With security threats increasing daily, businesses can’t afford gaps in their defenses. Building an effective vulnerability management program means proactively identifying, assessing, and fixing security flaws before attackers can exploit them.
But where do you begin, and how can you make sure your program stays effective over time? This guide covers eight actionable steps to help you create a comprehensive and resilient program that secures your organization, protects your assets, and minimizes risk. Because when it comes to cybersecurity, being proactive isn’t optional—it’s critical.
What Is a Vulnerability Management Program?
Before we proceed, you need to know the vulnerability management program (VMP) definition and what it means for you. A Vulnerability Management Program is a strategic process designed to continuously identify, evaluate, and address security weaknesses within an organization to minimize cyber risks.
It focuses on:
- Assessing and prioritizing vulnerabilities across IT assets.
- Integrating tools, processes, and systems for seamless vulnerability mitigation.
- Ensuring compliance with industry regulations and standards.
- Engaging key stakeholders for enterprise-wide security alignment.
Hackers exploit weak systems quickly, making it crucial to have a structured program that proactively manages vulnerabilities. By doing so, you enhance your organization’s security, avoid costly breaches, and ensure continuous improvement in your defense strategy.
| Read More: For a deeper dive into the fundamentals of vulnerability management and how it fits into your cloud security strategy, check out our exclusive article on What is Vulnerability Management? |
Difference Between Risks, Threats, and Vulnerabilities
Knowing the difference between risks, threats, and vulnerabilities isn’t just for security experts—it matters for every organization trying to stay ahead in the cyber arms race.
Why? Because understanding what you’re up against and how to prioritize fixes can be the difference between prevention and disaster. Clarity here saves time, money, and probably some sleepless nights.
Here’s the breakdown:
- Risk: The potential for loss or damage when a vulnerability is exploited. It’s the “what if” scenario—think of it as your possible downside.
- Threat: Anything that could exploit a vulnerability—like hackers, malware, or even an internal error. This is what you’re protecting against.
- Vulnerability: Weak points in your defenses—like unpatched software or poor configurations. These are what threats target.
Vulnerability Management vs. Patch Management:
- Vulnerability Management is the broader, ongoing process of identifying, assessing, prioritizing, and remediating vulnerabilities. It’s strategic, holistic, and constantly evolving.
- Patch Management is focused on deploying updates to fix specific vulnerabilities. Think of it as one critical tool in the larger arsenal of vulnerability management.
Understanding these distinctions helps you build smarter security strategies, knowing exactly where and how to act. Because in cybersecurity, precision matters.
Benefits of Vulnerability Management Program
The COVID-19 pandemic accelerated digital transformation at lightning speed, but it also blew the doors open for cyber attackers. Cybercrime surged by 600%, according to the United Nations Office on Drugs and Crime (UNODC). Ransomware attacks alone happen every 11 seconds, causing $20 billion in damages in 2021. It’s wild.
Here’s where a solid Vulnerability Management Program (VMP) steps in and makes a real difference:
- Security and Risk Reduction: Businesses and governments are prime targets. VMPs shore up defenses, safeguarding digital assets and cutting down risk exposure.
- Achieving Compliance: A well-managed VMP keeps systems fortified, helping you meet industry standards and boosting compliance. Better security isn’t just a benefit; it’s a business booster.
- Data Protection: Safeguard essential company data—because breaches aren’t just expensive; they’re reputation-killers.
- Protects Against Legal, Financial, and Reputational Damage: A proactive approach wards off future reputation damage, legal nightmares, and costly infrastructure harm.
- Strategic Security Investments: VMP insights allow you to invest smartly—targeting the tools and tech that matter most to your unique cyberspace.
Limitations of Traditional Vulnerability Management Tools
Traditional vulnerability management methods just can’t keep up with today’s speed of change. They’re slow, outdated, and too reactive for the threats we face now. Here’s why they’re not cutting it:
- Reactive, Not Proactive: They wait until vulnerabilities are found, which leaves wide-open gaps for attackers to exploit.
- Manual and Slow: Too many manual processes mean slow response times—by the time something’s fixed, it’s often too late.
- Narrow Focus: Old methods look at individual systems, missing the big picture. Vulnerabilities can slip through the cracks when things aren’t integrated across the board.
- No Continuous Monitoring: Threats evolve fast. Without constant monitoring, new vulnerabilities go unnoticed until they’re exploited.
- Wasted Resources: Without proper risk prioritization, companies waste time fixing less critical issues instead of focusing on what matters most.
Cybersecurity needs to be smarter, faster, and always on. Traditional methods are like driving with one hand on the wheel while the other’s texting. It’s time to shift gears.
7 Steps To Build an Effective Vulnerability Management Program
Building an efficient vulnerability management program is a multi-segmented process that requires you to set up effective protection layers and test them ritually. Follow the eight steps outlined below to get all-round protection from threat actors.
Step 1: Identify and Map Out Your Assets
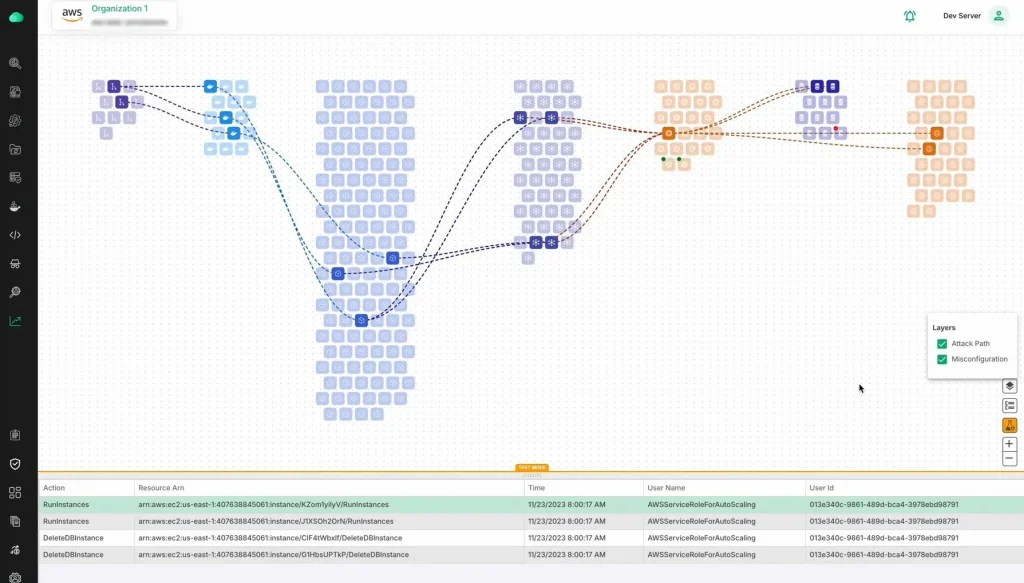
Before you can fix any vulnerabilities, you need to know what you’re protecting. Think about this: Do you know every single device, system, or piece of software running on your network? What about those shadow IT systems your employees might be using without telling you? If you don’t, that’s a problem.
The first step to building an effective vulnerability management program is to discover and map out all your assets. Why? Because vulnerabilities can exist anywhere—from company laptops and mobile devices to cloud platforms and third-party applications. If you can’t see it, you can’t secure it.
Ask yourself:
- Do you have a full inventory of your hardware and software?
- Are you tracking all endpoints, including those remote devices?
- Are cloud services fully integrated into your security view?
Get more specific. Map every asset. Knowing what you have—and where it is—gives you the visibility needed to prioritize risk and focus your efforts where they matter most. Remember, if it’s connected to your network, it’s a potential vulnerability waiting to be discovered.
Step 2: Categorize Vulnerabilities
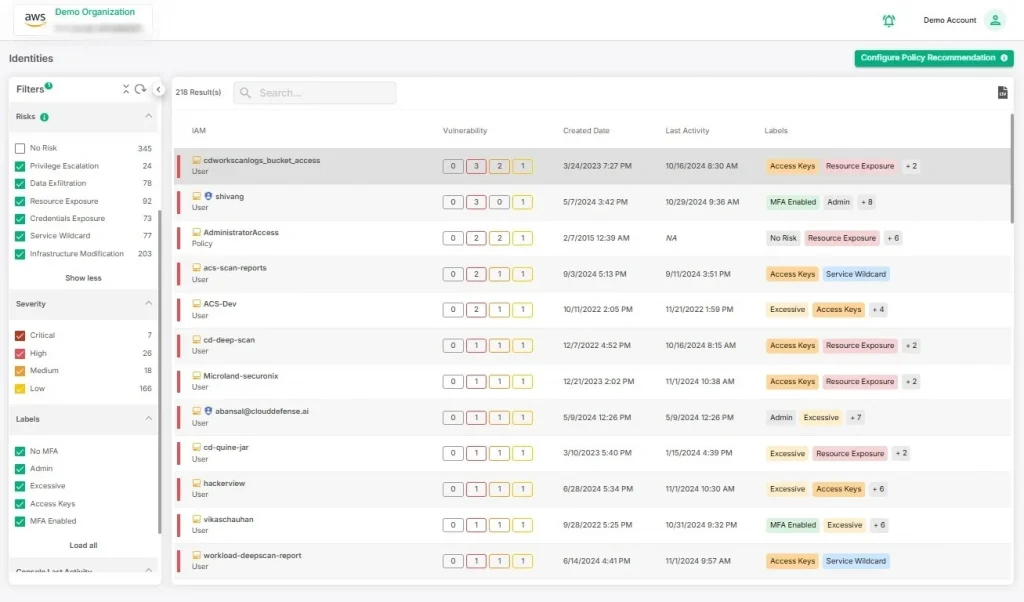
Once you’ve discovered your assets, the next critical step is to categorize vulnerabilities. But how do you know where to start? Not all vulnerabilities are created equal—some could be harmless, while others can lead to catastrophic damage. The key is to prioritize based on severity and impact.
- Which vulnerabilities pose the highest risk to critical assets?
- Are there vulnerabilities that attackers could exploit immediately?
- How would a breach in a specific system impact your business operations?
Start by grouping vulnerabilities into categories like high, medium, and low based on:
- Exploitability – Can attackers easily take advantage of this vulnerability?
- Impact – What would the damage be if this vulnerability were exploited?
- Exposure – How visible or accessible is this vulnerability to external threats?
This helps ensure you’re addressing the most dangerous issues first and not wasting resources on less pressing threats. Don’t treat them all the same—you need to act fast on high-priority vulnerabilities while developing a longer-term strategy for those less critical. Prioritization is everything.
Step 3: Secure Your Cloud-Native Applications
Cloud environments are a double-edged sword—great scalability, but more complexity and more chances for vulnerabilities to slip through. Your cloud-native applications—whether they’re virtual machines, containers, or serverless—need full, end-to-end security. Are you covering everything?
Think about this: Do you have eyes on every corner of your cloud infrastructure? From virtual machines to those ephemeral compute resources, every piece needs constant scanning. If you’re not looking for vulnerabilities like CISA KEV or hidden Log4j dependencies, you’re leaving yourself exposed.
Ask yourself the following questions:
- Can you see every asset in your cloud environment?
- Are all processes being scanned for vulnerabilities in real-time?
- How do you guarantee a fix didn’t create new vulnerabilities?
Vulnerability identification doesn’t stop when you apply a patch. Double-check, validate, and ensure remediation works. You need reporting mechanisms to document everything—from identification to remediation. The insights you gather? They’re critical to optimizing your security strategy for the long run. Keep the system secure, keep iterating, and keep improving.
Step 4: Conduct routine scans.
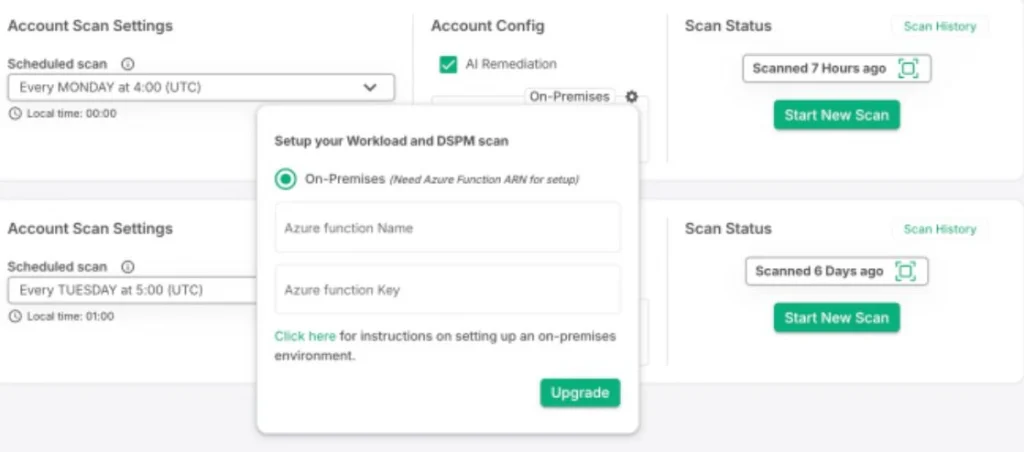
It only takes a few clicks to introduce a vulnerability into your IT ecosystem. With the rise of containers—those compact, reusable code packages running across environments—keeping your infrastructure secure becomes even trickier. In fact, studies show 75% of containers have high or critical vulnerabilities that can be patched. A simple keystroke from a developer, and boom, you’ve got a new risk to manage.
So, why is regular scanning so important?
- Do you have up-to-date visibility on every vulnerability, or are you waiting until something goes wrong?
- Are you scanning consistently, or just when you think something might be wrong?
Regular scans, unlike ad hoc ones, help you stay ahead of the game. Timely, accurate data gives you the power to identify weaknesses before they can be exploited. Industry standards recommend at least quarterly scans, but with constant changes to code or infrastructure, you’ll likely need to scan more frequently.
The key is frequency and relevance. If you’re scanning often enough, you’ll catch vulnerabilities early—and you won’t be playing catch-up when something critical breaks. Keep your scans continuous, relevant, and timely.
Step 5: Configure Policies
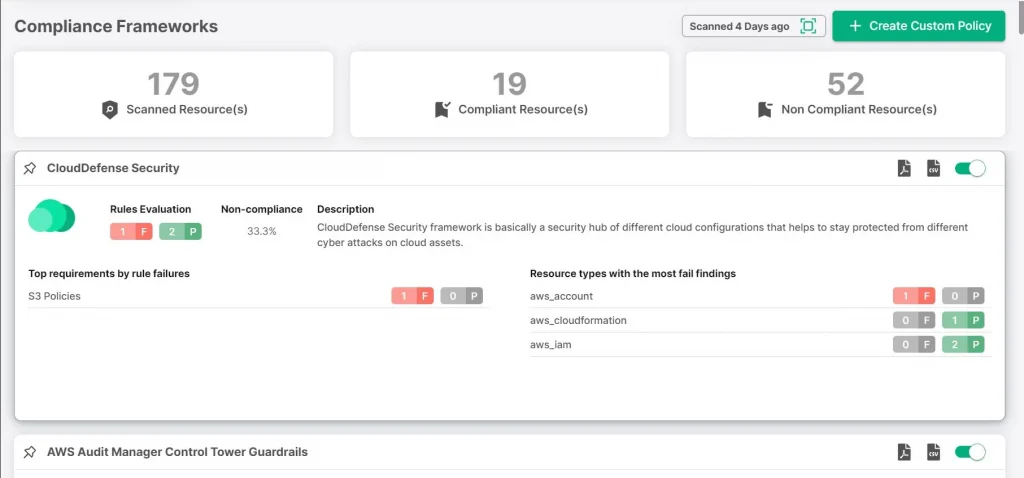
Vulnerability management isn’t one-size-fits-all. Default policy configurations just don’t cut it—they’re too generic and miss critical, organization-specific details. Your business, region, and industry each have unique requirements, and a generic policy won’t address those nuances. Consider these questions:
- Does your current policy reflect your specific security and business needs?
- Are you meeting industry benchmarks, but also accounting for your unique internal challenges?
- Are your policies flexible enough to adapt to new threats and changing business environments?
The key to success here is customization. The best vulnerability management solutions allow you to create tailored policies that align with both your internal and external requirements. Whether it’s meeting regulatory compliance or tackling specific threats, your policies should address every complexity your organization faces.
Don’t settle for default configurations. Your policy should evolve with your business and the security landscape, ensuring your vulnerabilities are managed effectively and continuously.
Step 6: Multi-Cloud Protection
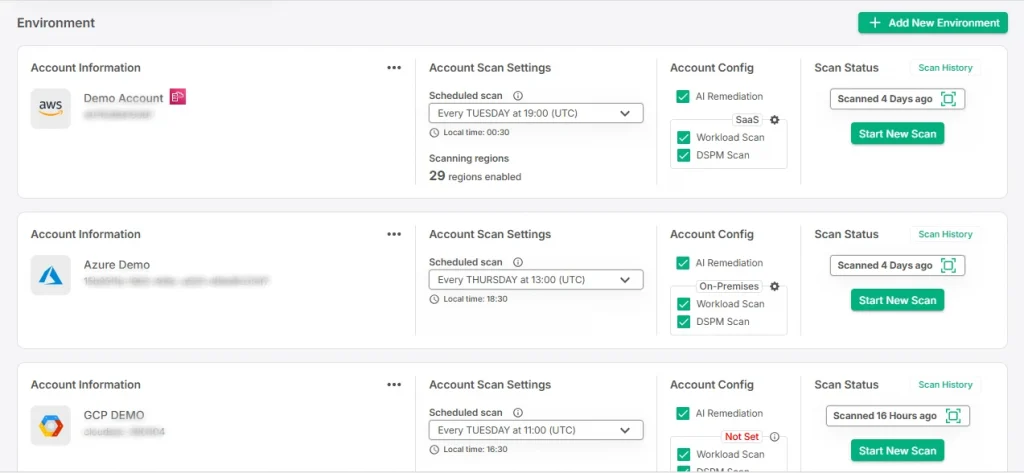
The reality of modern IT networks is that many organizations aren’t just using one cloud provider—they’re using multiple. While this multi-cloud strategy provides flexibility and resilience, it also adds layers of complexity and potential risk. Are you really securing every cloud environment your organization uses?
Take a moment to think:
- Do you have full visibility across all your cloud platforms—AWS, Azure, Google Cloud, etc.?
- Are you consistently monitoring and managing vulnerabilities across all cloud environments, or are some getting left behind?
- How do you ensure consistent security policies are applied across all clouds?
The problem with multi-cloud setups is that they multiply the attack surface. Each cloud provider comes with its own set of tools, policies, and potential vulnerabilities. If your vulnerability management approach isn’t comprehensive across every cloud platform, you’re leaving gaps.
Caution is critical. Use a solution that gives you centralized visibility and security management across all cloud environments. Whether it’s hybrid clouds, multi-cloud, or both, your vulnerability management program needs to work seamlessly across platforms—without compromise. Multi-cloud can be a huge advantage, but it’s only effective if every environment is secured properly.
Step 7: Make an Effective Remediation Plan
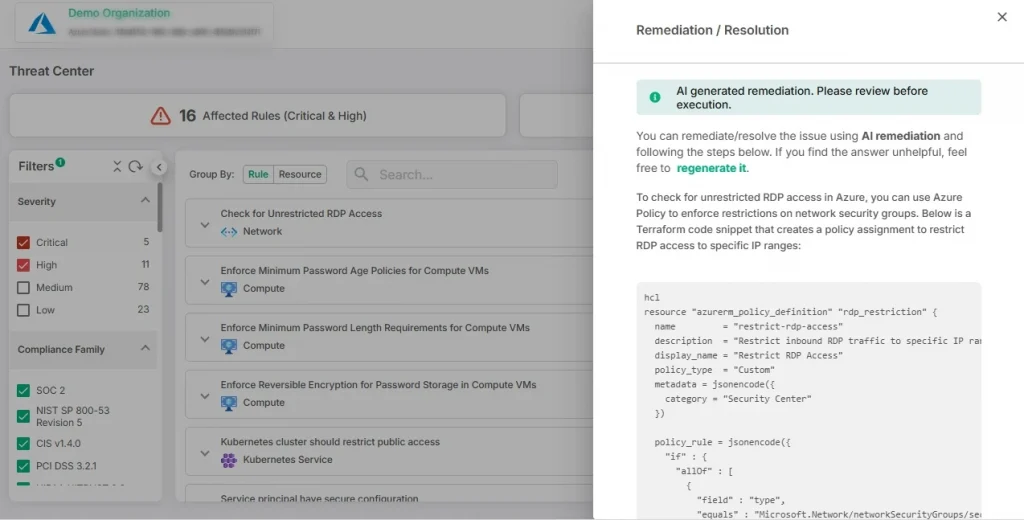
You’ve identified vulnerabilities, you’ve prioritized them, and now it’s time to act. But the big question is: How do you fix these issues efficiently and effectively? A strong remediation plan is key to ensuring vulnerabilities get resolved without introducing new problems.
Ask yourself:
- Do you have a clear, actionable plan for addressing each vulnerability?
- Are you tackling vulnerabilities based on their risk level, with critical ones prioritized?
- Is your team equipped to execute fixes quickly and verify they actually worked?
Your remediation plan should be more than just a list of to-dos. It needs to be structured and goal-oriented, with specific timelines, resources, and responsibilities. Don’t just patch and forget—each fix should be verified to ensure the vulnerability is completely closed and that no new risks have been introduced.
The best plans include:
- Clear prioritization based on the severity of each vulnerability.
- Timely execution, with immediate action taken for high-risk vulnerabilities.
- Post-fix verification to ensure the solution worked and no new issues arose.
And here’s where modern tools can really make a difference. Platforms like CloudDefense.AI provide AI-powered remediation that guides you through simple fixes, making the process smoother and more efficient. This technology helps you identify the best solutions quickly, reducing the complexity of manual remediation and enhancing accuracy.
CloudDefense.AI’s Streamlined Vulnerability Management Approach
All the steps we’ve covered—discovering assets, categorizing vulnerabilities, securing cloud-native applications, configuring policies, and building an effective remediation plan—are crucial for safeguarding your organization. But executing them across your IT ecosystem can be complicated, especially as your infrastructure scales and diversifies. But CloudDefense.AI simplifies all of it.
CloudDefense.AI offers a comprehensive, AI-powered vulnerability management solution that brings automation, integration, and advanced security together in one seamless platform. From automatic vulnerability detection and multi-cloud coverage to AI-based remediation and real-time visibility, CloudDefense.AI covers every aspect of vulnerability management.
Here’s what CloudDefense.AI provides:
- Automated vulnerability scans for continuous monitoring across all systems
- Cloud-native application security with end-to-end views, protecting even the most complex environments
- AI-guided remediation, offering quick and simple fixes based on real-time data
- Customizable policies tailored to your unique business, compliance, and security needs
- Actionable insights to help you strategize your security investments effectively
- Multi-cloud support, ensuring comprehensive security across all platforms
- Regular reporting and validation to confirm that vulnerabilities are effectively managed
Ready to see how CloudDefense.AI can simplify your vulnerability management and strengthen your security posture? Book a free demo today and experience firsthand how our platform can protect your organization from evolving threats.
FAQs
How can you prioritize vulnerabilities effectively?
A vulnerability can be easily prioritized by assessing the risks associated with it and determining how much of an impact it can have on your overall system.
Assessing how risky a vulnerability is can be determined by predicting the amount of damage it can cause if exploited. Additionally, the level of exploitation it offers an exploiter is also a key factor. Finally, the likelihood of such an attack happening can also help to prioritize the vulnerability.
How can you measure the effectiveness of your vulnerability management program?
The best ways to measure the effectiveness of a vulnerability management process are to conduct penetration testing and analyze data obtained from the VMP. A thorough analysis of the data obtained through vulnerability metrics will help assess how swiftly vulnerabilities are handled and give you an overview of the effectiveness of the VMP.
Conclusion
Securing your company’s cyberspace can often be a challenge, with new technologies entering the market every day. However, effectively testing your security measures, educating your staff on cyber threats, and using relevant tools can help tackle that easily.
Discard the idea that operating a vulnerability management system can disrupt company functionality. Instead, embrace that VMPs are a protective measure to ward off any future risks and prevent financial damage. Investing and effectively running a vulnerability management program will not only help secure the infrastructure but will ultimately boost business in the long run.







