What is Application Vulnerability?
An application vulnerability is basically a flaw or weakness in a software program that can be exploited by attackers. It’s like a crack in the armor of your app. These vulnerabilities come in all shapes and sizes, but they all have one thing in common – they’re security risks.
For example, a bug in the code could allow unauthorized users to access restricted areas of an application, or a design flaw might make it easy for an attacker to bypass security features. Even something as simple as outdated software can be a vulnerability if it hasn’t been patched with the latest security updates.
In tech terms, these vulnerabilities might be:
- Bugs in the code
- Design flaws
- Configuration errors
- Weak authentication systems
The tricky part is that these vulnerabilities aren’t always obvious. They can hide in complex code or in seemingly harmless features. That’s why companies should have necessary application security solutions dedicated to finding and fixing these issues before the cyber criminals do.
Why App Security Can’t Be an Afterthought
Alright, let’s talk about why application security is such a big deal these days.
First off, it’s not something you can just include on at the end. It’s gotta be baked into every step of making and updating your app. We’re talking about being on your toes all the time, constantly checking for threats. And let’s be real, doing this manually would be a nightmare. That’s where automation comes in clutch.
Now, if you’re in the dev world, you’ve probably heard of DevOps. These folks are all about using cool tools and tricks to keep apps secure at every stage—from building to testing to releasing.
Here’s the thing: more and more companies are jumping on the CI/CD bandwagon (that’s Continuous Integration/Continuous Delivery for the newbies). It’s great for pumping out updates fast, but it also means we need to step up our security game.
Real-World Impact
Studies show that as more people move to cloud-native setups, it’s changing how we need to defend against security weak spots. The biggest culprits? Stuff that’s set up wrong and old vulnerabilities that haven’t been patched. And the best part is that most of this blunder is totally avoidable if you’ve got a solid security strategy.
Here’s where it gets cool: we’ve got these awesome security tools that can hunt down known vulnerabilities and sort out the results. This means developers don’t have to spend hours manually combing through code. These tools are smart—they can spot trends, help devs catch errors while they’re building stuff, and keep an eye on things when updates go live.
Therefore, with new ways for hackers to break in popping up all the time, and the crazy amount of time it takes to check everything by hand, these automated security tools are lifesavers. They’re faster, smarter, and let’s face it, way less boring than doing it all manually.
What is CVE?
So, we’ve been talking about application vulnerabilities, right? Well, these Common Vulnerability Exploits (CVEs) are like the greatest hits album of those weak spots. They’re the ones that hackers love to target because they’re, well, common.
For example, you might hear something like “CVE-2021-44228” being thrown around. That’s the infamous Log4Shell vulnerability that had everyone freaking out in late 2021. Having these standardized IDs helps everyone stay on the same page when talking about security risks.
Basically, CVE stands for Common Vulnerabilities and Exposures. It is a comprehensive, constantly updated list of known security flaws, and it’s like a most-wanted list for software bugs. Each vulnerability gets its own unique ID number, making it easier for security pros to track and talk about specific issues.
The OWASP Top 10 Security Risks
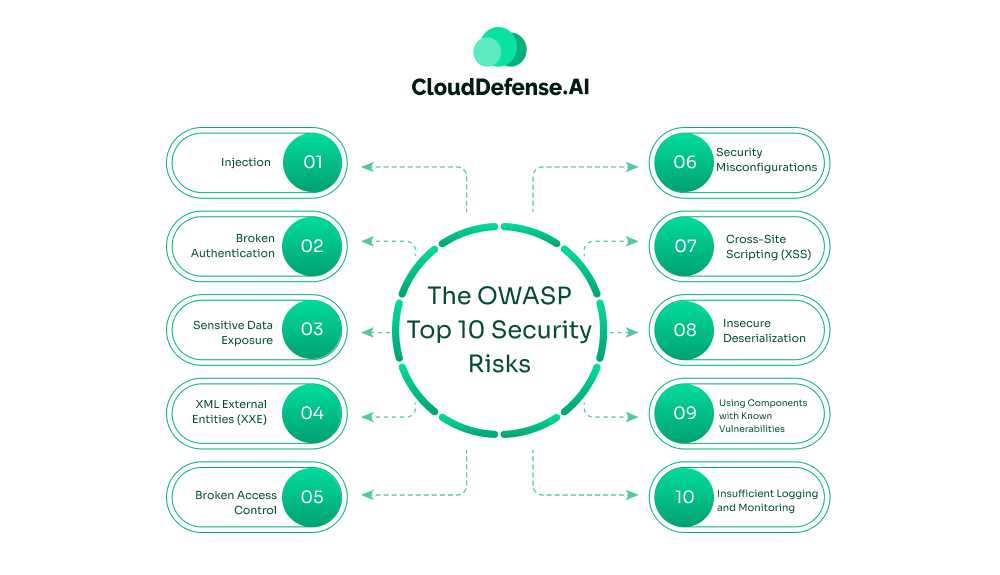
The Open Web Application Security Project (OWASP) puts out a list of the top 10 most critical security risks to web applications. It’s like the Billboard Hot 100, but for security flaws. The latest version dropped in 2021, and it’s a must-read for anyone in the dev game.
Here’s a more detailed look at common application vulnerability exploits, referring to the OWASP Top 10:
1. Injection
Injection flaws occurs when an attacker sends data to an application via forms or URLs, for instance, and the application subsequently executes these data as some sort of a command or query. The most common form is SQL Injection, whereby malicious SQL statements are injected into a query, allowing an attacker unauthorized access or modifications to the database.
Other varieties include OS Command Injection and NoSQL Injection. Web application security prevents injection attacks by validation and sanitization of input, using parameterized queries, and proper error handling.
2. Broken Authentication
Broken authentication vulnerabilities arise when an application fails to manage user sessions or login processes correctly. This might be in the form of using weak password policies, not implementing multi-factor authentication, or poorly managing sessions.
These weaknesses will give rise to password stealing by hackers, brute-forced passwords, hijacking of sessions, or impersonation of legitimate users. To minimize these factors, proper authentication techniques must be implemented with secure password storage and proper session management.
3. Sensitive Data Exposure:
Sensitive Data Exposure involves not properly protecting sensitive data, which may lead to exposure to unauthorized parties. Such exposure could include unencrypted data, inadequate data masking, or poor handling of sensitive information.
In fact, unencrypted data is susceptible to interception and exposure by an attacker, hence becoming one of the serious problems that can lead to identity theft, financial fraud, or data breaches. To properly protect sensitive data, encryption should be applied both at rest and in transit, with data masking if necessary, according to good practices in data protection.
4. XML External Entities (XXE)
XXE vulnerabilities occur when an XML parser processes the external entity references. Poorly configured XML parsers can be tricked into sending sensitive data to unauthorized entities or into revealing internal files.
This could lead to information disclosure, internal network scanning, and DoS attacks. In order to defend against XXE attacks, one has to disable external entity processing in the XML parsers and also validate and sanitize XML inputs.
5. Broken Access Control
Broken access control occurs when an application does not adequately restrict what users can perform and what they are allowed to access. This may allow unauthorized users to get into admin features, sensitive information, or other restricted areas.
An attacker can leverage such issues in certain circumstances to perform actions beyond his privileges. To reduce these risks, it is important to use role-based access control (RBAC), apply least privilege, and regularly check access permissions.
6. Security Misconfigurations
Security misconfiguration happens when apps or servers are not configured correctly with proper security measures. This can include using default settings, running unnecessary services, or exposing administrative interfaces to the public.
Misconfigurations are often a main reason for breaches and can be used by attackers to get into systems without permission or cause problems in services. It’s important to check settings often, update when needed, apply security patches and follow safe setup rules to reduce these risks.
7. Cross-Site Scripting (XSS)
XSS attacks happen when malicious scripts are put into web pages that other people see. These harmful scripts can steal cookies, manage sessions, or redirect users to unsafe websites. There are three main types:
- Stored XSS, where the script is saved on the server;
- Reflected XSS, where the script reflects back from the server through a URL;
- DOM-based XSS, which happens due to issues in client-side code.
To prevent these attacks, you should clean and verify user inputs thoroughly, apply Content Security Policy (CSP), and properly escape outputs.
8. Insecure Deserialization
This problem comes when an application takes untrusted data and deserializes it. When this happens, it can cause serious issues like remote code execution, injection attacks, or increasing user privileges without permission.
Attackers use these weaknesses by making harmful serialized objects that the application works with. To reduce this danger, do not deserialize data you cannot trust, choose safe libraries to work with, and put in place checks for integrity.
9. Using Components with Known Vulnerabilities
Applications often rely on third-party libraries and frameworks. If these components have known vulnerabilities and are not updated, they can become a weak link. Attackers can exploit these known issues to compromise the application. Keep track of the components you use, monitor for security updates, and apply patches or updates promptly.
10. Insufficient Logging and Monitoring
Many applications use libraries and frameworks made by other companies or developers. If these parts have known security problems and are not kept up-to-date, they can become a weak spot in the application’s safety.
This can allow attackers to break into the application. Therefore, it is important to keep a list of all components you use, watch for security updates, and quickly apply patches or updates when they become available.
Best Security Tools for Fixing Application Vulnerabilities
Even with the best coding practices, vulnerabilities can still sneak into your application. That’s why security tools are crucial for identifying and fixing these weak spots before attackers can exploit them. Let’s break down some of the most effective tools you can use to secure your applications:
Static Application Security Testing (SAST)
SAST tools dive deep into your codebase, analyzing the source code, binaries, and libraries without actually executing the program. It’s like giving your code a thorough health check before it even runs. These tools look for vulnerabilities based on predefined rules, identifying where exactly they are.
The great thing about SAST is that it finds problems early in the development process, which makes them easier and cheaper to solve. However, because it analyzes code statically, it might miss issues that only appear when the application is running.
Dynamic Application Security Testing (DAST)
DAST tools take the opposite approach—they test your application while it’s up and running, simulating real-world attacks without needing access to the source code. This type of testing is called black-box testing and it’s good for finding weaknesses that show up while the app is working, like problems with interfaces, how requests are managed, and session handling.
DAST tools are very important to find mistakes that SAST might not see, especially those connected with how the application works when it is running live.
Software Composition Analysis (SCA)
With modern applications now depending a lot on open-source parts, SCA tools become very important for handling risks from third-party sources. These tools check your software’s dependencies to find outdated libraries, issues with license compliance, and known security problems.
SCA tools also help you to follow updates and patches, making sure that no backdoors are left open. They are very important for keeping the complete security of your application’s ecosystem, especially as your codebase becomes bigger and changes over time.
Using these tools in your development process can greatly improve the security of your application. Using SAST, DAST, SCA, and other modern tools together, you can find weak spots at various stages of making the software. This helps to create a strong protection against possible attacks.
Why Choose CloudDefense.AI for Fixing Application Vulnerabilities?
When it comes to securing your applications, CloudDefense.AI stands out as a reliable choice. Here’s why:
Comprehensive Security Coverage: CloudDefense.AI offers an all-in-one solution that combines SAST, DAST, and SCA tools. This means you get complete coverage—detecting vulnerabilities in both your static code and during runtime, as well as managing third-party risks.
User-Friendly Interface: Security doesn’t have to be a headache. CloudDefense.AI makes it straightforward with a user-friendly interface that’s simple to navigate. You can dive into detailed reports, set up scans, and get actionable insights without needing to be a security expert.
Auto Remediation: Fixing vulnerabilities can be a hassle, but CloudDefense.AI simplifies this with auto remediation features. Our platform not only identifies issues but also provides automated fixes, saving you time and reducing the risk of human error.
CI/CD Integration: Why mess up your workflow? CloudDefense.AI fits right into your favorite CI tools—like Jenkins, Azure DevOps, and GitLab. It delivers insights directly within your workflow, so security becomes a seamless part of your development process without any extra hassle.
Infrastructure as Code (IaC) Security: our infrastructure needs just as much protection as your code. CloudDefense.AI checks your Infrastructure as Code (IaC) templates for misconfigurations and security gaps before they go live. A tiny error in the cloud can lead to big problems, but this feature helps you catch them early.
Don’t Wait Until It’s Too Late—Secure Your Applications Now!
Vulnerabilities can strike at any moment, leaving your systems exposed. Don’t risk it. Take action today to protect your business from devastating breaches. Book a demo with CloudDefense.AI and see how our comprehensive security solutions can safeguard your applications and infrastructure.







