Definition of a Firewall
A firewall is a critical network security device that serves as a protective barrier between a private internal network and the public Internet. It monitors and filters incoming and outgoing network traffic, following predefined security policies established by an organization.
The primary function of a firewall is to allow harmless traffic to pass through while blocking potentially harmful traffic, thereby protecting the network from cyber threats. Deployed in various architectures, including network-based, host-based, and cloud-based, firewalls operate based on predetermined rules to determine the legitimacy of external networks and applications.
As the first line of defense for network security, firewalls play a major role in preventing unauthorized access and ensuring the integrity of organizational data and systems.
What is the History of Firewalls?
Firewalls have a rich history dating back to the late 1980s when they emerged as packet filters, examining data packets transferred between computers. Initially, these packet-filtering firewalls provided rudimentary network security by scrutinizing packet headers for source and destination addresses.
As technology advanced, so did firewalls, evolving into more sophisticated forms to combat new cyber threats. In the 1990s, stateful inspection firewalls emerged, enhancing security by tracking the state of network connections.
The 2000s and the Present
The early 2000s witnessed the rise of proxy-based firewalls, adding an additional layer of protection by inspecting application-layer data. With the advent of cloud computing, FWaaS solutions became prevalent, offering scalable and flexible firewall protection.
Today, NGFW integrates advanced features like deep-packet inspection and IPS, reflecting the continuous evolution of firewalls to meet the dynamic requirements of the tech industry.
How Does a Firewall Work?
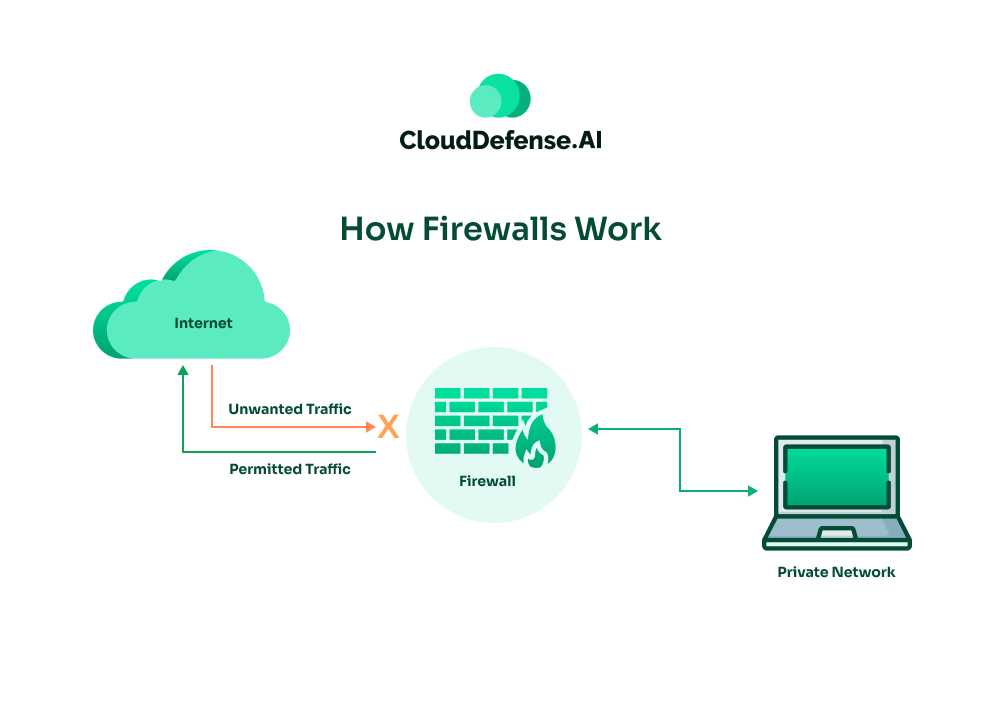
Firewalls serve as vigilant gatekeepers, shielding networks from potential threats by scrutinizing incoming data packets. Through a multi-layered approach, they analyze the content, intended destination, and origin of network traffic. Various firewall types employ distinct methods, including packet filtering, TCP verification, deep-layer inspections, and proxy checkpoints, to assess potential risks.
A firewall carefully evaluates incoming traffic based on predefined rules. It permits only authorized sources, or IP addresses, to access the network, effectively distinguishing between benign and malicious traffic.
These rules, established on packet data attributes like source, destination, and content, determine whether data packets are permitted or blocked. Modern firewalls, such as Next-Generation Firewalls, incorporate advanced techniques like machine learning to detect and thwart unusual data behavior preemptively.
Types of Firewalls
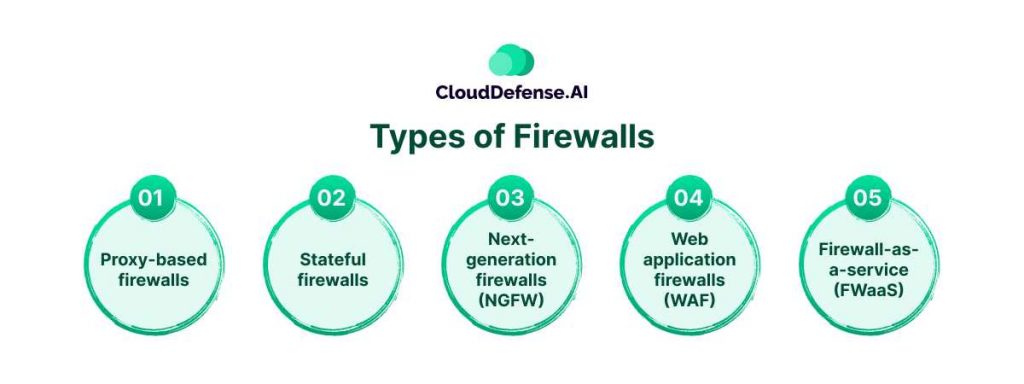
There are multitudes of types available when it comes to picking a Firewall. We have mentioned some of the widely used variants below for you:
Proxy-based firewalls:
Proxy-based firewalls operate at the application layer, filtering incoming traffic between networks. Acting as intermediaries, they establish connections to traffic sources, inspect incoming data packets, and evaluate TCP handshake protocols. This method enhances security by scrutinizing packet contents for malware and providing an additional layer of anonymity for network devices.
Stateful firewalls:
Stateful firewalls, also known as dynamic packet-filtering firewalls, monitor and regulate network traffic based on the state, port, and protocol of data packets. By maintaining a contextual database of validated connections, they make informed decisions regarding packet filtering, ensuring heightened security compared to traditional packet-filtering methods.
Next-generation firewalls (NGFW):
NGFW integrates deep-packet inspection with advanced features like application-level inspection and intrusion prevention systems. By analyzing network and endpoint events, NGFWs detect and mitigate emerging threats, offering comprehensive protection against sophisticated attacks beyond basic port and protocol filtering.
Web application firewalls (WAF):
WAF specializes in protecting web applications from common web-based attacks such as SQL injection, XSS, and DDoS attacks. They analyze HTTP traffic to identify and block malicious requests before they reach the web application, safeguarding against vulnerabilities and ensuring web application security.
Firewall-as-a-service (FWaaS):
FWaaS delivers firewall protection via cloud-based solutions, offering scalability and flexibility for evolving organizational needs. With the ability to scale resources dynamically, FWaaS ensures robust perimeter security and facilitates centralized management of firewall policies across distributed networks.
Why use a Firewall?
Firewalls, especially NGFWs, are essential for modern cybersecurity. They focus on blocking malware and application-layer attacks, swiftly detecting and combatting threats, and enforcing pre-established security policies.
Integrated with intrusion prevention systems, NGFWs provide simplified network-wide protection. With cyber threats enhancing themselves and expanding network complexities, firewalls are irreplaceable for businesses.
NGFWs offer comprehensive security solutions by integrating features like VPN, antivirus, and identity awareness, effectively guarding against advanced threats such as zero-day exploits and ransomware.
Are Firewalls Software-based or Hardware-based?
Firewalls are known to be both software-based and hardware-based. Consider checking the table below for a more in-depth comparison of both.
| Aspect | Software-based Firewalls | Hardware-based Firewalls |
| Deployment Location | Installed on individual computers or servers | Placed at the network perimeter or between network segments |
| Protection Scope | Protects the host it runs on (individual computer/server) | Protects the entire network beyond a specific point |
| Functionality | Monitors and filters network traffic at the host level | Acts as a secure gateway for the entire network |
| Operation | Analyzes data packets flowing to and from the device | Performs deep packet inspection and packet filtering |
| Scalability | Limited scalability, as each host requires individual setup | Broad scalability, suitable for medium to large networks |
| Resource Consumption | Consumes host resources such as CPU and RAM | Requires minimal host resources, independent operation |
| Configuration Complexity | Relatively easy to install and manage | Requires expertise to configure and manage effectively |
| Examples | Personal computer firewalls, server firewalls | Network appliances, router firewalls, gateway firewalls |
Final Words
It cannot be stressed enough how essential a Firewall is as the first line of defense for protecting against intruders. While simple packet-filtering or circuit-level gateways offer basic protection, stateful inspection, and next-gen firewalls provide a more impactful defense.
Employing multiple layers of firewalls enhances security through defense-in-depth, deterring attackers and buying time for response. Next-gen firewalls, equipped with advanced application-level inspection and threat prevention technologies, play a larger role in a security strategy.
We hope this article has equipped you with enough knowledge on the workings of a Firewall and how it has turned out to become a solid partner in protecting a company’s network.







