When it comes to communicating through text, video, or voice message, the Internet serves as the only medium that facilitates such communication. However with increase in usage of communication, the number of cyber incidents has also increased.
Thus protecting those communications has become an important requirement for every organization. Whether you send messages through WhatsApp, video call using Zoom, or communicate through Facebook, organizations employ a lot of processes to secure the messages.
End-to-end encryption, or E2EE, has proved to be the most effective security protocol for organizations to safeguard communication and prevent everyone except the sender and recipient from reading the communication.
Despite the robust security measures, nothing is impenetrable to potential security breaches. So you must be thinking, can end-to-end encryption be hacked? How does it work, and what are the advantages of E2EE? Well, today we are going to discuss whether end-to-end can be hacked and other details.
What is End-To-End Encryption (E2EE)?
End-to-end encryption (E2EE) is a highly secured communication method that ensures all the data sent from the sender to the recipient are entirely encrypted.
Through this security method, all the data is completely encrypted and can only be decrypted at the recipient’s device. The core principle of end-to-end encryption lies in the formation of a secured communication channel where third parties can’t intercept the communicated data. Apart from the sender and recipient, no one can access the data being communicated through the channel.
Whether it is service providers, government, hackers, or internet service providers, no one will be able to view the communicated data. In end-to-end encryption, the data gets encrypted at the device level, meaning the text, voices, emails, or files are encrypted on the sender’s device and get decrypted once the data is received at the intended sender’s devices.
The application that applies E2EE on the sender’s data not only turns the communicated data into a ciphertext but also creates a public-private key pair. The public key is used for encrypting the data at the origin, while the private key is used for decrypting the data.
In the modern era of data breaches and unauthorized access to sensitive information, E2EE’s data scrambling technique has become pivotal for protecting user privacy and securing digital communication.
Why Is End-To-End Encryption Important?
End-to-end encryption has become a valuable aspect of modern cybersecurity as it has enabled users to securely and efficiently transmit data from one device to another. However, E2EE is more than just securing your data; it is crucial for various reasons. Here are the primary reasons that make end-to-end encryption important;
Data Security
The primary reason behind end-to-end encryption is data security because it prevents anyone from intercepting the data and viewing or manipulating it. E2EE mitigates the chance of unauthorized access and data breaches by encoding all personal messages, financial transactions, and confidential business data.
Complete Privacy Protection
E2EE is responsible for creating a secure and private transmission environment that ensures complete privacy of the data that flows between the users. It encodes the data in such a manner that only the sender and intended recipient can access the message. It prevents malicious actors or service providers from surveillance or manipulation of data.
Trust Building
In modern times where every user emphasizes on the security of their communication, E2EE through its comprehensive approach helps build trust between the user and the communication platform. When a communication platform implements E2EE, it showcases the organization’s commitment to user data protection and confidentiality.
Compliance With Regulations
End-to-end encryption plays a vital role in many businesses to comply with various data privacy and protection regulations such as HIPAA and GDPR. As it ensures all the data is protected during transmission, it complies with all the regulatory requirements. Most importantly, it has become a primary part of cybersecurity strategy.
Protection Against Fraud
When it comes to preventing third-party individuals or cybercriminals from frauding users, E2EE plays a pivotal role as it eliminates the chance of message tampering. It completely prevents any malicious actor from altering the communicated data. Even if malicious actors can change the message, it would alert the user that the data has been compromised.
How Does End-To-End Encryption Work?
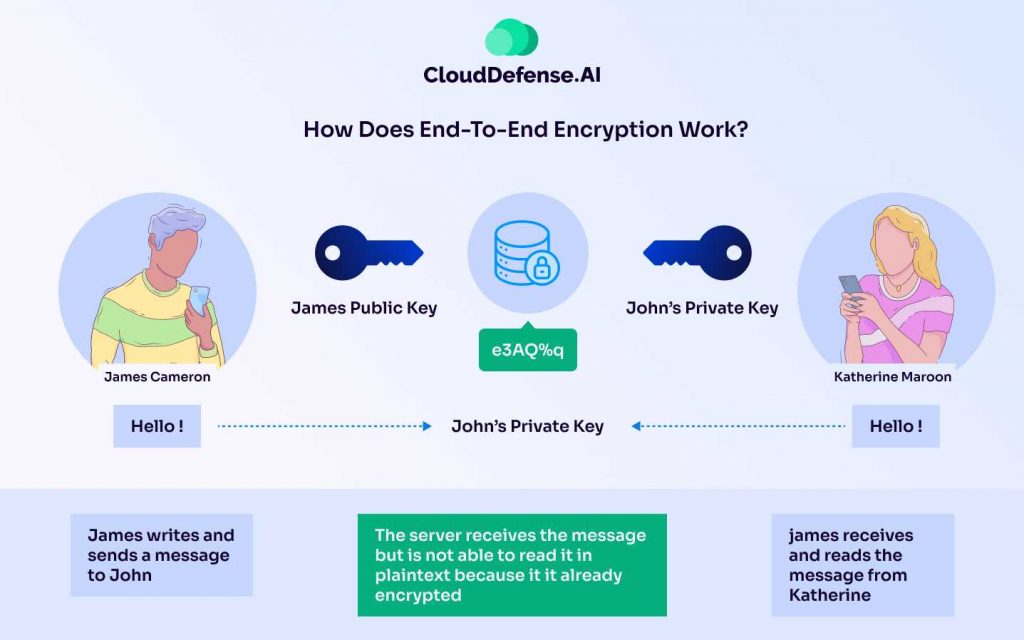
The working of end-to-end encryption is based on asymmetric cryptography, where two separate keys are generated for encrypting and decrypting data at the device level. Through the asymmetric encryption methodology, two cryptographic keys are created: public key and private key.
Organizations may use various key generation algorithms, such as Azure Key Vault or AWS Key Management Services, to generate encrypted keys. Public keys that are used for encrypting the data are accessible to every authorized user in the organization, and they can use it for encrypting specific communication.
However, the communicated data can only be decrypted by the correct private key, which is only known to the respective end user. The private key is designed to remain confidential, and only the intended user can use it to decipher the encrypted data.
An encryption algorithm such as Kyber or Falcon is employed for encrypting the data before it is sent to the intended user. Through the encryption algorithm, plain messages are converted to ciphertext, and images or videos are converted into binary format.
Along with the encryption algorithm, a decryption algorithm is also used to decrypt the data with the correct private key.
In the client-side processing, the encryption and decryption operation occurs on the device level rather than the server level. Client-side processing is vital for end-to-end encryption working.
Advantages of End-To-End Encryption
End-to-end encryption creates a secured communication method that prevents unauthorized users from accessing the data during transmission. Like other security methodologies, it too has many advantages, and they are;
Complete Security and Privacy
One of the primary advantages of E2EE is that it ensures complete security and privacy of the communicated data. Through complete encryption, it ensures only the sender and recipient user can read the message, and no one can explore the data. It not only helps protect sensitive information during communication but also maintains the privacy of the data.
Added Security Layer
By implementing E2EE, organizations can introduce an added layer of security to their existing security infrastructure and keep the data inaccessible to third-party individuals. The message transmitted remains confidential even if hackers manage to intercept it during transmission. E2EE also keeps the data stored in the server in encrypted form so during data breaches, malicious actors won’t be able to access the messages.
Maintain Data Integrity
End-to-end encryption is tasked with maintaining data integrity for an organization by protecting them against tampering. E2EE ensures that the message remains unaltered during transmission. If third-party individuals make any modification to the message, the recipient will get an alert regarding tampering.
Protect Against Surveillance
Thanks to E2EE, malicious actors, organizations, and government agencies can’t perform unauthorized surveillance on the messages sent from one device to another. It also prevents unauthorized entities from accessing the communicated data and makes sure all the information remains private, even if it is intercepted. It has been beneficial for journalists and activists in protecting free speech and getting monitored by government agencies.
User Control
End-to-end encryption enables users to control the privacy of the message they are sending. Through different Android messaging platforms, users can turn the E2EE on or off while sending messages to another device.
Adhere To Compliance Requirement
By implementing end-to-end encryptions, organizations can maintain compliance with different data regulations and government laws on data protection. E2EE makes sure all the data is protected through encryption, and this aspect helps organizations adhere to every regulation. It also enables organizations to avoid legal repercussions in case of data breaches.
Communicating Sensitive Information
Almost every organization in modern times has benefited from end-to-end encryption because it has allowed them to maintain complete confidentiality during communications. Organizations from legal services, healthcare, and finances rely on E2EE because it helps them communicate patient data, confidential data, or legal documents with complete protection.
Challenges of End-To-End Encryption
End-to-end encryption is an incredible security methodology that has done wonders for many organizations through its robust security benefits. However, it also has many drawbacks, including;
Visible Metadata
Every communicated message has metadata, which carries vital information like data, time, participants, and other details of the message. These metadata aren’t encrypted, and they stay visible during communication. Malicious actors can take advantage of the metadata for intercepting the communication.
Issue With Key Management
One of the biggest challenges of E2EE is the complexities of the key management system. You will have to utilize a robust key management system that will not only help you distribute, revoke, and store encryption keys but also prevent loss of them. Organizations that manage the encryption key adequately often tend to lose the encryption key to hackers.
Lower Processing Speed
Implementing end-to-end encryption leads to lower processing speed that ultimately hampers the user experience. The organization has to maintain high resource availability to maintain a smooth user experience, which leads to increased maintenance. Cloud-based infrastructure has been instrumental for organizations because it allowed organizations to counter overhead and maintain a smooth experience.
Vulnerable Endpoints
Even though end-to-end encryption creates a secured communication channel, if the endpoint is compromised, then the malicious actors can view all the content of the message. When an endpoint is compromised, it will allow attackers to get a full view of the content before encryption.
Misusing For Illegal Activities
E2EE doesn’t allow anyone to view the contents of the encrypted messages, and this allows malicious actors to misuse their privacy to perform illegal activities. Law enforcement faces many challenges in monitoring and intercepting these kinds of encrypted communications.
Spread of Misinformation
Since the service provider and government can’t regulate the type of content that is sent through end-to-end encryption communication, it enables users to spread misinformation. Moreover, it becomes a severe challenge for government agencies to track the origins of rumors.
User Safety
E2EE may allow users to send messages with complete privacy, but it can also create an online space where users might be subjected to cyberbullying and hate speech. Neither the service provider nor government agencies can completely regulate such activities, as they can’t intercept all the messages. This causes an impact on the user’s safety and makes them vulnerable to harmful activities.
Can End-To-End Encryption Be Hacked?
End-to-end encryption has allowed modern organization to strengthen their security posture by enabling them to communicate messages securely. The main motive of E2EE lies in creating a secure channel for communication.
However, in modern times, no current security mechanism is secured, and even end-to-end encryption can be hacked. Modern security technologies have advanced in many ways, but still, no system is entirely impenetrable against modern cyber-attacks.
Although it might take a considerable amount of time to view the content of an end-to-end encrypted message fully, modern hackers have been successful a few times in breaching secured communication channels.
By using advanced computational resources and modern techniques, hackers were able to exploit various vulnerabilities and get access to unauthorized data. Since end-to-end encryption is evolving with time, it has become highly complex for hackers to intercept the encrypted messages. To avoid the complexities, most malicious actors are now stealing the encryption keys for intended messages or finding ways to get access to data before they are encrypted. Weak encryption algorithms can also make the E2EE vulnerable and allow malicious actors to access sensitive data during communication.
Moreover, E2EE is ineffective against malware or phishing attacks, making the system vulnerable to hackers. Various organizations are investing heavily in end-to-end encryption to stay ahead of advanced security threats and allow them to safeguard all the communicated data.
E2EE can’t alone prevent data breaches, and organizations, as well as users, have to enhance security measures and stay vigilant to prevent breaches continuously.
Using FIPS-approved algorithms, anti-malware software, and strong security patches can help organizations protect against any data breaches.
FAQ
Is encryption safe?
Encryption is considered to be one of the safest ways to protect sensitive information during communication between two users. Encryption is considered entirely safe when it is appropriately implemented.
The use of a highly efficient encryption algorithm, complex encryption keys, best security practices, and regular security patches can help an organization strengthen its encryption. However, no encryption is considered foolproof, and hackers can exploit various vulnerabilities to intercept the encrypted data.
Can hackers get through encryption?
Theoretically, hackers can’t open encrypted data because the encrypted data is completely scrambled, and encryption keys are needed to decrypt the incoming data. However, no encryption is impervious to data breaches, and modern hackers are using sophisticated methodologies to gain access to sensitive data. Hackers are also making efforts to obtain an encryption key or break the encryption algorithm to decrypt the data.
What Can’t End-To-End Encryption Do?
End-to-end encryption is an incredible tool that offers a lot of security aspects, but it, too, has some limitations, and there are things it can’t do. A significant issue with E2EE is that it can’t protect the metadata, and it remains visible to everyone.
Importantly, E2EE is ineffective against any vulnerability in intermediary servers that may exploit the secured communication. End-to-end encryption also can’t protect the endpoints that have been compromised by hackers, and anyone with a decrypted key can explore the content of the message.
Can hackers see encrypted data?
Hackers can’t explore the content of the encrypted data as the data is unreadable without an encryption key. However, if the hacker can access the decryption key or break the encryption algorithm, then they can open the encrypted data. A compromised device also gives leeway to the hackers to explore the encrypted data.
Conclusion
In modern times, end-to-end encryption has become a pivotal tool for creating a secured communication channel for users to communicate sensitive data over the Internet. It provides the security and privacy that every user needs to engage in an online conversation without worrying about being eavesdropped.
Organizations are working to strengthen the E2EE tool so that users can securely send and receive all the data over the Internet. However, theoretically, E2EE can be hacked, and hackers with high expertise can break the algorithm or steal the encryption key to explore the encrypted data.







