What is the Cyber Kill Chain?
The term “kill chain” might conjure images of military operations, and that’s exactly where the concept for cybersecurity originated. Developed by Lockheed Martin in 2011, the concept of the Cyber Kill Chain was inspired by the military’s traditional “Kill Chain” model, which outlines the structure of an attack mission, from initially identifying a target to engaging and assessing the effects of the attack. The Cyber Kill Chain adapted this idea to the cyber realm, providing a framework for understanding the distinct stages of a cyberattack.
With a clear understanding of each of these stages, cybersecurity professionals could get a better grasp of the bad guys’ tactics and strategies. It was like having a sneak peek at the enemy’s playbook, allowing defenders to anticipate the next moves and fortify their defenses accordingly.
Over the years, the Cyber Kill Chain model has evolved and been tweaked by different organizations, sometimes adding or rearranging the phases to better capture the ever-changing landscape of cyber threats. But at its core, it remains a powerful tool for demystifying the complexities of cyber attacks and developing effective countermeasures.
How Does Cyber Kill Chain Help in Cybersecurity Practices?
Here’s how the Cyber Kill Chain plays a crucial role in cybersecurity:
- Provides a structured framework for understanding cyber attack lifecycles
- Helps organizations identify potential attack vectors and entry points
- Enables proactive defense by implementing security controls at each stage
- Facilitates threat modeling and risk assessment activities
- Aids in incident response and forensic analysis by mapping attack stages
- Serves as a common language for communication among security teams
- Supports the development of security playbooks and incident response plans
- Helps prioritize security investments and resource allocation
- Enables continuous monitoring and detection of adversary tactics
- Promotes collaboration and information sharing within the security community
- Serves as a foundation for security awareness and training programs
- Encourages a proactive mindset shift from reactive to preventive security
- Assists in aligning security strategies with business objectives and risk appetite
- Facilitates the integration of threat intelligence into security operations
- Supports the evaluation and selection of security tools and technologies
- Provides a basis for measuring the effectiveness of security controls
- Encourages continuous improvement and adaptation to evolving threats
The Cyber Kill Chain: A Step-by-Step Look at How Hackers Operate
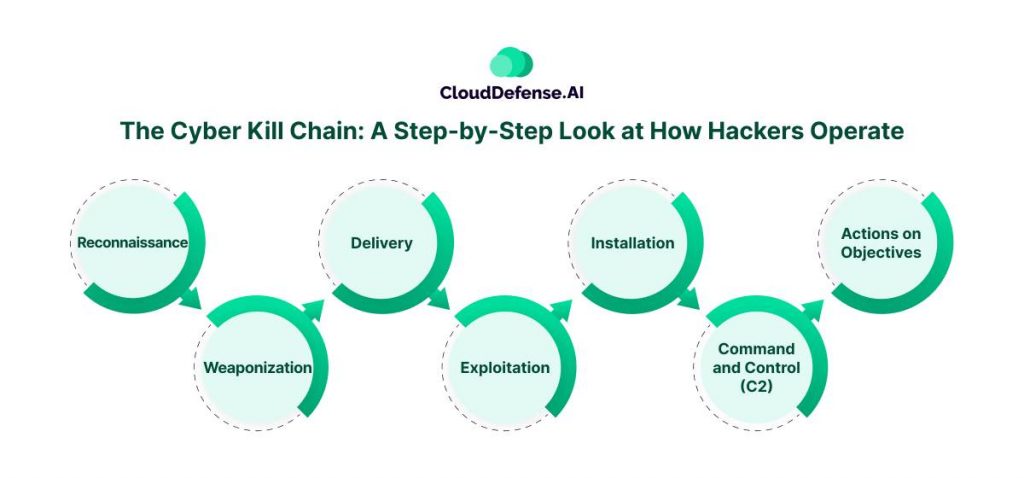
Imagine an attacker planning a heist. They wouldn’t just burst through the front door, right? They’d gather intel, find a weakness, and then carefully exploit it. The Cyber Kill Chain is like a blueprint for this cyber heist, outlining the seven distinct stages attackers typically follow to infiltrate a system and achieve their goals. Understanding these stages is crucial for building a strong defense against cyberattacks. So, let’s delve into each step:
1. Reconnaissance
Reconnaissance is the intel-gathering phase. Hackers scout potential targets, identifying valuable assets like financial data or intellectual property. They might use social media, phishing emails, or even exploit kits to gather information about your network infrastructure, employee habits, and security vulnerabilities—basically, anything that could give them an edge.
2. Weaponization
Armed with recon data, attackers craft their tools. This could involve modifying existing malware to exploit specific vulnerabilities or creating custom exploits. Think of it like customizing a weapon for maximum impact on your system’s defenses.
3. Delivery
Now comes the launch—getting that weaponized payload onto your systems. Phishing emails with malicious attachments, compromised websites, even legit sites injected with malware to target specific visitors—these are all fair game for hackers looking to slip past your security checks.
4. Exploitation
Here’s where the weapon is put to use. If the delivery is successful, the attackers will try to leverage those vulnerabilities they uncovered during recon. Maybe they’ll trick an employee into clicking a malicious link, exploit software bugs, or just brute-force their way through weak passwords. Any way in is a win for them.
5. Installation
Once they’ve breached your defenses, the hackers will dig in and make themselves at home, installing malware that gives them remote access, data-stealing capabilities, or the power to completely disrupt operations. It’s like they’ve picked up your digital lock and set up camp inside your network.
6. Command and Control (C2)
Of course, the hackers need a way to control their new digital playground remotely. They’ll establish covert communication channels to send commands, siphon stolen data, and manage their malware like a puppet master pulling the strings.
7. Actions on Objectives
With full access and control, they can finally execute their nefarious plans – stealing sensitive data, deploying ransomware, causing chaos by disrupting critical systems, or even using your network as a launch pad to attack others.
Critiques of the Cyber Kill Chain
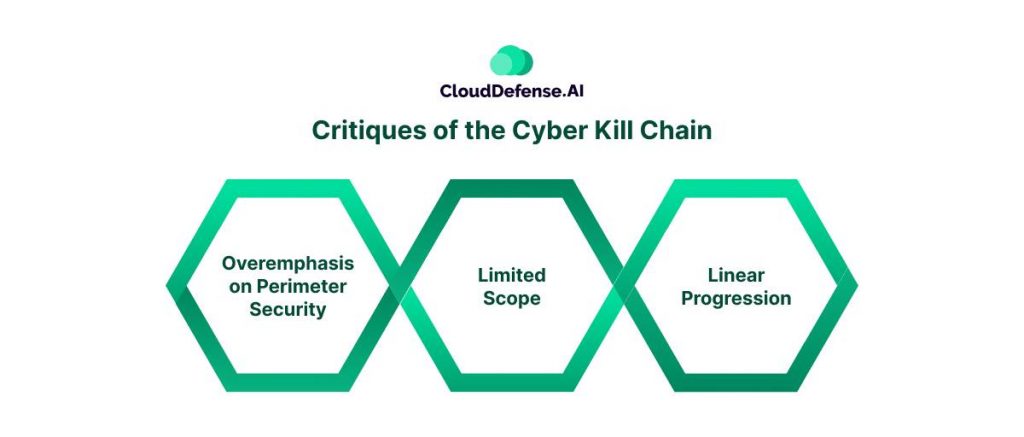
The Cyber Kill Chain has undoubtedly revolutionized cybersecurity by providing a framework for understanding attacker behavior. However, no model is perfect, and the Kill Chain has faced its share of critiques. Let’s dissect some of the key criticisms:
Overemphasis on Perimeter Security:
The Kill Chain heavily emphasizes the initial stages (reconnaissance, weaponization, delivery) which often occur outside an organization’s network perimeter. This can lead to a false sense of security if an organization focuses solely on perimeter defenses like firewalls. In today’s cloud-based world with a growing attack surface (remote work, IoT devices), traditional perimeter defense isn’t enough.
Limited Scope:
The original Kill Chain primarily focused on preventing malware-based attacks. However, modern threats encompass a wider spectrum, including insider threats, social engineering scams, and zero-day exploits (previously unknown vulnerabilities). The Kill Chain doesn’t adequately address these evolving threats.
Linear Progression:
The Kill Chain depicts a linear progression, suggesting a clear beginning, middle, and end. In reality, attacks can be more fluid. Attackers might jump between stages, linger in one stage for extended periods, or even launch multiple, simultaneous attacks. This linear view can make it difficult to adapt to real-world attack scenarios.
Cyber Kill Chain vs. MITRE ATT&CK
Both the Cyber Kill Chain and MITRE ATT&CK are valuable frameworks in the cybersecurity realm, but they serve different purposes. Here’s a breakdown of their key differences:
| Feature | Cyber Kill Chain | MITRE ATT&CK |
| Short Description | A sequential model outlining the stages of a cyberattack | A knowledge base of adversary tactics, techniques, and procedures (TTPs) |
| Focus | High-level view of attacker behavior | Detailed breakdown of specific attack methods |
| Stages | 7 stages (Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control, Actions on Objectives) | Continuously evolving list of TTPs categorized into tactics and techniques |
| Scope | Primarily focused on malware-based attacks | Covers a wider range of threats, including insider threats, social engineering, and zero-day exploits |
| Progression | Linear progression of stages | Attacks can be more fluid and non-linear |
| Goal | Disrupt attacks at any stage | Identify and understand attacker TTPs to improve defense and detection |
| Use Case | High-level planning and communication | Detailed security analysis, threat hunting, and incident response |
| Limitations | Overemphasizes perimeter security, limited scope (doesn’t cover all attack types), linear view may not reflect real-world attacks | Requires ongoing effort to stay updated with evolving TTPs |
Final Words
Don’t be drained into a false sense of security! The Cyber Kill Chain lays bare the attacker’s methodical plan, but it’s a wake-up call, not a shield. Traditional defenses are crumbling. Advanced threats, insider attacks, and constant mutation render the perimeter irrelevant. The Kill Chain exposes the cracks, but it also offers a fighting chance. By understanding each stage, we can fortify our defenses, disrupt attacks, and fight back. The time to act is now. Before you become the next headline.







