What is Security Automation?
Security automation can be defined as the process of automating security processes that includes administrative tasks and the process of identifying, managing, and correcting cyber threats. It involves the use of technology like AI and ML to automate tasks with or without human assistance and helps integrate security tasks, infrastructure, and applications.
Security automation begins its process by identifying the cyber threats, carrying out triage, sorting them according to their impact severity, and finally responding to them. This is the reason it has become a necessary component for modern SOC teams and helps them streamline most of their daily tasks. It not only helps in enhancing efficiency and speed but also enables the team to focus on more complex tasks or alerts.
Moreover, security automation also helps enhance overall response and lower human risks while managing threats. This solution is highly effective in enriching the organization’s threat intelligence and correlating and grouping alerts to boost threat investigation.
Modern security automation solutions widely use AI and ML to perform most tasks in seconds and remediate threats more efficiently. Moreover, the use of AI and ML also helps them harness a lot of data and accurately detect malicious patterns. From digital systems, data, and networks to applications, this solution has become necessary to protect them from an increasing number of cyber threats.
Benefits of Security Automation
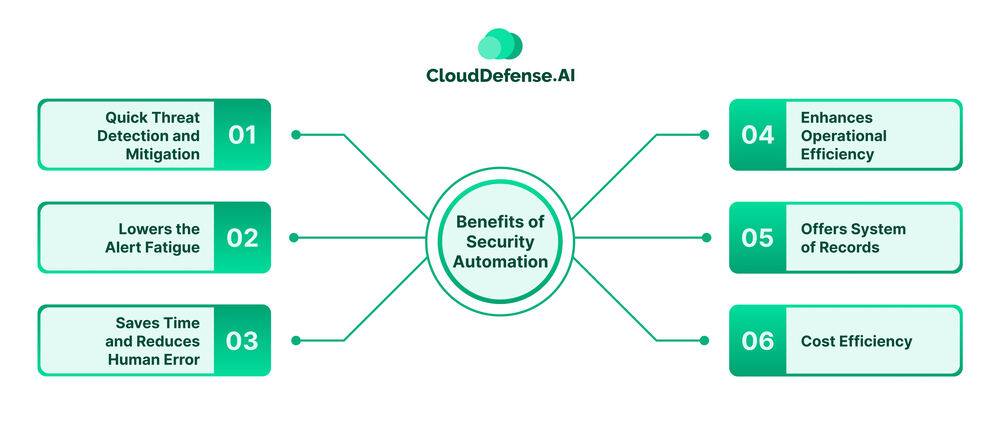
A Splunk report in 2022 stated that it takes around 14 hours to remediate a security incident on a business app, as a result businesses faced huge loss and reputation damage. However, security automation brought a revolution in the cybersecurity landscape with its benefits, and these benefits are:
Quick Threat Detection and Mitigation
With integration of security automation, SOC team and other analysts can achieve quick threat detection, investigation and remediation. By leveraging AI and ML, it can process a large number of data and find unusual patterns to mitigate unknown threats.
Most of the alerts are mitigated automatically through predefined responses, and security incidents are analyzed automatically to patch any security gaps. Thus helping reduce reaction time drastically and resolve issues at a speed better than standard processes.
Lowers the Alert Fatigue
Previously alert fatigue has been a big issue for security analysts as it led to oversight of many alerts of critical threats. However the security automation through prioritization, and filtration helps in addressing the alerts and ensure only the critical alerts are escalated. Not only does it reduce alert fatigue but also enhance the threat response accuracy.
Saves Time and Reduces Human Error
Automating repetitive and daily security tasks enables security teams to save a lot of time and concentrate on high-level threats that require human intervention. It also prevents SOC 2 analysts from getting overwhelmed with a huge number of incidents that lead to a lot of human error. Importantly, it provides security teams with deep insight into security incidents which helps them to accurately mitigate issues.
Enhances Operational Efficiency
Security automation is not only about automating manual and repetitive SOC tasks; it is also about assisting the SOC 2 team with security policies and strategies. Security teams often have to face many misconfiguration issues, and on some occasions, they also have to deal with various network policy rule change requests.
Solving the misconfiguration or making changes to policy manually slows down the whole operation. Security automation solves all these issues as it automates the process of policy change and mitigates misconfigurations or siloed data. This eliminates any disruption to security and enhances overall operational efficiency.
Offers System of Records
Security automation offers detailed reports, intuitive dashboards, and dynamic case management, and this allows various security to communicate while dealing with alerts. It encourages a collaborative approach as everyone can get the same insight and enables them to quickly respond to incidents.
Cost Efficiency
Manually solving security alerts is cost intensive, and it usually increases the overall operational cost of solving escalated security incidents on a daily basis. However integration of security automation drastically reduces operation cost as the SOC team won’t have to handle alerts manually. Moreover it helps in reducing security breaches that also saves the organization from remediation cost and potential fines.
What are the Signs That an Organization Needs Security Automation?
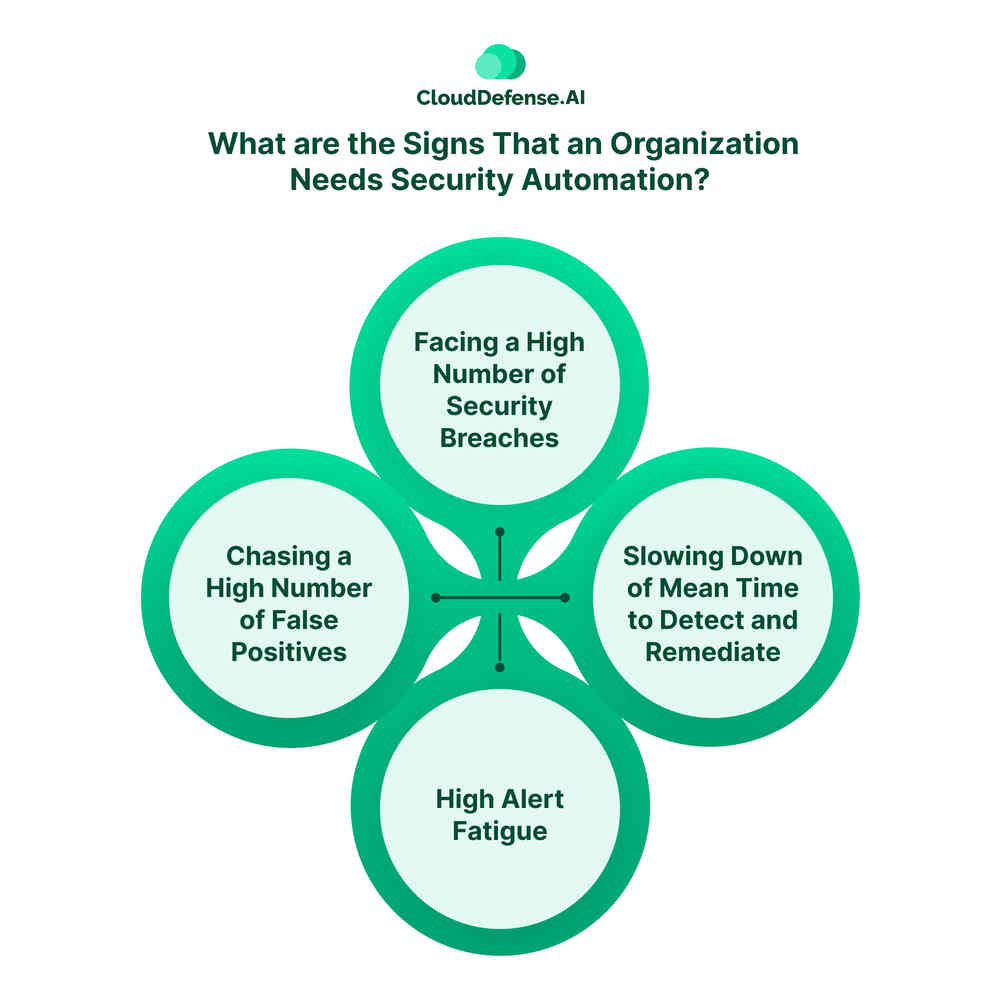
Besides dealing with security alerts on a daily basis, an organization might require security automation in various circumstances. Here are some common scenarios that indicate an organization needs to integrate cybersecurity with automation:
Facing a High Number of Security Breaches
A research conducted by Splunk stated that the number of security breaches on organizations is increasing with time and most security teams aren’t able cope with increasing cyberattacks. Even some of the incidents can be solved easily but not all of them. Organization facing a high number of security breaches should definitely opt for security automation as it will reduce operation cost and help in coping with security alerts.
Slowing Down of Mean Time to Detect and Remediate
Every organization needs to maintain a high incident response time as it will help them to cope with the increased number of issues. However, if the mean time to detect and remediate is slowing, then it is a sign that your organization’s security is falling behind in keeping up with the challenges. Having security automation is the only way to remediate the issue.
High Alert Fatigue
When your security team faces high alert fatigue, then they should be assisted with security automation. It will help them to save time and resources while staying ahead of the daily challenges. The need for security automation can be only conveyed by security teams and no one else.
Chasing a High Number of False Positives
A high number of false positives faced by your team also serve as a sign that they need the support of a security automation. Security teams face a high number of daily alerts and only after investigation, can they know whether an alert is false positive.
As a result, it is costing the security team a lot of time and resources in dealing with false positives. However, with the help of security automation, they can automate the investigation process and reduce false positives.
Security Automation Solutions
When you talk about security automation solutions, it serves as a platform that takes a holistic approach to handling security concerns across your IT environment. Basically, it works as a security software that integrates with your security system and automates most of the tasks. From firewalls, directory services, and endpoints to SIEM and ticketing systems, it seamlessly integrates with all the necessary security tools.
This integration helps in setting action plans that can address security incidents across the different attack vectors. Importantly, integrating a security automation solution will help you search and identify files on different endpoints and quarantine a device from the network if suspicious activity is detected.
It also has the ability to delete or quarantine any file if it finds signs of malware infection on any of the devices. With this solution, you also have the capability to find the geolocation of a particular IP address for security investigation. A great thing about this solution is that it can automatically block a URL on a perimeter device if any suspicion arises during the investigation.
Automation vs Orchestration
The terms automation and orchestration in the security domain are often considered the same or used interchangeably due to numerous commonalities. However, they are quite different from each other in different aspects. Security automation is all about automating various security tasks within a security system and streamlining the whole security workflow.
Whereas security orchestration is designed to consolidate all the automated security processes and tools, and ensure they work all together while responding to alerts and addressing concerns. Let’s take a detailed look at the two aspects:
| Aspect | Security Automation | Security Orchestration |
| Primary Aim | Security automation is meant to automate specific security tasks within a system without human intervention. | Security orchestration is designed to manage different automated tasks and ensure all of them work in synchronization. |
| Main Focus | The main focus of security automation is to make security operations effective and efficient while reducing the risk of human error. It is mostly dedicated to streamlining individual repetitive security tasks. | The primary focus of security orchestration is to ensure seamless working of all multiple automated processes between systems and tools. It aims to transform automated processes from end to end. |
| Complexity | It mostly automates repetitive tasks and streamlines different security processes. | It is designed to manage complex security processes and workflows that include different tools, systems, and dependencies. |
| Integration | Security automation integrates specific tasks and processes and doesn’t involve interaction between different tools. However, it can be integrated with a variety of tasks. | Security orchestration integrates and coordinates multiple automated tasks across security systems, platforms, and APIs. |
| Collaboration | Since it focuses on specific automated tasks or processes, it doesn’t promote collaboration among tools. | It facilitates collaboration among tools, functions, and teams through shared security management and workflow visibility. |
| Utilization | It only involves automation to increase efficiency and reduce error. | Security orchestration involves both automated and semi-automated tasks to help a security process or workflow. |
| Human Involvement | Security automation doesn’t require human involvement once the task has been completed. | Security orchestration requires human involvement in the coordination and management of the workflow. |
| Operational Cost | It is relatively low cost, but the overall operation cost depends upon the complexity of the task. | The cost of security orchestration is quite high and it is mainly due to the integration of multiple tools. |
Why Automate Security Processes?
The cyberattacks on organizations are increasing with time, and it is becoming complex for security teams, especially analysts, to handle a large number of alerts on a daily basis. The growing infrastructure and network of the organization also add to the difficulty of managing the security and compliance posture.
In many organizations, the trend of working from home has increased the security complexity as security teams also have to look after the security of the endpoint as many attackers target them. To manage such a complex and vast IT environment can be daunting, and manually controlling all the security aspects won’t be sufficient in modern times.
Having a manual operation will not only slow down the detection and response process and lead to inconsistent policy but also might lead to misconfiguration. Thus, your organization will become exposed, and the system, application, and infrastructure will be completely vulnerable to cyberattack.
That’s not all; an unplanned downtime of an application or any infected endpoint can lead to financial loss, reputational damage, and an overall decrease in efficiency. However, automating security processes can help streamline all daily tasks and increase the overall operational speed. Importantly, it helps organization in coping up with growing infrastructure and prevent most of the security breaches.
What Security Processes Can be Automated?
When it comes to automating security processes, not everything can be automated. There are certain tedious processes that can be automated, which will not only enhance the overall security but also free up time for security analysts. Here are the processes that can be automated:
Threat Hunting
When you automate threat hunting in your security system, it will facilitate quicker threat detection and enable analysts to find threats before they can cause a security breach.
Besides quicker identification, it also speeds up the validation and escalation of threats, enabling organization to stay ahead of modern threats. Manual threat identification in today’s complex IT environment will delay threat hunting function and it will make the security controls vulnerable to attack.
Security Incident Response
Another security process that would benefit from automation is security incident response. Manual detecting and containing security breaches across the tools, application and platform can be time consuming and often leads to error.
However by automating the remediation process, it will help the organization to respond and remediate security incidents quickly. Moreover it will help in streamlining the operation and maintenance of various security tools like SIEM and IDPS that help in detecting and responding to security threats.
Endpoint Protection
Endpoint protection platform serves as an important aspect of modern IT as endpoints are the most vulnerable component of an IT infrastructure. An EPP helps in detecting, investigating and remediating malicious activities at the endpoint device but doing it manually, slows down the whole process. However with automation, EPP tools can be integrated into larger processes and helps in detecting and remediating events in real-time.
Data Enrichment
Investigating security alerts on a daily basis to find the impact of real threats can be time-consuming and daunting for the security team. However, except for performing a thorough investigation, a threat investigation doesn’t always need human involvement.
Integrating the investigation process with automation can enable the machines to perform investigations on behalf of the team and get insight much more efficiently. It will enable security analysts to save time and utilize it to perform deeper investigations.
Security Monitoring
Every security team constantly monitors every facet of their IT environment to get complete on their security posture. However, as the infrastructure and number of devices grow with time, it becomes difficult to maintain optimum visibility through monitoring. Instead, security teams can introduce automation with the monitoring tool and utilize orchestration to sync all the tools to work from a unified command center.
User Permissions
Managing user permission can be overwhelming for security teams as a lot of system logins, modifications, and removal take place on a daily basis. Besides, the security is also tasked with managing the logins of new users and removing the credentials of departed employees.
When the infrastructure grows with the number of endpoints, managing users’ permissions manually can cause many vulnerabilities. Automation can solve the issue as it will automatically provision and deprovision users and investigate any usual activity in specific accounts.
Integrated Corporate Security Architecture
On many occasions, organizations have many singular security solutions that help the security in dealing with specific threats on a specific platform. Each standalone security solution comes with its own requirements and specifications, requiring the security team to operate each of them individually.
The complexity increases as the organization grows with time, and the number of security incidents increases. Maintaining, managing and monitoring such a complex security infrastructure can get difficult for security teams, lowering the ability to address and mitigate potential cyber threats.
To streamline such corporate security architecture, security automation can serve as an ideal solution as it will integrate all the security solutions and enable the security team to manage them from a single dashboard. APIs of the security solution can be utilized to link them together and integrate them into a centralized management system.
Types of Security Automation Tools
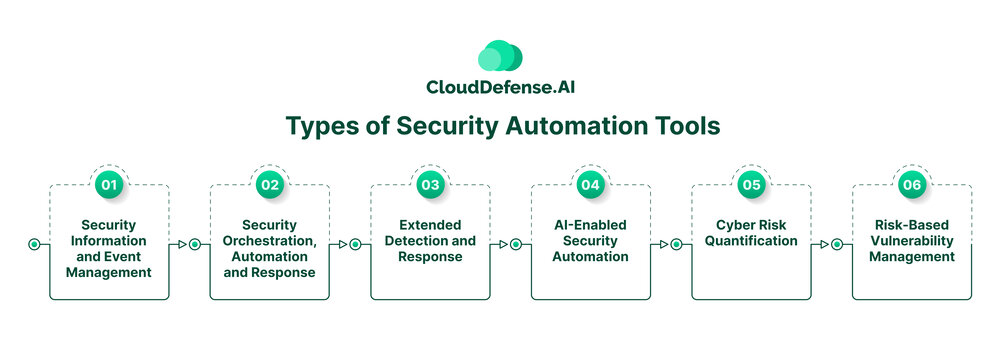
When you look for different types of security automation tools, you will come across many types that cater to the security requirements of different organizations. Here are some primary types of security automation tools used by organizations:
Security Information and Event Management
SIEM solutions are widely used by organizations all over the world as it collects, aggregates and assesses security data from every section of the organization’s IT environment. Through automatically analyzing security data, it provides security teams with insights into potential cyber threats and enables them to quickly respond to the incident. It thoroughly analyzes log data and then correlates event information to identify possible threats.
Security Orchestration, Automation and Response
Also known as SOAR, this tool is based on the capabilities of SIEM for data ingestion. It offers an additional capability of automated response and helps security analysts with threat alerts. When the SIEM tool aggregates and enriches the threat data, it is then used in the SOAR playbook and incident reporting. By collecting all these data, it enables the organization to automatically address security threats with no human intervention.
Extended Detection and Response
XDR serves as the next-generation endpoint detection and response platform that consolidates TDIR, SIEM, SOAR, and other security capabilities into a centrally managed console.
It utilizes threat intelligence and raw data to automatically detect and remediate threats at the endpoint and prevent security events. It also offers the capability of response orchestration and machine-learning based detection, enabling security analysts to proactive address and prevent threats.
AI-Enabled Security Automation
AI enabled security automation is another type that brings a modern approach to SecOps automation. It involves artificial intelligence and low-code automation technology that helps in enhancing the speed and effectiveness of the security processes. This type of tool comes geared with all the necessary features in a single platform that include collaboration tools, dashboards, low-code playbooks, case management and many more.
Cyber Risk Quantification
CRQ or cyber risk quantification tool automates the complete process of collecting, aggregating and reporting of threat data in the form of monetary terms. Usually these threat data are fed to senior executives and CISOs of an organization who look after the financial aspect for managing cyber risks.
Risk-Based Vulnerability Management
A risk-based vulnerability management tool is another type of security automation that automatically collects vulnerability data from all the security tools. It integrates contextual business insight with the vulnerability to prioritize vulnerabilities in the infrastructure and calculate the possible impact.
Security Automation Best Practices
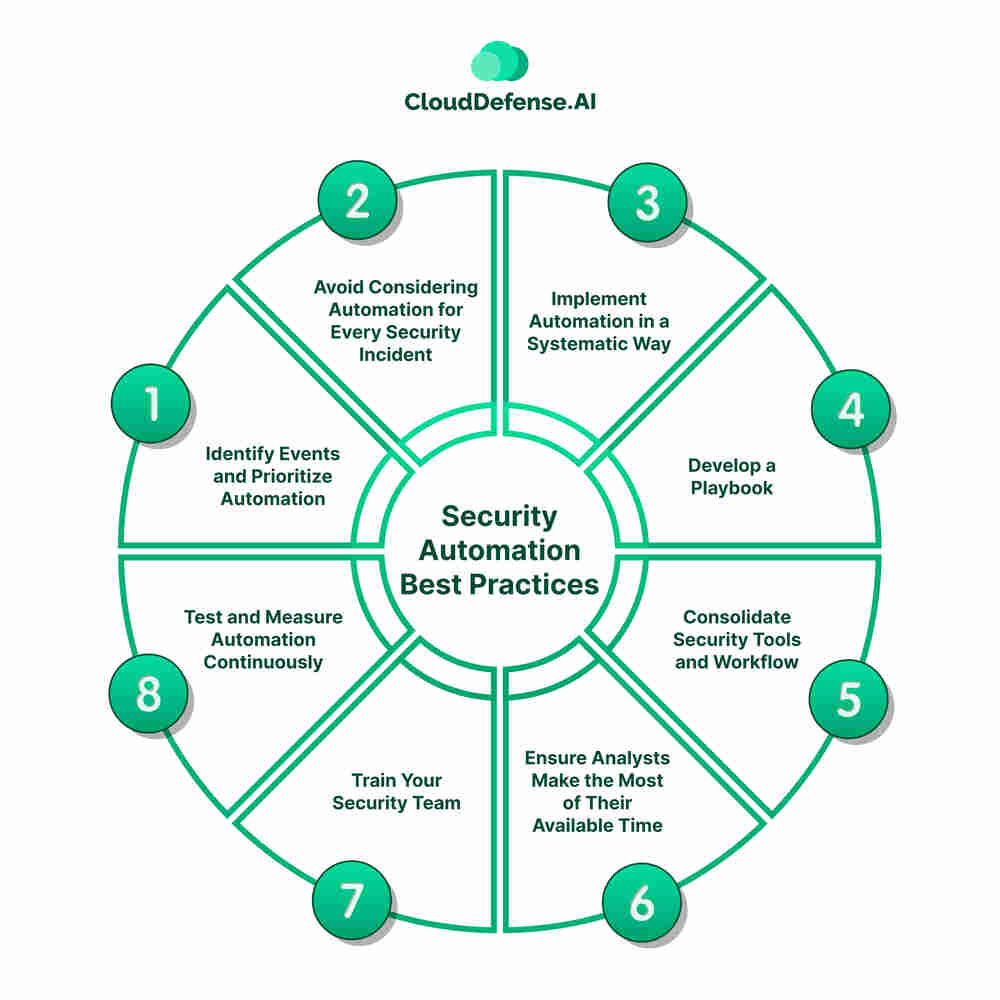
To get the best out of security automation and generate value, you need to follow certain best practices, and they are:
Identify Events and Prioritize Automation
For effective security automation, you need to identify all the repetitive security events that take a huge amount of time to investigate. Depending upon the security events, you need to define the use cases and define how security automation can be implemented. You should involve every employee who is responsible for the cybersecurity of the organization as it will help you establish priorities for different events and set security workflow automation.
Avoid Considering Automation for Every Security Incident
You shouldn’t consider complete automation for every security incident, as certain complex security incidents require the decision and expertise of security analysts. Automation should be implemented with specific tasks that follow a similar pattern.
Implement Automation in a Systematic Way
It is not possible to implement automation for every security process at once, and it is best to avoid automating everything in the beginning. You should automate tasks in a systematic way so that you get the most out of them and understand their effectiveness.
Monitoring and evaluating the effectiveness of automation in the first will help you make necessary adjustments in the following case. The success of automating specific processes will help you to prove your action on other processes.
Develop a Playbook
You should log every mitigation process you undertake to address various security incidents and build a complete workflow before you automate the security process. You should implement all the knowledge while automating the security response to make sure it properly follows all the steps that you take while mitigating such issues manually.
Consolidate Security Tools and Workflow
When you implement security automation across your multi-cloud environment, you should also opt for security orchestration. Not only will it help you coordinate complex security workflow across your IT environment from a single console, but it will also help you reduce response time and boost overall efficiency.
Ensure Analysts Make the Most of Their Available Time
Automation of the security process will free up the time of security analysts, and you need to ensure that they utilize their time to do more productive work. You should devise a plan on how they can utilize the time to spend on critical tasks and benefit the organization. Moreover, security analysts should also utilize the time to develop a model that will facilitate continuous improvement of the automation logic.
Train Your Security Team
When you introduce automation to your organization’s security processes, you need to first familiarize and train your security team. Your team will be responsible for building a solid workflow and improving the automation logic, so it is important for them to understand the automation process.
Moreover, your security team must be aware of the limitations and capabilities of automation solutions so that they can step in when it requires human intervention.
Test and Measure Automation Continuously
While implementing security automation for various processes, you should continuously test and measure the automation workflow. All the automation security processes should be continuously monitored to make sure they meet the specific requirement and achieve the objective of optimizing the process and system.
Final Words
Security automation has brought a revolution in the security domain and has enabled every organization to stay ahead of modern cyberattacks. It has enabled security analysts and teams to go past the time-consuming response process and achieve high efficiency and superior response time. Security automation plays a major role in organizations filling various gaps and coping with the rapidly growing cyberattacks.







