On May 28, 2024, Live Nation Entertainment, the parent company of Ticketmaster, confirmed a data breach that affected over 560 million users. The breach, first exposed by the hacking group ShinyHunters, highlighted severe vulnerabilities in third-party cloud services such as Snowflake. This case has been a crucial study for companies that showcased how a lack of proper security measures can put large amounts of data at risk.
Timeline of the Breach
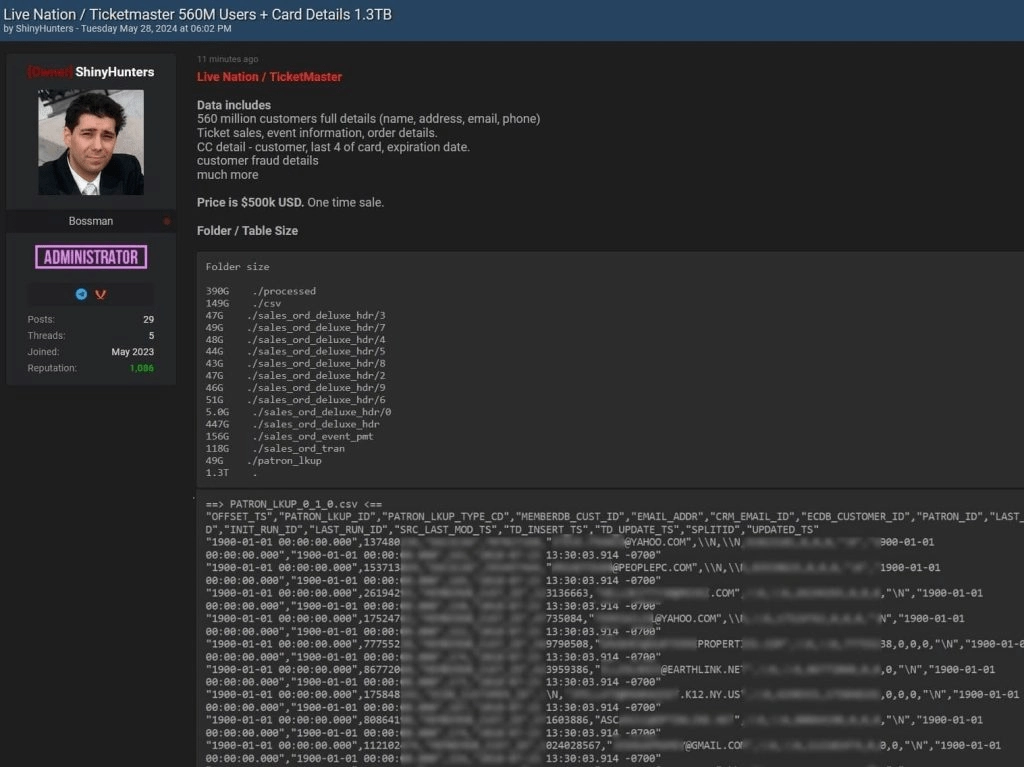
The breach was uncovered only after a cybercriminal group called ShinyHunters listed a massive stash of data for sale on Breach Forum. Let’s take a look at how the breach unfolded in a series of events:
- May 20, 2024: Live Nation discovered unauthorized activity within a third-party cloud database environment.
- May 27, 2024: ShinyHunters offered 1.3 terabytes of stolen data for sale on Breach Forums for $500,000.
- May 28, 2024: Media outlets reported the breach, bringing it into public awareness.
- May 29, 2024: Live Nation confirmed the breach in a filing with the U.S. Securities and Exchange Commission.
- May 30, 2024: ShinyHunters offered Santander customer and staff data for sale, indicating a broader supply chain attack involving Snowflake.
How Did the Breach Occur?
The Ticketmaster breach occurred due to a compromise in a third-party cloud-based data storage and analytics service called Snowflake. Security researchers traced the breach back to EPAM Systems, a Belarusian-founded contractor working with Snowflake customers. Hackers initiated a spear-phishing attack on an EPAM employee in Ukraine, installing info-stealer malware on the employee’s computer.
This malware captured unencrypted usernames and passwords stored in a project management tool, allowing the hackers to access Snowflake accounts without multifactor authentication. Using these credentials, the hackers siphoned off vast amounts of sensitive data, including the personal and payment information of Ticketmaster users.
Mandiant, the security firm Snowflake hired to investigate, revealed that old credentials stolen in previous info stealer malware attacks were used. This highlighted lapses in credential management and security protocols of companies that included Ticketmaster and Santander.
What Kind of Data was Stolen?
A huge amount of sensitive data was stolen and put up for sale by ShinyHunters. The data included both personal and financial information that was stolen due to the presence of vulnerabilities in the infrastructure of the victim companies. Here is a list of the types of data compromised in the breach:
- Personal Information: That included full names, addresses, email addresses, phone numbers, and event and transaction details of customers:
- Ticket sales information: Event details and order information.
- Payment information: Partial payment card data, names, last four digits of card numbers, and expiration dates of customer cards.
What Can We Learn from This Breach?
The Ticketmaster breach can be used to receive important lessons on cybersecurity. First, it brings forth the risks of relying on third-party cloud providers and contractors. This breach shows why strong security measures and regular audits of third-party services are essential.
It also points out the importance of using multifactor authentication, which could have provided an extra layer of security beyond just usernames and passwords. Furthermore, the breach reveals the dangers of poor credential management, such as storing passwords in plain text on employee systems and not updating them regularly.
This case also helps to emphasize the need for proactive threat monitoring, showing us the importance of a thorough and vigilant approach to effectively secure the cyberspace.
Could This Breach Be Averted?
Stronger security measures could have prevented the breach from occurring. Critical steps such as implementing multifactor authentication across all access points, encrypting sensitive credentials, and ensuring regular security audits of third-party services could have helped in avoiding this embarrassing situation. Moreover, using a CNAPP like CloudDefense.AI could enhance the security posture and give a clearer view of the activities on Ticketmaster’s network.
CloudDefense.AI’s CNAPP contains tools such as DSPM that provide a more unified and data-driven approach to allow organizations to protect their data effectively. By using real-time insights into potential threats provided by DSPM, companies such as Ticketmaster could prioritize security tasks effectively and allow for informed decision-making across the cloud environment.
Most importantly, CloudDefense.AI’s DSPM allows the integration of advanced analytics and unifying data from various sources, providing a more detailed view of the cloud security posture. Solutions like these help prevent data security risks that could have helped Ticketmaster identify vulnerabilities and respond to threats before a breach occurred.
Final Words
The Ticketmaster data breach remains a witness to how companies should start investing in strong cybersecurity measures, especially when dealing with third-party cloud services. Organizations must take a proactive approach to security, using advanced tools and best practices to protect sensitive data and minimize the risk of cyberattacks. Cloud security tools such as CloudDefense.AI’s DSPM should be utilized to ensure the most important asset, sensitive data, stays secure.







