Your computer is vulnerable to constant cyber threats lurking in the shadows. Malware is perhaps the most prominent— an insidious method of intruding into a system and causing harm. According to data, there were about 5.5 Billion malware attacks in 2022, with 550,000 new malware found daily.
Data like this shows the significance of malware in cyber security. However, having a clear understanding of this attack method is vital to take necessary security steps.
A quick read through this article will help you grasp the basics of how to prevent malware attacks and obtain a better understanding.
So, let’s dive right in!
What Is Malware in Cyber Security?
Malware, a portmanteau of the words malicious and software, is software designed to exploit a system after infecting it. It is an umbrella term including malicious components such as trojans, viruses, etc.
Hackers use malware as a method of infiltrating a system to show victims unwanted ads, steal information, or even take the whole system hostage by encrypting all files.
Malware comes in varying forms, with each one having different functions and ways they affect a system. Each one of them achieves a different goal for the attacker. Malware is often used as an initial attack vector to gain access to a system before a primary attack is launched.
What Is the Purpose of Malware?
As mentioned, malware is widely used to intrude into a system to gain remote access, steal personal information, and gain insight into the device or the network connected to the device. With the significant number of malware available on the internet, your system likely already has one present inside.
All malware is not severe or aggressive; some are just harmless software created for pranking others.
Nonetheless, it is a best practice to take anti-malware approaches to secure your computer from any potential malware attacks.
Types of Malware
Malware is an umbrella term that defines a number of different threat components. Below, we have listed 15 different types of malware attacks in cyber security.
- Viruses: Viruses infiltrate other programs or applications in a system. This makes it more challenging to detect them.
- Worms: A worm is similar to a virus. It continuously replicates itself to infiltrate as many components as possible by exploiting vulnerabilities.
- Trojan: Trojans are malicious software in the guise of legitimate-looking software. They primarily exist in the form of free versions of premium software.
- Backdoor: Backdoors allow cyber attackers to gain remote access to a system. They work covertly to bypass user authentication methods and gain access to the system.
- Ransomware: Ransomware takes a system hostage by encrypting the files in the system. The victim then must pay a ransom to get their files back.
- Adware: Adware is designed to present a victim with unwanted advertisements. In return, the attackers get paid for each click on the advertisements.
- Botnets: Botnets use a group of infected computers to carry out Distributed Denial of Service (DDoS) or other forms of self-operating attacks on a system.
- Hijackware: Hijackware hijacks the browser of a system to redirect users to random websites or advertisements.
- RAM Scrappers: This method targets the RAM where data is stored for a short period of time. It is highly effective against POS (Point of Sale) systems as it contains the credit card details of customers.
- Cryptojacking: Cryptojacking occurs when crypto mining malware installs itself on a victim’s device and runs in the background to mine cryptocurrency. This process is covert and hard for the victim to spot.
- Malvertising: Malvertising positions malicious advertisements on legitimate sites. When a user accidentally clicks on one of these ads, they accidentally download malware.
- Grayware: Grayware is not entirely malware but it is software that has minimum functionalities and only installs itself to slow down a computer. Grayware can be a point of access for hackers.
- Spyware: Spyware is software used to spy on a victim. It preys on the victim’s personal information and other data on the system and transfers it to the attacker.
- Bots: Bots are infected computers that can be controlled remotely. They are often used to launch cyber attacks by hackers.
- Phishing: Phishing emails or social engineering attacks work as carriers of malware. They are legitimate-looking emails that target certain individuals and entice them to download any malicious content that is attached to them.
How Is Malware Distributed?
The distribution of malware continues to rely heavily on exploiting human behavior through social engineering. Threat actors use various tactics to deceive and manipulate users, leading them to unintentionally download, install, and run malware on their computers or devices.
Here are some common methods that threat actors use for malware distribution.
Via Email Attachments
Phishing emails often employ a deceptive strategy in which malware disguises itself as seemingly harmless attachments, such as invoices or images. Users, unaware of the malicious nature, may unknowingly download these files.
Once on the user’s device, the malware uses techniques like self-unpacking or remaining dormant until activated by user interaction. Subsequently, when triggered, it executes its malicious code, potentially compromising the integrity of the system and exposing sensitive information.
Phishing Emails or Unsafe Websites
Phishing email scams utilize social engineering techniques to trick individuals into clicking on links disguised as threats, warnings, or tempting offers. These deceptive links often redirect users to malicious websites engineered to download malware automatically upon page loading.
Malicious Advertising
Malvertising involves the practice of implanting malware within online advertisements. When individuals visit websites featuring these compromised ads, the malware is inadvertently downloaded onto their devices.
The concerning aspect of malvertising lies in its ability to manifest on reputable websites, presenting a challenge in terms of evasion and prevention.
Infected Storage Devices
Cybercriminals might deliberately position storage devices like thumb drives containing hidden malware in public areas. If users insert these devices into their computers to check their contents, the malware can move onto the computer, causing an infection.
It’s essential to avoid connecting unfamiliar or suspicious storage devices to a computer to minimize the risk of potential harm.
Employee Negligence
The effectiveness of malware distribution increases when computer or device owners overlook the importance of keeping their software current. Outdated software creates openings for malware, as worms frequently exploit these vulnerabilities before patches can be applied.
Consistently updating software and adhering to security best practices are crucial in reducing the likelihood of malware infections.
How to Detect Malware?
Detecting malware is a crucial defense against potential threats to your systems and data. There’s a variety of methods and tools at your disposal to carry this out. Antivirus and anti-malware scanners serve as the most popular options, scanning for known malware signatures.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) monitor network and system behavior for any irregularities that may indicate a malware attack. Activity-based detection, on the other hand, directly matches files or processes with a database of known malware activities.
Additionally, network traffic analysis helps uncover signs of malware communication with command and control servers, and endpoint detection and response (EDR) offers real-time monitoring and response capabilities.
User and entity behavior analytics, file integrity monitoring, email and web filtering, and threat intelligence feeds all assist in malware detection.
How to Get Rid of Malware?
Malware removal from a compromised system is crucial to ensure the complete security of your system. Follow the advice suggested below to safely remove malware from your computer.
Isolate the System: The best way to start is by isolating the infected system from the network and disconnecting it from the internet to prevent further spread.
Use Anti-Malware Software: Use reputable antivirus and anti-malware software to scan and identify the type of malware. Isolate any infected files and processes found during the scan and ensure you have a backup of essential data.
Remove Manually: In case you can’t remove the malware using the security tools, you may need to remove it manually. This involves deleting malicious files, registry entries, and processes, but caution should be taken before doing this.
Constantly Monitor: Monitor the system for any signs of new malware and educate company employees on how to detect and report malware. Seeking professional help may be necessary if the malware proves to be stubborn or if sensitive data is at risk.
How to Prevent Malware Attacks: 7 Security Tips
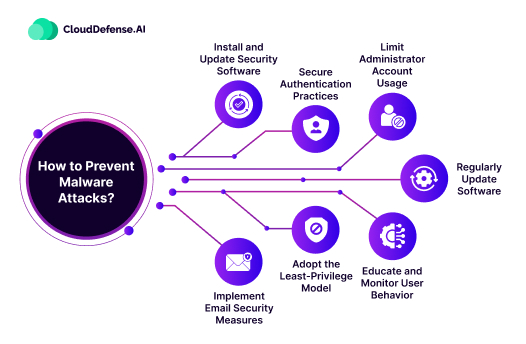
Preventing malware attacks is a piece of cake if you have certain best practices in place. Implementing strong cybersecurity practices, including regular software updates and patches.
Here are seven tips for you to prevent malware attacks.
Install and Update Security Software
Utilize reputable anti-virus and anti-spyware programs to scan and remove malware regularly. Keep these security tools up to date and promptly remove any detected threats.
Secure Authentication Practices
Enhance account security by enforcing strong passwords with a mix of characters. Implement multi-factor authentication methods, such as PINs or security questions, and consider biometric tools. Avoid saving passwords on devices and use secure password managers when necessary.
Limit Administrator Account Usage
Minimize the use of administrator accounts for routine tasks. Only log in as an administrator when necessary for specific administrative functions. Install software with administrator credentials only after ensuring its legitimacy and security.
Regularly Update Software
Stay proactive against malware by updating all software, including operating systems, browsers, and plug-ins. Regularly validate and install software patches to address new vulnerabilities and enhance overall system security.
Educate and Monitor User Behavior
Educate users about common malware threats, cybersecurity best practices, and how to recognize potential risks. Monitor user accounts for any suspicious activity, log incoming and outgoing traffic, and promptly investigate and address any unusual actions.
Adopt the Least-Privilege Model
Embrace the principle of least privilege by granting users in your organization the minimum access necessary to perform their work. Restricting access to system capabilities, services, and data helps minimize the potential impact of a malware attack by limiting the scope of compromised accounts.
Implement Email Security Measures
Recognizing email as a common channel for malware, implement strong email security and spam protection measures. Scan all incoming email messages and attachments for malware, set up effective spam filters to reduce unwanted emails, and limit user access to company-approved links, messages, and email addresses.
This helps fortify your defense against malware delivered through phishing or malicious email content.
FAQ
Does malware affect mobile devices?
Yes, there is a specific malware that is designed to target mobile devices known as mobile malware. Mobile malware targets smartphones, smartwatches, and tablets. They are capable of exploiting any vulnerabilities that can be found in these compact devices.
Is malware a virus?
No, but it is the other way around when it comes to Malware vs. Virus. Malware is an umbrella term that is used to describe malicious software used to harm computer systems, on the other hand, a Virus is a type of malware.
How do I know I’ve been infected with malware?
Anti-malware software is the best way to spot any hidden malware in your computer. If you don’t have one, then you would need to rely on your instincts to identify a malware infection. You can do this by identifying slow performance, random apps, and unwanted advertisements.
Does malware affect Macs?
MacOS is less vulnerable than Windows when it comes to malware. The complex runtime protections in a Mac make it close to impossible for malware to gain access to it. Even if malware gets inside, Mac’s security features help to remove malicious components easily.
Conclusion
Malware is one of the most common attack vectors that cyberattackers consider to intrude into a system. The variety of ways hackers can fool a victim into installing malware makes it a great method for them.
Even though most malware is taken lightly and not considered a serious threat to a system, it surely has the potential to harm your data or other aspects of your infrastructure gravely. Malware in cybersecurity is that needle you might not spot easily on the ground but can greatly hurt you when you step on it.
We hope this article has been useful to educate you on how to prevent malware attacks in the best possible way.







