What is Fileless Malware?
You know how most malware works by getting you to download a virus file or worm that then installs itself on your computer’s hard drive? Well, fileless malware takes a very different approach.
Here’s the key difference: traditional malware needs to be stored on your device (like a downloaded file) to run. Security software can often detect and block these files. Fileless malware, however, operates entirely in your system’s memory, leaving no trace on the disk. This makes it much harder to identify and eliminates the signs that traditional antivirus might look for.
It exploits legitimate tools like PowerShell or macros in documents and can perform various malicious activities. These can include stealing data, installing additional malware, disrupting system functions, or even launching ransomware attacks.
Characteristics of Fileless Malware
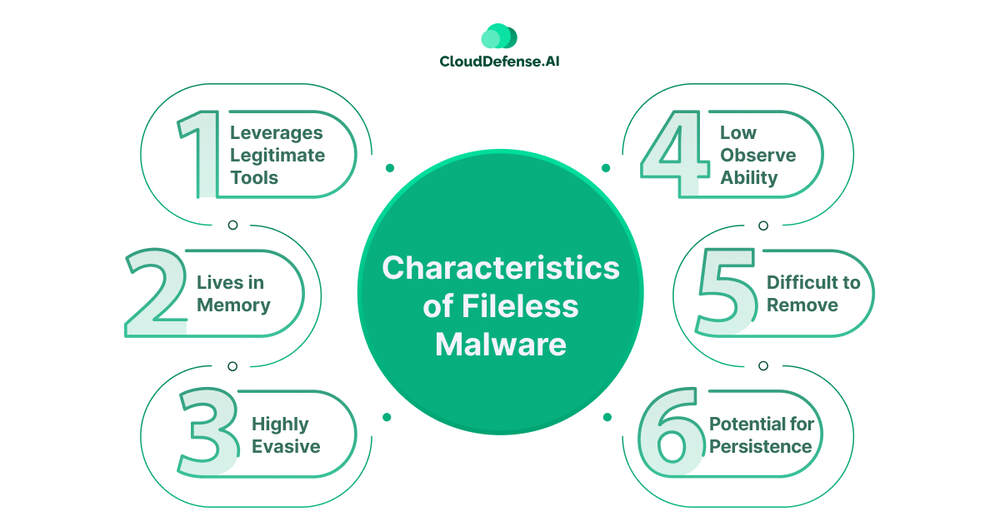
Fileless malware has become a major cybersecurity concern due to its ability to evade traditional defenses. Here’s a breakdown of its key characteristics that make it so sneaky:
- Leverages Legitimate Tools: Unlike traditional malware that arrives as a suspicious file, fileless malware weaponizes existing programs on your system. Think of it like a robber using your own tools to break in! This makes it harder to detect because these programs are often trusted and have legitimate purposes.
- Lives in Memory: Fileless malware operates entirely in your system’s memory, leaving no trace on the disk. Traditional antivirus software that scans for files on your hard drive becomes blind to this threat.
- Highly Evasive: By not leaving a physical footprint, fileless malware bypasses signature-based detection methods used by many antivirus programs. These programs rely on identifying known malware patterns, but fileless malware constantly evolves, making it difficult to track.
- Low Observability: Fileless malware often operates silently, making it harder to identify suspicious activity. There might not be any pop-ups, slowdowns, or unusual network traffic to raise red flags.
- Difficult to Remove: Since fileless malware doesn’t rely on files, traditional methods of simply deleting the malware might not be enough. Advanced security solutions are needed to detect and eradicate it from memory.
- Potential for Persistence: Some fileless malware can establish persistence mechanisms, allowing it to stay active even after a system reboot. This can involve hiding code in the registry or creating new user accounts.
How Does Fileless Malware Work?
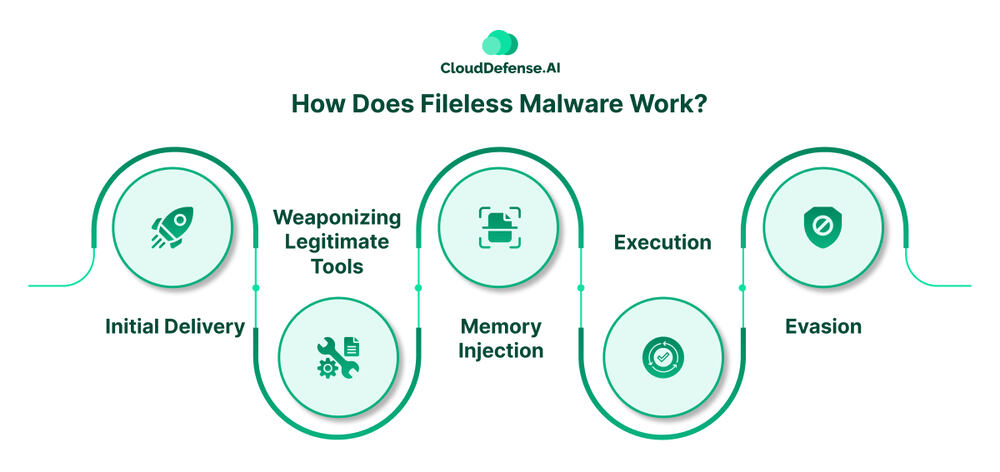
Fileless malware operates like a stealthy intruder, hijacking your system’s resources to achieve its nefarious goals. Here’s a breakdown of its typical attack cycle:
Initial Delivery
The first step is for the malware to reach your system. This can happen through various methods, including:
- Phishing emails: Clicking a malicious link in a seemingly legitimate email can download and inject the malware into memory.
- Infected websites: Visiting a compromised website can trigger scripts that launch the attack.
- Malicious downloads: Downloading infected attachments or software can unknowingly deliver the malware.
- Exploiting vulnerabilities: Hackers can exploit weaknesses in software like web browsers or document readers to inject the malware.
Weaponizing Legitimate Tools:
Once on your system, the malware doesn’t install itself like traditional malware. Instead, it leverages pre-existing tools you might already use, such as:
- PowerShell: This powerful scripting tool for Windows can be used for malicious purposes to download additional malware, steal data, or manipulate system settings.
- Macros: Macros embedded in documents like PDFs or Word files can be used to launch hidden commands and execute the malware.
- Script Host: Tools like Windows Script Host (wscript.exe) can be used to run malicious scripts disguised as legitimate task
Memory Injection
The malware code itself never touches the disk. It operates solely in your system’s memory (RAM), making it invisible to traditional file-based scans. Additionally, when you reboot your system, the malware disappears from memory, further hindering detection.
Execution
Now operating “in disguise,” the malware executes its malicious tasks within the memory of the compromised program. It can steal data, install additional malware payloads, disrupt system processes, or establish persistence to maintain access even after a reboot.
Evasion
Since it never writes itself to disk, fileless malware becomes a ghost in the machine, bypassing traditional file-based detection methods employed by antivirus software. This makes it incredibly challenging to identify and eradicate.
Types of Fileless Malware
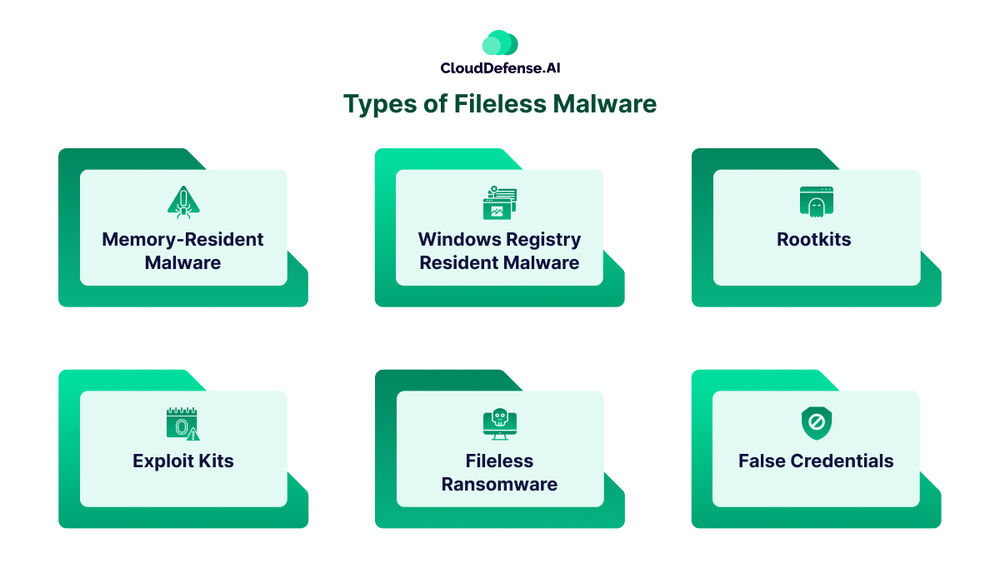
Fileless malware isn’t a one-trick pony. Attackers have developed various techniques to exploit your system’s resources. Here’s a closer look at some common types:
Memory-Resident Malware
As the name suggests, this type of malware lives exclusively in a system’s memory (RAM). It injects its malicious code directly into legitimate programs that are already running, essentially hiding inside approved software. Since it doesn’t write files to disk, it’s tough for traditional antivirus to catch.
Windows Registry Resident Malware
The Windows Registry acts like the brain of your operating system. This malware cleverly embeds itself within the registry, using a “dropper” program to deposit its malicious code. Configured to run at startup, it bypasses traditional security measures.
Rootkits
These are the master impostors of the malware world. Rootkits consume system memory and processing power to camouflage their malicious functions as approved operating system processes. Their intricate kernel-level disguise makes them a nightmare to identify.
Exploit Kits
Exploit kits are versatile hacker toolkits that probe for vulnerabilities in your system’s memory. Once they slip through the cracks, these kits can unleash a range of customized malware strains without touching disk.
Fileless Ransomware
This is ransomware 2.0. Instead of bulky files, it uses fileless tactics, hiding malicious code in document macros or exploiting memory. It then leverages built-in tools like PowerShell to encrypt your files, making them inaccessible without a hefty ransom payment.
False Credentials
This method involves brute force or stolen credentials to gain access to your system. Attackers then use “shellcode” – a series of commands – to launch their attack. They can maintain persistence by hiding code in the registry or kernel, or by creating new user accounts.
How to Detect Fileless Malware
Fileless malware might be stealthy, but there are ways to fight back. Here are some pointers to help you detect potential fileless malware infections:
- Maintain updated security software with the latest features to identify new fileless malware variants as they emerge. Consistent patch management is crucial.
- Monitor processes and network traffic patterns vigilantly for any anomalous behavior that could indicate fileless malware leveraging legitimate programs and network connections.
- Exercise caution when enabling macros or scripts from untrusted sources in Office documents, as these are common entry points for fileless malware payloads.
- Pay close attention to the usage of systems administration tools like PowerShell, WMI, and others, as threat actors exploit these utilities to execute malicious code directly in memory without dropping executable files.
- Be cognizant of signs that something is amiss, such as degraded system performance, crashes, or network lags, which may result from a fileless malware infection.
- Implement application whitelisting and least privilege controls where feasible to limit the execution pathways available for unauthorized code.
- Consider advanced endpoint detection and response solutions capable of behavioral monitoring to identify patterns associated with fileless attack techniques across your environment.
- Knowledge is power! Educate yourself and others who use your system about social engineering tactics and the dangers of clicking suspicious links or opening unknown attachments. Phishing emails are a common entry point for fileless malware.
- While not a direct detection method, having a recent backup can be a lifesaver in case of a ransomware attack. Regular backups ensure you can restore your files without succumbing to extortion demands.
Final Thoughts
The key is maintaining a healthy posture of security hygiene, ensuring your defenses are current, restricting attack surfaces, and closely monitoring for activity that deviates from the norm – as fileless malware employs insidious methods to obscure its presence. Proactive vigilance and robust security controls are essential to combat this evasive threat.







