Cloud technologies have brought a significant revolution in the information technology industry by providing an extensive option for storage, network, and scaling. Organizations are increasingly relying on cloud infrastructure to store sensitive data and develop applications on them.
However, it has also given rise to many security concerns where malicious actors are finding ways to gain access to cloud-based workloads, data, and applications. To tackle these issues, CSPM and CWPP have come up as two essential solutions in the cloud realm, where each of them is aimed at securing different aspects of the cloud environment.
However, people are often confused between these two, and that is why we have created this guide where we will look at the comparison of CSPM vs CWPP. Before we dive into the key differences between CSPM and CWPP, we want you to go through the following;
Understanding CSPM
Cloud security posture management, commonly known as CSPM, serves as a vital security solution that continuously monitors, manages, and mitigates security issues in a cloud environment.
More precisely, it implements automation to monitor and mitigate any cloud misconfiguration and compliance issues. Automating the security processes provides comprehensive security to the cloud infrastructure where applications, services, and workloads are deployed.
Moreover, automation of security and best security policies helps in continuous adherence to all industry regulations and standards and prevents any breach. The automation level varies from vendor to vendor, where some advanced CSPM tools can automatically solve security issues without requiring assistance.
This security solution provides clear visibility into your cloud infrastructure so you can quickly identify all the issues and maintain a proper security posture throughout. CSPMs are based on a pre-defined set of compliance and security best practices, and they continuously evaluate them against your cloud environment to identify misconfiguration and compliance shortcomings.
By implementing CSPM, your security team will get instant notifications regarding security events, misconfiguration, and compliance issues, which is helpful for quick response. CSPM provides your organization with an integrated interface where all the teams from different domains, like security and operation, can collaborate and efficiently solve issues.
Understanding CWPP
CWPP, or cloud workload protection platform, is a popular security solution that aims to secure all the workloads associated with your organization’s cloud infrastructure.
It provides you with a centralized framework through which it proactively monitors all the workloads, including virtual machines, containers, applications, services, serverless functions, and physical servers included in the cloud.
CWPP delivers many vital features to an organization, and here we will get a CWPP overview of features;
- Vulnerability management: CWPP deploys regular assessments in the cloud infrastructure for security gaps and helps you find vulnerabilities in the cloud. It also provides you with vulnerability prioritization so that your security team can address issues with the highest impact.
- Advanced threat management: CWPP also deploys modern threat intelligence so that it can identify modern cyber threats, including malware attacks and zero-day exploits.
- Different cloud support: Whether you have a hybrid, cloud, or multi-cloud environment, CWPP can proactively protect all your workload across the cloud environment.
- Compliance support: CWPP configures the cloud workloads in such a way that it follows the best security practices and policies that help maintain compliance with industry standards and regulations.
- Centralized view: Through CWPP implementation, you get a single interface using which you can monitor the security of your entire cloud environment. It helps you to address security issues in different cloud platforms through a single platform.
- Real-time incident response: CWPP provides you with alerts regarding risks in real time and also offers forensic capabilities. Thus helping security teams to assess and solve security issues in real-time.
Key Differences Between CSPM and CWPP
The primary motive of CSPM and CWPP may be cloud security, but they are pretty different from each other. Here, we will take a peak at the comprehensive CSPM vs CWPP comparison chart;
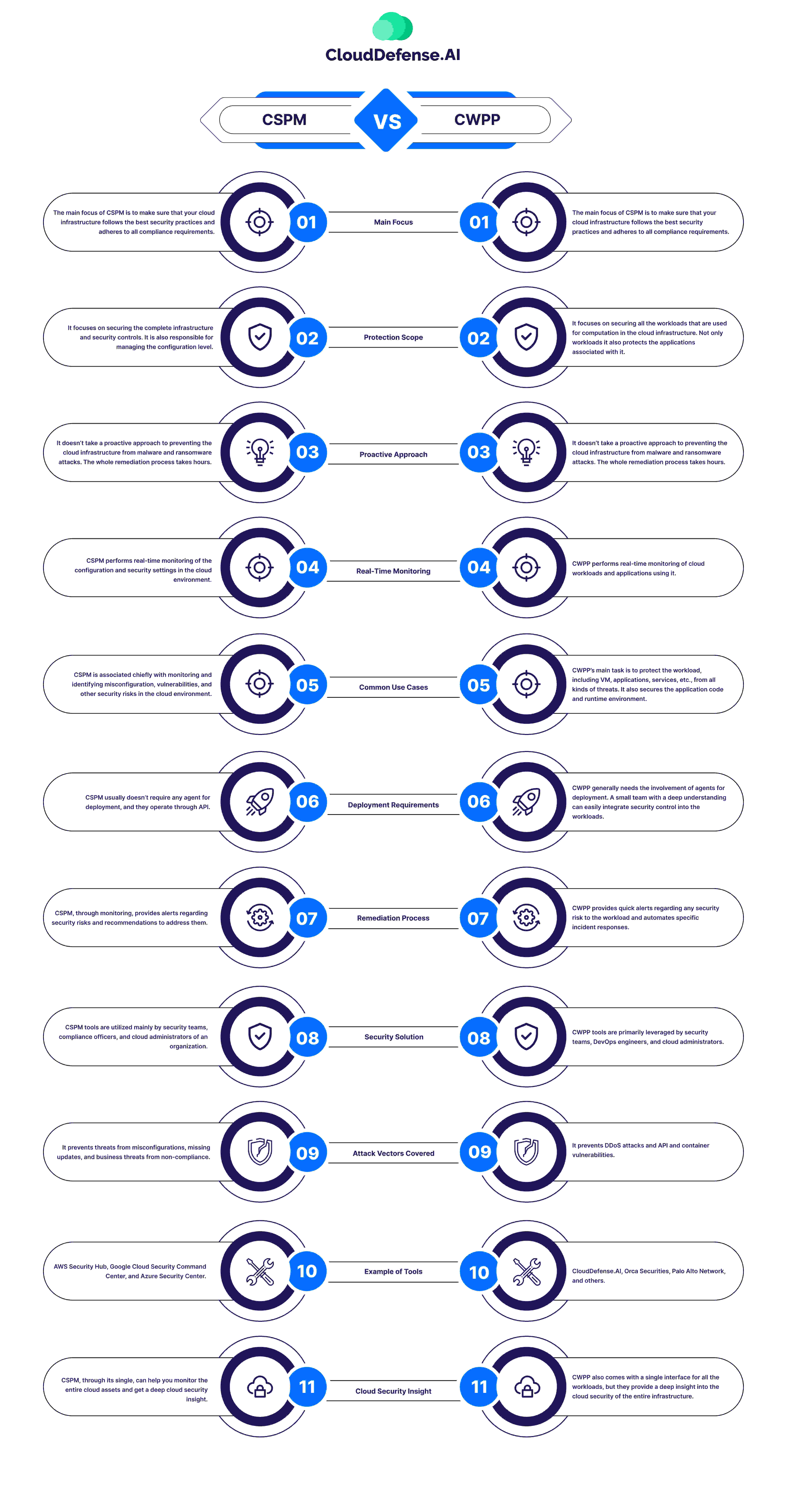
| Cloud Security Posture Management | Cloud Workload Protection Platform | |
| Main Focus | The main focus of CSPM is to make sure that your cloud infrastructure follows the best security practices and adheres to all compliance requirements. | The primary focus of the CWPP is to provide protection to the workloads and applications associated with it running in the cloud environment. |
| Protection Scope | It focuses on securing the complete infrastructure and security controls. It is also responsible for managing the configuration level. | It focuses on securing all the workloads that are used for computation in the cloud infrastructure. Not only workloads it also protects the applications associated with it. |
| Proactive Approach | It doesn’t take a proactive approach to preventing the cloud infrastructure from malware and ransomware attacks. The whole remediation process takes more than 7 hours. | It takes a proactive approach when it comes to addressing any type of malware and zero-day exploit. It uses advanced threat intelligence to help security teams solve them as soon as possible. |
| Real-Time Monitoring | CSPM performs real-time monitoring of the configuration and security settings in the cloud environment. | CWPP performs real-time monitoring of cloud workloads and applications using it. |
| Common Use Cases | CSPM is associated chiefly with monitoring and identifying misconfiguration, vulnerabilities, and other security risks in the cloud environment. It also continuously assesses security and checks compliance with industry standards and regulations. | CWPP’s main task is to protect the workload, including VM, applications, services, etc., from all kinds of threats. It also secures the application code and runtime environment. |
| Deployment Requirements | CSPM usually doesn’t require any agent for deployment, and they operate through API. | CWPP generally needs the involvement of agents for deployment. A small team with a deep understanding can easily integrate security control into the workloads. |
| Remediation Process | CSPM, through monitoring, provides alerts regarding security risks and recommendations to address them. Some advanced CSPM tools also automatically remediate issues. | CWPP provides quick alerts regarding any security risk to the workload and automates specific incident responses. |
| Users of The Security Solution | CSPM tools are utilized mainly by security teams, compliance officers, and cloud administrators of an organization. | CWPP tools are primarily leveraged by security teams, DevOps engineers, and cloud administrators. |
| Attack Vectors Covered | It prevents threats from misconfigurations, missing updates, and business threats from non-compliance. | It prevents DDoS attacks and API and container vulnerabilities. |
| Example of Tools | AWS Security Hub, Google Cloud Security Command Center, and Azure Security Center. | CloudDefense.AI, Orca Securities, Palo Alto Network, and others. |
| Cloud Security Insight | CSPM, through its single, can help you monitor the entire cloud assets and get a deep cloud security insight. | CWPP also comes with a single interface for all the workloads, but they provide a deep insight into the cloud security of the entire infrastructure. |
Benefits and Challenges of CSPM and CWPP
Both CSPM and CWPP have their own sets of benefits and challenges. To get a broad idea regarding the difference between CSPM and CWPP, it is essential we should understand their pros and cons.
Benefits of Cloud Security Posture Management
Here are some crucial benefits of CSPM:
- Continuous monitoring: CSPM, through automation, continuously monitors and assesses your cloud environment to ensure it adheres to compliances and is free from misconfiguration.
- Automatic remediation: Many advanced CSPM solutions can automatically remediate any misconfiguration and deviation from best practices to maintain a security posture.
- Comprehensive visibility: CSPM provides your security team complete visibility into all your cloud infrastructure and guides them to monitor security risks. It allows all teams to assess whether the cloud environment adheres to security policies.
- Saves capital: CSPM enables an organization to optimize its cloud infrastructure and prevents it from spending money on additional resources. It also allows the team to work collaboratively to identify security risks and avoid costly data breaches.
- Complete scalability: One of the most significant benefits of this security solution is that it is entirely scalable and enables organizations to scale their business by scaling the security posture. With CSPM in place, organizations can add services and applications without worrying about security.
- Promotes collaboration: CSPM, through its single interface, allows security and operation teams to work collaboratively toward addressing security risks and policies.
Challenges of Cloud Security Posture Management
Like other solutions, CSPM is plagued by many challenges, and they are;
- Automatic remediation issue: CSPM, through automated remediation, may solve problems quickly, but it can lead to some future issues. Moreover, there are misconfigurations that require human intervention for effective remediation.
- Lacks proactive approach: A significant drawback is that, in practice, CSPM doesn’t take a proactive approach to prevent malware and ransomware attacks. It takes several hours to identify and mitigate the attack.
- Doesn’t have vulnerability scanning: There are some CSPM tools that might not provide you with vulnerability scanning and depend on third-party security tools. This lack can cause complexity in the deployment process.
- Skill gap: If all your teams don’t have the same level of cloud security expertise and don’t have a deep understanding of CPSM, then it will get complex for you to manage CSPM tools. It would lead to inefficient usage and may require additional resources.
Benefits of Cloud Workload Protection Platform
CWPP is widely preferred by every cloud organization, and it is due to the benefits it has on offer. These CWPP advantages are;
- High agility: CWPP integrates directly into the DevOps CI/CD pipeline and secures the application during the development along with its workloads. It conducts a vulnerability assessment process and identifies issues throughout the application’s lifecycle.
- Tailored security controls: Workloads come with specific security requirements, and the CWPP solution enables you to cater to such provisions. It allows you to integrate tailored security control to protect the workloads from any kind of security threats and breaches.
- Total visibility to multi-cloud infrastructure: CWPPs provide you with a single platform to implement security solutions across all the cloud infrastructure. It helps you and your team monitor the security of the workload spread across all the cloud environments and mitigate any threat through a single point.
- Low implementation cost: Many CWPP solutions come with usage-based billing that allows the organization to make huge savings. Moreover, it is often implemented by an agentless platform, so you won’t have to spend on resources to integrate CWPP in your cloud.
- Adherence to compliance: Adhering to compliance is a daunting task for many organizations, but CWPP makes it easier for you. It automatically scans for compliance violations and deviations from best practices in workload security and implements controls to maintain compliance.
Challenges of Cloud Workload Protection
Despite having so many benefits, CWPP also face many challenges and they are;
- Lacks insight into the control plane: CWPP only gives you visibility across your cloud workload and nowhere else. Due to this, you will bring additional security solutions to get insight into the control plane.
- Partial coverage: Since cloud workloads are distributed across different cloud environments, it becomes daunting to deploy agents everywhere, and this leads to blind spots. It is being said that only half of the cloud assets are covered by CWPP.
- Lacks later movement risk detection: CWPP can’t get visibility in the cloud configuration, and this leads to their inability to find issues with the cloud infrastructure layer.
- Inability to perform IAM functionality: Almost every CWPP solution is unable to perform identity tracking and access management functionality. Moreover, they don’t provide cloud risk management, which requires you to include additional security tools, leading to high implementation costs.
Best Practices For CSPM and CWPP
Both CSPM and CWPP serve as primary pillars of modern cloud security, and it is imperative that CISOs should ensure that best practices are used for CSPM and CWPP. Here we will take a look at some best practices you can follow;
Best Practices for Cloud Security Posture Management
Let’s take a look at some of the best practices for CSPM;
- Properly declare the security responsibilities: While implementing CSPM, it is essential you should define the cloud security responsibilities so that there are no gray areas that can lead to security issues.
- Configuring CSPM tool for real-time alerts: CSPM should be configured in such a way that it offers real-time alerts for all types of security risks and policy violations identified by the tool. It is significant for quick remediation and mitigating the chance of any security breach.
- Automate compliance with security standards and regulations: It is vital to automate your organization’s cloud security policies and controls to align them with the security standards and regulations you want to stay compliant with. You should consider the dynamic aspect of the cloud object while automating the compliances.
- Enforce the least privilege access: One of the best security practices for CSPM is to implement the PoLP to make sure users and services are allotted with the necessary permission required to perform tasks. None of the users or services should be granted with over-access.
- Implementing IAM: While implementing CSPM, you should also implement identity and access management policies to manage the access of your cloud resources.
Best Practices for Cloud Workload Protection Platform
Here are some best practices for CWPP that you can follow;
- Asset inventory: You should always maintain an up-to-date inventory for all the workloads in your cloud, including all the dependencies because it is vital to protect them. Through CSPM, you can monitor them and prevent any breach.
- Implement continuous monitoring: It is vital that you implement continuous monitoring of the workloads through CSPM. It is beneficial for detecting security risks and mitigating issues in real-time.
- Maintain patch management: You should maintain an effective patch management process to keep all the workloads updated with the latest security patches. This will be highly helpful for CWPP to ensure the protection of the workloads across the multi-cloud infrastructure.
- Maintain logging and monitoring: To ensure CWPP works effectively, you should maintain logging and tracking of all the workloads in your cloud. You should keep a record of all the security events and assess them to detect potential threats that can jeopardize the workload.
- Periodic review and audits of the CWPP implementation: Perform systematic reviews and audits of your CWPP implementation to check CWPP effectiveness in the cloud workloads. It is needed due to the evolving cloud landscape and increasing threats to cloud workloads.
FAQ
What is the difference between CWPP and CSPM?
The main difference between CWPP and CSPM is that the former is focused on securing the cloud infrastructure, whereas the latter is focused on safeguarding the cloud workload.
CWPP looks after the cloud infrastructure and monitors its adherence to regulatory compliances and best security practices. On the other hand, CWPP makes sure no vulnerability would exploit the workload.
What is a CSPM?
Cloud security posture management is a security solution that is designed to enable organizations to assess and manage the security posture of the cloud environment. It provides complete visibility into your cloud infrastructure and helps you evaluate whether the security control follows all the best practices and regulatory compliances.
What is CWPP in cloud security?
Cloud workload protection platform in cloud security is essential as it helps the organization secure the cloud workload along with the associated application. CWPP hardens the cloud security of an organization by delivering consistent security control and securing all the physical machines, VMs, containers, and other workloads.
Conclusion
The cloud security comparison of CSPM vs. CWPP will give you an in-depth idea regarding the two cloud security tools. We have compared them in every aspect possible, including CSPM vs. CWPP features, to tell how they are different from each other. Even though they have different scopes, both of them play an important role in cloud infrastructure security, and it is vital to implement them both.







