What is Lateral Movement?
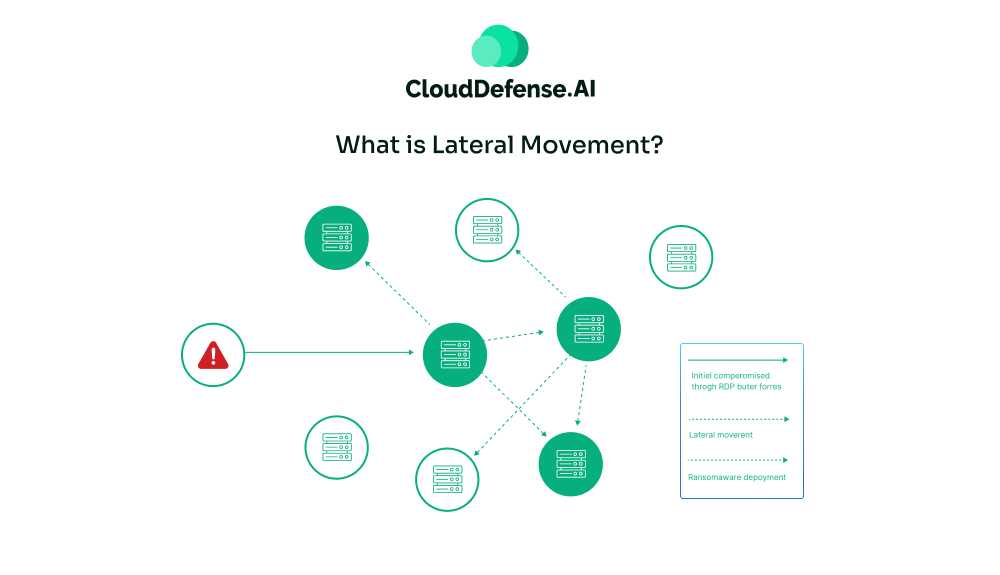
So, you know how cybercrime is a big problem these days? Well, there’s this thing called lateral movement that’s really got security experts worried. It’s not exactly new, but it’s becoming a bigger deal. Also, a recent study found that it shows up in about a quarter of all cyberattacks. That’s pretty wild.
Let me break it down for you. Lateral movement is basically what hackers do after they’ve gotten into a network. They don’t just sit there, twiddling their thumbs. Instead, they start exploring, looking for ways to spread out and infect more of the network. It’s kind of like if someone broke into your house through the bathroom window, then started trying to open every other door in the place.
Here’s an example: Say a hacker manages to get some malware onto an employee’s computer. That’s just the start. From there, they’ll try to jump to other computers, maybe hit some servers, and keep going until they find what they’re really after. The scary part? They’re trying to do all this without anyone noticing.
The real kicker is that even if someone spots the initial infection, the attacker might already be all over the network. It’s like playing whack-a-mole, but with hackers. You might catch one, but the others are still out there, causing trouble.
Now, you might think this is all automated, but that’s not always the case. Often, there are actual people behind these attacks, directing the whole thing. This hands-on approach lets them adapt on the fly, changing their tactics based on the specific network they’re in and how the security team responds.
Common Stages of Lateral Movement

Stage 1: Reconnaissance
This is where the hacker puts on their detective hat. They’re poking around your network, trying to figure out how everything’s set up. They’re looking at stuff like:
- What do you name your computers and servers
- How your network is organized
- Which ports are open on your firewalls
- Any weak spots they can exploit
It’s like they’re creating a map of your network in their head. The more they understand, the better they can plan their next move.
Stage 2: Infiltration
Now the hacker’s ready to make their move. Remember those phishing emails you’re always warning people about? This is where they come into play. The hacker might have tricked someone into giving up their password, or maybe they used some other sneaky social engineering trick.
With those login details in hand, they start digging deeper. They might use tools to grab even more passwords or find ways to get admin privileges. It’s like they’re picking locks and finding secret passages throughout your network.
Stage 3: Access
This is where things get really dicey. The hacker’s found their way to their target – maybe it’s a specific computer, or a database with sensitive info. Now they can do some real damage. They might:
- Upload malware
- Start stealing data
- Mess with your systems
- Or do any number of other nasty things
It’s like they’ve finally reached the safe and are ready to crack it open. The tricky part is that by the time you realize what’s happening, they might already be at stage 3. That’s why it’s so important to have good security measures in place to catch these folks early on.
Types of Attacks Using Lateral Movement
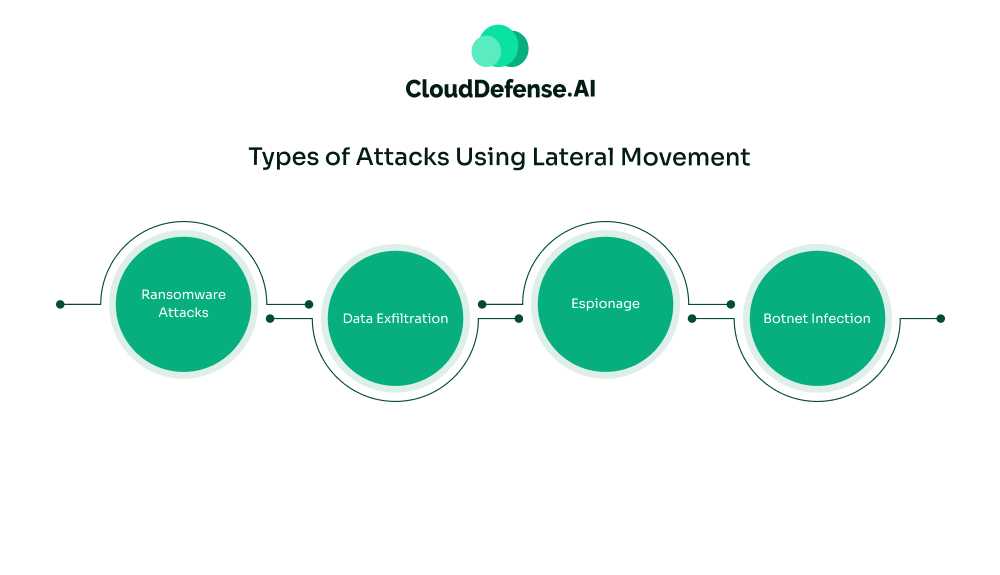
Alright, let’s break down the types of attacks that use lateral movement. It’s pretty interesting stuff, and it shows just how versatile this tactic is for different kinds of cybercriminals. Here’s the rundown:
1. Ransomware Attacks
These guys are after one thing: locking up as many of your devices as they can. Why? Because the more stuff they encrypt, the more likely you are to pay up. They’re especially keen on hitting your internal servers. Those servers usually have all the important data you need to keep your business running. So when the ransomware kicks in, it really puts the squeeze on you. It’s a nasty tactic, but it’s effective.
2. Data Exfiltration
This is all about stealing your data. The attackers might be after different things:
- Maybe they want your company’s secret sauce – you know, intellectual property and all that.
- Or they could be hunting for personal data to sell for identity theft.
- Sometimes they’ll grab the data and then threaten to release it unless you pay up. That’s what we call doxware.
The thing is, the data they want isn’t usually just sitting at the entry point. So they need to move around your network to find it.
3. Espionage
Now this one’s a bit different. It could be other countries, organized crime, or even your business rivals. They’re not always after a quick payday. Instead, they want to stick around and spy on what you’re doing. The key here is staying hidden. Unlike ransomware attackers who eventually want you to know they’re there, these guys want to stay in the shadows. They’ll use lateral movement to spread out and hide, making it harder for you to kick them out completely.
4. Botnet Infection
This is about turning your devices into their personal army. Attackers use lateral movement to infect as many of your devices as possible and add them to their botnet. These botnets can be used for all sorts of nasty stuff, but they’re especially popular for DDoS attacks. The more devices in the botnet, the more powerful it is.
The common thread here is that lateral movement lets attackers do more damage, get more valuable stuff, or hide better in your network. It’s a versatile tool in their kit, which is why it’s used in so many different types of attacks.
Understanding these different attack types helps you see why lateral movement is such a big deal in cybersecurity. It’s not just about keeping attackers out – it’s about limiting their options if they do get in. That’s why all those prevention and mitigation strategies we talked about earlier are so important.
Lateral Movement Techniques
Lateral movement isn’t just one thing. It’s a bunch of different techniques that attackers use to spread through a network. Here are some common ones:
- Pass the Hash (PtH): Instead of needing the actual password, attackers use the encrypted version of the password (the hash) to get into accounts. It’s like using a key copy without having the original.
- Pass the Ticket (PtT): This one’s specific to Windows. Attackers steal special “tickets” that Windows uses for login and use those to get around without needing passwords.
- Exploiting Remote Services: Once they’re inside, attackers look for weak spots in services that connect different parts of your network. They use these to hop from one system to another.
- Internal Spear Phishing: If an attacker has control of someone’s email, they can send fake messages to other people in the company. Since the emails look like they’re from a coworker, people are more likely to fall for them.
- SSH Hijacking: This one’s for Mac and Linux systems. Attackers can take over secure connections (SSH) between computers and use them to sneak into other parts of the network.
- Windows Admin Shares: Most Windows computers have something called “admin shares” turned on by default. If attackers get admin rights, they can use these to quickly spread to other computers.
How to Prevent and Mitigate Lateral Movement Attacks
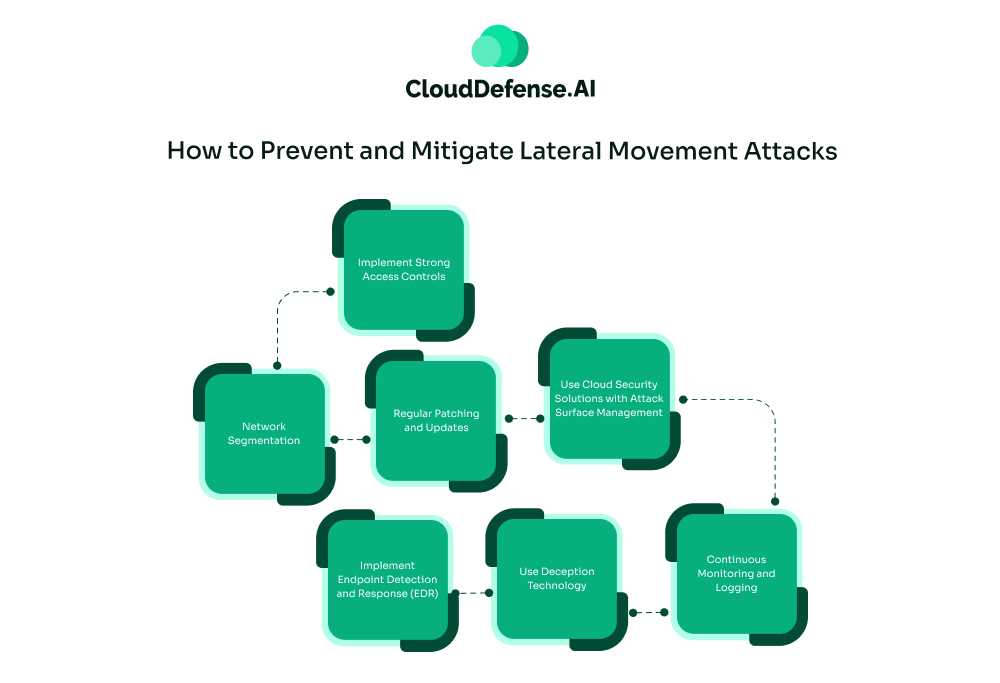
1. Implement Strong Access Controls
This is a big one. You need to be strict about who can access what in your network. Only give people the bare minimum access they need to do their jobs. Use multi-factor authentication everywhere you can—yeah, it’s a bit of a hassle, but it really works. Don’t forget to regularly review and update these access rights, especially when people change roles or leave the company. The goal is to give attackers as few entry points as possible.
2. Network Segmentation
Break your network into smaller, isolated segments. This way, if one part gets compromised, the damage is contained. Use firewalls and access controls between these segments. Make sure critical systems and sensitive data are in their own highly secured segments. This slows down attackers and makes it easier to spot unusual traffic between segments.
3. Regular Patching and Updates
Keep all your systems, applications, and devices up to date with the latest security patches. Attackers often exploit known vulnerabilities that have already been fixed in newer versions. Set up a regular schedule for updates and stick to it. Don’t forget about IoT devices and other non-standard equipment on your network.
4. Use Cloud Security Solutions with Attack Surface Management
This is a big one. Cloud security solutions with attack surface management give you a complete view of your entire network, including cloud assets. They continuously scan for vulnerabilities, misconfigurations, and exposed assets. These tools can alert you to potential entry points before attackers find them. They also help you understand your network better, making it easier to spot unusual activity that could indicate lateral movement.
5. Implement Endpoint Detection and Response (EDR)
EDR tools monitor endpoint devices (like computers and smartphones) for suspicious activity. They can detect and respond to threats in real-time. This is crucial for stopping lateral movement, as endpoints are often the first targets. Good EDR solutions can spot the tactics attackers use to move laterally, like credential dumping or remote code execution.
6. Use Deception Technology
This is pretty cool. Set up fake assets on your network – things like fake servers, fake accounts, or fake data. When an attacker tries to access these, you know something’s up. It’s like a tripwire for your network. This can help you detect lateral movement early, before the attacker reaches any real, valuable assets. Plus, you can learn a lot about the attacker’s methods by watching what they do with these fake resources.
7. Continuous Monitoring and Logging
You need to keep a close eye on what’s happening in your network all the time. Set up robust logging for all systems and network devices. Regularly review these logs for any signs of unusual activity. Use Security Information and Event Management (SIEM) tools to help correlate and analyze log data from different sources. This can help you spot patterns that might indicate lateral movement, like multiple failed login attempts or unusual data transfers between systems.
Final Words
Lateral movement attacks are getting more sophisticated every day, and they’re hitting businesses hard. You can’t afford to be complacent. Your network’s security isn’t something to mess around with.
But here’s the thing—you don’t have to face this alone. There are tools out there like CloudDefense.AI that can give you a fighting chance. Our cloud security solution comes with attack surface management and auto-remediation. That means it’s not just spotting threats; it’s actually fixing them.
Don’t wait until it’s too late. Your company’s data, reputation, and bottom line are all at risk. Take action now. Book a demo with Clouddefense AI. See for yourself how it can protect your network. In this digital age, you’re either secure or you’re a target. Which one do you want to be?







