The shift to public cloud infrastructure has brought organizations greater flexibility, scalability, and simplified application management. However, it has also introduced security challenges, particularly around misconfigurations and excessive permissions, especially in multi-cloud environments. Securing access and enforcing security controls can be complex.
Luckily, solutions like Cloud Infrastructure Entitlement Management (CIEM) and Cloud Security Posture Management (CSPM) address these issues. But how do you decide which is right for your organization?
Nothing to worry about, as we have you covered in this extensive guide! We will not only check for the differences between CIEM vs CSPM but also study the benefits of using both of them together. Before we dive into the comparison of these two articles, let’s get a quick overview of how these tools work.
Cloud Infrastructure Entitlement Management (CIEM) Defined
Cloud Infrastructure Entitlement Management (CIEM) is a cloud security solution designed to manage and secure access entitlements across various cloud environments. It focuses on identifying and controlling excessive, unused, or misconfigured permissions, ensuring that only the right users and services have the appropriate access to resources.
By continuously monitoring permissions and roles, CIEM helps prevent privilege escalation and reduces the attack surface, making it a critical tool for maintaining cloud security and ensuring compliance with access control policies.
Read more about CIEM from our CIEM blog
How Does CIEM Work?
CIEM automates the monitoring and management of access privileges across multi-cloud environments. It identifies over-permissive or inactive permissions, reducing security risks by enforcing the Principle of Least Privilege.
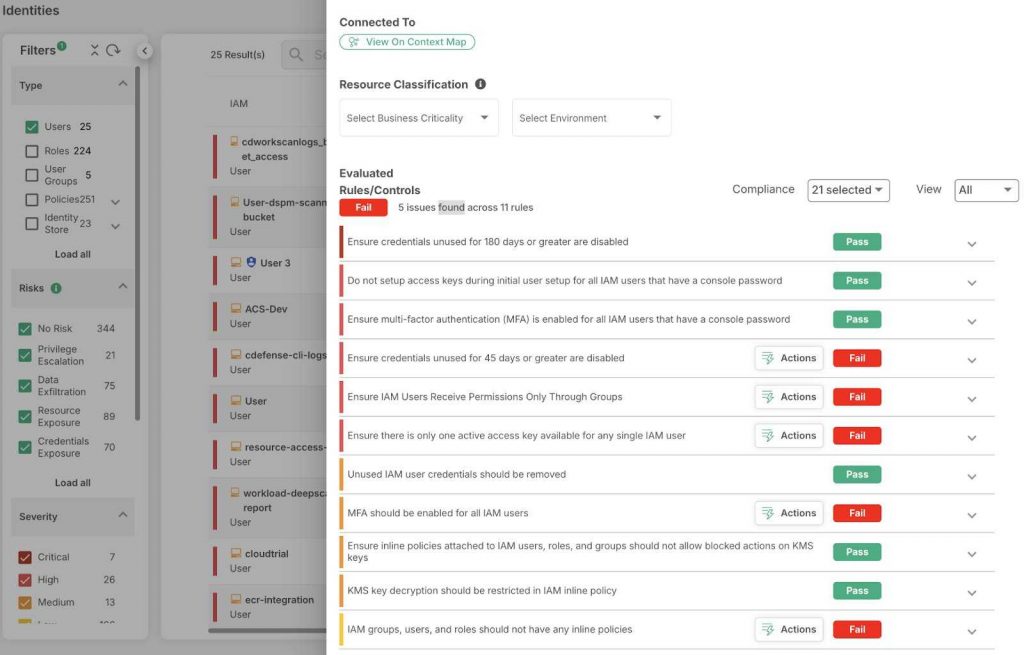
Using AI and machine learning, CIEM continuously monitors for suspicious activity, detects anomalies, and automates the remediation process, such as revoking unnecessary permissions.
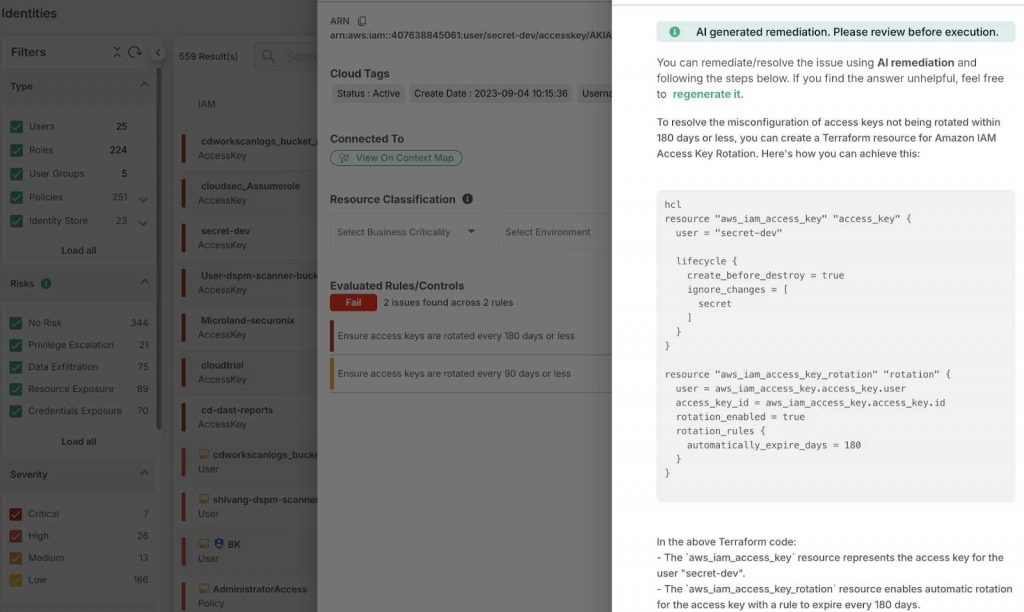
It provides dynamic, context-aware access controls and ensures compliance by offering continuous auditing and reporting, strengthening cloud security and minimizing the attack surface.
Benefits of CIEM
- Reduced Risk of Over-Permission: CIEM continuously monitors cloud entitlements to identify and eliminate unnecessary or excessive access permissions, reducing the risk of insider threats and privilege misuse.
- Enhanced Cloud Security: By enforcing the Principle of Least Privilege, CIEM ensures users have only the access they need, reducing potential attack surfaces.
- Cross-Cloud Visibility: CIEM provides a unified view of access permissions across multiple cloud environments, ensuring consistent security policies.
- Compliance Assurance: CIEM helps maintain regulatory compliance by continuously monitoring access controls and providing audit trails of entitlements and permission changes.
Cloud Security Posture Management (CSPM) Defined
Cloud Security Posture Management (CSPM) is an automated security solution that helps organizations manage and improve their cloud security by identifying and addressing misconfigurations, compliance violations, and risks across cloud environments.
It continuously monitors cloud infrastructure, ensuring adherence to best practices and security policies. CSPM tools detect vulnerabilities, offer remediation recommendations, and help maintain compliance with industry standards, minimizing the risk of data breaches and security incidents in multi-cloud or hybrid-cloud setups.
Read more about CSPM from our CSPM blog
How Does CSPM Work?
CSPM continuously monitors cloud environments for misconfigurations, compliance risks, and security vulnerabilities. It compares current configurations against security best practices and predefined policies, identifying potential threats or violations.
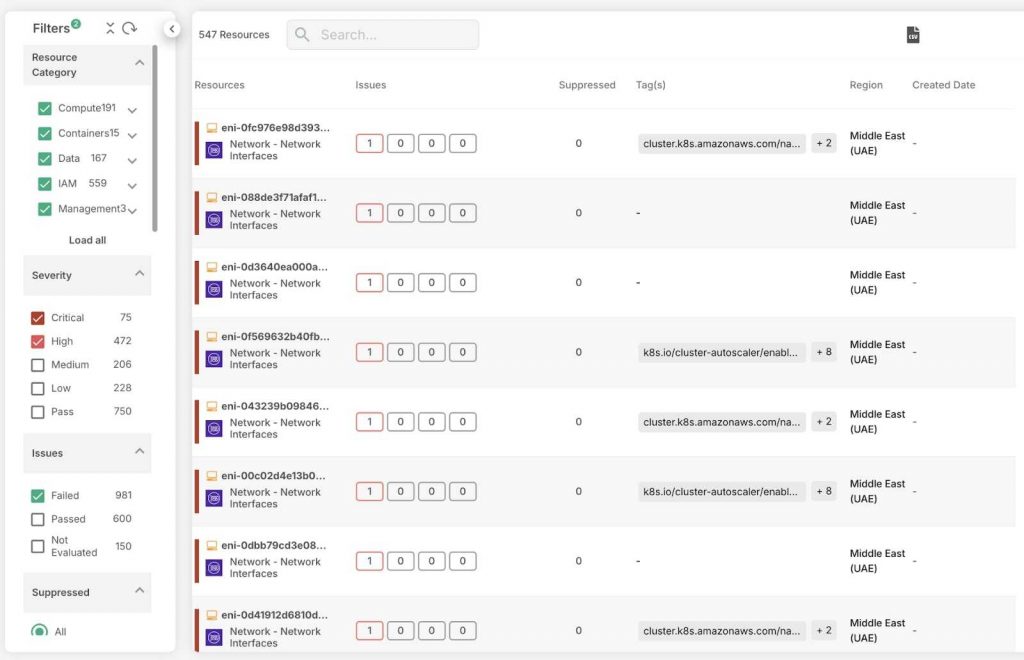
CSPM provides automated or manual remediation recommendations based on the cloud environment, ensuring optimal security. It also supports compliance with regulatory standards like HIPAA by automating the detection and correction of misconfigurations, helping organizations maintain a secure and compliant cloud infrastructure.
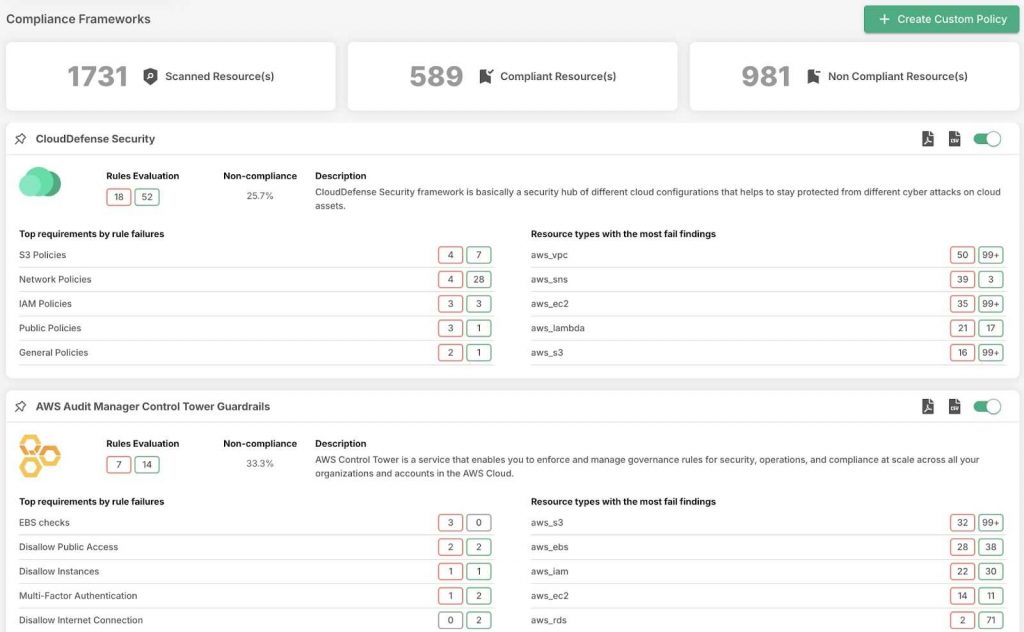
Benefits of CSPM
- Continuous Monitoring: CSPM continuously scans cloud environments to detect security misconfigurations and compliance gaps, ensuring real-time visibility into potential risks.
- Compliance Checks: It simplifies regulatory compliance by automatically checking cloud resources against industry standards like HIPAA, PCI-DSS, and GDPR.
- Misconfiguration Remediation: CSPM identifies and provides actionable recommendations to fix cloud misconfigurations, reducing the risk of exploitation.
- Enhanced Security Posture: By maintaining consistent security configurations across cloud environments, CSPM strengthens an organization’s overall security.
- Multi-Cloud Support: CSPM tools offer centralized security management, simplifying cloud security across multiple cloud platforms like AWS, Azure, and GCP.
Key Differences Between CSPM and CIEM
With a clear understanding of both the terms, lets now move on the understand what exactly makes them different from each other.
Primary Focus
CSPM primarily emphasizes identifying and remediating misconfigurations and compliance issues within cloud environments. In contrast, CIEM concentrates on managing and securing user access rights and entitlements to cloud resources.
Scope of Security
CSPM provides a broader overview of the cloud security posture by continuously monitoring configurations across multiple cloud services. CIEM, however, narrows its focus to specific user permissions, ensuring that access is limited to what is necessary and appropriate.
Risk Mitigation Approach
CSPM aims to reduce risks associated with misconfigurations and compliance violations that can lead to security breaches. CIEM works to mitigate risks related to excessive or unnecessary user privileges, preventing insider threats and unauthorized access.
Implementation Timing
CSPM tools are generally implemented to assess the security posture of cloud environments after they are deployed, continuously monitoring for changes. CIEM tools, on the other hand, are used throughout the development lifecycle to manage and enforce access controls before and after deployment.
Automation and Remediation
While both CIEM and CSPM utilize automation, CSPM focuses on automatically detecting misconfigurations and compliance issues, often providing remediation suggestions. CIEM automates the monitoring of user access and entitlements, offering real-time adjustments to permissions to ensure compliance with the principle of least privilege.
CIEM vs CSPM: Differences Comparison
CIEM and CSPM are important aspects of modern cybersecurity solutions where each solution caters to specific security requirements. Even though the primary focus is cloud security, there are some critical differences between the two:
| Cloud Infrastructure Entitlement Management (CIEM) | Cloud Security Posture Management (CSPM) | |
| Primary Goal | The main goal of CIEM is to manage the user’s permission level and mitigate the risk arising from it. CIEM also helps in enforcing security policies. | The primary goal of CSPM is to mitigate misconfiguration and compliance risks arising in the cloud environment. |
| Main Scope | CIEM is only designed to manage user and system privilege and access control to various resources in the cloud infrastructure. | CSPM not only helps an organization by mitigating misconfiguration and compliance risks but also helps in covering best security practices. |
| Main Function | Complete control and management of users’ access permissions to resources. | Real-time monitoring of cloud infrastructure configuration for security and compliance adherence. |
| Secondary Functions | Management of entitlement lifecycle along with right-sizing the level of user’s access. Continuous monitoring and identification of risks originating from unauthorized entitlement. | Discovery of misconfigurations, vulnerabilities, and compliance risks in the cloud infrastructure. Implementation of best security practices and policies to ensure adherence to industry-specific regulatory standards. |
| Threat Coverage | CIEM focuses on remediating overprivileged access, inactive accounts, unauthorized access, and access detail misuse by threat actors. | CSPM mainly covers threats from misconfigurations, non-compliance risks, and missing updates. |
| Main Use Case | Managing user and system access permission to resources. | Compliance management, assessing security posture, and detection of misconfiguration. |
| Tools Involved | CIEM mainly involves identity and access management tools. | CSPM encompasses automated policy enforcement, API integration, and continuous monitoring. |
| Scalability | It would offer the same entitlement management with an increasing number of users or roles. | It adapts according to the growth of the cloud infrastructure. |
| Suitable For | Entitlement and access control management. | Configuration and compliance management. |
Use Cases for CIEM and CSPM
CIEM and CSPM are essential tools that have a range of use cases in the cloud computing industry. Here’s a look at their specific applications.
CIEM Use Cases
- Multi-Cloud Access Management: CIEM simplifies permission controls across diverse cloud environments. For example, Netflix uses CIEM to manage AWS permissions, ensuring appropriate access for development teams.
- Zero Trust Architecture: Financial institutions use CIEM to enforce a zero-trust model, reinforcing security by verifying access continuously.
- Minimizing Insider Threats: Healthcare providers use CIEM to monitor access to sensitive patient data, reducing risks from insider threats.
- Automated Access Reviews: Rapidly growing companies, especially in hospitality, benefit from CIEM’s automation of user permission reviews, which makes it easy to manage access.
CSPM Use Cases
- Consistent Security Practices: CSPM ensures uniform security configurations across multiple cloud providers, which is crucial for multinational corporations managing AWS, Azure, and Google Cloud.
- Automated Compliance Checks: E-commerce businesses rely on CSPM to regularly scan for vulnerabilities and compliance issues, enhancing their security posture.
- Proactive Misconfiguration Prevention: CSPM helps financial services identify and remediate misconfigurations before they lead to security breaches.
- Cloud Security Visibility: CSPM offers insights into an organization’s cloud security status, aiding in strategic decision-making.
- Continuous Regulatory Compliance: Healthcare organizations employ CSPM to ensure compliance with standards like HIPAA, maintaining security and regulatory adherence.
CIEM and CSPM Combined in a CNAPP
Choosing between CIEM and CSPM and deciding which solution will be better for the cloud can In the rapidly changing landscape of cloud security, the integration of CIEM and CSPM within a Cloud-Native Application Protection Platform (CNAPP) offers a complete defense strategy. This approach emphasizes the complementary strengths of both tools, enhancing the overall security effectiveness.
- Unified Visibility: A CNAPP brings together data from CIEM and CSPM to give organizations a clear view of their cloud security. By combining access management with configuration monitoring, businesses can quickly spot vulnerabilities and misconfigurations. This all-in-one visibility reduces the need for manual data checks, making security operations more efficient and speeding up response times.
- Streamlined Threat Response: Integrating CIEM and CSPM in a CNAPP streamlines processes, making threat detection and response more effective. When security problems occur, CIEM can quickly change user permissions, while CSPM fixes configuration issues. This teamwork allows security teams to act quickly against threats, lowering the chances of successful attacks.
- Proactive Risk Mitigation: By correlating access control data with configuration information, CNAPP empowers organizations to adopt a proactive approach to risk management. CIEM identifies excessive or unnecessary user permissions that may lead to insider threats, while CSPM continuously monitors for misconfigurations that could expose vulnerabilities. Together, they create a layered defense, minimizing the risk of cyberattacks.
- Simplified Compliance and Governance: The integration of CIEM and CSPM within a CNAPP simplifies compliance with industry regulations. By providing a unified framework for managing access controls and monitoring configurations, organizations can demonstrate adherence to regulatory standards more efficiently. This consolidation enhances accountability and streamlines reporting processes.
FAQs
What is the difference between CIEM and SIEM?
CIEM focuses on managing user access and entitlements in cloud environments to reduce risks, while SIEM centralizes security event data from various sources, providing analysis and incident response capabilities for overall threat detection and compliance monitoring.
What is the difference between CSPM and SSPM?
CSPM (Cloud Security Posture Management) focuses on identifying and mitigating misconfigurations and compliance risks in cloud environments, while SSPM (SaaS Security Posture Management) explicitly addresses security risks associated with SaaS applications, including data security and user access management.
What is the difference between CSPM and CNAPP?
CSPM (Cloud Security Posture Management) primarily focuses on identifying and correcting misconfigurations in cloud environments, while CNAPP (Cloud-Native Application Protection Platform) offers a broader security framework, integrating CSPM with runtime protection, workload security, and compliance across cloud-native applications.
What are the Best CIEM and CSPM Solutions?
Top CIEM and CSPM Vendors
- CloudDefense.AI (providing both CIEM and CSPM features)
- Prisma Cloud by Palo Alto Networks
- Sonrai Security
- Zscaler Cloud Protection
- Check Point CloudGuard
- CloudKnox Security
- Ermetic
These are some popular CIEM and CSPM tools that offer a range of capabilities to enhance your cloud security posture and manage access effectively across various environments.







