?
- Detection: Monitor login logs for patterns of repeated failed attempts, signaling potential brute force attacks.
Unusual Applications
- Question: Are users logging in using unexpected remote access applications?
- Detection: Scrutinize audit logs to identify irregular applications used for logins, indicating potential compromise.
Examining Outbound Connections
Unexpected Destinations
- Question: Are local users logging into unexpected computers from this computer?
- Detection: Identify outbound connections and cross-check them with known user behavior to identify lateral movement.
Remote User Identity
- Question: Did the local user change login names when logging into the remote system?
- Detection: Access remote account information to detect potential multiple compromised accounts.
FAQ
What is the difference between malicious and suspicious activity?
Suspicious activity suggests behavior that raises concern or doubt, warranting investigation. Malicious activity, however, indicates intentional harm or wrongdoing. Suspicion precedes investigation, while maliciousness implies harmful intent.
Is suspicious activity the same for all organizations?
No, suspicious activity varies among organizations due to differing structures, operations, and contexts. What may be considered suspicious depends on individual organizational norms, making it essential to tailor detection strategies to specific environments and risks.
What are the signs of suspicious activity?
Signs of suspicious activity include unusual logins, abnormal access patterns, atypical network traffic, multiple failed login attempts, unexpected application usage, lateral movement, changes in user behavior, unusual outbound connections, suspicious system processes, and altered configurations.
Conclusion
Protection against suspicious network activity is essential in the face of rising numbers of data breaches. Detecting anomalies early, such as unauthorized access or unusual patterns, acts as an effective early warning system. Using effective security measures, monitoring, and regular audits are necessary steps.
You need to understand data, update policies, and learn continuously to efficiently monitor your systems. Detecting and preventing suspicious activity requires a vigilant, adaptive approach, breaking down complex challenges into manageable components for a more effective defense profile.







