As the landscape of cybersecurity attacks becomes more sophisticated and complex, organizations face significant challenges in identifying and countering these threats effectively. To address this, the MITRE ATT&CK® Framework has emerged as a valuable resource for security practitioners. In this blog, we will explore the benefits of using ATT&CK as a baseline to comprehensively understand threats and how Falco can detect and respond to these threats.
The ATT&CK Framework serves as an extensive repository of documented tactics, techniques, and procedures (TTPs) commonly employed by cyber adversaries. By gaining a comprehensive understanding of these TTPs, organizations can enhance their defensive capabilities and fortify their cybersecurity posture.
Falco is an open-source tool that provides runtime security for containers, virtual machines, and standalone Linux hosts. It allows organizations to monitor, detect, identify, and respond to suspicious activity. Falco operates on static rules provided in the rules file, which enables it to detect suspicious activities and alert security teams in real-time.
Whether you are a security analyst, a DevOps engineer, or an avid container enthusiast, this blog offers invaluable insights into utilizing MITRE ATT&CK-focused Falco rules to bolster your environment against advanced adversarial attacks.
Step 1: Gather Necessary Details
Understanding the Attacker’s Perspective:
To create rules that identify specific ATT&CK techniques, you must think like an attacker and consider how they might try to harm or take advantage of a victim’s environment. Conducting an in-depth assessment of MITRE’s ATT&CK TTPs will provide you with enough information to understand an attacker’s perspective.
Identify Relevant System Events and Calls:
Falco relies on system events (syscalls) generated within the user’s environment to detect malicious activities using static rules. It is essential to carefully consider the relevant system calls that occur during an attack and capture events related to network activity and file/directory changes.
Step 2: Write the Falco Rule
Rule Writing Process:
Writing a Falco rule is an iterative process that starts with crafting a basic rule and gradually refining its conditions to be more specific. Incorporating exceptions into the rule helps prevent false positives and ensures that only genuinely malicious activities trigger alerts.
Example Rule for Inhibit System Service Technique:
Let’s focus on the specific MITRE ATT&CK technique of “Inhibit System Service” and develop a Falco rule to effectively identify it. This technique involves attackers targeting recovery services to make the system inaccessible. They might employ commands like “rm” and “systemctl” to delete important system files or overwrite the hard drive with random data, hindering system recovery.
Create an Enabled Field:
We can enable or disable the rule as per our requirements. If this field is not set, the rule is automatically enabled by default.
Write an Output Field:
This is the text that Falco sends when alerting on a suspicious activity. The output should be descriptive, including relevant information like process names, usernames, container names, or IDs.
Specify a Priority:
Rules can have different priorities indicating their urgency. For this critical rule, we assign the highest priority level, known as CRITICAL.
Add Appropriate Tagging:
Tags serve as metadata providing additional information about the rules. We can include tags like mitre_impact, inhibit_system_recovery, and T1490 for this rule.
Consolidated Rule:
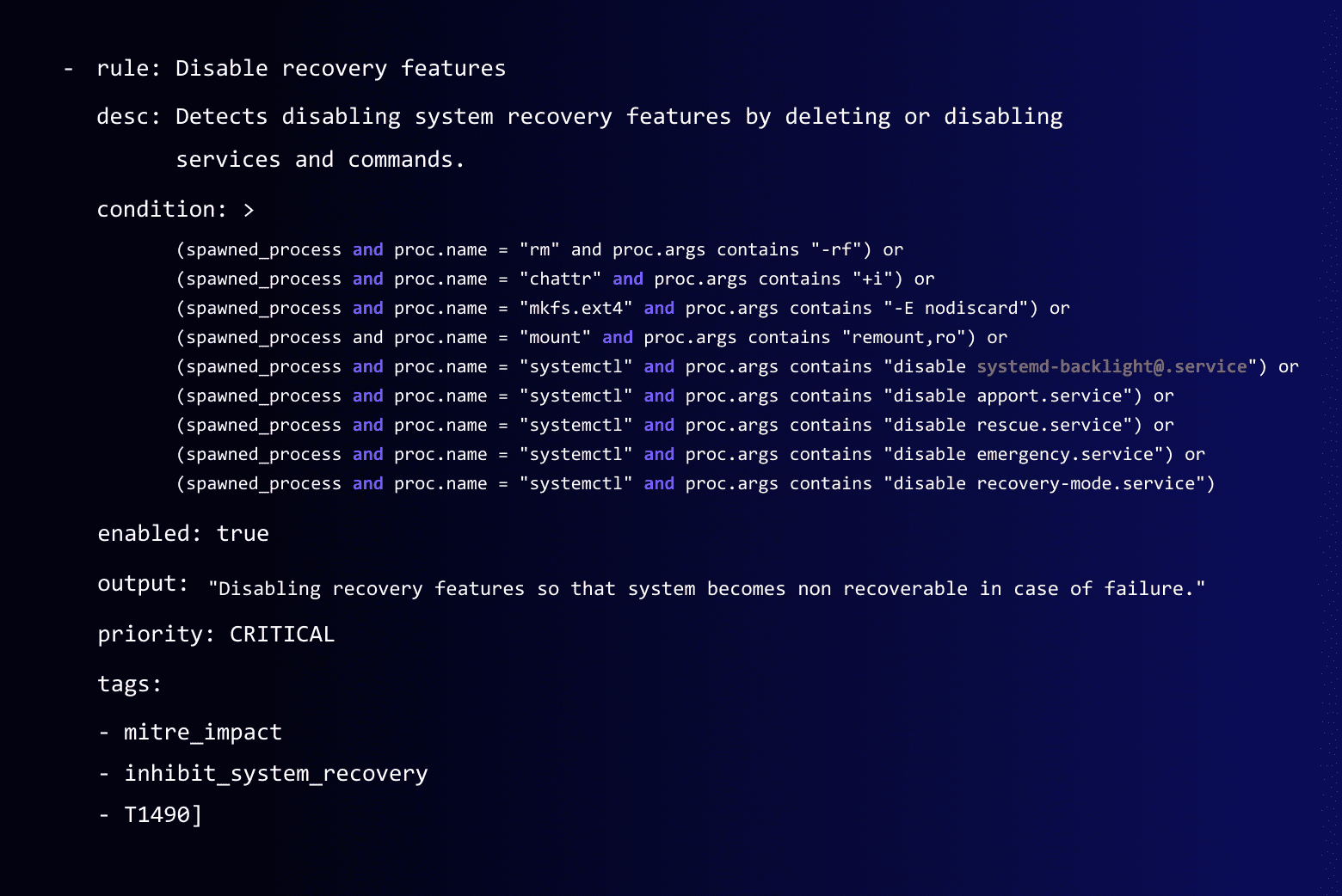
(rule: Disable recovery features
desc: Detects disabling system recovery features by deleting or disabling services and commands
condition: > (spawned_process and proc.name = “rm” and proc.args contains “-rf”) or (spawned_process and proc.name = “chattr” and proc.args contains “+i”) or (spawned_process and proc.name = “mkfs.ext4” and proc.args contains “-E nodiscard”) or (spawned_process and proc.name = “mount” and proc.args contains “remount,ro”) or (spawned_process and proc.name = “systemctl” and proc.args contains “disable systemd-backlight@.service”) or (spawned_process and proc.name = “systemctl” and proc.args contains “disable apport.service”) or (spawned_process and proc.name = “systemctl” and proc.args contains “disable rescue.service”) or (spawned_process and proc.name = “systemctl” and proc.args contains “disable emergency.service”) or (spawned_process and proc.name = “systemctl” and proc.args contains “disable recovery-mode.service”)
and user.name != “root”
enabled: true
output: “Disabling recovery features so that the system becomes non-recoverable in case of failure.”
priority: CRITICAL
tags: [mitre_impact, inhibit_system_recovery, T1490])
Conclusion
By leveraging the synergies between the MITRE ATT&CK Framework and Falco’s capabilities, we can greatly enhance our ability to detect and respond to potential threats. Writing targeted Falco rules, based on specific ATT&CK techniques, allows us to actively detect and respond to emerging security threats and ensure a robust shield against attackers.
However, this is an ongoing process, and continuous refinement of Falco rules is crucial to minimize false alarms and improve accuracy in threat detection. Armed with the knowledge gained from this blog, security professionals and DevOps teams can strengthen their defenses and proactively protect their environments.
Relevant Article:
1. Enhancing Linux Security: Improving Potential of Falco Threat Detection Using Extended Rules







