Digital transformation is reshaping how organizations protect sensitive data, shifting from traditional on-premises security to agile cloud security solutions. Today’s cyberspace requires top-notch security for business continuity and competitive advantage.
This blog explores how cloud security offers scalable, cost-efficient protection compared to legacy systems. You’ll learn the fundamental distinctions between cloud security vs traditional security and why the modern approach is critical for meeting today’s digital challenges.
What is Traditional Security?
Traditional security, also known as on-premises security, refers to the cybersecurity strategies and technologies used to protect IT infrastructure that is physically hosted within an organization’s data centers.
This approach relies on dedicated hardware, firewalls, network security appliances, and endpoint protection solutions that are deployed and managed in-house.
In a traditional security model, organizations control all aspects of their security, from hardware procurement and software deployment to ongoing maintenance and monitoring.
This model was widely used before the rise of cloud computing, as businesses relied on in-house IT teams to protect their networks, servers, and data from cyber threats.
Common Tools and Techniques in Traditional Security
Organizations utilizing traditional security typically employ a combination of tools and techniques to safeguard their infrastructure. Some of the most common include:
- Firewalls: Hardware-based or software-based firewalls serve as the first line of defense, monitoring and controlling incoming and outgoing traffic based on predefined security rules.
- Antivirus and Anti-malware Solutions: These tools detect, prevent, and remove malicious software, ensuring endpoints remain secure.
- Intrusion Detection and Prevention Systems (IDPS): IDPS solutions monitor network traffic for suspicious activity and can block or alert administrators to potential threats.
- Virtual Private Networks (VPNs): VPNs create secure, encrypted connections between remote users and an organization’s internal network, ensuring data remains protected.
- Access Control Systems: These systems enforce policies such as role-based access control (RBAC), requiring authentication mechanisms like multi-factor authentication (MFA).
- Physical Security Measures: Server rooms and data centers implement biometric authentication, key card access, and surveillance systems to prevent unauthorized physical access.
Traditional IT Security Challenges
While traditional security models have long been the standard for organizations, they come with several inherent challenges that make them less adaptable to modern business needs.
- Limited Scalability: One of the biggest challenges with traditional security is its limited scalability. As businesses grow, expanding IT security infrastructure requires purchasing additional hardware, configuring new devices, and hiring more IT staff. This can be both costly and time-consuming, making it difficult to scale security operations quickly.
- Complex Hardware Deployment and Maintenance: On-premises security demands continuous hardware management, including installation, updates, and patching. Organizations must allocate resources for ongoing maintenance, ensuring all systems remain secure and functional. Hardware failures, system outages, and capacity constraints can significantly impact business operations, leading to downtime and increased costs.
- Longer Time to Value and Slower Update Cycles: Deploying traditional security solutions often takes weeks or months due to hardware procurement, configuration, and testing. Additionally, updates and patches require manual implementation, making it harder to respond swiftly to emerging threats. Unlike cloud-based security solutions, which receive automatic updates, traditional security often falls behind in addressing the latest vulnerabilities.
What is Cloud Security?
Cloud security refers to the policies, technologies, and controls designed to protect cloud-based systems, data, and infrastructure from cyber threats.
Unlike traditional security models that rely on on-premises hardware and software, cloud security is inherently cloud-native, meaning it is designed to function within cloud environments efficiently.
One of the key characteristics of cloud security is its distributed and dynamic nature, allowing organizations to implement security measures that scale alongside their cloud resources. As businesses migrate their operations to the cloud, cloud security ensures data confidentiality, integrity, and availability across various environments, including public, private, and hybrid clouds.
Benefits of Cloud Security
1. Rapid Deployment – Cloud security solutions can be deployed quickly and easily compared to traditional security setups that require extensive hardware and manual configurations.
2. Elastic Scalability – Cloud security scales automatically to accommodate changes in demand, ensuring that security measures remain effective as workloads expand or contract.
3. Reduced Operational Costs – With cloud-based security solutions, organizations eliminate the need for expensive on-premises infrastructure and maintenance costs.
4. Advanced Threat Protection – Cloud security employs AI-driven threat intelligence, automated response mechanisms, and machine learning algorithms to detect and mitigate cyber threats in real-time.
5. Centralized Security Management – Cloud security platforms offer centralized dashboards that enable IT teams to monitor security across multiple cloud services and environments.
Core Components of Cloud Security
Cloud security comprises several critical components that work together to provide comprehensive protection for cloud environments.
SaaS-Based Security Tools
Many cloud security solutions are delivered as Software-as-a-Service (SaaS) tools, providing organizations with cloud-native security features without the need for on-premises deployments. Common SaaS-based security tools include:
- Cloud Access Security Brokers (CASBs) – Enforce security policies and ensure compliance across cloud applications.
- Identity and Access Management (IAM) – Controls and verifies user identities, ensuring only authorized users can access cloud resources.
- Endpoint Detection and Response (EDR) – Monitors and protects endpoints such as cloud-hosted virtual machines and workstations from cyber threats.
- Cloud-Native Application Protection Platforms (CNAPPs) – Provide comprehensive security for cloud-native applications, integrating features such as workload protection, vulnerability scanning, and compliance enforcement.
Log Management & Security Information and Event Management (SIEM)
Effective cloud security requires continuous monitoring and logging of security events. Cloud-based SIEM solutions collect, analyze, and correlate security logs from various sources to detect anomalies and potential threats. Some key features include:
- Automated Threat Detection – Uses AI and machine learning to identify suspicious activity.
- Real-Time Alerts & Incident Response – Enables security teams to respond quickly to security incidents.
- Regulatory Compliance Monitoring – Ensures cloud security meets industry regulations such as GDPR, HIPAA, and SOC 2.
Continuous Monitoring & Threat Intelligence
Unlike traditional security, which relies heavily on periodic security updates, cloud security is proactive and continuous. Key aspects of continuous monitoring include:
- Real-Time Traffic Analysis – Monitors network traffic for anomalies and potential security threats.
- Automated Patching & Updates – Ensures all cloud applications and infrastructure remain up to date against emerging vulnerabilities.
- Behavioral Analytics – Identifies abnormal patterns of user activity that could indicate insider threats or compromised accounts.
Detailed Comparison: Cloud Security vs. Traditional Security
As more businesses transition to the cloud, it is important to understand the fundamental differences between cloud security and traditional security. While traditional security relies on on-premises infrastructure and manual processes, cloud security leverages cloud-native solutions that offer flexibility, scalability, and automation. Below, we explore how these two security models compare across key areas, including visibility, deployment, time to value, maintenance, and cost structure.
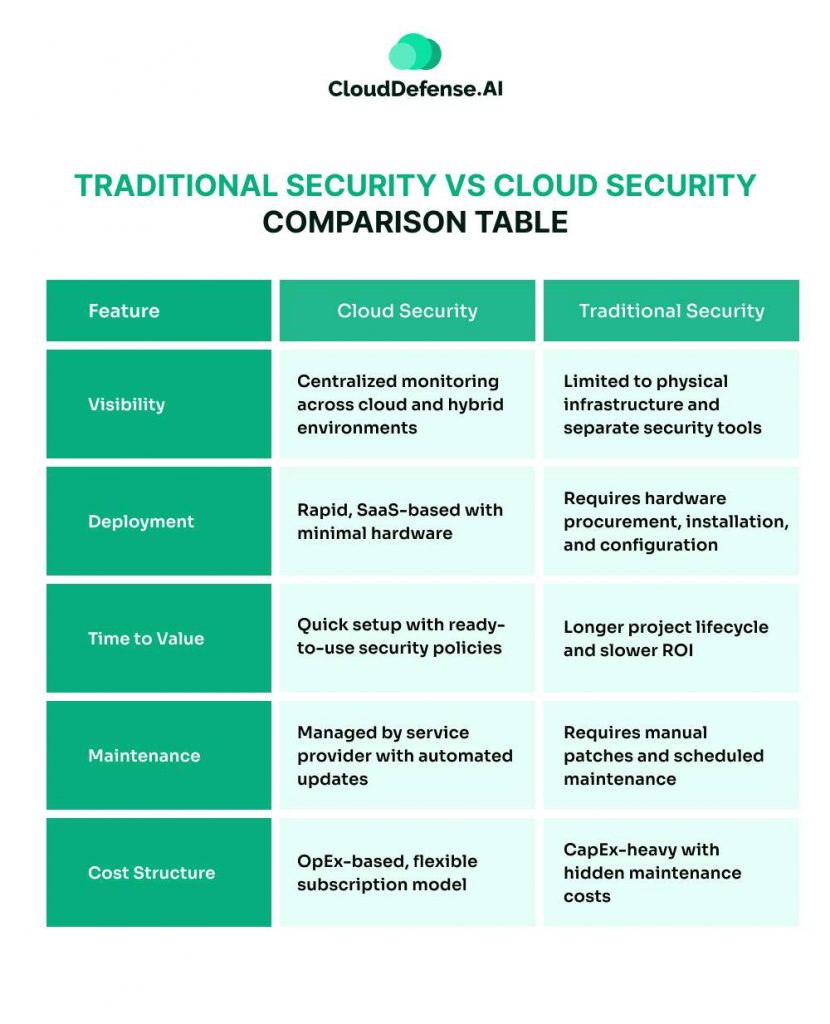
Visibility
- Cloud Security: Cloud security provides centralized monitoring and visibility across multiple cloud and hybrid environments. Organizations can track and analyze security events in real-time, using cloud-native security tools like Cloud Security Posture Management (CSPM) and Cloud Access Security Brokers (CASB). These solutions help detect misconfigurations, unauthorized access, and compliance violations.
With cloud-based logging and analytics, security teams can consolidate data from different cloud services into a single, unified dashboard, enabling faster detection and response to threats.
- Traditional Security: Traditional security is often limited to physical infrastructure and on-premises networks. Monitoring requires multiple security appliances such as firewalls, intrusion detection systems (IDS), and SIEM solutions, which operate separately. This siloed approach makes it difficult to gain a unified view of security threats, increasing the risk of undetected breaches.
Deployment
- Cloud Security: One of the biggest advantages of cloud security is rapid deployment. Cloud security solutions are SaaS-based, meaning they can be deployed instantly without extensive hardware installation. Organizations can automate security configurations and policies across cloud workloads, reducing setup time and operational complexity.
Additionally, cloud security solutions scale automatically, adjusting to demand as workloads increase or decrease. This flexibility ensures that organizations always have the right level of protection without manual intervention.
- Traditional Security: Traditional security requires hardware procurement, installation, and manual configuration. This process can take weeks or even months, delaying security implementation. Furthermore, traditional security solutions are often hardware-dependent, making it difficult to scale as an organization grows.
Scaling traditional security involves purchasing additional firewalls, servers, and security appliances, making it costly and time-consuming.
Time to Value
- Cloud Security: With pre-configured security templates and automation tools, cloud security provides immediate protection upon deployment. Businesses can quickly enforce security policies and integrate security solutions across multiple cloud environments, reducing time-to-value.
Cloud security solutions also offer built-in compliance frameworks for regulations like GDPR, HIPAA, and SOC 2, making compliance faster and easier.
- Traditional Security: Traditional security has a longer project lifecycle due to the manual setup of security appliances, patching, and software configuration. Organizations may need to hire additional staff to maintain on-premises security systems, further delaying implementation.
Compliance is also more complex with traditional security, as manual audits and log analysis are required to meet regulatory requirements.
Maintenance and Updates
- Cloud Security: Cloud security is fully managed by the service provider, meaning software patches, updates, and security enhancements are applied automatically. This ensures that organizations are always protected against the latest threats without requiring manual intervention.
Many cloud security providers also offer AI-driven threat intelligence, which continuously improves security detection and response capabilities.
- Traditional Security: With traditional security, organizations must manually install patches and schedule maintenance. This creates vulnerabilities, as delayed updates can expose systems to new threats. Maintaining traditional security also requires dedicated IT staff, increasing operational costs.
Organizations using traditional security often struggle with downtime during maintenance, affecting productivity and business operations.
Cost Structure
- Cloud Security: Cloud security follows an OpEx (operational expenditure) model, meaning businesses pay for what they use through a flexible subscription model. This makes cloud security cost-effective for businesses of all sizes, as they can scale up or down based on their needs.
Additionally, cloud security eliminates the need for expensive hardware purchases, reducing upfront capital expenses.
- Traditional Security: Traditional security follows a CapEx (capital expenditure) model, requiring significant upfront investments in hardware, infrastructure, and personnel. Costs can be unpredictable, as organizations may need to purchase additional appliances, licenses, and storage to handle growing security needs.
Moreover, hidden costs like hardware maintenance, software upgrades, and IT labor add to the total cost of ownership.
Traditional Security vs Cloud Security Comparison Table
Cloud security offers significant advantages over traditional security in terms of visibility, deployment, scalability, and cost-effectiveness. With centralized security monitoring, rapid SaaS deployment, automated updates, and flexible pricing models, cloud security enables organizations to stay ahead of evolving cyber threats while reducing operational complexity.
On the other hand, traditional security solutions require more manual effort, higher upfront costs, and complex hardware maintenance, making them less adaptable today.
Understanding the Limitations of Traditional Security in a Cloud World
As organizations move toward cloud-based infrastructures, the limitations of traditional security become more apparent. Legacy security models, designed for static, on-premises environments, struggle to protect dynamic, distributed cloud ecosystems. To maintain a strong security posture, businesses must transition from traditional security approaches to cloud-native solutions that offer real-time protection, scalability, and automation.
This is Why Traditional Security Falls Short
- Inability to Monitor Transient and Elastic Workloads: Traditional security solutions were built for static environments, where servers, applications, and workloads remain in fixed locations. However, cloud infrastructure is highly dynamic, with workloads spinning up and shutting down automatically based on demand.
Legacy security tools lack the ability to track and secure these transient workloads, leading to visibility gaps that attackers can exploit. Without continuous monitoring and automated policy enforcement, businesses risk leaving cloud assets unprotected.
- Limitations in Real-Time Threat Detection: Cloud environments generate massive volumes of security data, requiring real-time analysis to detect and respond to threats. Traditional security solutions, such as firewall appliances and on-premises SIEM systems, rely on manual log analysis and periodic scans, which are too slow for modern cloud-based attacks.
Unlike cloud-native security tools, which use AI-driven threat intelligence and automated response mechanisms, traditional security solutions lack agility and often result in delayed threat detection and response.
How to Transition from Traditional Security to Cloud Security?
Traditional security models, designed for on-premises environments, often struggle to protect dynamic, distributed cloud ecosystems. To bridge this gap, businesses must adopt modern security strategies that integrate cloud-native solutions while ensuring compliance and control over existing systems.
Integrating Traditional Security with Cloud-Native Solutions
Rather than completely replacing legacy security infrastructure, organizations can enhance their security posture by incorporating cloud-native security tools. This hybrid approach allows businesses to leverage the benefits of cloud security without disrupting existing operations. Key strategies include:
- Deploying Cloud-Native Security Platforms: Solutions like Cloud-Native Application Protection Platforms (CNAPPs) provide comprehensive visibility, threat detection, and compliance management across hybrid and multi-cloud environments. CNAPPs integrate multiple security capabilities, such as runtime protection, vulnerability scanning, and posture management, to protect cloud workloads.
- Using CASBs: CASBs serve as an intermediary between on-premises security and cloud applications, ensuring that security policies remain consistent across all environments. These solutions help detect unauthorized cloud usage, prevent data leakage, and enforce access controls for SaaS, IaaS, and PaaS applications.
- Extending Identity and Access Management (IAM): With cloud adoption, managing user identities and permissions across multiple environments becomes challenging. Organizations should implement cloud-based IAM solutions that centralize authentication, enforce multi-factor authentication (MFA), and apply role-based access control (RBAC). This ensures that only authorized users can access sensitive cloud resources.
Embracing a Hybrid Approach During Digital Transformation
For organizations undergoing cloud migration, adopting a hybrid security model enables a gradual transition while minimizing security gaps. Best practices include:
- Implementing Zero Trust Architecture (ZTA): A Zero Trust model enforces continuous verification of users, devices, and workloads, rather than assuming trust based on network location. By adopting least privilege access, micro-segmentation, and identity-based authentication, organizations can significantly reduce the risk of unauthorized access and insider threats.
- Using Cloud Security Posture Management (CSPM): Misconfigurations in cloud environments are a leading cause of data breaches. CSPM solutions continuously monitor cloud resources for policy violations, misconfigurations, and compliance risks, ensuring that cloud infrastructure remains secure and adheres to industry regulations. CloudDefense.AI provides CSPM bundled together with other cloud security solutions.
- Adopting DevSecOps Practices: Security must be embedded into the software development lifecycle (SDLC) to proactively detect vulnerabilities and enforce security controls. By integrating DevSecOps practices, organizations can automate security testing, enforce secure coding standards, and deploy security updates faster, reducing exposure to cloud-based threats.
Discover Cloud Security with CloudDefense.AI!
CloudDefense.AI simplifies cloud security, delivering a comprehensive Cloud-Native Application Protection Platform (CNAPP) designed to safeguard your cloud infrastructure with automation, real-time monitoring, and proactive threat detection.
Why Choose CloudDefense.AI?
Traditional security solutions often struggle to keep up with the scalability and complexity of cloud environments. CloudDefense.AI bridges this gap with an all-in-one security platform that ensures visibility, compliance, and protection across your cloud infrastructure.
With CloudDefense.AI, you get:
- Automated Risk Identification & Mitigation
- End-to-End Protection for Cloud Workloads
- Proactive Security Posture Management
- Real-Time Threat Detection & Response
A Fully Integrated Security Suite
- Cloud Security Posture Management (CSPM): Misconfigurations are a leading cause of cloud breaches. CloudDefense.AI’s CSPM solution continuously scans your cloud environment to detect and fix security misconfigurations. With real-time alerts and automated remediation, your cloud infrastructure remains secure and compliant with industry regulations like SOC 2, HIPAA, and GDPR.
- Cloud Workload Protection Platform (CWPP): Cloud workloads—whether virtual machines, containers, or serverless functions—need constant protection. CWPP defends against runtime threats, vulnerabilities, and malware by monitoring workload behavior and automating security responses to stop attacks before they spread.
- Cloud Infrastructure Entitlement Management (CIEM): Excessive or misconfigured user privileges pose a significant security risk. CloudDefense.AI’s CIEM solution enforces the principle of least privilege (PoLP), ensuring that users and services only have the permissions they absolutely need. This minimizes the risk of insider threats, accidental data exposure, and privilege escalation attacks.
- Kubernetes Security Posture Management (KSPM): Managing Kubernetes security can be complex. KSPM provides deep visibility into your Kubernetes clusters, detecting misconfigurations and enforcing security policies to prevent unauthorized access and maintain compliance.
- Data Security Posture Management (DSPM): Your sensitive cloud data needs continuous protection. DSPM scans for misconfigured storage buckets, exposed databases, and unauthorized access, ensuring that critical data remains private and secure.
- Real-Time Asset Monitoring: Security teams need a clear view of their cloud environment. CloudDefense.AI provides real-time asset monitoring, allowing you to track all servers, applications, and workloads. The platform instantly flags suspicious activity, enabling quick incident response.
- Hacker’s View: Simulate Real Attacks: Think like a hacker to stay ahead of threats. Our Hacker’s View feature simulates attack paths and vulnerabilities, helping you proactively patch weaknesses before cybercriminals can exploit them.
- AI-SPM: AI-Driven Security Posture Management: Harness the power of artificial intelligence to analyze security trends, detect evolving threats, and automate risk assessments. AI-SPM ensures that your security strategy adapts in real time, keeping your defenses one step ahead of cybercriminals.
Take Control of Your Cloud Security Today!
Cyber threats are evolving—but so is CloudDefense.AI. With our intelligent, automated, and proactive cloud security platform, you gain full control and visibility over your cloud environment. Ready to experience the future of cloud security? Book a demo today and see how CloudDefense.AI can secure your cloud assets, simplify compliance, and prevent breaches before they happen!







