What is Penetration Testing?
Penetration testing, often called pen testing or ethical hacking, is a security exercise where a cybersecurity expert attempts to find and exploit vulnerabilities in a computer system. The goal of this simulated attack is to identify weak spots in a system’s defenses that attackers could exploit.
Penetration testing is similar to a bank hiring someone to dress as a burglar and attempt to break into its building and vault. If the burglar succeeds, the bank learns how to improve its security measures. Likewise, organizations use penetration testing to discover and address vulnerabilities before malicious actors can exploit them, helping them stay one step ahead of potential breaches.
Why is Penetration Testing Important?
Penetration testing is like a fire drill for your security systems. It simulates real-world cyberattacks to uncover vulnerabilities before hackers do. By proactively identifying weaknesses, you can patch security gaps and improve defenses, reducing the chances of a data breach.
It’s also a great way to test whether your security measures actually hold up under pressure, helping you stay compliant with regulations that require regular system testing. In short, penetration testing is an essential tool for staying one step ahead of hackers and keeping your organization secure.
Who Performs Pen Tests?
Penetration tests, or pen tests, are best performed by individuals with little to no prior knowledge of the system’s security setup. This approach helps uncover blind spots that developers might miss. Typically, companies hire external contractors, often referred to as ‘ethical hackers,’ to conduct these tests. Ethical hackers have permission to hack into a system to enhance its security.
These ethical hackers come from diverse backgrounds. Many are experienced developers with advanced degrees and certifications in pen testing. However, some of the most skilled ethical hackers are self-taught, including reformed criminal hackers who now use their expertise to improve security rather than exploit it.
What are the Types of Penetration Testing?
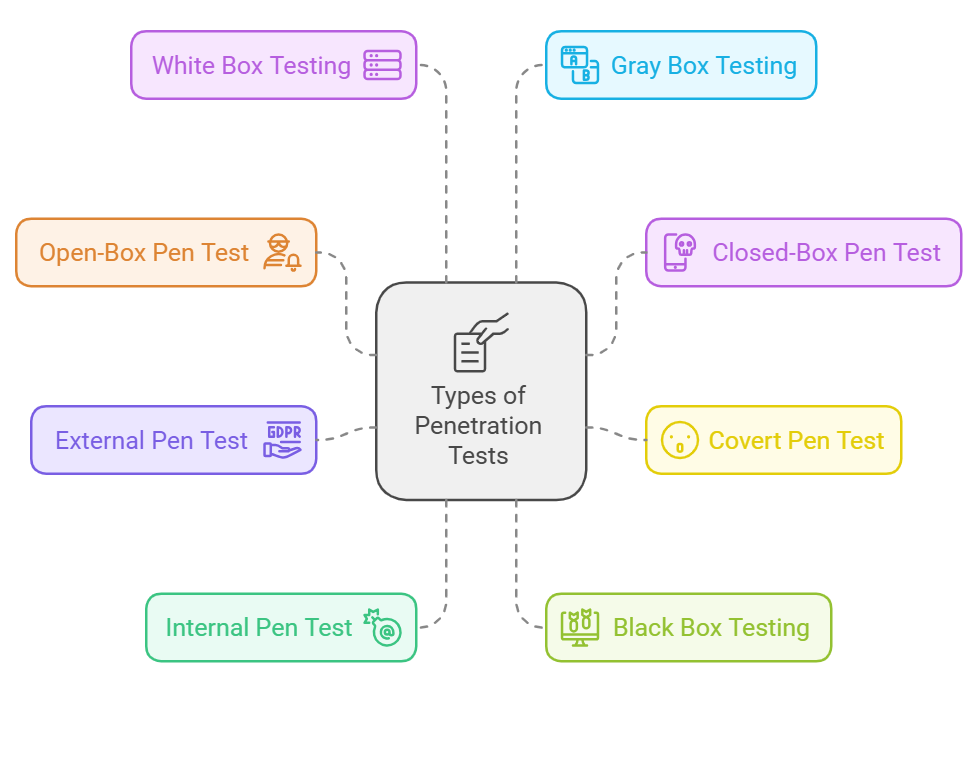
Penetration testing can take several forms, each designed to simulate different attack scenarios and assess how well an organization’s security measures hold up. Here’s a breakdown of common testing techniques:
- Open-Box Pen Test: In this test, the attacker is given some background information about the company’s systems. It’s useful for mimicking insider threats or situations where an attacker has partial access.
- Closed-Box Pen Test: Also known as a “single-blind” test, this approach provides the tester with minimal information. The goal is to replicate an external attack without the tester’s prior knowledge of the company’s systems.
- Covert Pen Test: This is a “double-blind” test where the company’s internal team, including IT and security staff, is unaware of the test. It simulates a surprise attack, assessing how well the organization responds to an unexpected threat.
- External Pen Test: This test focuses on external-facing technologies, such as websites and servers. The tester tries to penetrate the company’s network from outside, testing defenses against remote attackers.
- Internal Pen Test: An internal pen test is conducted within the company’s network, simulating an attack from inside the organization, such as from a disgruntled employee with access to sensitive systems.
- Black Box Testing: In black box testing, the tester is provided with little to no prior knowledge about the company’s network. This approach mirrors real-world cyberattacks and is often time-consuming due to the lack of information.
- White Box Testing: In White box testing, the tester has complete knowledge of the network infrastructure. Though it doesn’t simulate external attacks, it’s ideal for testing insider threats and provides a comprehensive security assessment.
- Gray Box Testing: Gray box testing offers a middle ground between black and white box testing. The tester is given partial information, typically focusing on specific applications. It’s faster than black box testing but still provides valuable insight into system vulnerabilities.
Each of these methods provides unique advantages, helping businesses identify weaknesses in different attack scenarios and strengthen their overall security posture.
How is a Typical Penetration Testing Carried Out?
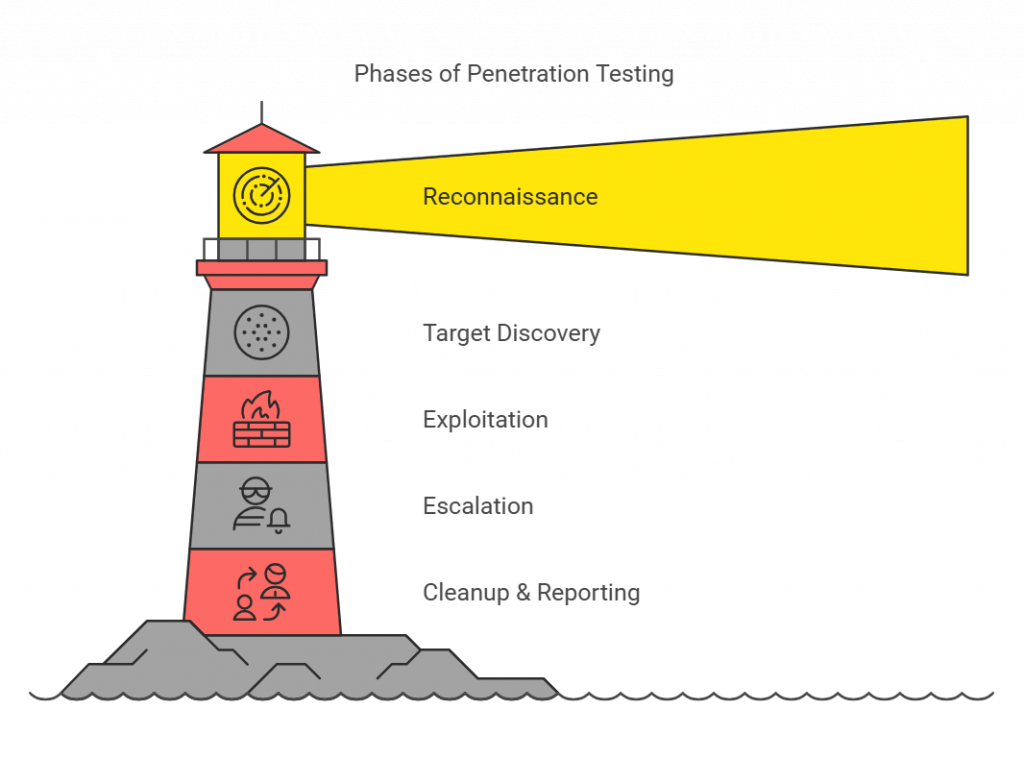
A typical penetration test follows a structured sequence of phases, each designed to simulate different stages of a cyberattack. Here’s a breakdown of the process:
- Reconnaissance: Pen testers begin with reconnaissance, gathering publicly available information about the target. This phase often involves using open-source intelligence (OSINT) tools to analyze domain names, network configurations, and publicly exposed systems. The goal is to map out the target’s attack surface and identify potential entry points.
- Target Discovery and Development: In this phase, testers identify specific vulnerabilities within the target environment. They use port scanning tools, vulnerability scanners, and techniques like social engineering to gather more information. This step might include developing fake scenarios or phishing attacks to trick employees into revealing sensitive data, such as login credentials.
- Exploitation: Once vulnerabilities are discovered, testers attempt to exploit them. Common techniques include SQL injections, cross-site scripting (XSS), and brute force attacks to gain unauthorized access to the system. The purpose here is to test how well the system responds to known attack methods.
- Escalation: After gaining initial access, the penetration testers move on to the escalation phase, where they attempt to elevate their privileges within the system. This phase simulates how attackers might move deeper into the network, establishing persistence and gaining further control over the target system. The goal is to mimic advanced persistent threats (APTs).
- Cleanup and Reporting: Finally, the tester removes all traces of their activities from the system to avoid disrupting operations. They then compile a comprehensive report, detailing all vulnerabilities discovered, attack methods used, and specific recommendations for improving security. This report serves as a roadmap for the organization to fix the identified weaknesses.
What Happens in the Aftermath of a Pen Test?
After completing a pen test, the ethical hacker shares their findings with the target company’s security team. The team then uses this information to implement security upgrades to address any discovered vulnerabilities. These upgrades may include rate limiting, new web application firewall rules, DDoS minimization, and tighter form validations and sanitization. The goal is to strengthen the system’s defenses and prevent future breaches based on the insights gained from the pen test.
How Much Access is Given to Pen Testers?
Organizations grant ethical hackers different levels of access to use the wide range of tools and techniques used by both intentional and accidental hackers.
- Opaque box test: Pen testers start with no prior knowledge of the system, simulating an external hacker probing for weaknesses. This thorough approach can take up to six weeks.
- Semi-opaque box test: provides pen testers with some insight, such as credentials and internal data structures, allowing them to bypass initial trial-and-error phases.
- Transparent box test: Pen testers receive unlimited access to business systems and artifacts, including source code and application design. This approach, requiring sophisticated tools like code analyzers and debuggers, typically takes two to three weeks to complete.
What are the Benefits of Penetration Testing?
Below are key benefits that illustrate why pen testing is a critical component of a strong security strategy.
Uncovering Flaws
Pen testing can identify even the smallest vulnerabilities that, if left undetected, could compromise the entire system. By discovering these issues early, companies can address them before malicious actors exploit them.
Regulatory Compliance
It helps ensure compliance with stringent security and data privacy regulations such as HIPAA and PCI DSS. By adhering to these standards, companies can avoid hefty fines and legal consequences associated with non-compliance.
Staying Current with Cyber Threats
Regular penetration testing keeps IT staff informed about the latest cyber threats and the methods to defend against them. This ongoing education helps maintain a strong security posture and reduces the risk of successful attacks.
What are the Disadvantages of Pen Testing?
Despite its advantages, penetration testing also has its drawbacks. Understanding these disadvantages is crucial for organizations to make informed decisions about integrating pen testing into their security protocols. Here are some of the notable downsides.
Labor-Intensive and Expensive
Penetration testing requires significant time and resources. The process involves detailed planning, execution, and analysis, which can be costly, particularly for smaller organizations with limited budgets.
Does Not Prevent Bugs and Flaws
While pen testing can identify existing vulnerabilities, it does not prevent new bugs and flaws from being introduced into the system during development. Continuous development and deployment processes might still introduce new issues after testing is completed.
Potential for Business Disruption
The testing process can disrupt normal business operations. Testing activities might slow down systems, cause temporary outages, or interfere with regular business functions, leading to potential revenue loss and reduced productivity.
False Sense of Security
Penetration testing might provide a false sense of security. Identifying and addressing known vulnerabilities does not guarantee that all possible threats have been mitigated. New vulnerabilities can emerge, and previously unknown flaws might still exist.
What are the Types of Penetration Testing Tools?
Penetration testing tools are essential for evaluating the security of an organization’s IT infrastructure. These tools fall into five broad categories, each serving a distinct purpose in the penetration testing process:
Reconnaissance Tools
These tools are used to gather preliminary information about the network’s internals. They analyze network traffic to identify patterns, monitor data flow, and detect potential entry points. Reconnaissance tools help testers understand the network’s structure and identify targets for further testing.
Vulnerability Scanners
Vulnerability scanners are designed to discover security issues within an organization’s IT infrastructure. These tools can scan network services, web applications, and APIs to identify weaknesses that could be exploited by attackers. They provide a comprehensive overview of potential vulnerabilities that need to be addressed.
Proxy Tools
Proxy tools inspect and test the security of web filters, firewalls, secure web gateways, and other software security products. They act as intermediaries that intercept and analyze traffic between the client and server, helping testers to identify and exploit weaknesses in web security mechanisms.
Exploitation Tools
Exploitation tools assist testers in crafting, delivering, and injecting malicious payloads to gain control over targeted assets. These tools are used to simulate real-world attacks and exploit identified vulnerabilities, allowing testers to evaluate the effectiveness of the organization’s defenses.
Post-Exploitation Tools
Once access is gained, post-exploitation tools are used to maintain control over the compromised system and escalate privileges. These tools help testers stay in control of the machine until they achieve their objectives, providing insights into the potential impact of a successful attack and the effectiveness of the organization’s incident response.
How does Pen Testing Differ from Automated Testing?
While pen testing primarily involves manual effort, pen testers also utilize automated scanning and testing tools. However, they extend beyond these tools by applying their expertise in the latest attack techniques to conduct more thorough testing than what is achieved through a standard vulnerability assessment.
Manual Pen Testing
Manual pen testing goes beyond automated assessments by using the expertise and creativity of skilled testers. These professionals uncover vulnerabilities and weaknesses not included in popular lists like the OWASP Top 10 and test aspects of business logic that automated tools often overlook, such as data validation and integrity checks. Manual testing is adept at identifying false positives flagged by automated tools.
Automated Testing
Automated testing, in contrast, excels in speed and efficiency, delivering results faster and requiring fewer specialized professionals compared to manual pen testing. These tools can scan systems, track results, and export findings to centralized reporting platforms, providing a streamlined process. Automated testing ensures consistency, as running the same tests repeatedly on a system will yield the same results, unlike the variable outcomes of manual tests.
While automated tools offer a broad and rapid assessment, they lack the depth and adaptability of manual pen testing, making them a complementary, rather than a standalone, solution for comprehensive security evaluation.
Final Words
Penetration testing is essential to any strong cybersecurity strategy, but continuous efforts like bug bounty programs and regular vulnerability scanning should complement it. These programs help identify and address vulnerabilities in real time, providing ongoing protection. By combining penetration testing with these security measures, organizations can significantly enhance their security posture, ensuring strong defenses against cyber threats.







