Cloud Security Posture Management (CSPM) and Kubernetes Security Posture Management (KSPM) serve as two crucial components in the modern cloud environment. With the increase in the adoption of cloud technologies and containerization, the requirement to safeguard them is also increasing, and that is where CSPM and KSPM come in.
The main aim of these solutions is to address unique challenges and safeguard different aspects of the cloud infrastructure. While both CSPM and KSPM are tasked with security posture management of an organization’s cloud infrastructure, they have different focuses and utilize various methodologies to address issues.
CSPM is focused on the security and compliance of cloud services and resources, whereas KSPM concentrates only on the protection of Kubernetes clusters. This guide will explore the fundamental comparison of CSPM vs KSPM while shedding light on their focus, functionalities, and various other aspects.
Understanding Cloud Security Posture Management
Definition of Cloud Security Posture Management (CSPM)
CSPM, or Cloud security posture management solution, is a cyber security tool that is designed to help organizations find misconfigurations and compliance issues in the cloud infrastructure.
This security solution is tasked with incident response, implementation of best security practices, automated compliance monitoring, risk assessment, and DevOps integration.
The main focus of the CSPM cloud tool is to automate the process of identifying and addressing all the security issues across the cloud infrastructure, including IaaS, PaaS, and SaaS.
CSPM security helps organizations enforce various frameworks, security policies, and regulatory requirements so that security issues can be proactively discovered and mitigated at the earliest.
It follows a robust assessment process where it assesses and compares the current cloud security and configurations with the best security practices and known security issues and provides a report accordingly. Traditional CSPM solutions give reports to the organization, while some advanced CSPM tools can automatically remediate the problem.
Advantages of Implementing CSPM
Implementing a CSPM solution in your cloud environment will offer you numerous advantages, and it will help maintain the optimum security posture of your cloud. The primary benefits are:
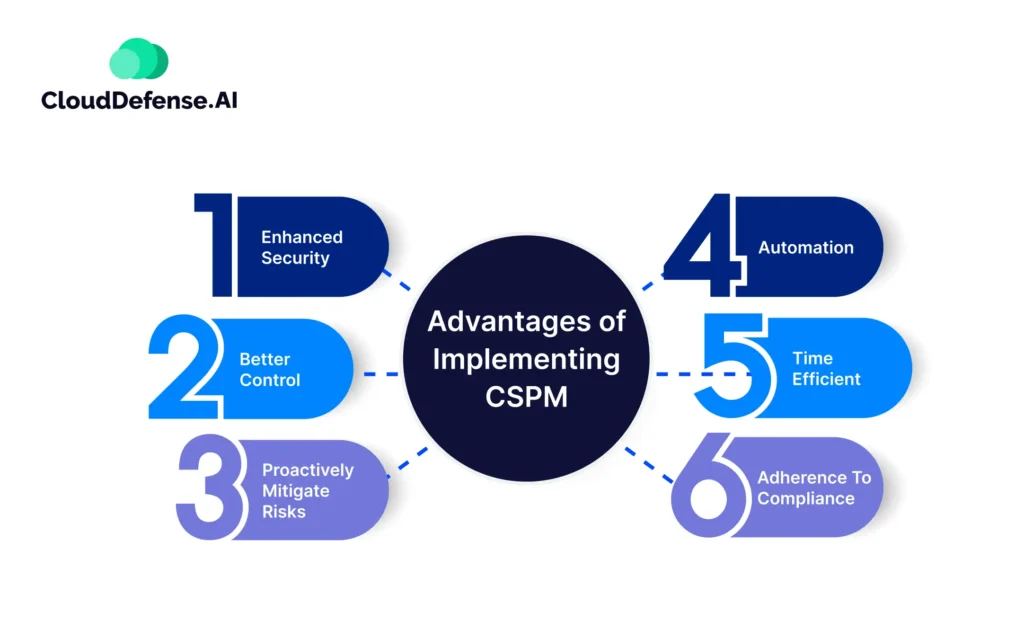
Enhanced Security
With the Cloud security posture management tools, organizations can proactively identify and rectify security issues like misconfiguration, compliance gaps, and vulnerabilities in their cloud infrastructure. It helps in curbing attack surfaces and ensures all the best security practices are implemented.
Better Control
When you use a CSPM solution, you will have the option to manage all your cloud security policies and enforce policies across the cloud environment, whether it is hybrid or multi-cloud.
Proactively Mitigate Risks
The proactive approach of the CSPM tool makes it a handy tool for most organizations because it proactively monitors and assesses cloud infrastructure. It provides alerts to the organization for any kind of security risks and allows them to address those issues before they can cause any threat.
Automation
One of the most significant benefits of CSPM is the automation of monitoring and remediation processes that help organizations streamline security and reduce manual workload.
Time Efficient
With the CSPM solution, you can save a lot of time as it automates a lot of tasks, especially compliance checking, and allows your team to utilize the time for productive tasks.
Since it continuously monitors the cloud infrastructure and provides reports automatically, your team won’t have to invest a lot of time there.
Adherence to Compliance
CSPM will assist your organization in adhering to all the industry-specific standards and regulations by assessing all the cloud configurations against compliance requirements. From GDPR, HIPAA, and SOC 2 to CIS, you won’t have a problem adhering to compliances.
Challenges in CSPM Implementation
Implementing CSPM may improve your overall security posture, but its implementation can pose numerous challenges. Here are the common challenges:
Unable to Stop Attacks
CSPM can not proactively prevent any kind of malware and ransomware attack, which is a massive issue for a security solution. It will only provide reports and require human intervention to prevent such attacks.
Complexity in Implementation
The Gartner CSPM solution is quite complex to implement and configure and requires the support of expert individuals. Your employees might experience a steep learning curve to implement and manage CSPM tools.
Lacks Standardization
A considerable drawback regarding CSPM implementation is that cloud service does not maintain any kind of standardization.
Every provider has their specific configuration and APIs, so it becomes an issue for many organizations to maintain consistent integration in different cloud environments.
Alert Fatigue
CSPM tools provide reports regarding any kind of vulnerability and misconfiguration through alerts or notifications. On a daily basis, they can produce a large number of alerts without prioritization, and this can overwhelm the security team of your organization.
Understanding Kubernetes Security Posture Management
Definition of Kubernetes Security Posture Management (KSPM)
Kubernetes Security Posture Management (KSPM) is a set of practices and tools that helps in automating the identification and mitigation of security and compliance issues across K8s clusters.
It can assess, identify, and enhance Kubernetes security along with containerized workloads associated with it. This security solution takes a comprehensive approach as it is mainly focused on securing the Kubernetes clusters operating in a complex and dynamic environment.
Securing a Kubernetes cluster can be a complex task as there are a lot of components and configurations along with vulnerabilities.
That is where KSPM comes in. It offers organizations all the technologies and processes that ensure all the Kubernetes clusters and resources are configured correctly and securely. KSPM Kubernetes tool continuously scans container images, monitors cluster configuration, looks for potential vulnerabilities, and assesses the runtime behavior of containerized workloads.
Advantages of KSPM Integration
Integrating KSPM into the Kubernetes environment of your organization will provide you with numerous advantages. These benefits are:
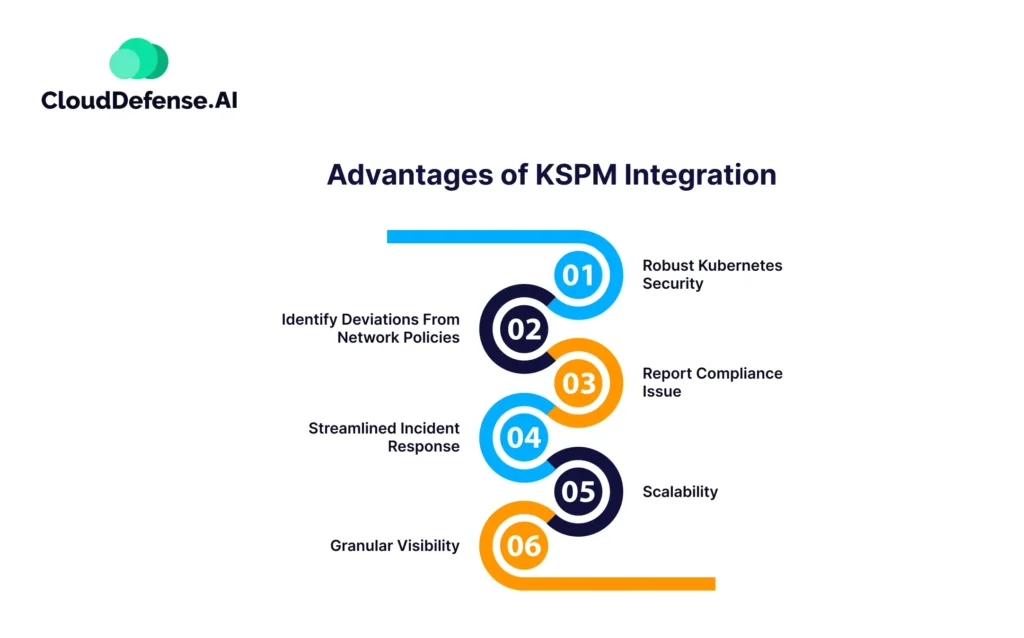
Robust Kubernetes Security
KSPM offers robust security for all your Kubernetes clusters and containerized workloads, making sure it is free from any security issues. It proactively looks for vulnerabilities, misconfigurations, and other issues and addresses them quickly.
Identify Deviations from Network Policies
KSPM can identify deviations from the standard network security policies set by the organization and helps you identify any malicious activity.
It helps ensure systematic network isolation so that only users with proper credentials can access Kubernetes resources.
Report Compliance Issue
Every industry regulation, like HIPAA, ISO, and PCI, has its own set of compliance requirements, and the organization must maintain them. KSPM helps you to adhere to those requirements and also scans for any potential compliance deviation.
Streamlined Incident Response
One of the most significant advantages of KSPM is that it can automate the incident response to any kind of security threat that may arise within the environment. It helps the organization to proactively mitigate threats before they leave any severe impact.
Scalability
As your Kubernetes environment grows, the KSPM tool can scale accordingly and ensure the comprehensive security of your clusters.
The number of containers and clusters in your Kubernetes won’t matter as they can adapt to the increasing number with proper effectiveness.
Granular Visibility
KSPM solution provides you with granular visibility into your Kubernetes clusters and provides you with all the insights and reports. The information it offers helps you make informed decisions and devise your organization’s policy accordingly.
Challenges in KSPM Integration
Like every cloud security solution, KSPM also has many challenges associated with its implementation in the Kubernetes environment. These challenges are:
Complexity in KSPM Integration
It is not easy to integrate KSPM solutions in your Kubernetes environment, and it will require a team to have deep knowledge regarding the architecture along with other aspects. You will need a specialized team who are well aware of the security aspect of Kubernetes.
Complexity with Image Usage
Images are the primary aspect of Kubernetes containers, but images can pose a threat to the security posture of the clusters. To ensure optimum security, organizations must source images from high-quality sources and maintain strong governance using specific registries.
High Resource Usage
KSPM tools have high resource consumption for maintaining security, which hampers Kubernetes clusters’ performance. Not only does the performance get impacted, but also overall operation cost increases.
CSPM vs KSPM: Key Differences Between CSPM and KSPM
Cloud Security Posture Management and Kubernetes Security Posture Management are two critical components of cloud security but with a distinct focus. KSPM is often considered a subset of CSPM, but they are tasked with addressing unique security risks.
To help you understand the differences simply, we will provide the comparison between CSPM and KSPM in a detailed chart:
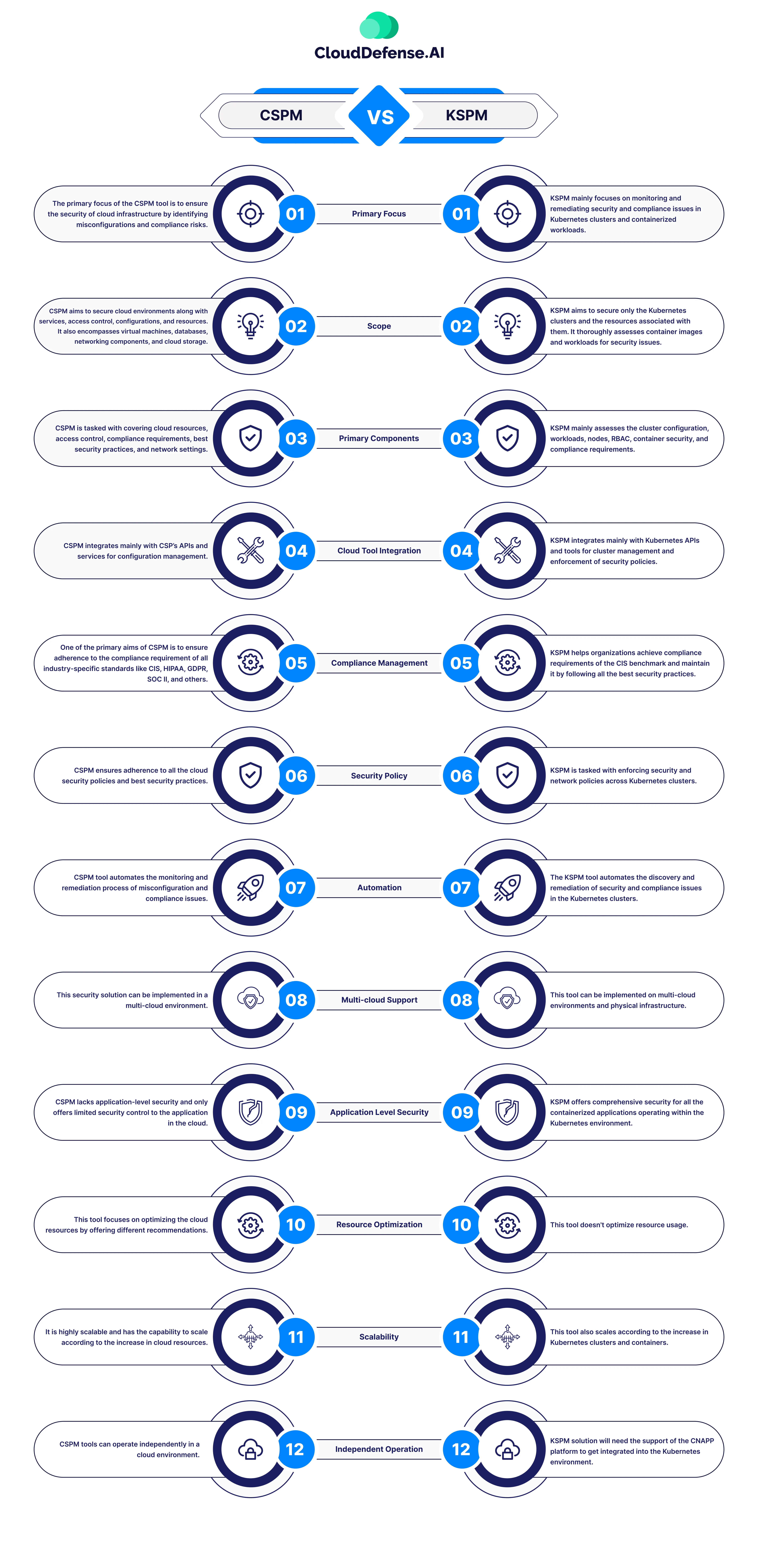
| CSPM | KSPM | |
| Primary Focus | The primary focus of the CSPM tool is to ensure the security of cloud infrastructure by identifying misconfigurations and compliance risks. | KSPM mainly focuses on monitoring and remediating security and compliance issues in Kubernetes clusters and containerized workloads. |
| Scope | CSPM aims to secure cloud environments along with services, access control, configurations, and resources. It also encompasses virtual machines, databases, networking components, and cloud storage. | KSPM aims to secure only the Kubernetes clusters and the resources associated with them. It thoroughly assesses container images and workloads for security issues. |
| Primary Components | CSPM is tasked with covering cloud resources, access control, compliance requirements, best security practices, and network settings. | KSPM mainly assesses the cluster configuration, workloads, nodes, RBAC, container security, and compliance requirements. |
| Cloud Tool Integration | CSPM integrates mainly with CSP’s APIs and services for configuration management. | KSPM integrates mainly with Kubernetes APIs and tools for cluster management and enforcement of security policies. |
| Compliance Management | One of the primary aims of CSPM is to ensure adherence to the compliance requirement of all industry-specific standards like CIS, HIPAA, GDPR, SOC II, and others. | KSPM helps organizations achieve compliance requirements of the CIS benchmark and maintain it by following all the best security practices. |
| Security Policy | CSPM ensures adherence to all the cloud security policies and best security practices. | KSPM is tasked with enforcing security and network policies across Kubernetes clusters. |
| Automation | CSPM tool automates the monitoring and remediation process of misconfiguration and compliance issues. | The KSPM tool automates the discovery and remediation of security and compliance issues in the Kubernetes clusters. |
| Multi-cloud Support | This security solution can be implemented in a multi-cloud environment. | This tool can be implemented on multi-cloud environments and physical infrastructure. |
| Application Level Security | CSPM lacks application-level security and only offers limited security control to the application in the cloud. | KSPM offers comprehensive security for all the containerized applications operating within the Kubernetes environment. |
| Resource Optimization | This tool focuses on optimizing cloud resources by offering different recommendations. | This tool doesn’t optimize resource usage. |
| Scalability | It is highly scalable and can scale according to the increase in cloud resources. | This tool also scales according to the increase in Kubernetes clusters and containers. |
| Independent Operation | CSPM tools can operate independently in a cloud environment. | KSPM solution will need the support of the CNAPP platform to get integrated into the Kubernetes environment. |
Best Practices for Cloud Security Posture Management
CSPM is instrumental in maintaining the optimum security posture of your cloud infrastructure. To achieve this, we have listed some best practices that you can follow.
Get Complete Visibility into Your Cloud
In a cloud environment, sensitive data is regularly processed by different applications and networks in various areas, so it becomes vital to identify and map all the data locations.
You need to use a data security management tool to identify, map, and tag all the sensitive data so that you can monitor all the configuration and compliance issues.
Classifying the Important Assets
It is a wise move to classify all the critical assets according to their importance and risk factors. Classifying the assets will enhance your organization’s security posture because it will help in configuring the remediation process according to the risk priorities.
Enforcing Security Assessment in CI/CD Pipelines
Enforcing security assessment in the CI/CD pipelines will help you to identify security shortfalls early in development and mitigate the risk of the broad attack surface.
You should also create awareness among developers regarding the detection of any vulnerability late in the development process that can cause huge problems.
Applying the Principle of Least Privileges
When weak identity policies are applied while doing new temporary projects, it provides leeway for attackers to gain entry into the infrastructure.
It would be a wise move to apply the POLP, where users with the proper credentials can access an adequate amount of resources that they need for performing a task.
Rectify Security Issues Once Reported
Not all CSPM tools can automate the remediation of security issues, and whenever a security issue is reported, responding to the issue promptly is vital.
When an issue is rectified quickly, it will help prevent the security issue from making any significant impact. Strong encryption should be applied for all the data, and access policies should be implemented to avoid unwanted traffic.
Best Practices for Kubernetes Security Posture Management
It is vital for securing the Kubernetes clusters and workloads as it will safeguard the containerized application from any kind of vulnerability and threat. Here are the best practices you can follow:
Keeping KSPM Policies and Rules Updated
To ensure the KSPM solution can effectively secure all the Kubernetes clusters and resources, you should update the KSPM rules and policies at regular intervals.
The updated policies should cover protection against new security issues and new security features that will upgrade the security posture.
Robust Image Scanning
Container images often carry vulnerabilities, and if not rectified will cause the container to inherit them. Leveraging an image scanning tool can help you scan the base images along with their package and learn whether they are carrying any CVE.
Reducing the Attack Surface
The best way to reduce the attack surface is by utilizing container images that have only the required amount of package needed for the smooth functioning of the container. You can also create a minimal that only has specific packages necessary for functioning.
Categorizing KSPM Vulnerabilities
For security teams of your organization, it can be challenging for them to respond to security incidents without priority because it widens the chance of impacts.
It is best to categorize all the security issues reported during the KSPM scanning process because it will help you to prioritize the problem and address the one having the most impact.
Auditing Cluster Activities
Auditing all the Kubernetes cluster activities and maintaining a log of all the audits can help you mitigate a lot of vulnerabilities before they can make an impact. You can enforce a centralized monitoring and auditing feature that will help you detect all the abnormal activities that can lead to security breaches.
The Future of CSPM and KSPM
CSPM and KSPM are crucial cloud security components that ensure the security and compliance of cloud infrastructure.
As the need for comprehensive security of cloud infrastructure and Kubernetes cluster increases, both CSPM and KSPM will evolve to respond to changing security incidents. Both security solutions will come with enhanced security capabilities and policies that will help them address dynamic customer requirements in the cloud environment.
In the future, CSPM and KSPM will no longer be concentrated in the security team; instead, it will become an organizational tool by providing them with centralized visibility. CSPM is expected to go beyond standard multi-cloud infrastructure and also offer monitoring of different associated platforms and tools.
For KSPM, the orchestration capabilities are expected to increase by a considerable margin. The Zero Trust security model is also likely to get more attention, and both KSPM and CSPM will serve as the main drivers behind it.
FAQ
How often should CSPM and KSPM scans be performed?
The frequency of CSPM and KSPM scans should be performed entirely depending upon the security requirements and compliance obligation of the organization. There is no specific figure regarding the number of scans that an organization should perform.
Can CSPM and KSPM be used in hybrid cloud environments?
In practice, you can effectively use CSPM and KSPM in a hybrid cloud environment as they are highly adaptable to various deployment models.
CSPM will provide you with a broad view of the security posture of your hybrid cloud. In contrast, KSPM will offer robust security management of clusters and also provide a granular view.
What are some popular CSPM and KSPM tools?
Some popular CSPM and KSPM tools that are widely used by organizations are AWS Config, Azure Security Center, Google Cloud Security Command Center, CloudDefense.AI, K-Rail, and K-Rail security insights. Additionally, there are many other tools utilized by businesses of various sizes.
Are CSPM and KSPM compatible with each other?
CSPM and KSPM are not directly compatible with each other due to their different approaches and technologies. However, they have the same aim of securing an aspect of the IT environment.
Conclusion
CPSM and KSPM are essential components of modern cloud security, and even though they are aimed at securing the IT environment, they take a different approach.
In this guide, we have thoroughly explained the comparison of CSPM vs KSPM and help you understand the characteristics of each security solution. Along with the comparison, we have also put forward many other pieces of information that will give you in-depth knowledge regarding CSPM and KSPM.







