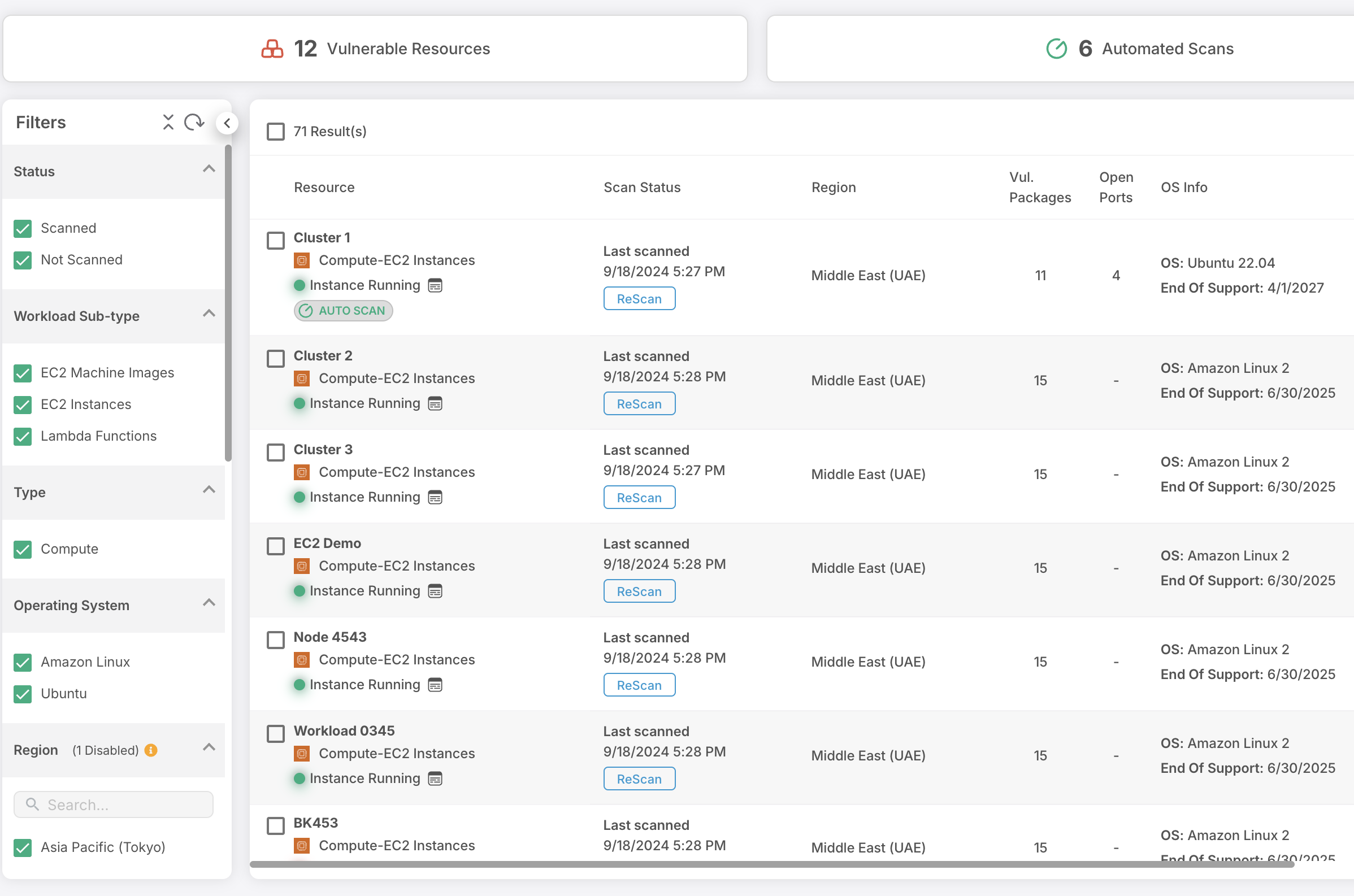
Cloud Workload Protection Platforms (CWPP)
Best-rated Cloud Workload Protection Platform (CWPP)
Trusted by enterprises globally, our platform provides unparalleled protection for your cloud workloads, guaranteeing exceptional defense against ever-evolving cyber threats.
Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
Our Top-notch CWPP Features
Safeguarding Hosts, Containers, and Serverless Environments in Multi Cloud and Hybrid Scenarios
Our cutting-edge agentless cloud workload protection platform ensures total security for diverse cloud workloads across multi cloud and hybrid setups. Gain visibility and protection without compromising performance.

Rapid Risk Identification
Our comprehensive CWPP swiftly pinpoints vital cloud threats, including vulnerabilities, misconfigurations, malware files, and open ports, within minutes.

Data Collection Beyond Limits
Collect data from your cloud setup and runtime storage to provide comprehensive insights into potential risks and vulnerabilities.

Holistic Security Assessment
Our CWPP seamlessly integrates workload-specific intelligence with cloud configuration details, offering you an unmatched, all-encompassing security solution.

Robust Compliance Management
Ensure regulatory and industry compliance with our CWPP, simplifying the process of meeting and maintaining necessary standards.
Our Comprehensive Approach to Cloud Workload Protection Platform (CWPP)
Advanced Cloud Workload Security
Unveil hidden vulnerabilities with our top-tier CWPP. Discover and safeguard sensitive data throughout your cloud infrastructure, even on idle workloads. Identify risks to your most valuable assets and strengthen your defenses.
Vulnerable Packages Detection
Identify all vulnerable packages within your cloud workloads, ensuring proactive mitigation of potential threats.
Malware Files Detection
Uncover malicious files in your cloud infrastructure, providing an extra layer of defense against cyber threats.
Open Ports Monitoring
Monitor and manage open ports in your workloads, reducing attack surfaces and bolstering your cloud security posture.
Severity Prioritization
Classify vulnerabilities as Critical, High, Medium, or Low, enabling efficient resource allocation for remediation.
Vulnerability Type Insights
Easily discern whether vulnerabilities stem from installed applications or the operating system, gaining crucial insights for targeted protection.
Prioritize Cloud Vulnerabilities
Discover and prioritize vulnerabilities across your entire cloud setup with CloudDefense.AI. Our cloud-native CWPP utilizes comprehensive data sources and contextual analysis to pinpoint critical vulnerabilities and ensure rapid response in risk mitigation.
Comprehensive Cloud Inventory
Gain a holistic view of your cloud environment with detailed workload information.
Multi-Source Vulnerability Data
Leverage 20+ vulnerability data sources to identify and assess vulnerabilities accurately.
Contextual Risk Assessment
Move beyond CVSS scores. Understand cloud asset connections and risks for prioritized vulnerability resolution.
Discover and Eliminate Threats with Precision
Safeguard your cloud workloads with our cutting-edge malware detection, employing signature-based, heuristic, dynamic scanning, and genetic signature detection techniques for comprehensive security.
Genetic Signature Identification
Detect related malware using past definitions, enhancing accuracy.
Signature Validation
Match file hashes against a repository of known malware, reinforcing cloud security.
Heuristic Analysis
Probe files extensively to uncover intent, purpose, and potential risks.
Dynamic Inspection
Execute files within a controlled virtual environment to uncover malicious behaviors.
Cloud Runtime Defense
Discover comprehensive runtime defense with our CWPP. Safeguard your cloud-native applications across diverse environments effortlessly. Automate security, unify protection, and empower your SOC teams with rich contextual data for efficient threat identification and response.
Unified Protection
Secure Linux and Windows® hosts, containers, Kubernetes, and emerging technologies from a single solution. Simplify defense management across public clouds, private clouds, PaaS, and serverless platforms.
Automated Enterprise-scale Security
Effortlessly enforce baseline policies for process, file system, and network activity. Achieve robust security across dynamic cloud-native environments through automated measures, reducing manual overhead.
Detailed Forensics for Incident Response
Capture secure and comprehensive forensics data in a timeline view. Enable swift incident response by analyzing data within our CWPP or sending it to other systems for in-depth analysis.
Centralized Console for Runtime Policies
Manage runtime policies centrally with an intuitive console. Ensure consistent security deployment throughout every phase of application development and deployment across all environments.
Threat Tracking and Analysis
Elevate your SOC team's capabilities with contextual data mapped to the MITRE ATT&CK® framework. Simplify threat identification and tracking for ephemeral cloud-native workloads using detailed forensics and rich metadata.