What is Vidar Stealer?
The Vidar Stealer is a type of information-stealing, infostealer, malware that operates on the malware-as-a-service model, that was first discovered in late 2018. This malware targets Windows systems and is designed to collect a broad spectrum of sensitive data, including information from browsers and digital wallets. Vidar trojan is also utilized as a downloader for ransomware, enhancing its versatility and threat level.
Vidar Stealer Spreading Method
The primary method of delivery for Vidar Stealer throughout its history has been email spamming. This involves sending out mass emails that contain malicious attachments or links, which, when opened by the recipient, result in the installation of the Vidar malware on their system. This approach accounts for the vast majority of Vidar infections.
In less than 10% of cases, Vidar malware has also been distributed through other means, including:
- Injecting into Cracked Software Packages: Vidar malware can be embedded into pirated software that users download from untrusted sources. When the user installs the cracked software, they inadvertently install the Vidar malware as well.
- Deployment through Dropper Malware: Vidar malware can be installed on a victim’s system via dropper malware, which is a type of malicious software specifically designed to install additional malware.
While these alternative delivery methods are less common, they still pose a significant threat as they expand the range of vectors through which Vidar malware can infect systems. Consequently, a comprehensive strategy to prevent Vidar infections must include measures to guard against these various methods of distribution, not just email spam.
This requires a broader set of preventive actions, including strong email security, careful downloading practices, and the use of reputable anti-malware tools.
Vidar Stealer Analysis
Vidar Stealer is a sophisticated piece of malware that employs various techniques to evade detection and ensure its execution. Here is a detailed analysis of its methods and execution chain:
Evasion Techniques
One of the first tactics used by Vidar malware to avoid detection by antivirus software and analysis platforms like VirusTotal involves manipulating the file size. The malware sample includes a row of null bytes at the beginning of the file, inflating its size to approximately 700 MB. This bloated file size exceeds the limits that many anti-malware solutions are designed to handle, causing them to skip over the file entirely. This evasion technique is particularly used when Vidar is distributed via archives, such as through malvertising campaigns or email attachments.
Execution Chain
The execution chain of Vidar malware starts with its delivery method. When launched through macros, Vidar does not require any user intervention to execute, as the macros automate the process. However, the launch process involves several layers:
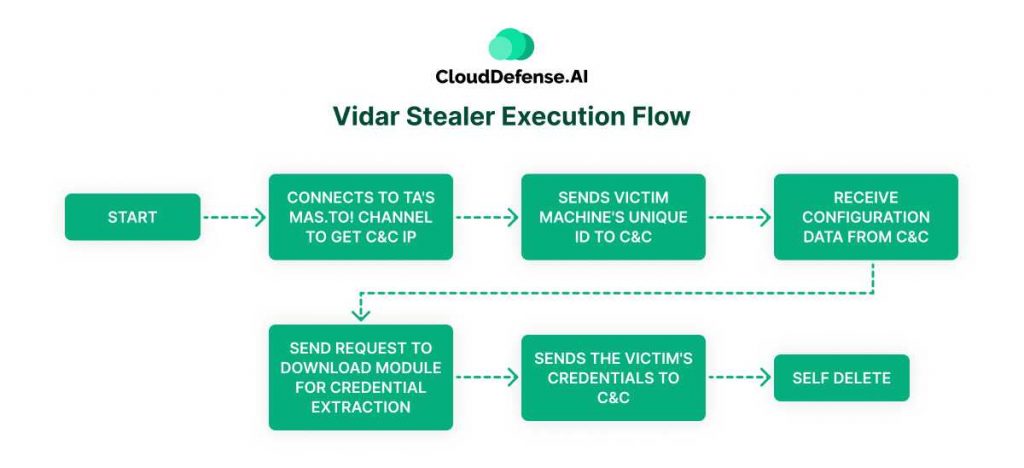
- String Encoding and Encryption: Vidar trojan samples often use base64 encoding and various encryption methods to obscure their strings. Although these measures add a layer of complexity, they are not exceptionally strong, allowing analysts to eventually decode and analyze the malware statically.
- Loader Utilization: Since early 2021, Vidar has consistently used a specific loader known as DerpLoader. This loader is responsible for the initial stages of execution:
- Memory Allocation: The loader uses the `VirtualAlloc` function to create a dedicated memory area for the malware.
- Decryption: The loader includes an 18-bit RC4 decryption key embedded in its code. This key is unique to each sample, ensuring that even if one instance is decoded, others remain protected.
- Injection and Execution: After decrypting the malware payload, the loader injects it into the allocated memory area and transfers execution to this area.
Post-Execution Behavior
Once Vidar is successfully executed, its first action is to contact its Command and Control server. This connection allows the malware to receive further instructions, download additional payloads, and exfiltrate stolen data.
How to Protect from Vidar?
Vidar poses significant threats to personal and organizational cybersecurity by stealing credentials and potentially delivering additional malicious payloads. Protecting against Vidar requires a well-planned approach that includes the use of advanced security software, employee training, and strict cybersecurity practices. Here are detailed strategies to protect against Vidar Trojan:
Use Anti-Malware Software
To defend against Vidar malware and similar threats, using strong anti-malware software is essential. Programs like GridinSoft Anti-Malware offer advanced detection systems and frequent updates, ensuring new malware samples are effectively blocked. Anti-malware tools can identify and neutralize threats that traditional antivirus solutions might miss, providing an additional layer of security.
Employee Training
Vidar malware often infiltrates systems through phishing emails and fake downloads. Training employees to recognize and handle suspicious emails and attachments can significantly reduce the risk of infection. Employees should be taught to verify the sender’s email address and look for discrepancies.
Email Security Solutions
Deploying email security solutions that scan and inspect email attachments for malicious content can prevent Vidar from reaching users’ inboxes. These solutions can detect and block phishing emails that deliver the Vidar malware, typically disguised as legitimate files.
Web Security Measures
Web security solutions can help identify and block malicious downloads and access to dangerous websites. Vidar often masquerades as free versions of legitimate software. Using web filters and secure browsing tools can prevent accidental downloads of malicious software.
Avoid Cracked Software
Using pirated software is a common way through which Vidar spreads. These cracked versions often come bundled with malware. To avoid this risk always download software from official sources. Other than that, encourage the use of licensed software within the organization and educate users on the dangers of using pirated software.
Check URLs Carefully
Phishing campaigns often use URLs that are slightly misspelled or look suspiciously similar to legitimate ones. Educate users to carefully check URLs before clicking, especially in emails and ads. You also need to look for signs of fraudulent URLs, such as misspellings or unusual domain names.
Endpoint Security Solutions
Endpoint security solutions provide comprehensive protection by monitoring and securing endpoints against various threats. These solutions can detect and block malicious downloads and clean up infections and prevent the spread of malware within the network.
Strong Passwords
Vidar targets credentials, often capturing password hashes. Using strong, complex passwords can make it significantly harder for attackers to crack them. Encourage the use of long and random passwords. You can also use password managers to generate and store strong passwords securely.
Multi-Factor Authentication (MFA)
Implementing MFA adds an extra layer of security, making it more difficult for attackers to use stolen credentials. Even if Vidar captures login details, MFA can prevent unauthorized access by requiring an additional verification step.
How Can Vidar Malware Be Removed?
Vidar malware is a persistent and dangerous threat that can compromise sensitive information and deliver additional malicious payloads. Removing Vidar from an infected system involves several critical steps, from initial detection to thorough system clean-up and recovery. Here’s a comprehensive guide to removing Vidar malware:
1. Disconnect from the Network
Immediately disconnect the infected computer from the internet and any connected networks to prevent further data exfiltration and the spread of malware to other devices.
2. Boot in Safe Mode
Restart your computer in Safe Mode to prevent Vidar and other malware from running during the removal process. To boot in Safe Mode:
- Restart your computer.
- Press F8 (or the appropriate key for your system) before the Windows logo appears.
- Select “Safe Mode with Networking” from the options.
3. Run a Full System Scan with Anti-Malware Software
Use a reputable anti-malware program to perform a comprehensive scan of your system. Software such as GridinSoft Anti-Malware, Malwarebytes, or a similar advanced anti-malware tool can detect and remove Vidar:
- Ensure the anti-malware software is up-to-date with the latest virus definitions.
- Perform a full system scan, not just a quick scan.
- Follow the software’s instructions to quarantine and remove any detected threats.
4. Delete Suspicious Files
Manually inspect and delete any suspicious files or programs. Pay particular attention to:
- Recently installed applications that you don’t recognize.
- Suspicious files in the Downloads folder or other common directories.
5. Check and Clean Up System Registry
Vidar may have added malicious entries to your system registry. Cleaning the registry can help remove residual malware components:
- Open the Windows Registry Editor (regedit).
- Navigate to HKEY_LOCAL_MACHINE and HKEY_CURRENT_USER and look for suspicious entries in the Software subfolders.
- Be cautious while editing the registry; deleting essential entries can harm your system.
6. Use a Bootable Antivirus Rescue Disk
If the malware persists, consider using a bootable antivirus rescue disk. These tools run outside of the infected operating system, making it easier to detect and remove deeply embedded malware:
- Download a rescue disk from a reputable antivirus provider (such as Bitdefender or Kaspersky).
- Create a bootable USB drive or CD.
- Boot your computer from the rescue disk and follow the on-screen instructions to scan and clean your system.
7. Update and Secure Your System
After removing the malware, take steps to secure your system and prevent future infections:
- Update your operating system and all software to the latest versions.
- Enable automatic updates for your operating system and security software.
- Install and configure a firewall to block unauthorized access.
- Use a comprehensive security suite that includes real-time protection and regular scans.
8. Change All Passwords
Vidar is known for stealing credentials. Change all passwords immediately after removing the malware:
- Use strong, unique passwords for each account.
- Consider using a password manager to generate and store complex passwords securely.
- Enable Multi-Factor AuthenticationA wherever possible.
9. Monitor for Signs of Further Infection
Keep an eye on your system for any unusual behavior that might indicate reinfection or residual malware:
- Regularly scan your system with anti-malware software.
- Monitor network activity for unusual connections or data transfers.
10. Seek Professional Help if Needed
If you are unable to remove Vidar malware using these steps, consider seeking help from a professional cybersecurity expert or a dedicated malware removal service.
Vidar Detection and Protection with CloudDefense.AI
At CloudDefense.AI, we offer a comprehensive suite of solutions designed to effectively tackle threats like Vidar malware. With our innovative Hacker’s View™ solution, we provide continuous monitoring for vulnerabilities and potential intrusion pathways, enabling us to anticipate and mitigate attacks proactively.
Our Noise Reduction technology prioritizes critical risks, allowing us to focus on actionable insights and efficiently reduce actual threats. Through our “Code to Cloud” approach, we ensure that security best practices are embedded from the earliest stages of development, preventing malware vulnerabilities from proliferating into production environments.
From infrastructure scanning to real-time threat detection and automatic remediation, we deliver strong protection across cloud environments. Our user-friendly dashboard empowers both technical and non-technical users to easily detect and remove malware, facilitating informed decision-making and swift responses to security incidents.
Book a free demo with us now and experience the full potential of CloudDefense.AI in protecting against Vidar malware and other cyber threats.







