Code vulnerabilities often go unnoticed, leaving software exposed to threats. Yet many developers overlook a potent tool in their security suite: Static Application Security Testing (SAST).
But here’s the thing – implementing SAST the right way takes more than just running a scan. You need a solid plan and approach. In this article, we’ll explore the best practices for implementing SAST into your workflow to keep your code base secure.
What is SAST?
SAST stands for Static Application Security Testing. It’s a way to check your code for security issues before you even run it. SAST tools dig into your code’s structure and detect issues like buffer overflows, SQL injection risks, and other vulnerabilities. The goal is to catch these problems early, preventing potential security threats from becoming real-world incidents.
Head on to our blog on What is SAST to learn more.
Now, where does this fit in the SDLC?
Well, it’s not just a one-and-done deal. SAST is most effective when it’s woven throughout the development process. You start early, ideally when you’re still writing code. This way, you catch vulnerabilities before they turn into bigger issues.
But it doesn’t stop there. You keep running SAST checks at different stages – during code reviews, before merging into the main branch, and definitely before pushing to production. The ultimate goal is to catch and fix security bugs early, saving time, money, and issues down the road.
Understood. Here’s a revised version with formal subheadings and a more human-like explanation style:
Benefits of Static Application Security Testing (SAST)
Early Vulnerability Detection
SAST finds security issues in the code before the application is even run. This means we can fix problems much earlier in the development process. It’s a lot easier and cheaper to fix issues when we’re still writing the code, rather than after we’ve built the whole application.
Efficient Handling of Large Codebases
As our projects get bigger, it becomes really hard for developers to manually check every line of code for security issues. SAST tools can handle massive amounts of code quickly and consistently. They don’t get tired or miss things because they’re in a hurry.
Regulatory Compliance Support
Many industries have tight regulations around software security, and SAST makes it easier to stay compliant. It provides detailed logs of all our security scans, so when audits come up, we’ve got solid proof that we’re taking security seriously and doing things right.
Reduced Remediation Costs
Fixing security problems after the software is released is expensive. It can cost much more than fixing the same issue during development. By catching problems early, SAST saves a lot of money in the long run.
Multi-Language Support
Most SAST tools work with many different programming languages. This is great for teams that use multiple languages in their projects. We can apply consistent security checks across all our code, regardless of the language in which it’s written.
Integration with Development Workflows
Modern SAST tools are designed to fit into existing development processes. They can be set up to run automatically whenever code is changed. This means security checks happen continuously without slowing down development.
Security Posture Tracking
SAST gives us data about our security status over time. We can see if we’re improving, where we commonly make mistakes, and what areas need more focus. This helps us get better at secure coding practices across the whole team.
8 Best Practices for Implementing SAST
Start Security Checks Early
Start using SAST tools as soon as you begin coding. Don’t wait until the end. Run scans during requirements gathering, design, coding, and testing phases. This helps catch issues early when they’re easier and cheaper to fix. For example, if you’re working on a new feature, run a scan on that specific code before merging it into the main branch. This prevents vulnerabilities from piling up.
Establish Risk-Based Prioritization Protocols
When SAST tools generate findings, don’t treat all issues equally. Set up a system to rank vulnerabilities based on their potential impact and likelihood of exploitation. Consider your organization’s specific risks and priorities. For instance, if you’re handling sensitive customer data, prioritize fixes for any potential data leakage issues. This approach ensures you’re tackling the most critical problems first.
Customize SAST Rules and Configurations
Out-of-the-box SAST tools often flag many false positives. Take time to tune your tool’s settings. Adjust rules based on your codebase, frameworks, and libraries. This might involve excluding certain files or directories or modifying sensitivity levels for specific checks. It’s a bit of work upfront, but it pays off by reducing noise and helping your team focus on real issues.
Integrate Automated SAST Scans in CI/CD Pipeline
Set up your SAST tools to run automatically with each code commit or pull request. This makes security checks a routine part of development. For example, configure your CI/CD pipeline to trigger a SAST scan whenever code is pushed to the repository. If issues are found, have the system notify developers or even block the merge until critical problems are resolved.
Develop KPIs Focused on Vulnerability Remediation
Instead of just counting the number of open bugs, track how many issues are actually being fixed. This gives a better picture of your security improvement. Set up dashboards that show trends in vulnerability remediation over time. Are high-severity issues being addressed quickly? Is the overall number of vulnerabilities decreasing? These metrics help demonstrate the value of your SAST efforts to management.
Implement Regular SAST Tool Evaluations
The field of application security is always evolving. New types of vulnerabilities emerge, and SAST tools improve to detect them. Schedule regular assessments of your SAST tools. Are they still meeting your needs? Are there new features or alternatives that could enhance your security posture? This might involve running pilot tests with different tools or attending security conferences to stay informed about the latest developments.
Conduct Regular SAST Tool Training for Developers
Your SAST tool is only as good as the people using it. Make sure your dev team knows how to use it properly. Run regular training sessions. Show them how to interpret results, how to avoid common pitfalls, and how to write code that’ll sail through scans. The more they understand the tool, the more effective your whole security process becomes.
Establish a Feedback Loop for Continuous Improvement
SAST isn’t a set-it-and-forget-it deal. Use the data from your scans to keep getting better. Look for patterns in the issues that come up. Maybe there’s a certain type of vulnerability that keeps popping up – that’s a sign you need more training in that area. Or maybe certain parts of your code are always clean – what are those developers doing right? Learn from your successes and failures to keep improving your security game.
Why Choose CloudDefense.AI for SAST?
Comprehensive Scanning
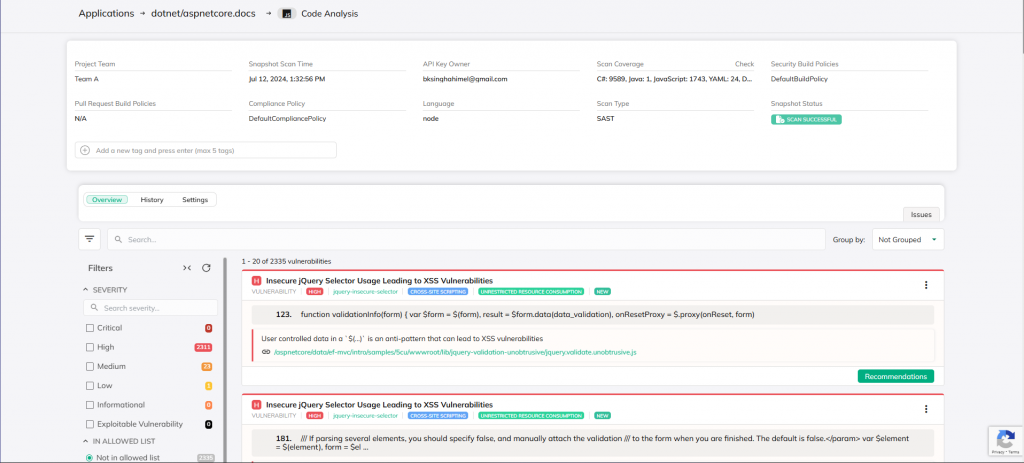
CloudDefense.AI’s SAST solution isn’t a basic scan-and-go tool—it’s engineered to analyze your application’s entire codebase with precision. Security isn’t just about finding vulnerabilities; it’s about finding them at the right time. Our SAST tool integrates seamlessly into every stage of the software development lifecycle, from the earliest design phases to pre-deployment readiness. This approach ensures that security issues are identified and resolved before they can become costly problems in production.
Automated Code Remediation
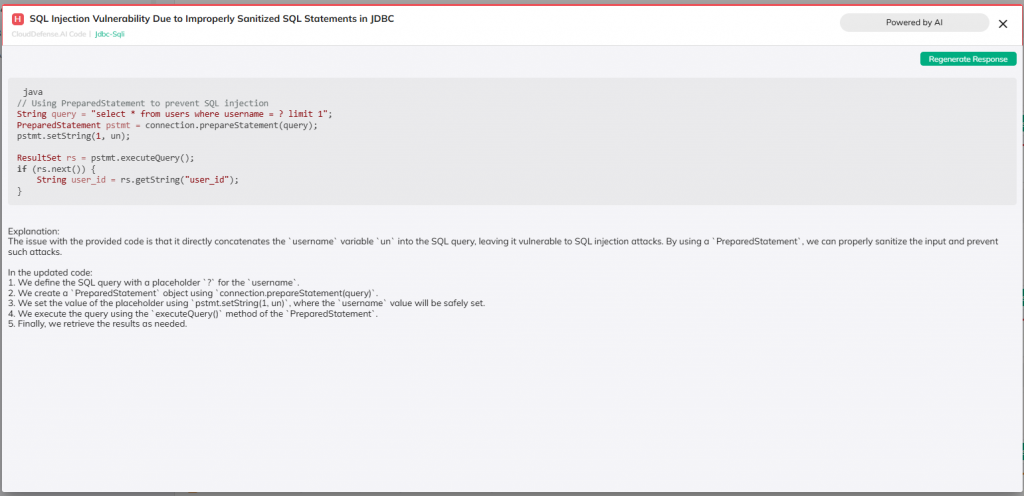
We understand that manual fixes are inefficient and prone to delays, especially in fast-moving development cycles. That’s why our SAST solution focuses heavily on automation. When a vulnerability is detected, the system provides a detailed breakdown of the issue and delivers clear remediation steps. No vague reports or guesswork—just actionable insights that developers can immediately use to address the problem. This reduces downtime and accelerates the development pipeline without compromising security.
Broad Language Support
Modern development teams work across a variety of languages and platforms, so flexibility is critical. Our SAST tool supports an extensive range of languages, including C, C++, Docker, .NET, Go, Java, JavaGradle, JavaMaven, Kotlin, Kubernetes, JavaScript, Objective-C, PHP, Python, Ruby, Rust, Secrets, Terraform. We also cover essential frameworks like Kubernetes, Terraform, and JavaMaven. No matter your stack, we’ve got you covered.
Compliance with Industry Security Standards
Compliance is a non-negotiable part of modern software development, and we make it easy for you to meet the highest security benchmarks. Our SAST solution is built to ensure alignment with OWASP Top 10, and CWE Top 25 (2019–2021). By integrating these standards into your development workflow, you don’t just check a compliance box—you elevate the overall security posture of your application.
Actionable Insights
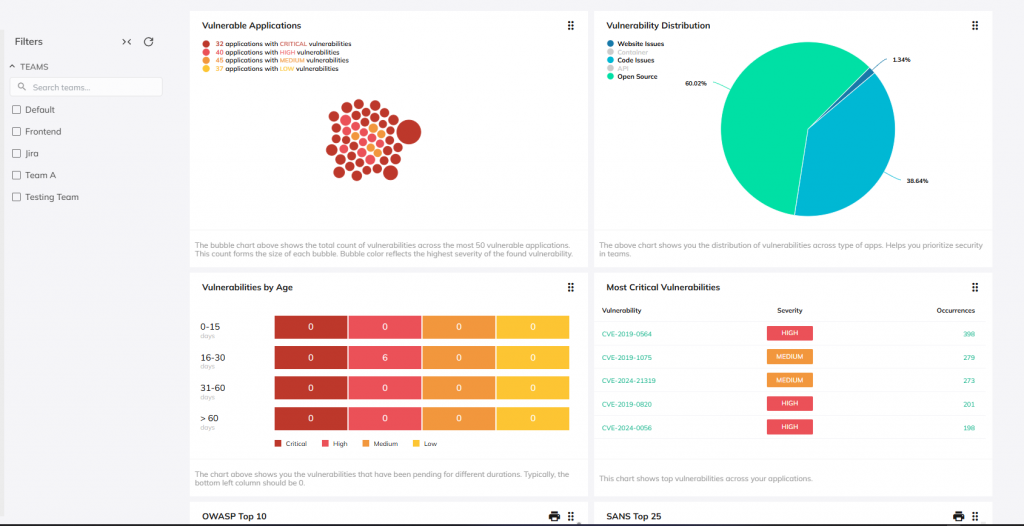
Detailed reporting is a core feature of our SAST tool. When vulnerabilities are flagged, you’re not left wondering what to do next. We provide clear, structured insights that explain the issue, its potential impact, and the steps required to fix it. Beyond fixing immediate problems, our reporting includes metrics to help you measure your progress and continuously improve code quality over time.
We use a variety of security tools to check every part of your application. We don’t just look at one layer—we examine the whole thing, giving you a more complete picture of its security.
If you’re interested in seeing how Clouddefense.AI can improve your application security, we invite you to schedule a demo. Our team would be happy to show you our SAST tool in action and discuss how we can address your specific security needs.







