As organizations continue to rapidly adopt cloud computing, the challenges of managing user access and entitlements have become increasingly complex. There are a couple of frameworks out there that aim to tackle this – Cloud Infrastructure Entitlement Management (CIEM) and Identity and Access Management (IAM).
On the surface, they might sound pretty similar, but the truth is, they represent quite different approaches to making sure the right people have the right levels of access to critical cloud resources. In this post, we’ll break down the key differences between CIEM and IAM, examining their unique capabilities, strengths, and use cases. By the end, you’ll have a clearer understanding of how CIEM and IAM differ, and how you can leverage these powerful tools to maintain tight governance over your cloud environments.
What is CIEM?
The core idea behind CIEM is to provide organizations with deeper visibility and control over who has access to what cloud resources. This is especially critical in today’s cloud-first world, where the traditional perimeter-based security model has largely gone out the window. With users, devices, and data distributed across multiple cloud platforms, it’s become exponentially harder to keep track of all the different access rights and privileges that have been doled out.
Benefits of CIEM
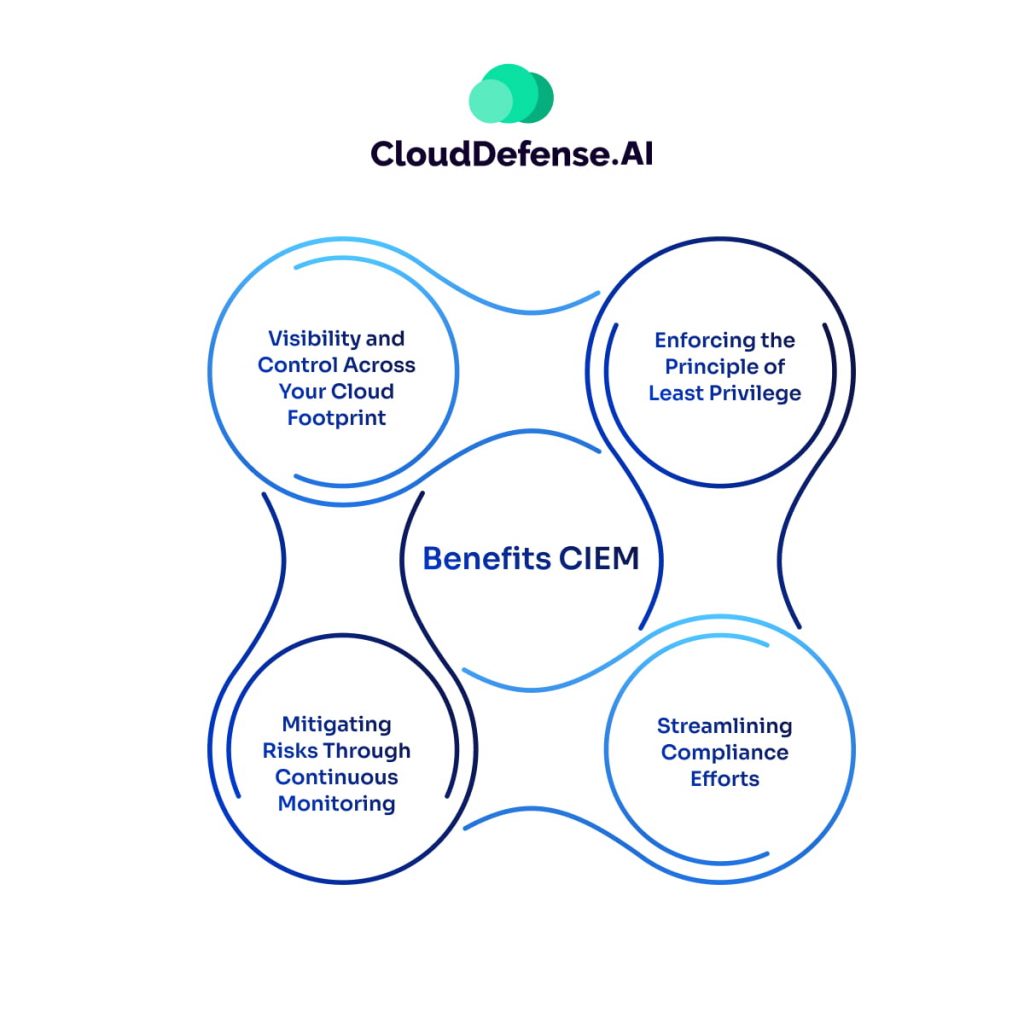
Here’s how CIEM empowers your cloud security:
Visibility and Control Across Your Cloud Footprint
One of the biggest challenges with cloud security these days is just keeping track of all the different user entitlements and access rights that are spread across your various cloud environments – whether that’s public clouds like AWS, Azure and GCP, or your own private cloud setup. CIEM gives you a centralized dashboard to see everything in one place. This comprehensive visibility is game-changing, as it allows you to really understand who has access to what, so you can effectively manage and govern those permissions.
Enforcing the Principle of Least Privilege
A foundational principle of robust cloud security is the concept of least privilege – making sure users only have the bare minimum access required to do their jobs. CIEM is designed to help enforce this. These tools are constantly analyzing user entitlements, identifying anything that looks excessive or unnecessary. Then they give you the ability to easily trim back those over-privileged access rights. This dramatically reduces your attack surface and the potential for bad actors to gain a foothold in your cloud environment.
Mitigating Risks Through Continuous Monitoring
CIEM isn’t just a static tool – it’s continuously monitoring user activity and access patterns, looking for any anomalies or suspicious behavior. Say an account gets compromised, or someone accidentally stumbles into elevated privileges they shouldn’t have. CIEM will detect that in real-time and alert you, so you can jump in and remediate the issue before it turns into a full-blown security incident. This proactive risk mitigation is crucial in today’s threat landscape.
Streamlining Compliance Efforts
A lot of the major industry regulations these days, like GDPR, HIPAA, and PCI-DSS, require organizations to demonstrate robust control and visibility over access to sensitive data and cloud resources. CIEM makes this compliance piece way easier, providing detailed audit trails and reports on all your entitlements. So when the auditors come knocking, you can quickly show them exactly what’s going on and prove you’ve got your cloud security house in order.
How CIEM Helps in Securing Cloud
CIEM really goes above and beyond when it comes to safeguarding your cloud environments. It’s not just about providing visibility into user entitlements – these solutions actually become proactive guardians of your security posture.
Here’s a real-world example that helps illustrate the power of CIEM’s threat detection capabilities. Let’s say you’ve got a marketing employee who normally has permission to access the customer email lists, so they can send out newsletters and such. But one day, CIEM’s analytics pick up on this employee trying to dig into the company’s highly sensitive financial databases. That’s a huge red flag – it could mean their account has been compromised, or maybe they’re a malicious insider trying to steal valuable data.
The beauty of CIEM is that it spots anomalous activity in real time and instantly alerts the security team. Now they can jump in, investigate what’s going on, and shut it down before any real damage is done. Rather than just sitting back and reacting after the fact, CIEM gives you the ability to get out in front of evolving cloud security threats. It’s continuously monitoring user behavior and entitlements, looking for those early warning signs so you can address vulnerabilities before they can be exploited.
That proactive risk detection is a game-changer, in my opinion. It transforms cloud access management from a reactive, compliance-driven exercise into a strategic, forward-leaning discipline. The visibility and control CIEM provides are crucial, no doubt. But its ability to be a true guardian of your cloud security posture is what really sets it apart as an indispensable tool in your security arsenal.
What is IAM?
When it comes to managing user access and identity across an organization, Identity and Access Management (IAM) is the name of the game. Unlike CIEM, which is focused specifically on governing cloud infrastructure entitlements, IAM takes a much broader, enterprise-wide approach. At its core, IAM is the framework that allows businesses to control who has access to what resources – whether that’s on-premises systems, cloud-based applications, or anything in between.
Key benefits of IAM
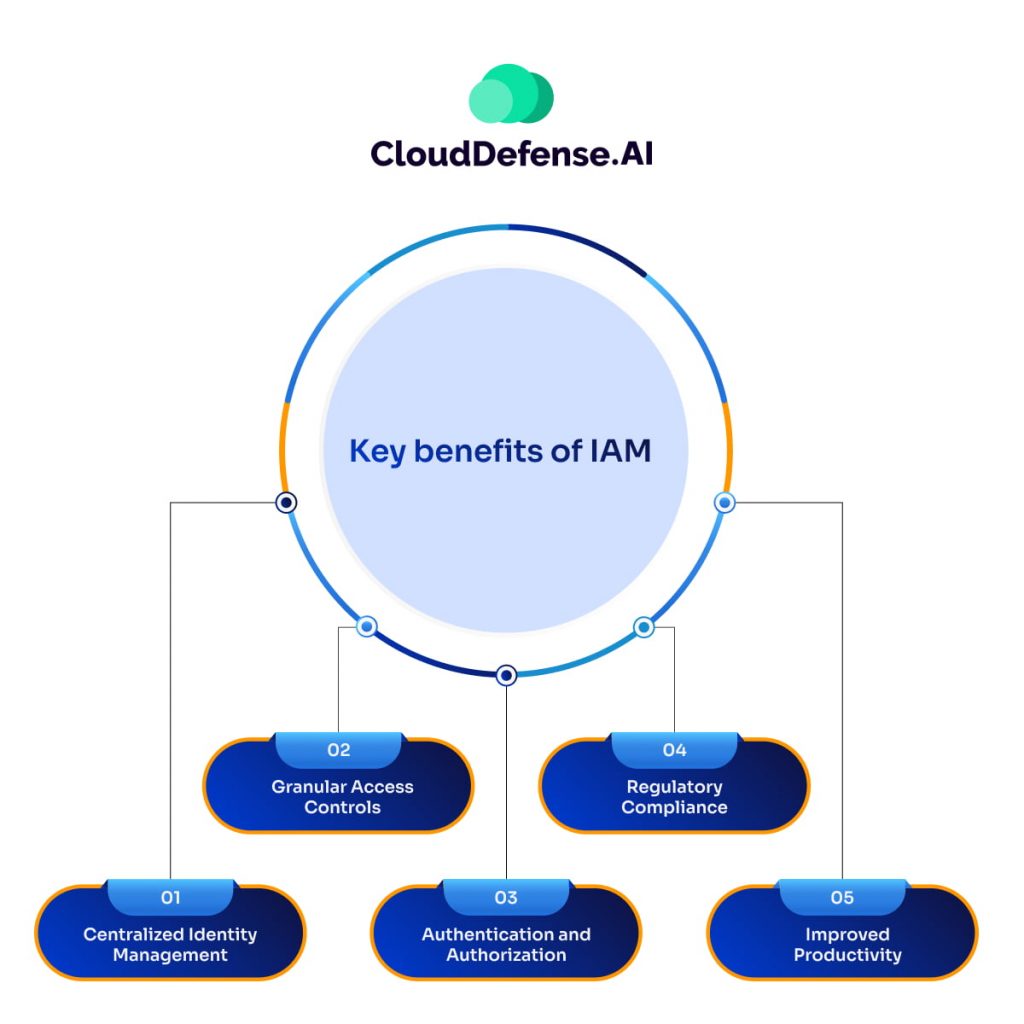
IAM provides a number of key benefits that help strengthen an organization’s overall security posture:
Centralized Identity Management
The great thing about IAM solutions is that they give you a single, unified view of all your user identities across the organization. No more jumping between different systems to onboard, offboard, and manage permissions for employees, contractors, partners, and all the rest. You’ve got it all right there in one central dashboard.
Granular Access Controls
IAM empowers you to implement fine-grained access policies. You can make sure users only have the bare minimum permissions they need to do their jobs. That principle of least privilege is huge for reducing the risk of data breaches or unauthorized access.
Authentication and Authorization
Plus, IAM handles all the critical identity verification (authentication) and access control (authorization) functions. That gatekeeping is absolutely essential for keeping your sensitive data and systems locked down tight, especially in today’s threat landscape.
Regulatory Compliance:
Many industry regulations, such as HIPAA, GDPR, and PCI-DSS, mandate robust identity and access management controls. IAM makes it easier to demonstrate compliance by providing detailed audit trails and access reports.
Improved Productivity
And let’s not forget – IAM can actually boost employee productivity by streamlining identity and access management across the organization. No more waiting around for permissions or fighting with complicated policies. People can just focus on their actual work.
How IAM Supports Cloud Security
As more and more mission-critical stuff migrates to the cloud, having a strong, enterprise-wide identity management framework like IAM is crucial for maintaining robust security. These IAM solutions integrate right with an organization’s cloud infrastructure, providing unified access control and visibility.
Think about it – without IAM, you’d be stuck trying to manage user identities and permissions in a fragmented way across on-premises and cloud environments. That’s just asking for vulnerabilities to creep in. But IAM lets you enforce consistent policies everywhere, closing those gaps and keeping the bad actors out.
Last but not least, IAM’s identity lifecycle management features – things like streamlined onboarding, offboarding, and permission changes – help reduce the risk of orphaned accounts or overly permissive access rights that could be exploited. Another critical safeguard against vulnerabilities in the cloud.
While both CIEM and IAM play crucial roles in securing access within an organization, they have distinct functionalities and areas of focus. This table provides a detailed comparison to help you understand their key differences:
| Feature | CIEM (Cloud Infrastructure Entitlement Management) | IAM (Identity and Access Management) |
| Primary Focus | Focused specifically on managing user entitlements and permissions within cloud infrastructure (e.g. IaaS, PaaS) | Takes a broader, enterprise-wide approach to governing user identities and access rights across on-premises, cloud, and hybrid environments |
| Environment | Specifically designed for cloud environments (public, private, hybrid) | Functions across on-premises, cloud, and hybrid environments |
| Identity Types | Users, applications, and services within the cloud | Users (employees, contractors, customers), applications, services |
| Visibility | Provides a centralized view of entitlements across all cloud accounts | Offers a centralized view of user identities and entitlements across the full IT ecosystem, including both cloud and on-premises resources |
| Least Privilege Enforcement | Helps enforce least privilege by identifying and eliminating excessive permissions | Enforces access controls based on user roles and job functions |
| Risk Mitigation | Continuously monitors user activity and entitlements to detect anomalies and suspicious behavior | Manages access controls to prevent unauthorized access and potential breaches |
| Compliance | Simplifies compliance by providing audit trails and reports on entitlements | Facilitates compliance by providing a centralized platform for managing user identities and access privileges |
| Automation | May offer automated remediation actions for security risks (quarantine accounts, revoke permissions) | Often automates user provisioning and de-provisioning |
| Focus | Proactive threat detection and entitlement management for cloud security | Identity governance and access control across various IT resources |
CIEM vs IAM: Choosing the Right Tool for Your Needs
When it comes to choosing between CIEM and IAM, the answer depends on your specific cloud security requirements. Here’s a breakdown to guide your decision:
Use CIEM if:
- Your organization heavily relies on cloud services (public, private, or hybrid)
- You need granular control over cloud entitlements and permissions
- You require continuous monitoring and risk detection for suspicious activity in the cloud
- Enforcing least privilege and streamlining compliance for cloud resources are priorities
Use IAM if:
- You have a mix of on-premises, cloud, and hybrid IT environments
- You need a centralized platform to manage user identities and access controls across various systems
- Simplifying user provisioning, de-provisioning, and access management is a key concern
- Enhancing overall security posture and meeting compliance requirements are your primary goals
Consider both if:
- Your organization is experiencing significant cloud migration and requires a comprehensive security strategy
- You need robust identity governance across all IT resources alongside in-depth cloud entitlement management
Taking Action: Building a Secure Cloud Environment
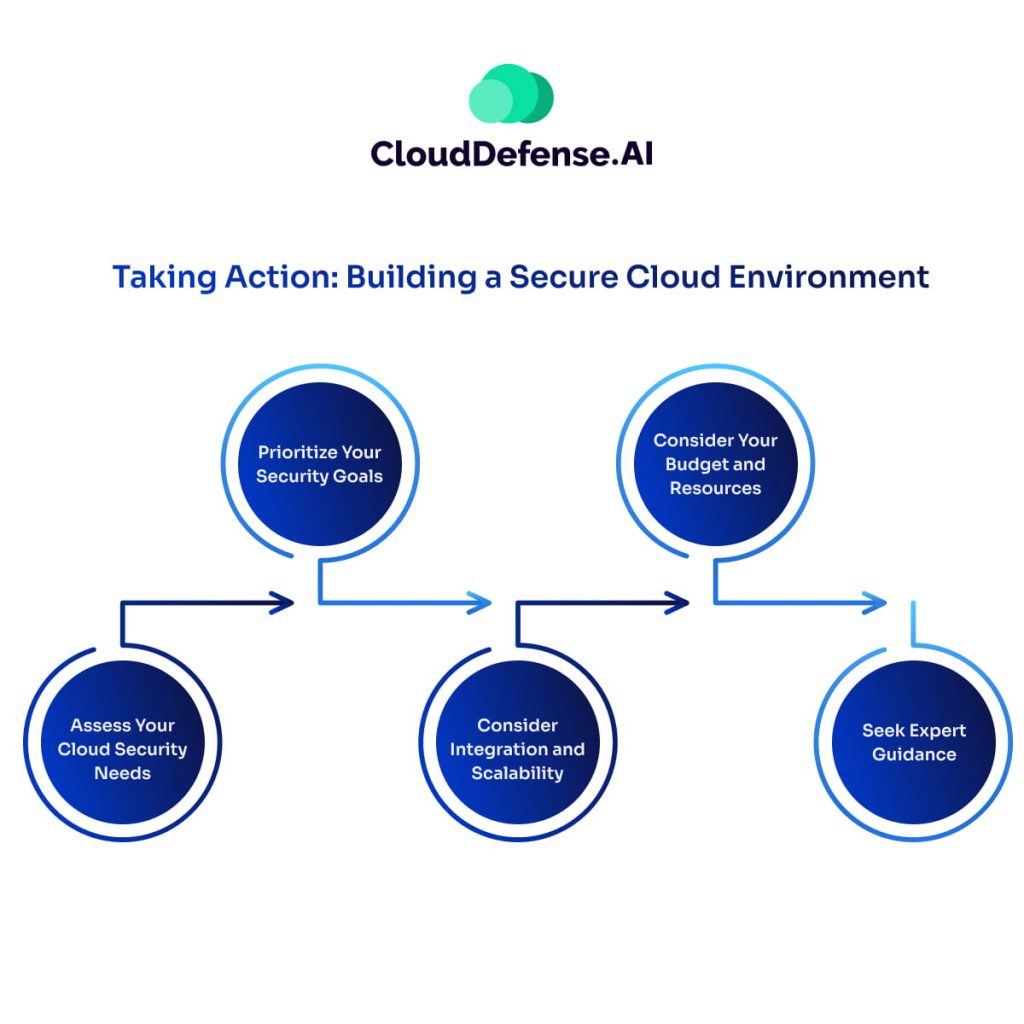
Now that you understand the strengths of CIEM and IAM, let’s delve into how you can leverage these tools to build a robust cloud security strategy. Here are some key considerations:
1. Assess Your Cloud Security Needs:
- Where is your organization on the cloud journey? Are you just dipping your toes in, or are you heavily reliant on cloud services?
- Where are your data and resources stored? Is it a mix of on-premises and cloud environments, or are you primarily cloud-based?
- What access control measures are you currently using? Do you have a centralized IAM system in place?
- What kind of data are you storing in the cloud? The sensitivity of your data will influence the level of security required.
- Have you experienced any security incidents in the past? If so, understanding the attack vectors can help you choose the right tools for prevention.
By reflecting on these questions, you can gain a clearer picture of your specific security needs.
2. Prioritize Your Security Goals:
- Are you primarily concerned with preventing unauthorized access across all IT systems? This might point towards a robust IAM solution.
- Do you need in-depth visibility and control over permissions within your cloud environment? CIEM could be a valuable addition.
- Are compliance regulations a major concern? Both IAM and CIEM can simplify compliance by providing centralized management and audit trails.
Identifying your key security goals will guide your decision on whether to implement CIEM, IAM, or a combination of both.
3. Consider Integration and Scalability:
- Do your existing security tools integrate seamlessly with CIEM or IAM solutions?
- How will your chosen tools scale as your cloud adoption grows?
Choosing solutions that integrate well with your current infrastructure and can adapt to future needs is crucial for long-term success.
4. Consider Your Budget and Resources:
- Do you have the resources to implement and manage both CIEM and IAM? While they offer complementary benefits, they also require dedicated staff and ongoing maintenance.
- Can you prioritize one solution over the other based on your immediate security needs?
5. Seek Expert Guidance:
Cloud security is a complex domain. Don’t hesitate to consult with security professionals who can assess your specific environment and recommend the most appropriate tools and strategies.
By following these steps and leveraging the complementary strengths of CIEM and IAM, you can create a secure and well-managed cloud environment that protects your valuable data and resources.
Remember: There’s no one-size-fits-all approach. The ideal solution depends on your unique environment, security priorities, and resource constraints.
Ready to take the next step toward securing your cloud identity?
CloudDefense offers a comprehensive CIEM solution designed to provide unparalleled visibility and control over entitlements in your cloud environment. Our platform can help you:
- Enforce the least privilege and eliminate excessive permissions
- Continuously monitor for suspicious activity and potential breaches
- Simplify compliance with automated reporting and audit trails
Book a free demo today and see how CloudDefense.AI can help you build a robust cloud security strategy.
Don’t wait to safeguard your sensitive data and resources in the cloud!







