As developers increasingly turn to third-party libraries to enhance productivity, ensuring code security is more vital than ever. However, while these integrations can speed up development, they can also pose security threats if overlooked.
To help you choose the best SCA tool, we’ve researched and compiled the 10 best software composition analysis (SCA) tools for 2025. Let’s get started!
What is SCA?
Software Composition Analysis (SCA) is all about understanding and assessing the components that make up your software, especially those third-party libraries and open-source code snippets that can speed up development. By profoundly analyzing these elements, SCA helps developers spot known vulnerabilities, check for licensing issues, and manage security risks, particularly in the context of supply chain attacks.
This way, developers can catch and fix security risks early on, ensuring that their applications are safe and compliant. In short, SCA tools help you build reliable software while keeping potential threats at bay.
Want to know more about SCA? We’ve curated a comprehensive guide on “Software Composition Analysis” to simplify your understanding. Don’t miss out! |
What to Look For in a SCA Solution?
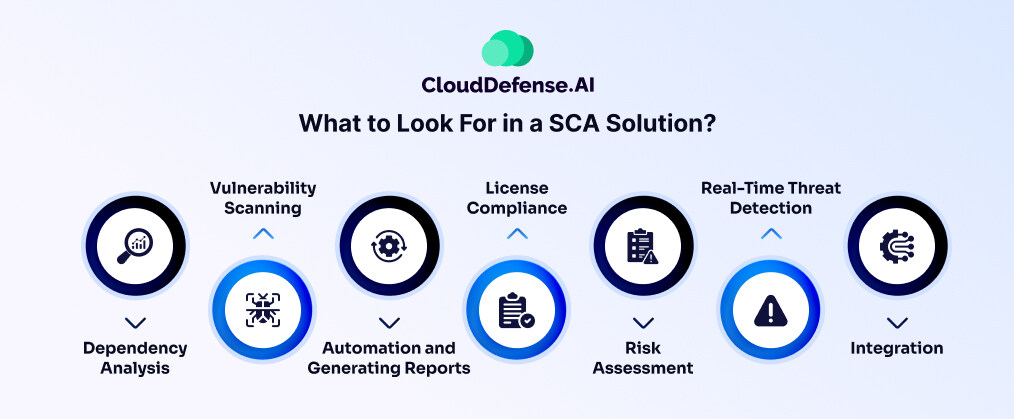
When looking for the best SCA solution, you can’t randomly choose a particular tool. You have to be diligent and evaluate various factors that will blend with the software security requirements of your organization. Here are some key factors that you should look into a SCA solution:
Dependency Analysis
The first thing you should check in the SCA tool is the dependency analysis capability. It should be capable of automatically analyzing the codebase to identify all the open-source components, third-party libraries, and other code assets associated with it.
Vulnerability Scanning
The SCA tool should offer vulnerability scanning to identify potential vulnerabilities and security risks present in the software's codebase. It should analyze the vulnerabilities by checking them against known vulnerability databases like the National Vulnerability Database and provide reports about severity.
Comprehensive Library Coverage
The best SCA vendor should offer extensive coverage, identifying vulnerabilities, licensing issues, and quality concerns across a wide array of open-source libraries and components.
Reporting and Analytics
Choose a tool that offers clear, detailed reporting and analytics. This feature makes it easier to track your progress, monitor trends, and identify areas needing improvement.
License Compliance
When analyzing the best SCA tool, you should make sure that it is capable of analyzing the license embedded with each open-source component. By analyzing the licenses, it enables the organization to adhere to legal obligations and compliance requirements.
Risk Assessment
Offering risk assessment of all the detected vulnerabilities and licensing issues allows the security team to prioritize the issues and remediate them accordingly. If it doesn't remediate automatically, it should at least offer guidance for corrective measures.
Real-Time Monitoring
In more dynamic companies, real-time monitoring capabilities are essential. The tool should detect potential vulnerabilities or issues as soon as they arise, preventing them from escalating into major problems.
Automation
Automation is essential for the best SCA tool. It should streamline the scanning and analysis processes, reducing manual effort and saving valuable time while minimizing the risk of human error in vulnerability detection.
Integration
Lastly, ensure that the SCA tool integrates smoothly with your existing development tools and processes. This integration allows developers to identify vulnerabilities and compliance issues early in the development cycle, making it compatible with CI/CD pipelines, issue-tracking systems, IDEs, and other tools used in your workflow.
10 Best Software Composition Analysis Tools in 2025
Before we dive into the list of best SCA vendors in 2025, we would like you to go through the SCA solution comparison:
SCA Tools | Vulnerability Scanning | CI/CD and IDE Integration | Risk Prioritization | Price |
Available | Available | Available | Pricing starts from $50 per month for every user. Book a Free demo today! | |
CAST Highlight | Available | Available | Available | Pricing starts at $26K for 25 applications. |
Veracode | Available | Available | Available | Pricing starts from $50 per month for every user. |
Checkmarx SCA | Available | Available | Limited. | The pricing is available on quote request. |
Synopsys Coverity | Available | Available | Limited | The pricing starts at $500 per month. |
JFrog Xray | Available | Available | Available | The pricing is available on quote request. |
Mend.io | Available | Available | Available | The pricing starts at $25K per year for 100 developers. |
Snyk Open Source | Available | Available | Limited | The pricing starts from $25 per month. |
SonarCloud | Available | Available | Available | The price starts at $11 monthly for 100K lines of code. |
HCL AppScan | Available | Available | Limited | The price starts at $60 per month for every user. |
Now it is time we dive into the list of best SCA tools in 2025 that require your attention:
CloudDefense.AI

CloudDefense.AI 
Undoubtedly, CloudDefense.AI serves as the obvious choice when you are looking for a comprehensive SCA tool that lets you take control of security and license compliance. It is a highly effective tool that blends deep code analysis and real-time context to assess the vulnerabilities.
The holistic scanning capabilities and ability to provide deep insights into third-party components leave no stone unturned when it comes to identifying issues. It serves as a comprehensive tool to enhance the overall application security and compliance.
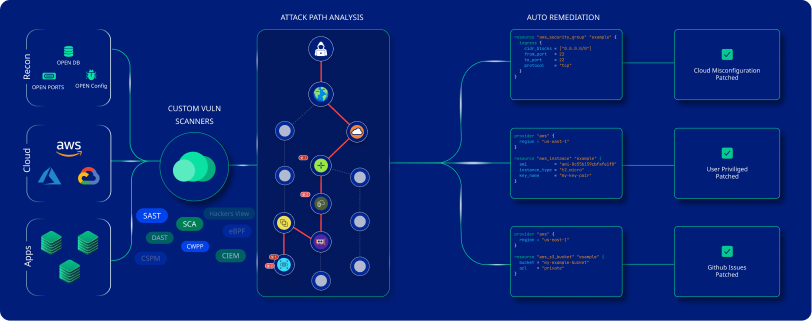
Features
Here are some of the key features of CloudDefense.AI that make it a brilliant choice:
Open Source Vulnerability Detection
Easily spot vulnerabilities and license risks in open-source libraries. With our clear, actionable remediation guidance, you can tackle these issues head-on without the guesswork.
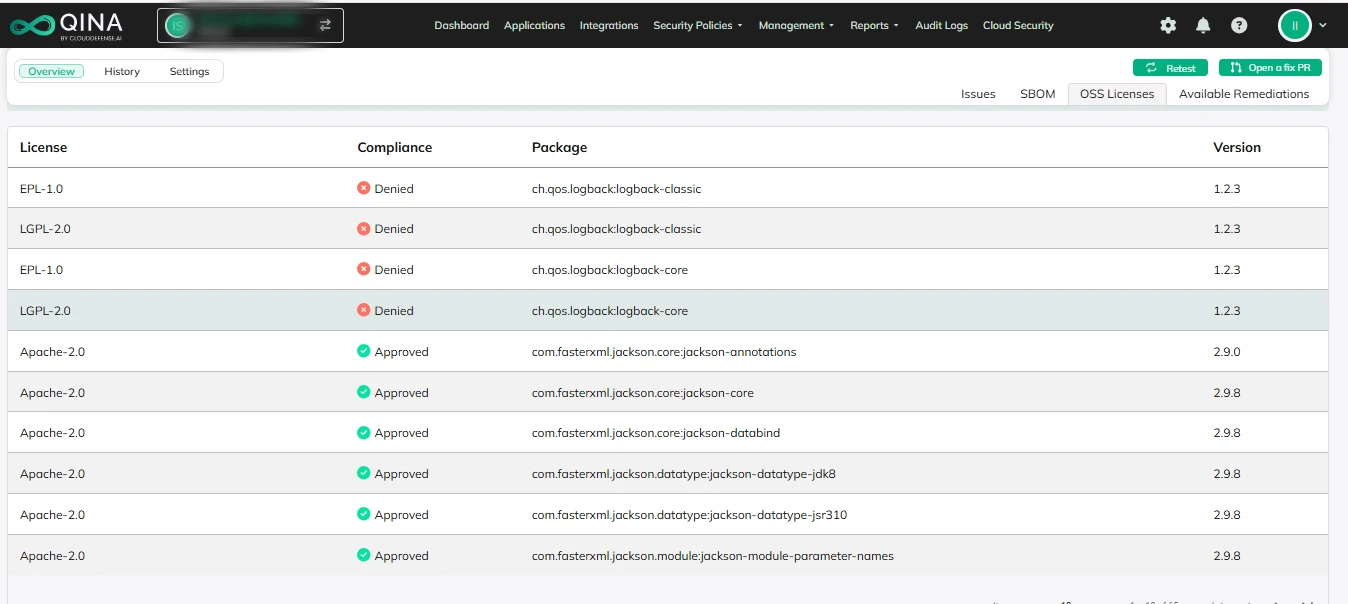
Prioritize Top Open Source Risks
Use broad application context to zero in on open-source issues that are reachable, deployed, or publicly exposed, which pose the highest risks to your organization. This approach helps you tackle the threats that could have the biggest impact.
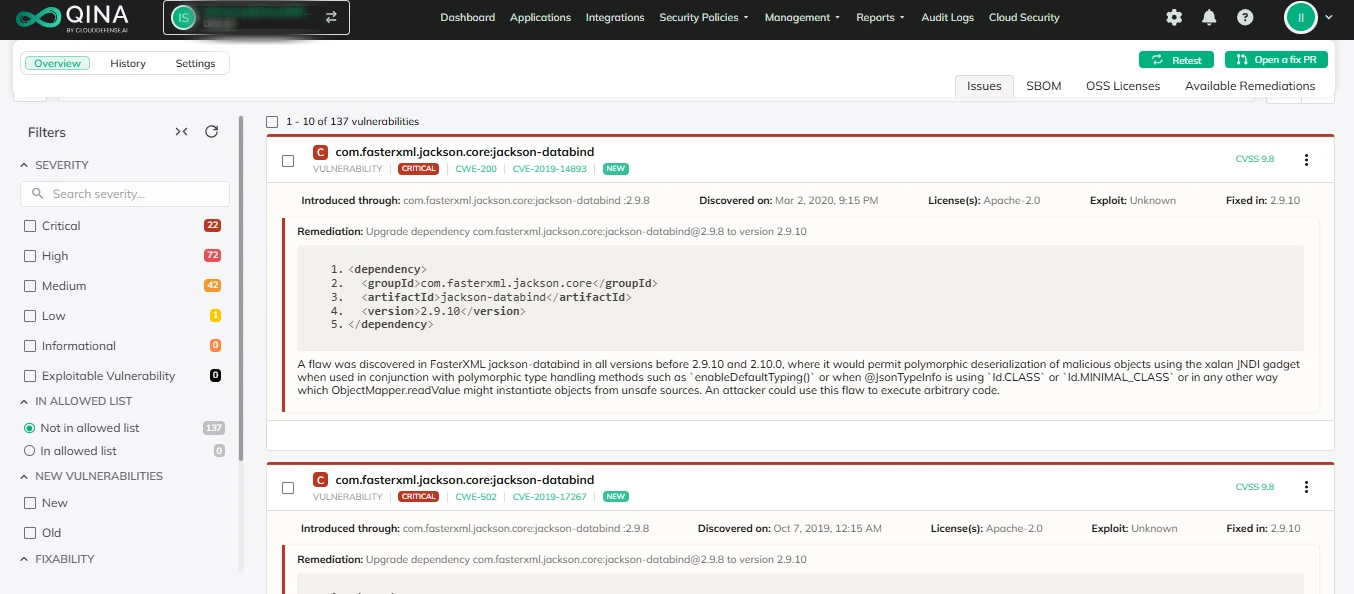
Auto Remediation
We provide auto-fixes and clear steps to help you address vulnerabilities quickly and efficiently, making it easier to keep your projects secure. With this proactive approach, you can confidently stay ahead of potential security issues.
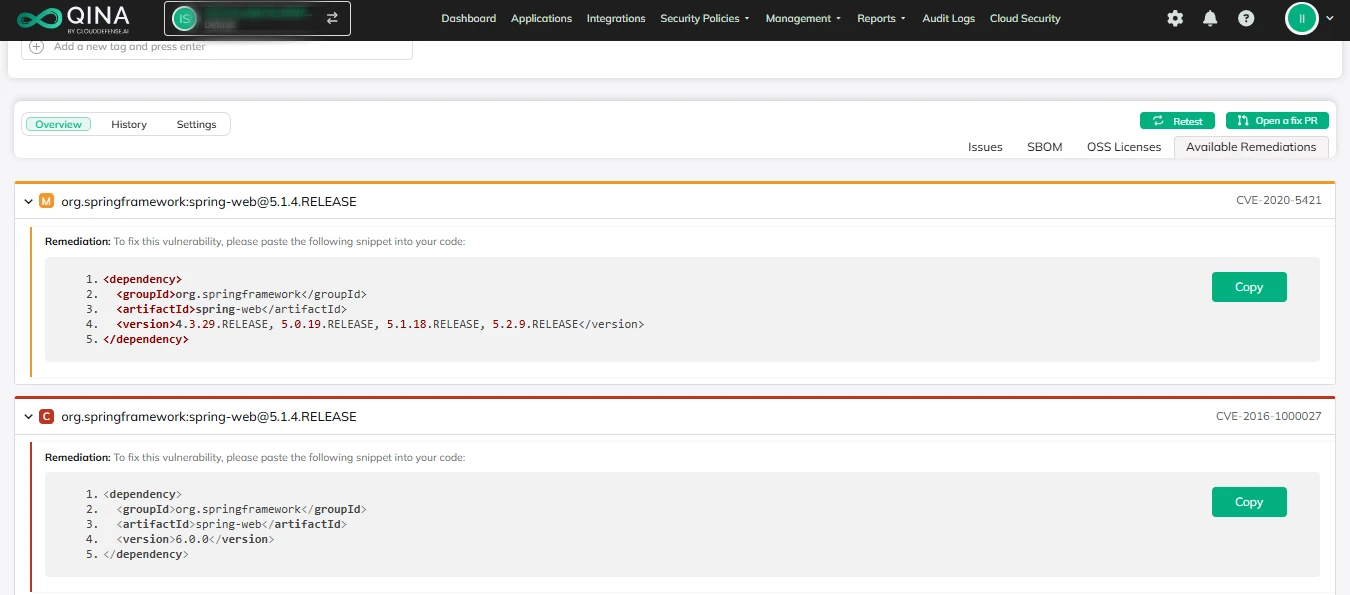
Advanced Reporting and Analytics
Get detailed insights into your security stance with handy reporting and analytics features. This helps you keep tabs on vulnerabilities, track how well you’re fixing them, and make smart choices for your security game plan.
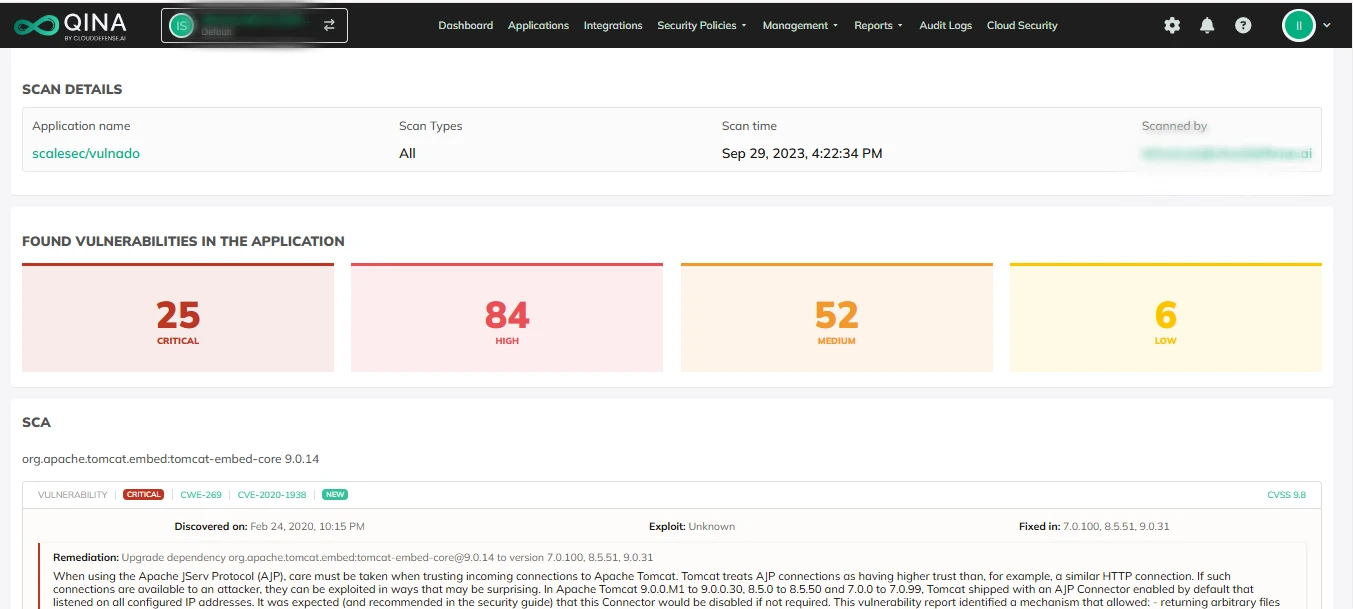
Developer-Friendly Workflow
CloudDefense.AI fits seamlessly into your existing development CI/CD tools and practices, making security a natural part of your workflow. This integration means your team can focus on building great software without skipping a beat on security.
Reduced Noise
CloudDefense.AI's built-in false positive management helps you focus on what really matters by eliminating unnecessary alerts. By filtering out the noise, you can trust that you're working with accurate, relevant data every time.
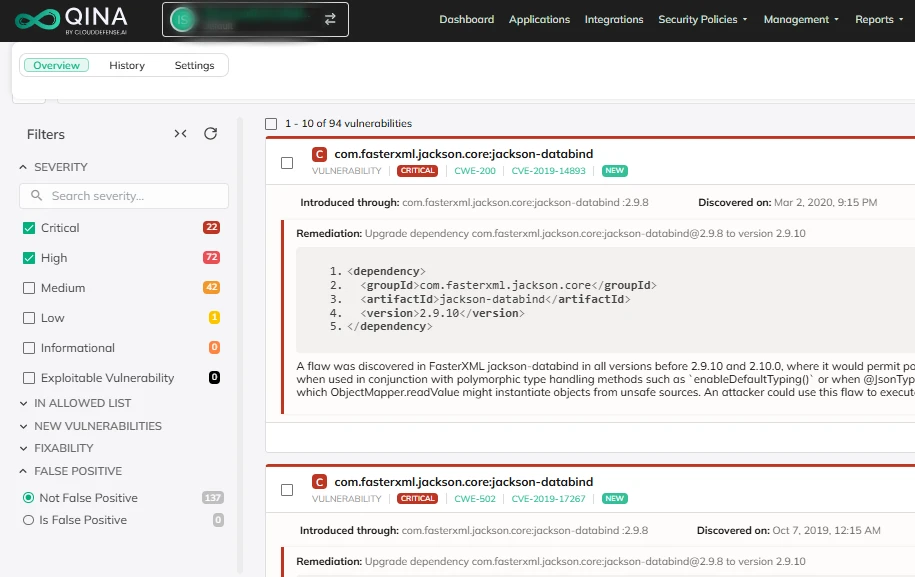
Pros

It offers complete end-to-end security to secure your code and the application.

Provides clear steps to address security issues effectively.

Focuses on the most critical vulnerabilities that could impact your applications.

This solution streamlines the remediation process and ensures quick fixes by providing you with actionable insights.

Ensures ongoing security by automatically checking for vulnerabilities in deployed code.

Prioritizes vulnerabilities into high, severe, and low categories to address the most pressing threats.

Works effortlessly with your existing development tools and workflows.
Cons

The UI can initially feel complicated, but it becomes easier to navigate with regular use.
Don’t just take our word for it. Book a free demo and witness firsthand the power and simplicity of CloudDefense.AI.
CAST Highlight

CAST Highlight
You can consider CAST Highlight as a comprehensive SCA tool that offers security from code to development and deployment in your application.
This automated application governance solution provides a deep analysis of vulnerability, and it works well with organizations of any size. It is one of those solutions that focuses on a green software development approach without disturbing productivity.
Features
It provides developers and security teams with automatic recommendations on prioritized vulnerabilities and helps them focus on the most critical issues.
Offers developers a single and integrated view of their applications and components associated with them.
Through centralized control towers, it performs rapid analysis to identify and address security vulnerabilities and IP licensing exposures.
Promotes a green software development approach by identifying areas where CO2 emission can be reduced.
Veracode

Veracode
Among top-tier SCA vendors, Veracode has established itself as one of the leading tools that goes beyond traditional code scanning and NVD. It has been designed in such a way that not only fixes code issues but also automates the finding of vulnerabilities. With this tool, maintaining software security gets easier as you get a bunch of advanced tools.
Features
Scans for vulnerabilities through the command line in the pipeline and IDE, enabling developers to fix errors at the early stage.
Automates scanning and remediating of open-source vulnerabilities and license risks and prevents the organization from hefty penalties.
Offers a premium database of vulnerabilities that helps identify many emerging threats that are yet to be discovered.
Enables developers to create SBOM for the open-source components and it is saved in CycloneDX format.
Read More: Curious about securing your applications? Learn the key differences between SCA, SAST, and DAST in our blog post! |
Checkmarx SCA

Checkmarx SCA
Checkmarx SCA is undoubtedly one of the finest SCA tools you will come across that scans your applications and keeps all the open-source vulnerabilities in check.
Besides, this SCA tool also helps developers maintain license compliances and recommended updates. It is a leading vendor that is trusted by 1400 organizations throughout the world, including many top Fortune 100 organizations.
Features
Efficiently finds vulnerable open-source packages in your application code and provides remediation guidance to solve them.
Enables developers to prevent all types of compliance risks by helping to apply accurate licenses to open source code and make sure all the attributions are correct.
Employs an open-source security research team that helps organizations with remediation guidance and details regarding known CVEs and specialized vulnerabilities.
It integrates seamlessly with CI/CD pipelines and SDLC and alerts users regarding new threats, including threats affecting previous applications.
Synopsys Coverity

Synopsys Coverity
When it comes to getting one of the best SCA tools, you have to consider Synopsys Coverity. It provides the organization with a detailed static analysis and enables the developers to deliver high-quality software that maintains security, industry regulations, and functional safety.
Features
Synopsys Coverity goes through numerous libraries and files across your codebase and identifies code quality and security issues to fix them.
It can scale and analyze applications of any size, even large web apps with millions of lines of code.
Makes it easy for the security team to track and manage compliance by providing security teams with insights into issues and prioritize remediation.
Supports more than 22 programming languages, 200 frameworks, and various IaC platforms to enhance overall code quality.
JFrog Xray

JFrog Xray
JFrog Xray is a one-of-a-kind universal SCA tool that efficiently analyzes the source and binary files to identify vulnerabilities and resolve them. It is an all-around SCA tool that urges developers and DevSecOps teams to emphasize introducing security assessments as early as possible in the development stage.
Features
Deploys automated and continuous scanning and auditing of software artifacts and other components through the development stage to prevent security issues.
It works well with self-hosted platforms, AWS, GCP, Azure, and other popular cloud platforms.
Offers an extensive JFrog vulnerability database that sources data from NVD, GitHub, Red Hat, and other databases to provide rich insights into vulnerabilities.
Allows DevSecOps teams to analyze and understand all the dependencies of the components associated with the application.
Mend.io

Mend.io
Trusted by top organizations in the world, Mend.io is truly an exceptional SCA that helps you discover and fix vulnerable open-source dependencies and other vulnerabilities.
It is well-suited for organizations working with GitHub and integrates easily with such an environment. A highlight aspect that makes Mend.io a great choice is that it reduces the burdens on developers by integrating security into registries, repositories, and IDEs.
Features
The 360-degree Malicious package protection efficiently detects and mitigates malicious packages in your codebase.
Offers a comprehensive vulnerability database and efficient tracking system to identify new critical vulnerabilities and prevent them from affecting the application.
Curbs MTTR by 80% by leveraging automated remediation processes and ensuring security throughout the development.
It offers path analysis that enables developers to detect and analyze vulnerabilities that have the highest impact potential.
Snyk Open Source

Snyk Open Source
If you are looking for a developer-focused SCA tool that will help you find, prioritize, and remediate vulnerabilities, then Snyk Open Source serves as a possible choice. Unlike others, it offers an advanced software composition analysis that combines application and security intelligence to find vulnerabilities throughout the development cycle.
Features
Enables developers to discover vulnerabilities while coding in the IDE or CLI, ultimately saving them from hefty fixes in the future.
Deploys automated Snyk tests at the CI/CD pipeline and prevents any new vulnerabilities from reaching the deployment stage.
Snyk Open Source assesses the product environment to ensure it is free from the impact of existing vulnerabilities and looks for new issues.
It automates the monitoring of your application and codebase to identify vulnerabilities and also provides reports of the latest NVEs.
SonarCloud

SonarCloud
SonarCloud is an emerging SCA tool that garners a lot of attention with superior analysis capability and precision reports to reduce false positives. It is a cloud-based solution that offers developers complete scalability and flexibility to work on their application development.
Features
SonarCloud protects your application across different frameworks, IaC platforms, and numerous programming languages.
It offers automated analysis and code checks to identify vulnerabilities and provides quick feedback regarding the issue.
Features Sonar Quality Gate, whose main function is to prevent codes that don't meet the required quality requirement.
Maximizes the remediation process through precision analysis and helps you focus on issues with high severity.
HCL AppScan

HCL AppScan
Another top software composition tool that you can take into consideration is HCL AppScan. It is a dynamic SCA tool that offers you a suite of technologies to identify vulnerabilities in your application. Automating the testing throughout the SDLC ensures continuous security and prevents any malicious component from entering production.
Features
It enables the DevOps team to deploy automated testing through the development lifecycle and accelerate the remediation process.
Maintain a shift left paradigm by integrating into CI/CD pipelines and IDEs and discover vulnerabilities from the start of the development.
Offers auto-fix capability by leveraging machine learning and auto-issue correlation to prioritize vulnerabilities according to their impact level.
It provides a centralized dashboard for real-time visibility into your risk posture and compliance.
Conclusion
Choosing the best SCA tool from the list of 10 best software composition analysis tools in 2025 might seem difficult at first. However, we are confident that this guide will ease up the process of finding the appropriate SCA tool that will cater to your organization’s requirements and prevent vulnerabilities from affecting the development stage.
Don’t leave your software security to chance. Try CloudDefense.AI for comprehensive SCA solutions that proactively identify risks, ensure compliance, and keep your code secure. Book a demo today and see the difference for yourself!







