Containers have transformed modern software development, changing how applications are created, deployed, and managed. But with this evolution, container security has become equally essential, ensuring application safety throughout the container lifecycle.
The best container security tools offer solutions that simplify securing containerized environments, from scanning images and setting access controls to vulnerability management and compliance.
While managing container security across numerous components might seem complex, top container security tools make it achievable by automating critical security tasks.
To help you find the right fit, we’ve compiled a list of 2025’s 10 top container security vendors to secure every aspect of your CI/CD pipeline and containerized infrastructure.
- CloudDefense.AI
- Prisma Cloud
- Snyk
- PingSafe
- Aqua Security
- Qualys
- Sysdig
- Orca Security
- Anchore
- Alert Logic
Before we dive into the tool comparison, let’s explore what to look for in a solution.
What to Look For in a Container Security Tool?
When you are looking for a container security tool, you can’t randomly select any tool. There are certain factors you will have to consider because they cumulatively assist in maintaining the security posture of the application and the containerized environment. Here are some key factors that you should look at in the container security tool:
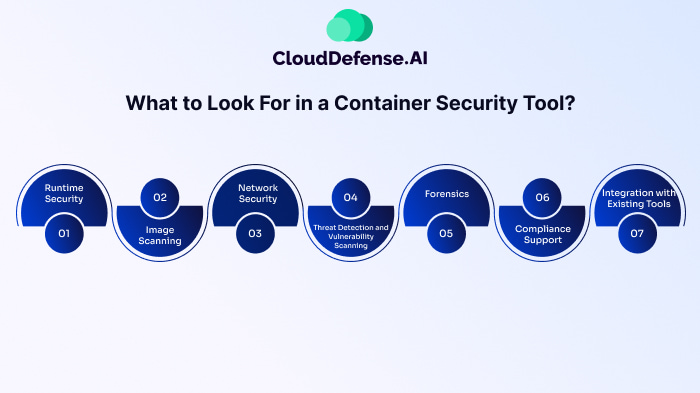
Runtime Security
Runtime security is an important aspect to consider when looking for a container security tool. It helps in real-time monitoring of the containers where it discovers and addresses risks and vulnerabilities that might reach the deployment stage. Runtime security features help protect the containerized application from attacks and breaches that may happen after deployment.
Image Scanning
Along with runtime security, image scanning serves as one of the primary requirements of a container security tool. It continuously scans all the container images and finds vulnerabilities and flaws that might jeopardize the whole application's security. It mainly aims that only secured and safe container images should be present in the product stage.
Network Security
The container security tool you will choose must offer comprehensive network security. It should be able to regulate all the traffic happening between external systems and containers and help in isolating apps as well as preventing lateral movements.
Threat Detection and Vulnerability Scanning
The container security tool must conduct continuous monitoring of the containerized app and infrastructure to identify threats and vulnerabilities. Once it identifies the threat and vulnerability, it should be able to respond to the issue quickly to prevent any data breach or other impact.
Forensics
Having a tool with forensics capabilities will help you to analyze all the security events and find out the main reason behind the origin. Based on the details of the attack, it will help your team to implement corrective measures and prevent such events from occurring in the future.
Compliance Support
Compliance support is important for an organization because it helps them comply with the specific industry regulations they follow. So, it would be best to have a tool with compliance control and reporting features, as this will ensure that the application adheres to all the guidelines.
Integration with Existing Tools
You will have to make sure that the container security tool integrates seamlessly with DevOps and SIEM tools. The integration with DevOps tools will help you automate the security inspection across the development stage, whereas integration with SIEM will ensure all the security events are recorded.
10 Best Container Security Tools in 2025
We understand going through all the top security tools in 2025 and finding the appropriate one for your organization can be very tricky. That is why we have come up with a brief comparison table that will help you to differentiate between all tools and diligently select the ideal container security tool:
|
Tools |
Threat Detection |
Compliance Support |
Key Features
|
Pricing |
|
CloudDefense.AI |
Limited |
Available |
1. Accurately vulnerability scanning. 2. CI/CD integration. 3. Extensive security information. 4. Prioritization tag. |
The price is available after you request a demo. |
|
Prisma Cloud |
Available |
Available |
1. Prioritization remediation. 2. Maintain audit history. 3. Repository and registry scanning. |
The price starts at $9000 per year. |
|
Snyk |
Available |
Limited |
1. Automated remediation. 2. Continuous monitoring. 3. Dev-centric design. |
It starts at $52 per month for teams. |
|
PingSafe |
Limited |
Available |
1. Complete visibility into containers. 2. Contextual alerts. 3. Unique attack intelligence. |
The price is available after you request a demo. |
|
Aqua Security |
Available |
Available |
1. Dynamic scanning for malware. 2. Flexible image assurance policies. 3. Virtual patching. |
The price starts at $50,000 per year. |
|
Qualys |
Available |
Available |
1. High-accuracy vulnerability scanning. 2. Metadata of images. 3. CI/CD integration. |
The price starts at $995 per host for every year. |
|
Sysdig |
Available |
Available |
1. Managed policies based on ML and Falco. 2. Compliance standard controls. 3. Automated incident response. |
The price is available after you request a demo. |
|
Orca Security |
Available |
Available |
1.SideScanning technology. 2. Support over 100 compliance templates. 3. CDR capabilities. |
The price is available after you request a demo. |
|
Anchore |
Available |
Available |
1. Automated vulnerability scans. 2. Monitors SBOMs across the lifecycle. 3. Flexible policy enforcement. |
The price is available after a quote request. |
|
Alert Logic |
Available |
Available |
1. Real-time analysis. 2. Insight into container activity. 3. Continuous security monitoring. |
The price starts at $31,800 per year. |
|
Wiz |
Available |
Available |
1. 100% complete visibility. 2. Real-time monitoring and detection. 3. Security graph for prioritization. |
The price is available after you request a demo. |
Here’s the detailed review of all the top container security tools in 2025 we have found out after a thorough investigation based on our past experience:
CloudDefense.AI

CloudDefense.AI 
With CloudDefense.AI integrated seamlessly into your containerized environment, you won’t ever have to worry about protection and risk mitigation. It is a leading tool with container vulnerability management that will revolutionize the way you protect your containerized application.
From providing advanced container scanning and shift left security and prioritizing vulnerabilities to offering security insight, CloudDefense.AI provides a comprehensive container security solution for you. However, the features that have made it popular among organizations are agentless deployment and complete coverage across your infrastructure.
Key Features
CloudDefense.AI is equipped with some defining features that make it easy for you to detect all the security flaws and prevent them from entering the deployment stage. Here’s how CloudDefense.AI’s container security tool delivers comprehensive protection for containerized environments through a proactive, fully integrated approach:
Smooth CI/CD Pipeline Integration
Security measures are embedded directly within CI/CD pipelines, catching vulnerabilities early and preventing risks from progressing to production.
Thorough Container Image Scanning
Every container image undergoes advanced scanning before deployment, allowing only trusted, compliant images to be introduced into your environment.
Real-Time Threat Detection
Continuous monitoring flags suspicious activities in real time, enabling rapid response to threats and minimizing potential damage.
Automated Compliance Management
Compliance checks are automated, simplifying regulatory adherence and ensuring container environments consistently meet industry standards.
Lifecycle Runtime Protection
Our security monitoring continues post-deployment, catching anomalies and potential breaches throughout the container’s lifecycle.
Customizable Security Policies
Customize security policies to meet your organization’s specific needs, adapting these policies as your requirements evolve.
Automated Remediation
Swiftly mitigate risks as they arise, reducing manual intervention and keeping your team focused on strategic, high-priority tasks.
Pros

Helps the developers with an accurate vulnerability assessment in the container and prevents them from entering runtime.

It scans both base container images and Dockerfile commands.

Integrates with CI/CD pipelines to introduce vulnerability checks.

Provides vulnerability prioritization tags and allows the team to target the most impactful issue.

Highly intuitive interface with a detailed insight into vulnerabilities.
Cons

It might be expensive for an organization with a limited budget.

This tool is only suitable for organizations looking for vulnerability scanning.
What Sets Us Apart?
CloudDefense.AI might seem like just another container security tool, but there are certain factors that make it a top choice for most organizations:
Accurate Assessment
One primary reason CloudDefense.AI is widely preferred by many is because of its ability to accurately identify flaws and vulnerabilities in assessment.
Developer Centric Approach
Unlike a lot of container security tools, this solution provides a developer-centric approach where they offer insight into vulnerable images and dependencies.
Prioritization Tags
This tool helps in effective risk management by providing prioritization tags for each identified vulnerability in the container.
Prisma Cloud

Prisma Cloud
Another top container security tool that helps you secure your containers on any private or public cloud is Prisma Cloud. It is a one-stop solution that not only scans container images but also helps you to enforce policies for full development lifecycle.
Prisma cloud provides full visibility into your images and dependencies and also maintains compliance. Importantly, the agentless deployment makes it easier for you to integrate the solution to your containers.
Pros

Prisma Cloud, by using machine learning, delivers impressive threat detection and mitigates them before they make any impact.

It detects anomalous behavior by automatically running containers based on network and process behavior.

Gives you complete visibility into all your container network communication across your cloud.

It integrates with secret management to enable secrets to be securely provided to the container.

It adds compliance checks at every stage of the build and runtime.
Cons

For deployment, you will take professional assistance.
Snyk

Snyk
Snyk is a dev-first container security tool that helps developers to identify, and fix vulnerabilities through the SDLC. Through this console, DevOps can evaluate the risk posture of all the container images and prioritize them based on criticalness.
Moreover, it continuously monitors the containers and dependencies to prevent any vulnerability from reaching the deployment stage. A unique feature of this tool is that it scans PRs and test projects directly from the repository.
Pros

Snyk provides actionable remediation advice that aligns with most organization’s DevOps processes.

It helps remediate issues in open-source dependencies present in the base image and Dockerfile commands.

Provides a unified security platform to help you get a broad view of your containers.
Cons

The threat detection capability isn’t highly robust.

It doesn’t offer complete compliance management.
PingSafe

PingSafe
Considered as one of the advanced container security tools in the industry, PingSafe makes an agentless approach where it scans containers and nodes to minimize blind spots. It protects containers across development and deployment and creates alert prioritization that ultimately helps you remediate issues with proper effectiveness. This solution also offers compliance monitoring and unique attack intelligence to enhance the security posture.
Pros

You get complete visibility into all the containers along with the cloud infrastructure and SBOM.

It simulates various cyber attacks to understand the perspective and help you take necessary measures.

Through continuous compliance monitoring, it makes sure all the policies align with the regulation requirement.

Ensure effective vulnerability mitigation by contextualizing alerts.
Cons

The basic plan comes with an expensive price tag.
Aqua Security

Aqua Security
When it comes to protecting containerized applications throughout its full lifecycle, one tool that many organization prefer is Aqua Security. This tool scans all the container images to provide you full visibility of vulnerability posture and also offers detailed audit reports to ensure optimum compliance posture. With this tool, you will also get dynamic analysis, risk explorer, behavioral analysis, workloads firewall, and many other impressive features.
Pros

Aqua Security offers a suite of features that help in building optimum container security.

It is helpful in finding advanced malware hiding under 3rd-party images and open-source packages.

This tool provides you with vShield that offers virtual patch unfixable vulnerabilities.

Runtime control enables the team to identify and prevent suspicious behaviors.

Uses advanced behavioral profiling by leveraging machine learning to analyze container’s behavior.
Cons

It is highly resource-intensive.

The base plan comes at a significant price point.
Qualys

Qualys
You can also consider Qualys as your container security tool, as it provides you with deep visibility and security across your container environment. It is a powerful tool that not only offers vulnerability detection and remediation capability but also enables the DevOps team to enforce policies to block vulnerable images. It can also analyze vulnerability scans on container images and detect configuration drift in the running containers.
Pros

It provides a complete inventory of container assets like images, registration, and associated containers.

Provides you with a granular classification of all vulnerabilities.

Ensures continuous vulnerability scanning to identify threats with high accuracy and remove false positives.

It gives the DevOps team actionable data for effective remediation.
Cons

To get all the features, you will have to go for the higher subscription model.

The incident response capability isn’t that great.
Sysdig

Sysdig
Detects threats in your containers and deploy applications securely with Sysdig, which has emerged as one of the best container security tools. This tool seamlessly integrates into your CI/CD pipeline and runtime to secure the application and dependencies across the containerized environment. Sysdig has been garnering a lot of attention with its ability to automatically eliminate malicious containers before they make any impact.
Pros

Leverages specialized security policy-based ML and Falco to secure the runtime.

Perform deep image scanning to eliminate vulnerabilities, misconfiguration, and exposed secrets and automatically prioritize them.

Helps in passing audits of various compliance standards for the container environment and enforces OPA.

It is completely suitable for both mid-range and large-scale organizations.

The interface is properly laid out, making it easy to navigate.
Cons

It will require a lot of resources to handle a large number of containers.
Orca Security

Orca Security
Once you implement Orca Security in your containerized environment, you will never have to worry about container security. This agentless tool deploys within minutes and scans every layer of your container to provide complete visibility to vulnerability posture. It utilizes patented SideScanning technology that quickly finds and prioritizes risks.
Importantly, it integrates compliance checks into CI/CD pipelines and ensures optimum compliance support.
Pros

Orca Security has the capability to detect, investigate, and respond to threats in your containers with ease.

It provides over 100 out-of-the-box compliance templates for effective compliance.

Orca Security combines workload-deep intelligence and cloud configuration metadata and shows them through a single platform.

It is an agentless platform that utilizes patented technology to thoroughly check for threats in the container images.
Cons

Getting accustomed to the advanced features can be complex.

You won’t get upfront pricing for this tool.
Anchore

Anchore
Anchore is a top-of-the-line container security tool that automates vulnerability scans in your development lifecycle and monitors SBOMs to identify container risks. With this tool, you will get almost little false positives and it is due to the impressive signal-to-noise ratio. Anchore can easily identify container images that violate compliance and utilizes flexible policies to ensure the images meet compliance standards.
Pros

It offers a wide coverage by extending scanning for dependencies.

Anchore helps in the quick remediation of vulnerabilities by implementing security scans at an earlier stage of development.

This tool prioritizes vulnerabilities based on their severity and minimizes false positives.

It analyzes SBOMs to identify software dependencies and get reports of vulnerabilities.

Helps in maintaining compliance with industry standards throughout the lifecycle.
Cons

Implementation requires a huge learning curve.

You won’t get real-time threat detection.
Alert Logic

Alert Logic
We proudly present Alert Logic, which analyzes signatures of your data packets in your containerized environment in real-time and provides notifications about threats. It collects and analyzes network traffic and provides you with complete visibility of the vulnerability posture. Most importantly, it provides reports to the team on whether a vulnerability is actively targeting your container environment.
Pros

Alert Logic provides the developers with real-time visibility of their container environment.

It provides insight into container activity by collecting, aggregating, and searching container application logs.

You can utilize this tool in an on-premise environment and on the AWS, Azure, or GCP platforms.

It helps in staying compliant with popular industry regulations like PCI DSS, GDPR, SOC 2, NIST, and others.

It delivers a highly effective incident response.
Cons

The extensive feature list can be difficult to manage.
Wiz

Wiz
With Wiz integrated into your container environment, you can get complete visibility into your containers and eliminate all blind spots. Wiz offers the Security Graph feature, which helps the tool to identify vulnerabilities and misconfigurations and prioritize risks according to their severity. Unlike a lot of tools, Wiz equips real-time monitoring and detection capability that helps in discovering lateral movement and various serious threats.
Pros

Wiz provides an in-depth risk assessment which helps the team to find threats with the most impact.

It helps in securing the container images from development to runtime.

It automatically correlates container security threats across real-time signals and cloud activity to identify lateral movement.

Wiz connects public and private registration to scan them.
Cons

The compliance management is basic.

It comes with advanced capabilities that might be difficult to handle.
What is Container Security?
Container security refers to the practice of implementing protective measures to secure containerized applications and their infrastructure throughout the entire lifecycle, from deployment to runtime.
It ensures that containers are safeguarded against vulnerabilities and security risks by integrating continuous security processes within the development workflow. Key elements of container security include access control, vulnerability scanning, network segmentation, configuration management, and real-time monitoring.
Unlike traditional security, container security addresses the complex, dynamic nature of container environments, focusing on safeguarding applications and sensitive data within these adaptable, scalable systems as a critical part of modern cybersecurity practices.
What are Container Security Tools?
Container security tools are specialized solutions designed to protect containerized environments by addressing security challenges across application components, networks, and infrastructure.
Widely used by DevOps teams, these tools enable complete security management throughout the container lifecycle, from development to deployment and runtime. Key features include access control, vulnerability testing, and real-time monitoring to ensure secure access and proactively identify potential risks, including zero-day vulnerabilities.
By integrating security into CI/CD pipelines, these tools enforce security standards, simulate attack scenarios, and protect infrastructure, ensuring all container components operate securely and in compliance with established security configurations and policies.
Conclusion
Container security tools have become a vital requirement for modern organizations building their application in a containerized environment. An integration of these tools helps you proactively identify vulnerabilities, ensure compliance, and discover malicious activity.
In this article, we have outlined the 10 best container security tools. From here, you can choose the security tool that best suits your organization’s requirements. These tools can easily integrate into your SDLC, and as your container environment grows, they can adapt accordingly.







