Without a doubt, the cloud has become a go-to choice for most organizations to offer products and services to customers. According to Gartner, by 2022 almost 60% of businesses have moved from physical infrastructure to cloud environments.
As cloud adoption has increased, so does the increase in misconfiguration. Cloud misconfiguration is one of the most common cloud security issues in the cloud computing realm. A McAfee report has suggested that a large organization faces around 3,500 misconfiguration incidents on a monthly basis.
Despite implementing a large number of cloud security solutions, misconfiguration is still a prevalent issue in modern times, and it leads to security breaches, data leaks, service disruption, and other issues. In this guide, we are going to discuss the most common misconfiguration on the cloud that you need to consider to improve your security posture.
What are the Cloud Misconfigurations?
Cloud misconfiguration is one of the leading security issues in the cloud environment, and it has been affecting organizations for years. The misconfiguration meaning usually refers to the glitches, gaps, errors, and other unintended errors that occur when cloud resources are not correctly configured.
When the cloud configuration doesn’t adhere to industry regulatory standards and best security practices, it leads to cloud misconfiguration and occurs in both private and public cloud environments. Misconfiguration in the cloud heavily affects various cloud security models, including IaaS, SaaS, and PaaS. Cyber threats that arise due to misconfiguration come in different forms, like security breaches, ransomware, malware, and insider threats.
Even though these security issues are not highly sophisticated, still the occurrence is more than expected. Detecting and remediating these cloud misconfigurations is a complicated human task as it involves complex security controls and multi-cloud environments. A report by OWASP suggested that around 4.5% of cloud applications are configured in such a way that it leads to vulnerability.
The Impact of Cloud Misconfiguration
The impact of cloud security misconfiguration is pretty immense, and it significantly affects the modern cloud environment in many ways. Zscaler’s security reports have stated that 98.6% of organizations in the world have severe concerns regarding cloud misconfiguration. Let’s discuss the impact it has on organizations;
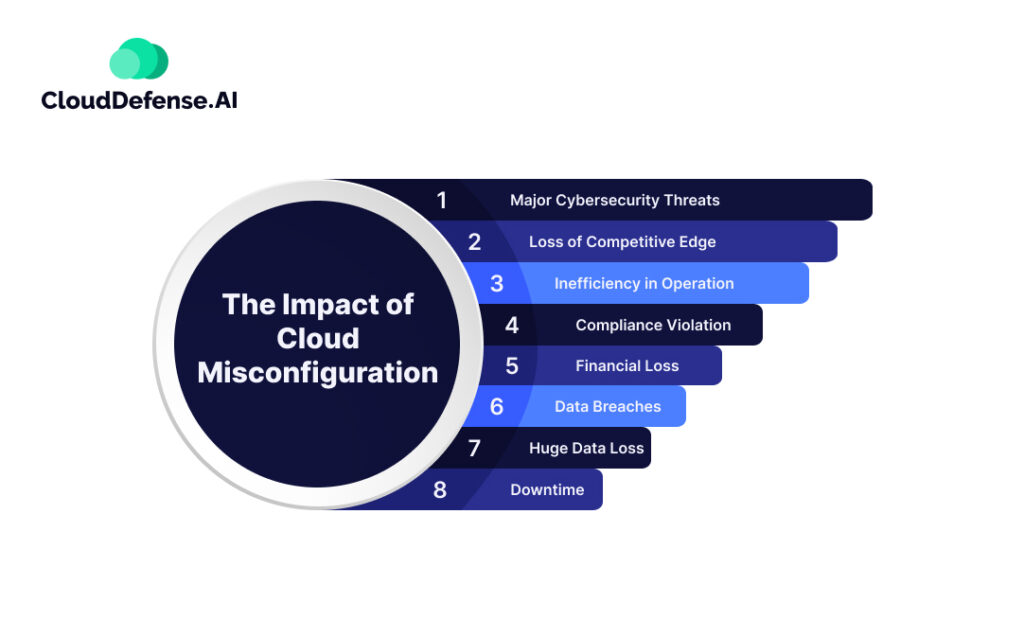
Data Breaches
Misconfiguration in the access control of the cloud environment leads to serious damage as it makes the system utterly vulnerable to exploitation. Malicious actors can quickly gain entry into the infrastructure and gain access to sensitive data, leading to serious cloud misconfiguration breaches.
Huge Data Loss
Another vast impact misconfiguration incurs is enormous data loss. When the cloud storage and backup options are not correctly configured, many data are irretrievably overwritten or deleted, leading to severe loss of critical information.
Compliance Violation
Poor configuration in the storage solutions and access controls also leads to non-compliance with standard industry regulations. Many industries follow strict regulations when it comes to data security, and failing to adhere to GDPR, HIPAA, or CCPA can result in penalties and legal actions.
Financial Loss
If your cloud access controls, security settings, and storage solution are inefficiently configured, then it will have an impact on your cloud resource usage. Misconfiguration causes overconsumption of cloud resources, resulting in inflated cloud service bills.
Downtime
In a cloud infrastructure, a misconfiguration in-network or storage settings can cause severe service outages or downtime. When disruption occurs in the business operation, not only does it affect your customer satisfaction and the organization’s reputation, but it also leads to a loss in revenue.
Inefficiency in Operation
Due to misconfiguration, your organization may face difficulty in efficiently managing and scaling the business operation. Teams might have to manually intervene in various areas to maintain smooth functioning, which ultimately leads to operational overhead and poor agility.
Major Cybersecurity Threats
Misconfigured cloud resources are highly vulnerable to exploitation by cyber criminals, and by gaining access, they use the resource for other purposes. Cybercriminals often inject malware or launch ransomware attacks once they exploit the misconfiguration.
Loss of Competitive Edge
Organization suffering from cloud misconfiguration often lose their competitive edge over their competitors in the market. Since it incurs inefficiency and service disruption, customers may lose their trust and move to other organizations offering better cloud security.
13 Most Common Misconfigurations on The Cloud and Their Solutions
In the modern landscape of cloud computing, it is imperative to stay aware of the most common cloud misconfigurations that could hamper your cloud environment. Here are the 13 most common misconfigurations in the cloud, along with their solution:

- Excessive Permissions
- Unrestricted Open Network Ports
- Exposed Storage Buckets
- Absence of Logging and Monitoring
- Open ICMP
- Keeping Default Credentials
- Keeping Development Configuration in Production
- Extensive Access to HTTPS and Non-HTTP Ports
- Neglecting Safe Configuration For Third-Party Components
- Poorly Configured Automated Backup
- Lack of Network Segmentation
- Weak Password Policies
- Insecure API Configurations
Excessive Permissions
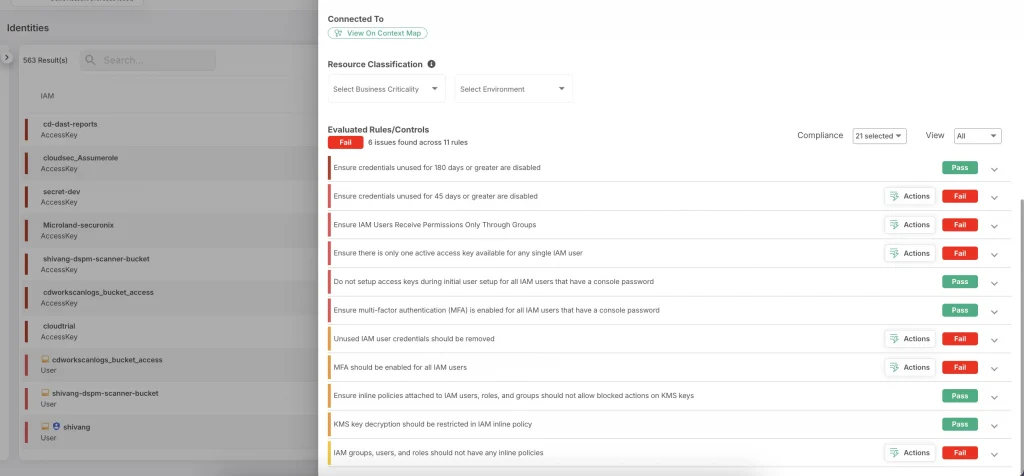
Due to configuration misalignment, providing excessive permission to cloud resources can lead to excessive access. This excessive permission to the resources provides a pathway for cybercriminals to capitalize on this misconfiguration for lateral movement in the cloud infrastructure.
The best way to solve this issue is by implementing the principle of least privilege and using IAM policies to restrict access. Your team should review and audit access controls at regular intervals to avert this misconfiguration.
Unrestricted Open Network Ports
Another common cloud misconfiguration is the availability of excessive open network ports because these ports allow internet access to your resources and it leads to security risk. When RDP and SSH access to servers from public or external networks are allowed, it leads to serious security issues in the cloud resources.
The best way to solve it is by limiting access to network ports according to the requirement and implementing the least privilege rule. Outbound traffic from the application server should be tightly controlled, and access should be only given to the application and server that needs them.
Exposed Storage Buckets
Leaving cloud storage buckets like Google Cloud and Amazon S3 storage open to the public is an impactful misconfiguration that puts all the data at risk. Confusion between authenticated and authorized users leaves the storage accessible to everyone, even when the user is not part of the organization.
To solve this misconfiguration, all the data should be encrypted with strong encryption, and all unnecessary access to public storage nodes should be eliminated. Enabling appropriate access control, especially logging, can be helpful in solving the issue.
Absence of Logging and Monitoring
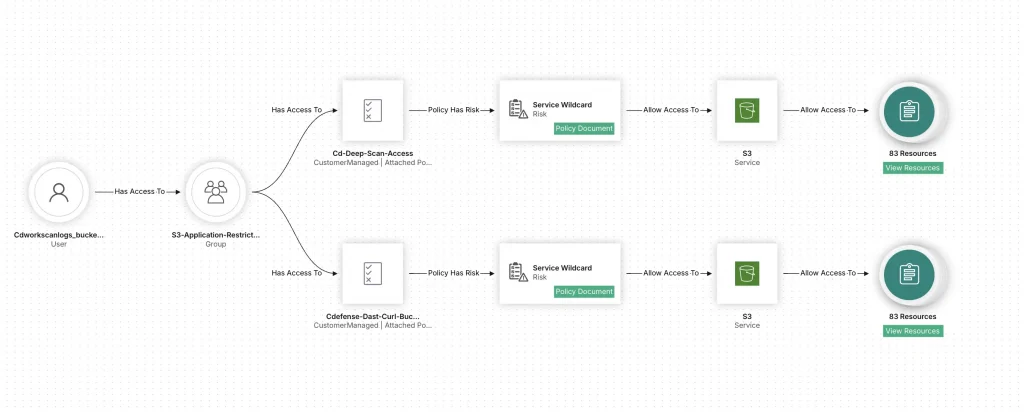
Many organizations operating in the cloud environment often fail to configure or enable logging and monitoring of cloud resources. It is vital for organizations to keep track of security events and telemetry data and flag any issues.
Organizations should enable logging for all the cloud services because it will provide audit trails and information to improve security posture. You should focus on creating automated monitoring and alerts for any suspicious or breach pattern activity so that they can be remediated immediately.
Open ICMP
The Internet Control Message Protocol or ICMP is designed to report network device errors to the system. But when it is left open, it becomes a lucrative target for malicious actors because then these cyber criminals can launch their cyber attacks.
Although ICMP will continue to display server status, cyber attackers capitalize on it, launch DDoS, or inject malware. The organization has been facing this misconfiguration for a long time, but it still remains a practical issue in the cloud security realm.
The only way to bypass this issue is by blocking ICMP in your cloud configuration, which will prevent attack vectors from hindering your cloud operation.
Keeping Default Credentials
During development, many developers keep the default password for software and cloud infrastructure services. However, in most cases, the default password is left in place after deployment, and this allows cybercriminals to get easy access as these default passwords are pretty generic.
Integrating the scanning of code through any solution during the application development cycle will remediate the issue and ensure there are no exposed passwords.
Keeping Development Configuration in Production
During the development process, the security is quite lenient, facilitating developers to make changes to the code and gain agility. However, developers often keep the same configuration in the production, and it leads to data leaks or compromise. Malicious actors can act upon the relaxed security structure of the product and gain entry.
However, correctly assessing the code settings before implementing them in the product stage will ensure all the data are secured and default security settings aren’t promoted.
Extensive Access to HTTPS and Non-HTTP Ports
All the HTTPS and non-HTTP ports should be checked regularly as system operation is dependent on these vulnerable ports for the internet.
It is an excellent practice to provide access to only those ports that are needed, and other ports should be blocked from any network. However, maintaining access to all the ports can be tricky, and if these ports are left with poor configuration, it will pave the path for attackers to get access to your resources.
When you open HTTPS and non-HTTPS ports to the internet, you have to implement a security solution that will ensure the traffic is entirely encrypted and will be restricted to specific addresses only.
Neglecting Safe Configuration For Third-Party Components
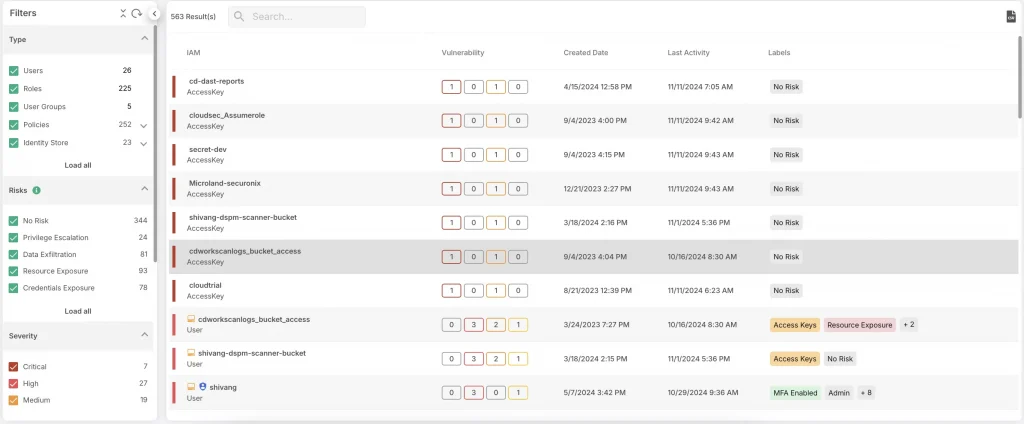
Most modern software development processes utilize third-party libraries, applications, and elements to ease up the development stage. During this time, many libraries access the cloud resources. If any of the libraries that you are using have vulnerabilities, cybercriminals can exploit those vulnerabilities and access the resources of your cloud infrastructure.
You will have to research all the third-party libraries you use and check whether they have any vulnerabilities or not. All the third-party vendors prescribe best practices and security configurations, and it is essential that you follow them to maximize security. You should also scan the code in the CI/CD pipeline to ensure it is free from vulnerability.
Poorly Configured Automated Backup
Poorly configured and insecure automated backup is a well-known misconfiguration, and organization from different sectors faces this issue. Organizations pay a lot of attention when it comes to securing the master storage, but they inefficiently configure the backup, making it vulnerable to insider threats.
Insider threats are a predominant risk in the cybersecurity world, and as McAfee’s report stated, 92% of an organization’s employee credentials are sold to malicious attackers.
While commencing an automated backup of your data during migration to the cloud, you will have to make sure that the backup is completely encrypted. You should also curtail the number of access to the storage backups.
Lack of Network Segmentation
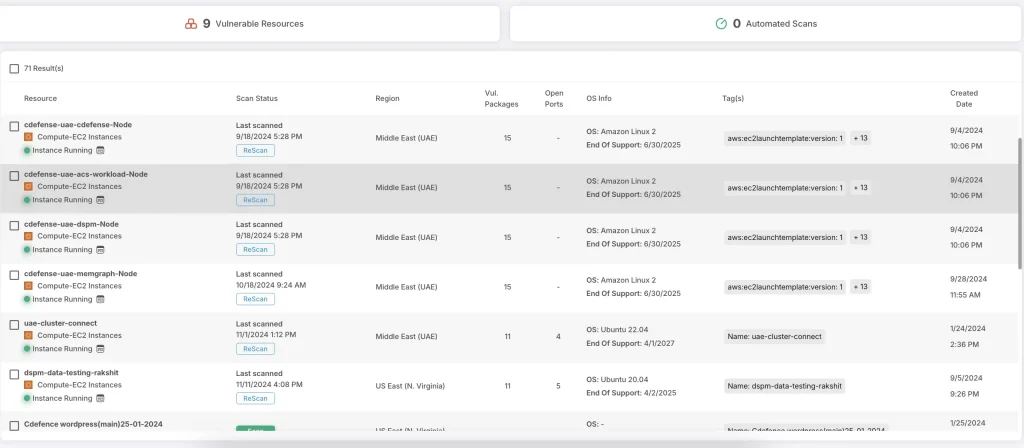
Network segmentation is a vital aspect of the cloud, and failing to configure it properly can make critical resources vulnerable to exploitation. Organizations often fail to segment their network correctly, which puts resources at unnecessary risk.
Utilizing VPC or virtual private cloud and network security groups to segment networks and restrict resources depending on the security requirement can help you mitigate any exploitations.
Weak Password Policies
Weak password policies are less sophisticated yet impactful misconfiguration that makes sensitive data vulnerable to attacks. Even though many organizations in the world follow strict security policies when it comes to passwords, there are still organizations that allow weak passwords and don’t enforce stringent password policies.
To prevent this kind of misconfiguration, you should implement strong password policies that will involve the use of complex password combinations. It is also a best security practice to encourage all users to enable MFA, enhancing overall security.
Insecure API Configurations
In many instances, organizations expose cloud APIs through different orchestration tools like Kubernetes without proper authentication and authorization. This allows attackers to get hold of the APIs and exploit or modify the workloads for malicious purposes.
The convenient way to address this misconfiguration is by securing the APIs through API keys or OAuth and limiting the access to authorized users. You should also pay attention to implementing access controls and making use of WAFs for securing APIs from cybercriminals.
How to Safeguard Your Data From Cloud Misconfiguration?
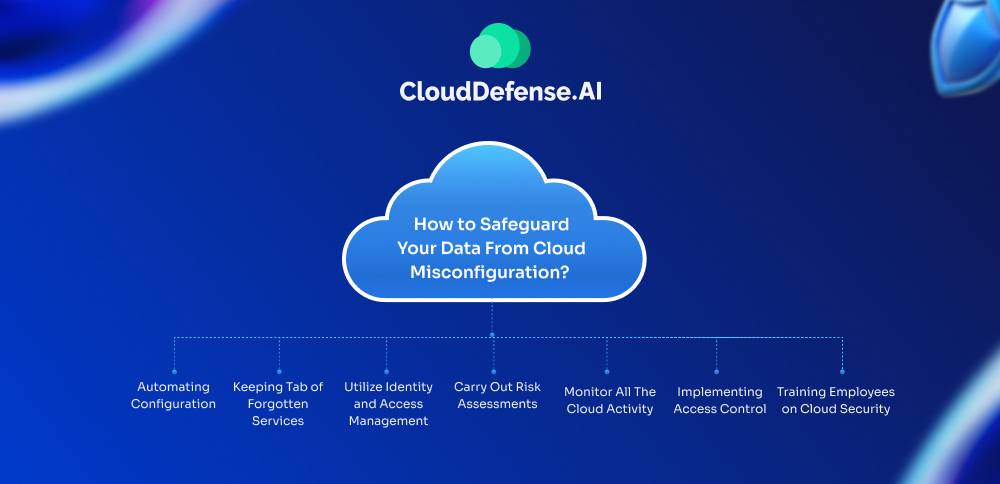
Safeguarding all the sensitive data from cloud misconfiguration is crucial for every organization. That is why we have made a list of expert recommendations that will help you to configure your cloud environment securely;
Automating Configuration
In modern times, organizations leverage the capability of automation tools, and you can also utilize them to automate your cloud configuration. It will not only ensure that your cloud infrastructure is set up according to policies and follows the best security practices but will also make sure there is minimal human error. Automation tools will also help you to enforce various security policies to minimize vulnerability.
Keeping Tab of Forgotten Services
During the development stage of an application and services, DevOps engineers and operation teams create a lot of configuration, but they usually forget to recheck before deployment. To prevent misconfiguration, you must keep a tab of old cloud services and associated assets.
Utilize Identity and Access Management
You should focus on leveraging IAM services in your cloud infrastructure so that you can efficiently manage all the user and service identities. Most cloud providers nowadays offer IAM services so you can manage the service. Along with IAM, you should also enforce MFA and strong password policies.
Carry Out Risk Assessments
Your security and operations teams should carry out cloud risk assessments because they will enable you to identify vulnerabilities and other risks. Through thorough risk assessment, you can discover risks in the cloud infrastructure when migrating your operations, applications, and data to the cloud.
Monitor All The Cloud Activity
Implementing constant monitoring of all the cloud activity is a great way to identify any misconfiguration or vulnerability that could jeopardize the security posture. Along with monitoring, you should also log all the cloud activity, and while reviewing the logs, you can also detect and respond to any potential misconfiguration.
Implementing Access Control
You should implement robust access control for all the cloud resources because it will limit user access to sensitive data and prevent any potential misconfiguration. You can implement strong access control through the PoLP model so that only data access should be given to users who need it. You should also audit the access control regularly to eliminate excessive permissions.
Training Employees on Cloud Security
Human error is the leading cause of misconfigurations in the cloud, so training employees on various cloud security will help you minimize these issues. You should train all the employees in your organization on implementing best security practices and what steps they should follow. Through the training, the employees should also be made aware of risks that arise due to misconfigurations.
Now, before ending this guide, we would request you to take a look at some FAQs;
FAQ
Why do misconfigurations in the cloud happen?
Misconfigurations in the cloud happen for different reasons, and they often stem from the lack of understanding and complexity of the cloud computing environment.
Human error in web-based consoles and the inability to keep up with the rapid cloud changes is another reason that many misconfigurations happen in the cloud. Lack of monitoring, access control issues, and inadequate documentation also lead to misconfigurations.
What are the effects of cloud misconfiguration?
Cloud misconfiguration is a significant security issue that has a wide range of adverse impacts on an organization.
Ranging from compliance violations, unauthorized access, and malware attacks to data loss and misconfigured backup, cloud misconfigurations leave many adverse effects. Due to cloud misconfiguration, organizations also face downtime, loss of reputation, and increased operational costs.
Are cloud misconfigurations impacting your security?
Misconfigurations heavily affect the security posture of an organization and leave the system vulnerable to attacks. Misconfiguration cloud security is one of the leading causes of security incidents and breaches.
It allows cybercriminals to gain unauthorized access to the system resources and system and provides a platform to inject malware or launch ransomware- resulting in severe data breaches.
Conclusion
We are confident that this guide regarding the most common misconfiguration on the cloud will help you stay aware of misconfiguration in your cloud infrastructure.
In modern times, when you stay aware of common cloud misconfigurations, it will not only help you mitigate any potential security risks but will keep you ahead of the cybercriminals. In this guide, we have also put forward different ways and solutions to safeguard and minimize the occurrence of misconfiguration in your cloud environment.







