What is a Rootkit?
A rootkit can be described as a malicious program that gives remote access to a system to a cyberattacker while staying hidden. The term “root” refers to the admin account of the system, whereas “kit” refers to the software component that implements the tool. Basically, it provides privileged root-level or administrative access to an endpoint device and enables threat actors to perform all malicious activities without raising any suspicion.
Once it is executed in the system, the rootkit generates a backdoor exploit, enabling the attacker to execute additional cyberattacks like ransomware, Trojans, keyloggers, etc. It also enables the delivery of payloads like bots to help attackers launch DDoS attacks or programs to disable security software.
In simple terms, the rootkit provides complete access through which the cybercriminal can control every aspect of the system and those connected to it. These types of malware can reach the kernel of the system disguised as legitimate code and simultaneously boot as the OS to avoid detection.
As a result, threat actors can steal all the data or manipulate the devices remotely without getting detected by antivirus or malware scanners. In modern times, rootkit malware is easily available on the dark web, and cybercriminals use social engineering techniques to trick users to enable permission for rootkit installation.
How Rootkits Work
Rootkit works in a smart way where they cover all the malicious code at the root and allow the attacker to take complete control of the system remotely. However, rootkits can’t propagate by themselves and require the support of various methodologies to infect a targeted system.
Methodologies like phishing, executable malicious software, malicious PDF documents, and social engineering techniques are utilized to trick users into giving permission to rootkit-installed programs for installation.
The malicious program gets embedded into the root of the OS and stays hidden until the cybercriminal activates it. Most of these malicious programs are built in such a way that they find a way around security efforts and solutions and stay hidden in the framework. Progressed rootkit attacks may create a situation where it will become difficult for the security team to eliminate the beginning of the attack.
The rootkit usually conceals various types of malicious tools like keyloggers, Trojans, antivirus disablers, bots, and banking credential stealers. Besides, there are some rootkits that are only designed to set up a backdoor exploit in the system.
Effects of Rootkit Attacks
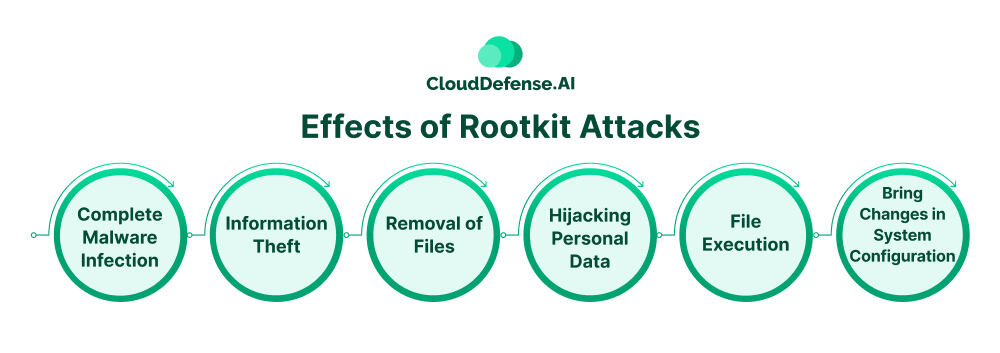
A rootkit attack has a severe impact on the system, and it not only puts many sensitive information on the endpoint at risk but also makes the business workflow vulnerable. When a rootkit gets entry, it provides remote access and enables an attacker to control the system.
So, a rootkit attack has a different outcome depending upon the intention of the attackers. Here are some common effects of rootkit attacks that your organization should know:
Complete Malware Infection
A rootkit, after getting installed on the system, can help in spreading malware containing Trojans, worms, bots, spyware, adware, and other disastrous malicious software. It compromises the performance and privacy of the device along with the network and devices with which it is connected.
Information Theft
Information theft is one of the severe effects of rootkit attacks as attackers can steal all the sensitive information and files containing login credentials, financial details, card details, and others. It creates a backdoor entry for remote access, and all the data can be transferred without any detection.
Removal of Files
Once a rootkit is executed into your system, it takes complete control of the OS, enabling it to delete files or system code according to the requirement of the attacker. Users won’t be able to recognize if any file is deleted.
Hijacking Personal Data
Rootkit carries various malicious tools like keyloggers to track all the keystrokes and extract all the required financial information. Rootkit attacks also lead to phishing attacks where attackers hijack sensitive financial and personal data that includes birth dates, credit card details, banking details, etc.
File Execution
An adverse effect of this malware attack is that attackers can remotely access the files on the system. Using complete access, the attacker can execute other files on the network connected to the device and facilitate large-scale infection.
Bring Changes in System Configuration
Besides deleting files or stealing data, rootkit attacks also allow cybercriminals to bring changes in the system configuration. Not only do they change the firewall settings but also bring changes in the startup script.
Symptoms of Rootkit Infection
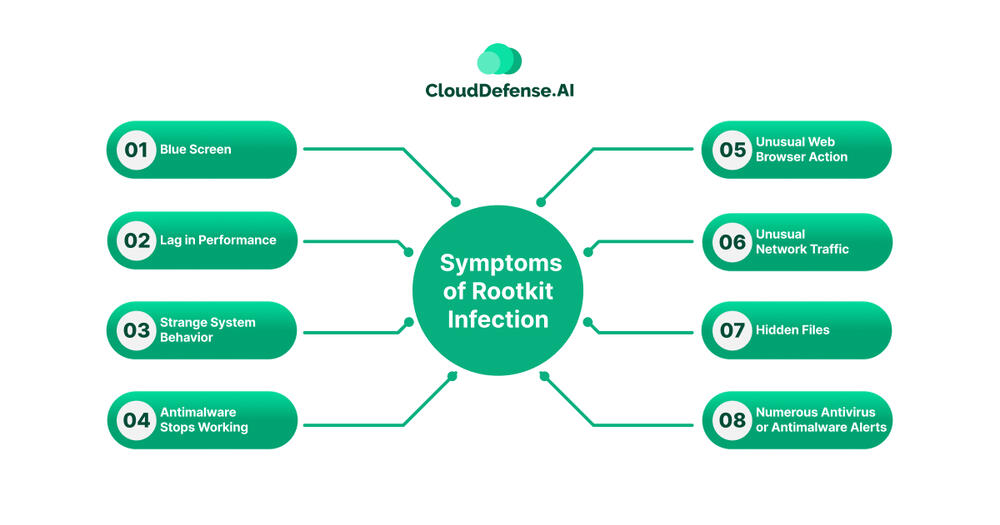
Detecting a rootkit infection on the system is not an easy task as they are designed to hide in the system code. Even though the program stays hidden, it showcases some signs that could indicate their presence in the system:
Blue Screen
A rootkit attack may lead to occasional blue screens with warning signs, and users will have to reboot the system to solve the issue. If you face such an issue, then it could be an indication of a rootkit presence in your kernel.
Lag in Performance
If you face sudden degradation in performance, slow boot time, unresponsiveness, or delayed shutdown, then it could mean that your system is rootkit-infected. Usually, rootkits, after gaining entry, consume a lot of resources, leading to a lag in performance.
Strange System Behavior
When a rootkit infects a system or endpoint of an organization, it could lead to strange system behavior. The system may face frequent crashes, sudden restarts, unexpected error messages, or other errors. In most cases, the rootkit brings changes in the system processes, which leads to strange system behavior.
Anti-malware Stops Working
If you observe that the antivirus or anti-malware software in the system suddenly stops working, then it is a sign of a rootkit attack. There are specific types of rootkits that are designed to disable anti-malware or antivirus to enable the attacker to carry on their malicious work smoothly.
Unusual Web Browser Action
While opening the browser, if you are redirected to an unrecognized website, then it could mean that you have a rootkit in your system.
Unusual Network Traffic
Rootkits create a backdoor for attackers to deliver more payload, and to achieve it, rootkits often establish unauthorized networks. If you see a sudden spike or excessive network activity even when you are not using the system, then it indicates a rootkit attack. Moreover, attackers often send or receive a massive amount of traffic, which can cause unusualness.
Hidden Files
Rootkits utilize advanced techniques to stay hidden in the system. If you discover hidden files or processes that are not supposed to be hidden or are suspiciously renamed, then it indicates that the rootkit is hiding in the file or directory.
Numerous Antivirus or Antimalware Alerts
Some modern antimalware or antivirus software has the ability to detect rootkit activity and generate alerts. If your security software repeatedly detects and quarantines some specific files or processes, then it is an indication of the presence of a rootkit.
Types of Rootkits
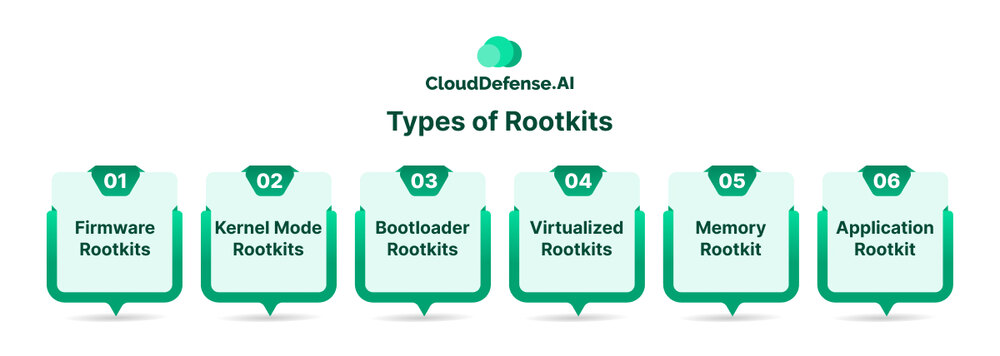
An attacker utilizes various types of rootkits when it targets a system, but the type of rootkit entirely depends upon the targeted system component along with the level of access.
Here are some common types of rootkits utilized by cybercriminals:
Firmware Rootkits
A firmware rootkit is the most common type of rootkit that is utilized by attackers and it is mostly utilized to infect the target system’s hard drive and BIOS. Also known as a hardware rootkit, this rootkit is usually installed on a small memory chip in the motherboard or on software that facilitates the boot process of the operating system.
This type of rootkit is as highly stealthy as it can stay in the system even after the OS has been reinstalled. Modern firmware rootkits can be remotely updated, and they also enable attackers to infect routers. Some popular firmware rootkits are UEFI rootkit, Cloaker and VGA rootkit.
Kernel Mode Rootkits
Designed to modify the functionality of the OS, the Kernel mode rootkit introduces malicious code and often structures to the OS of the infected system. It enables the attacker to take complete control of the system, which helps them to bypass security and prevent detection during the stealing of sensitive information.
By inserting their code, the hacker also can introduce their malicious program and carry on their malicious intent. The kernel rootkit gets injected into the memory when the OS boots, and it stays active until the OS shuts down.
Bootloader Rootkits
Bootloader rootkits are designed to target the Master Boot Record on the hard drive, which is the code that boots when a system starts. This rootkit type has the capability to subvert the boot process, and it can execute its malicious program before the OS loads in the system. It is also called a bootkit because it enables the attacker to control the system from the early stage of the boot process.
As the hacker replaces the legitimate boot-loaded with a malicious boot-loader, it becomes difficult for any kind of security solution to detect and remove them as they execute before the security solutions. Some famous bootkits are Stoned Bootkit, Olmasco, and Rovnix.
Virtualized Rootkits
It is a unique type of rootkit that has the same characteristics as a kernel rootkit, but it boots up before the operating system of the infected device. It is much more potent than traditional rootkits as it is deeply embedded into the system and enables a gateway for other malware.
Virtualized tools mostly control the master hypervisor machine as virtual machines and utilize it to perform various malicious activities. It is extremely difficult to detect as it doesn’t create a noticeable lag in the performance of the system Moreover, it is embedded in such a way that even many advanced anti-malware solutions can’t remove it.
Memory Rootkit
Memory or RAM serves as a critical component of a system, and through memory rootkit attacks, attackers hide the rootkit in the RAM of the infected system. Basically, it embeds itself in the framework’s RAM and doesn’t inject any malicious code. RAM of systems is widely targeted because it allows the attackers to perform various activities in the background without raising suspicion.
From modifying the running process and manipulating data to intercepting system calls, it performs a lot of malicious tasks. However, since RAM is a volatile memory, this rootkit has a short lifespan, and it only persists until the system restarts.
Application Rootkit
An application rootkit targets the regular application at the application layer of the target system, which enables hackers to utilize the system whenever a user opens the infected app. Basically, the attackers replace the regular files, especially files associated with the system, with rootkit files, giving complete access to the OS.
These rootkits mostly infect regular programs such as Office, Paint, Notepad, and others that are used regularly so that cybercriminals can use the system whenever they use them. The primary challenge is to detect these rootkits as the infected programs run normally. However, anti-malware and antivirus solutions can detect them as they run on the application level.
How to Detect a Rootkit Attack
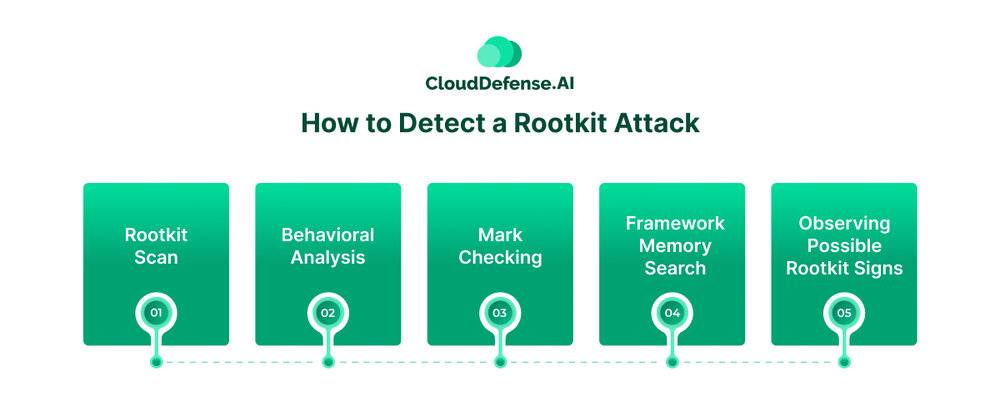
Detecting a rootkit in the system is quite a challenge as most of the rootkits have been designed to stay hidden.
Moreover, they embedded themselves deep into the system and boots before antivirus software, making it difficult for security solutions to detect them. Importantly, some rootkit disables security software. Here are some approaches you can utilize to detect rootkit attacks:
Rootkit Scan
A rootkit scan serves as the most effective way to detect rootkit attacks. It combs through the system for known attack signatures and performs memory dump analysis that identifies the instructions executed by the rootkit in the system’s memory.
Behavioral Analysis
Behavioral analysis is an effective functionality that you can utilize in the existing anti-malware or antivirus to discover rootkit-like behavior. Since it looks for rootkit-like behavior, it can spot rootkits before you understand you are being attacked.
Mark Checking
You can utilize a specific security solution to look for known rootkit marks in your infrastructure, and if you find any rootkit strain, then it could mean the presence of a rootkit. Every system works with numbers, and every product has a particular mark, which is a string of numbers designed to address the product in the system. Known marks from the database can help in detecting the rootkit.
Framework Memory Search
Another effective way to detect a rootkit is by scanning the framework’s memory and checking the overall status. The memory search will help you identify whether the memory is utilized for malicious activity or not. Examining the access point and keeping track of imported library operations DLLs can help you detect the presence of rootkit attacks.
Observing Possible Rootkit Signs
You can observe the system for possible signs like frequent blue screens, unexpected website redirections, unusual browser behavior, or laggy performance. These signs usually indicate the presence of a rootkit. Other signs that show your system has been infected by a rootkit are unauthorized changes in Windows settings, unusual network activity, or changes in system settings.
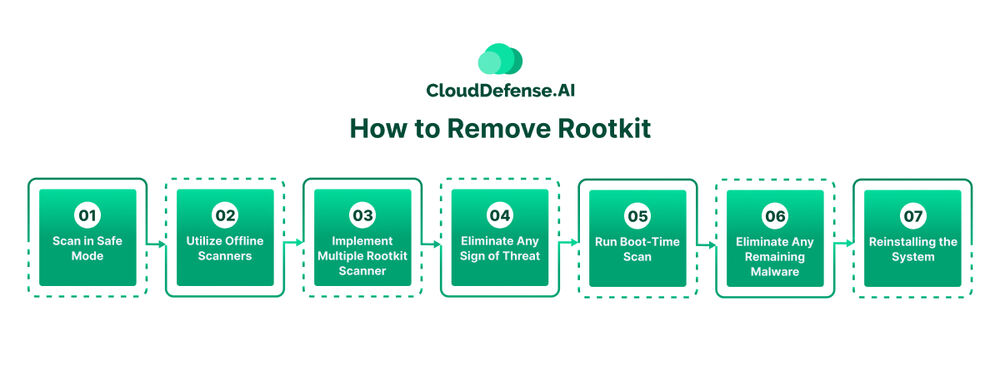
How to Remove Rootkit
Rootkit removal is not an easy task as it embeds into kernels, firmware, framework, and storage devices. Many modern antiviruses and anti-malware tools still face challenges to achieve them.
Here are some effective rootkit removal steps you can utilize before initiating the remediation process:
Scan in Safe Mode
Many rootkits prevent users from using or installing antivirus or anti-rootkit solutions when they are using the system. However, you can install or run the security solutions in Safe Mode by booting up the system.
Starting the system in Safe Mode prevents the rootkits from booting during startup, and this allows the security solution to remove them. However, the process to start Safe Mode may be different for different OS.
Utilize Offline Scanners
Some of the rootkit types are difficult to detect, and many modern antiviruses fail to identify their location. However, utilizing offline scanners can help you overcome the issue as they are executed through a bootable USB or DVD. This type of scanner scans every component of your system and uncovers the presence of a rootkit.
Implement Multiple Rootkit Scanner
There are different rootkit scanners in the industry with different capabilities. It would be best to use a combination of scanners that will help you detect various types of rootkits that can be removed by other security solutions.
Eliminate Any Sign of Threat
When your security solution finds any threat related to the rootkit, you should follow all the instructions to remove it from the system. If you get frequent alerts regarding a particular infected file or process, then you should make an effort to remove or quarantine it as it often indicates rootkit presence.
Run Boot-Time Scan
Many modern antivirus and anti-malware scanners offer the option of boot time scanning and this can help you detect rootkits before they are active. Once detected, the security solution can quarantine them and wipe them from the infected component.
Eliminate Any Remaining Malware
When you have removed any particular rootkit, it doesn’t guarantee that your system is completely free from rootkit attacks. There are many other malware injected by the rootkit in the system and they will stay active until removed. You should use effective security solutions to quarantine or freeze remaining malware in the system and help in the complete removal of malicious programs.
Reinstalling the System
Bootloader rootkits are difficult to remove even with an anti-rootkit solution. The effective way to remove it is by reinstalling the OS, which will eliminate the rootkit attack. However, you might also need to use a clean storage device if there is a presence of other malware.
Examples of Rootkit Attacks
Over the years, rootkits have grown into a severe cybersecurity threat and it is widely used by cybercriminals to infect a particular system. Here, we will take a look at the prominent rootkit attacks that enterprises have come across:
Stuxnet
Stuxnet is considered to be one of the dangerous rootkits in the cybersecurity landscape which came into the limelight in 2010. It was believed that the US and Israel jointly created this rootkit to sabotage the nuclear program of Iran.
Rustock
It is a powerful rootkit that was developed to infect the Master Boot Record or MBR of hard disks in a Windows Operating system. MBR stores the data that is required to boot the Windows system, and Ruckstock sneakily embeds itself in that area on the hard drive to hide itself from security solutions and the OS.
Flame
Discovered in 2012, Flame is a notorious rootkit that was utilized to carry out cyberattacks or cyber espionage in the Middle East. This rootkit focused on taking control of the entire infected system to track network traffic, take screenshots, log keystrokes, and record communication from the device. It utilized around 80 servers spread across three continents to control all the infected systems.
Necurs
Appearing first in 2012, Necurs is a rootkit that is estimated to have infected around 83,000 devices. According to experts, it was supposedly created by top cybercriminals in Eastern Europe, and it emerged as a powerful malware due to its complexity and ability to evolve. It is basically a botnet controller that spreads the malware through email attachments or drive-by downloads.
Zeus
Also known as Zbot rootkit, Zeus is a deadly malware program that has been designed to extract banking details like bank details, credit card numbers, and login details from the target system. The attackers leverage the traditional way of drive-by downloads or email attachments to infect the system, and once the malware is executed, it starts stealing sensitive financial data.
Duqu
Duqu is a set of malware that was developed by Unit 8200 in September 2011 and it is supposedly linked with Stuxnet worm. Duqu became popular by exploiting the zero-day flaw in Microsoft Windows and the threat was detected by CrSyS Lab and Budapest University of Technology.
ZeroAccess
Zero Access which is often called Sirefef is a kernel-mode rootkit that mainly targets Windows systems by spreading malware through infected websites or drive-by downloads. It doesn’t modify the infected system’s operation and install malware on it so that hackers can use it as a botnet to launch cyberattacks. According to experts, it is estimated to have infected more than 2 million machines.
Mebroot
Mebroot is a popular rootkit that infects the MBR of Windows systems and makes modifications so that it can boot before the operating system. Like every other rootkit, it is also distributed through malicious websites, attachments, and drive-by downloads.
Machiavelli
Machiavelli was discovered in 2009, and it was the first of its kind malware that primarily targeted the Mac OS X operating system. The main focus of this rootkit was to generate hidden kernel threats and system calls to trigger an action from the core of the system.
Scranos
In 2019, Scranos became a popular rootkit because its main focus was to steal keys and install subtleties from gadgets. Many cybercriminals started using it as it enabled them to turn specific gadgets into click farms, which helped the attackers to generate video income and YouTube endorsers.
Final Thoughts
Having the support of a robust security platform, good cyber hygiene, and a couple of security practices can help you protect your enterprises from all types of rootkits. This article presents you with all the required information you need to protect your organization from rootkit.
Not only have we described ways to detect and remove rootkits, but also what the symptoms and effects of a rootkit attack are. We are hopeful that this article will guide you to build a hardened security strategy that will keep all types of malware attacks at bay.







