2025 is expected to be a pivotal year for cloud security. With businesses rapidly adopting cloud-first strategies, the cloud security trend is shifting, and new challenges are emerging. So, what cloud security trends will define this critical year?
You will get an answer to this by the end of this blog, we explore the top cloud security trends in 2025 that will shape how organizations protect their digital assets. If you’re working with cloud technologies, this is what you need to know to prepare for the year ahead.
How Cloud Security Has Evolved Over Time?
Before diving into the cloud security trends shaping 2025, it’s important to understand how far the industry has come. Cloud security has changed significantly over the years. What started as a new concept has now become a critical focus for businesses around the world. Here’s how cloud security trends has evolved:
2006: Cloud Computing Begins
In 2006, Amazon Web Services (AWS) launched and marked the start of cloud computing as we know it. At this point, security wasn’t the main concern for most companies adopting cloud services. Businesses still relied on traditional security measures for their own systems, and cloud security was still in its early stages.
2010: Growth of Public Cloud
By 2010, public cloud services like AWS, Microsoft Azure, and Google Cloud became more popular. As more companies moved to the cloud, security became a bigger concern. There was a focus on basic encryption and access controls, but the cloud security space was still immature and evolving.
2014: The Shared Responsibility Model
In 2014, the shared responsibility model was introduced. This model clarified the division of security responsibilities between cloud providers and customers. Cloud providers secured the infrastructure, while customers were responsible for protecting their data, applications, and identities in the cloud. This was a key step in building a clearer framework for cloud security.
2017: Focus on Identity and Access Management (IAM)
As cloud environments became more complex, the need for stronger Identity and Access Management (IAM) systems grew. Multi-factor authentication (MFA) and Single Sign-On (SSO) became more common as organizations focused on securing access to cloud services and preventing unauthorized use.
2020: Cloud Security Becomes Critical
The COVID-19 pandemic accelerated the shift to cloud-based operations. With this shift came an increase in cyberattacks. Ransomware, data breaches, and other threats grew in scale. Businesses realized the importance of stronger security practices, and AI and machine learning started playing a bigger role in detecting and responding to threats.
2023: Proactive and Automated Security
By 2023, cloud security had become more proactive. Companies started using real-time monitoring and automated threat detection tools. This allowed for faster responses to security risks. Automation also helped streamline incident response, making it easier to manage cloud security in a more dynamic environment.
2025: Zero Trust and AI-Driven Security
In 2025, cloud security is focused on zero-trust architectures and AI-powered tools. As cyber threats become more sophisticated, companies are adopting continuous security models that don’t trust any user or device by default. AI-driven security tools are helping businesses predict, detect, and prevent threats more effectively than ever before.
Cloud security has come a long way, and it’s clear that it will continue to evolve. With these changes in mind, let’s dive into the top cloud security trends in 2025.
Top 5 Cloud Security Trends
1. Zero-Trust Approach
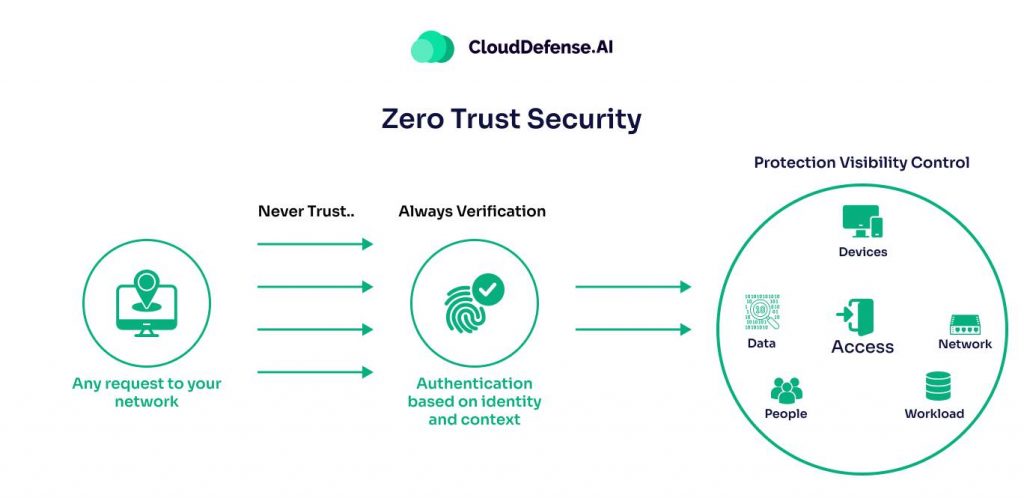
Zero Trust is no longer just a buzzword; it’s the foundation of cloud security in 2025. The old idea that if you’re inside a network, you’re trusted, just doesn’t cut it anymore. We’ve moved past that.
Here’s why Zero Trust is so critical and what makes it different from traditional approaches.
Verify Everything:
In the past, the assumption was that anyone inside the network was safe. Zero Trust challenges that. Now, every access request, whether it comes from inside or outside the network, has to be verified. This means no one gets automatic trust—everyone has to prove they belong.
Context Matters:
Zero Trust isn’t just about checking who’s asking for access. It’s about understanding the situation.
- Where is the request coming from?
- What device is being used?
- Is this request typical for this user at this time?
These details matter. Zero Trust takes all of this into account to ensure only legitimate access is granted.
Smarter Access Control:
Zero Trust doesn’t give broad access to the network. Instead, it limits access to only the resources a user or device absolutely needs.
- By breaking the network into smaller, manageable segments, it ensures that if something goes wrong, the damage is contained.
- If an attacker gains access to one part of the network, they can’t move around freely to other parts.
Ongoing Authentication:
Zero Trust doesn’t stop once a user logs in. It’s about constantly checking whether the user, the device, and the session are still secure. If something seems off, access can be denied right away.
Automating Security:
Zero Trust is getting a boost from AI and automation. By using these tools, organizations can make security decisions faster and with more precision. AI can detect unusual activity in real-time and adjust policies without waiting for manual intervention.
2. Growing Focus on Intelligent Security Investments
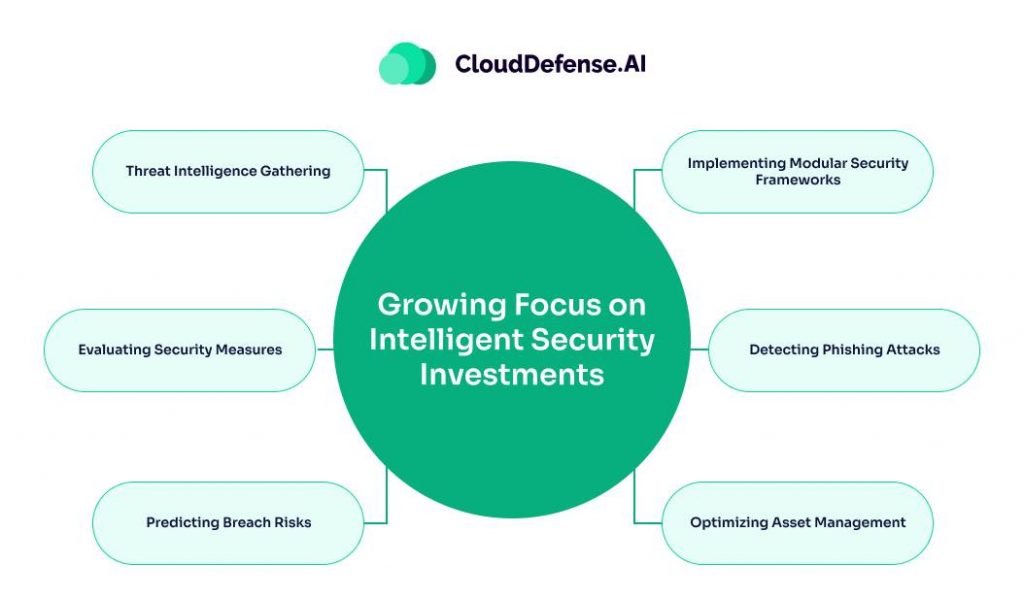
In 2025, cloud security is shifting from just adding more tools to focusing on making smarter, more strategic investments. Organizations are realizing that throwing more money at security doesn’t solve the problem—it’s about making those resources work smarter. Here’s why intelligent security investments are becoming the new priority.
AI and Machine Learning in Security:
The speed and scale of today’s security threats are too much for traditional methods to handle. AI and machine learning are changing that.
- Proactive Threat Detection: These technologies can spot patterns and anomalies in data, identifying threats before they even occur.
- Predictive Analytics: Artificial Intelligence is being used to predict what might happen based on past events, giving teams the ability to act before an attack is in motion.
Automated Security Operations:
Manual security processes are too slow. Automation speeds things up and cuts down human error.
- Faster Incident Response: By using Security Orchestration, Automation, and Response (SOAR) tools, organizations can respond to threats much faster.
- Continuous Monitoring: Real-time, AI-driven monitoring helps detect anomalies 24/7 and notifies the right people immediately.
Cloud-Native Security Tools:
Cloud environments are different from on-prem setups, so it’s crucial to use tools designed specifically for the cloud.
- Integrated Security: Cloud-native tools, like Cloud Security Posture Management (CSPM) or Cloud Access Security Brokers (CASBs), seamlessly integrate with cloud platforms and give you the visibility and control needed to secure your environment.
- These tools make security part of the cloud’s fabric, rather than something added on top.
Risk-Based Security Approach:
Instead of trying to secure everything equally, the focus is shifting to prioritizing based on risk.
- Organizations are identifying their most critical vulnerabilities and investing in security measures that directly address them.
- This ensures that security efforts are concentrated on the areas with the highest risk, making your budget more efficient.
Security as a Business Enabler:
Security is no longer seen as a blocker to growth. In fact, it’s being treated as a key enabler of business innovation. By investing in intelligent security systems, organizations can create a more secure cloud environment, enabling business agility and scalability without compromising on safety.
What does this mean? You can adopt new technologies and expand your cloud infrastructure confidently, knowing that your security systems are flexible enough to adapt.
3. Increased Adoption of CNAPPs
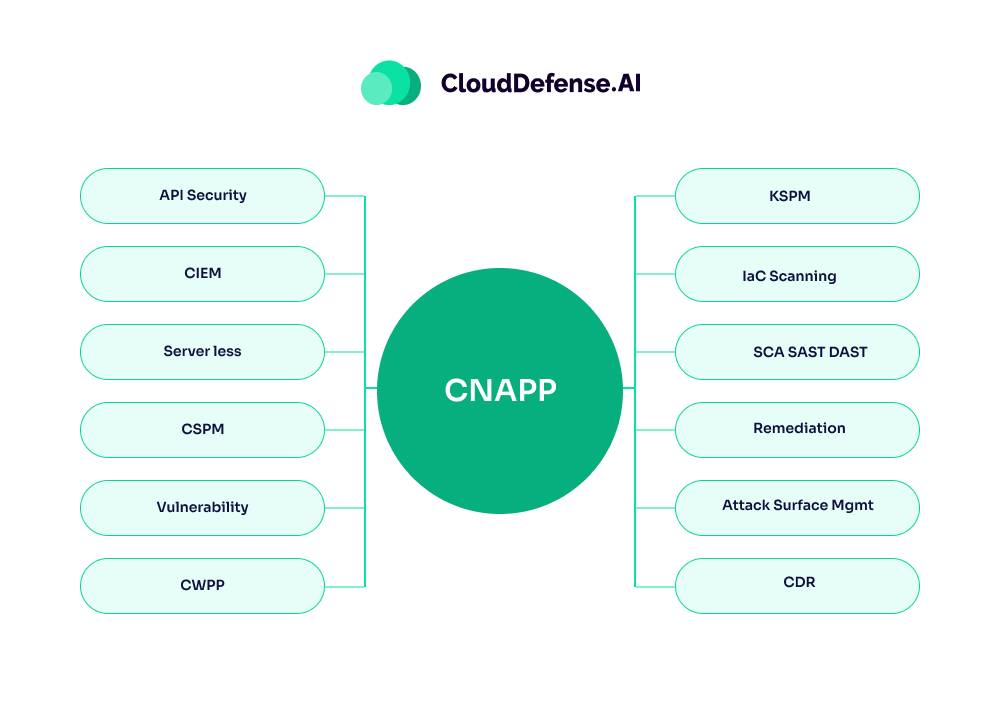
In 2025, security is becoming more integrated, with CNAPPs (Cloud Native Application Protection Platforms) at the center of it. These platforms are the answer to securing cloud-native applications—applications that run in modern, dynamic cloud environments.
The reason for their rise is simple: Traditional security tools don’t work for cloud-native apps. CNAPPs are changing the game by providing comprehensive, real-time protection throughout the entire development lifecycle.
Why CNAPPs?
- Complete Protection: CNAPPs provide end-to-end security, covering everything from development to runtime. They don’t just secure code; they monitor, detect, and fix vulnerabilities as the app is running in the cloud.
- Built for the Cloud: Cloud-native applications use containers, microservices, and serverless architectures. CNAPPs are specifically built to understand and protect these architectures, providing the right kind of protection for cloud-based apps.
Why Are They Gaining Traction?
- Increased Complexity of Cloud: As cloud-native environments grow, they introduce new security challenges. CNAPPs are designed to handle that complexity, offering visibility and control over every aspect of cloud infrastructure.
- Proactive Security: CNAPPs shift security left—meaning security is integrated early in the development process, allowing teams to catch vulnerabilities before they become a problem in production.
- Faster Remediation: With CNAPPs, you don’t need to wait for a scheduled scan or audit. Security teams can address issues in real-time, improving response time and reducing the risk of an attack.
4. Implementing DevSecops Practices
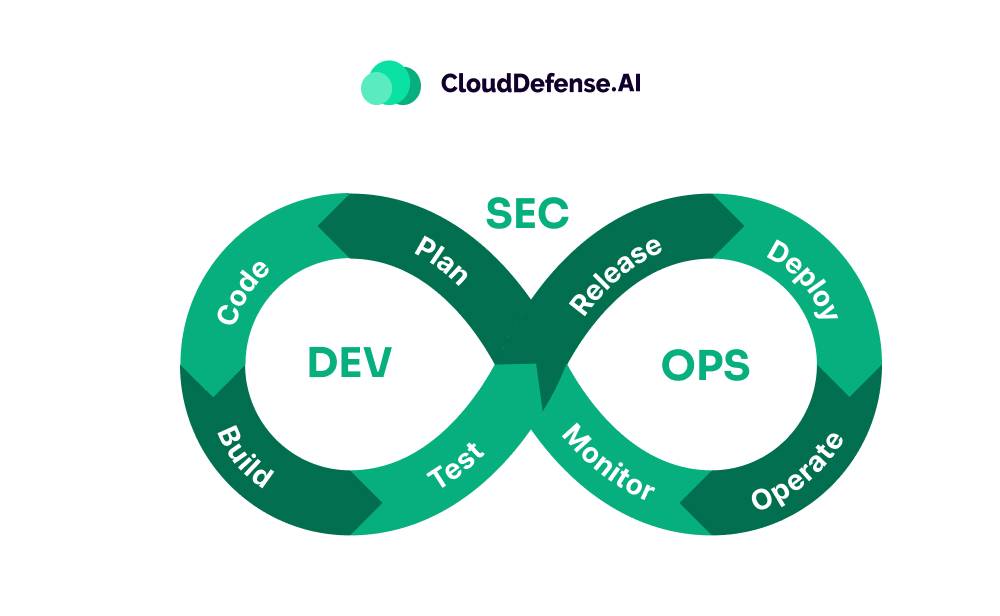
Nowadays, we can’t afford to treat security as a last-minute consideration in the development process. For instance, in 2024, the average cost of a data breach reached $4.88 million. This is why businesses are embedding security throughout their development pipeline, rather than waiting for vulnerabilities to emerge after deployment.
Why Is DevSecOps Critical Now?
- Rising Costs of Breaches: The financial impact of a data breach has grown significantly. Organizations can’t afford to deal with security issues after they happen. Integrating security earlier in development saves money in the long run.
- Speed of Development: With agile development moving at a faster pace, security needs to keep up. DevSecOps integrates security directly into the process, ensuring vulnerabilities are caught in real-time rather than during post-deployment testing.
What Exactly is DevSecOps?
- Automated Security: Security isn’t an afterthought. It’s part of the continuous integration pipeline, with automated tools scanning for vulnerabilities throughout the entire development lifecycle.
- Shift Left: Instead of waiting until the end of the process, security is embedded right from the start—during coding, testing, and deployment. The earlier issues are caught, the cheaper and faster they are to fix.
Why This cloud security Trend Matters:
- Security and Speed Can Coexist: The core benefit of DevSecOps is that it allows for rapid development without sacrificing security. In fact, it enhances security by identifying vulnerabilities early in the development process.
- A Matter of Cost: As data breach costs continue to climb, integrating security into DevOps is a no-brainer. DevSecOps helps prevent costly breaches, saving both time and money.
The focus on DevSecOps is clear—companies are moving towards a more proactive, integrated approach to security that doesn’t slow them down but keeps them ahead of potential threats. This isn’t just a cloud security trend; it’s a response to the growing cybersecurity risks every business faces.
5. The Emerging Need for Better Visibility in Cloud Security with Multi-Cloud Adoption
As more organizations move to multi-cloud environments, the challenge of ensuring solid security visibility across all platforms has grown significantly. It’s not just about having a backup plan with different cloud providers. It’s about managing and securing data across multiple providers, all with their own security models and policies.
Why Multi-Cloud Is Becoming Essential
- Avoiding Vendor Lock-In: Relying on a single cloud provider can be risky. Companies are distributing workloads across multiple cloud services to avoid this. But this also brings complexity, especially when it comes to security.
- Optimizing for Performance and Cost: Each cloud provider has strengths, whether it’s compute, storage, or AI tools. But coordinating security across these platforms has become increasingly difficult.
The Importance of Visibility
- Increased Complexity: Managing multiple cloud environments means different security models, tools, and policies to keep track of. Without proper visibility, it’s easy to miss a vulnerability or misconfiguration.
- Consolidated Threats: Attackers can move between cloud environments. Gaps in visibility can allow threats to spread and go unnoticed, which increases the risk of a breach.
- Compliance: Regulations are stricter than ever. Keeping track of security policies and ensuring compliance across multiple cloud environments requires constant visibility.
What’s Being Done?
- Unified Security Dashboards: More companies are relying on integrated dashboards to manage security across various cloud platforms. This allows security teams to monitor everything from a single location.
- AI and Analytics: Tools powered by AI are becoming essential for detecting threats across multi-cloud environments. They analyze large amounts of data quickly, finding anomalies that might be missed otherwise.
- Faster Detection of Issues: With multi-cloud, organizations have more potential points of failure. Better visibility helps teams detect vulnerabilities quickly and act before they can be exploited.
The key lesson learned is: Visibility across multi-cloud environments isn’t just a nice-to-have anymore. It’s necessary. Without it, organizations risk missing key vulnerabilities, opening the door to serious security breaches. The cloud security trend is clear: better visibility will be the backbone of cloud security in the coming years.
Stay Ahead of Cloud Security Trends in 2025 with CloudDefense.AI
At CloudDefense.AI, we’re all about making cloud security straightforward. Our CNAPP brings together cloud and application security in one platform, so you don’t have to juggle multiple tools. We focus on zero trust and fast, AI-driven threat detection to keep your multi-cloud environments secure.
With our platform, you get real-time insights and visibility—helping you catch risks before they escalate. It’s all about saving you time, reducing complexity, and giving you a clear view of your cloud security. From compliance to securing configurations, we’ve got everything integrated in one place.
Want to stay on top of these cloud security trends in 2025? Reach out to us or book a free demo to chat about how CloudDefense.AI can make your cloud security easier and more effective.







