What is an Advanced Persistent Threat (APT) Attack?
An Advanced Persistent Threat (APT) attack is a stealthy and ongoing cyberattack targeting a specific organization. Unlike a quick hack that might deploy ransomware or cause a denial-of-service attack, APTs are designed to infiltrate a network, remain undetected for a long time, and steal sensitive data.
What makes it APT?
There are three key things that define an APT attack:
- Advanced: These attacks leverage sophisticated techniques to bypass security measures. Attackers exploit software vulnerabilities, develop custom malware, and employ social engineering tactics to gain a foothold.
- Persistent: The attacker’s goal is to establish a long-term presence within the network. This allows them to gather information, move laterally to different systems, and exfiltrate data over time.
- Threat: Their goal is to steal valuable data, like intellectual property, financial records, or personal information. They might also want to disrupt operations or cause damage.
Who carries out APT attacks?
These attacks are often carried out by well-funded groups, including:
- Cybercriminal organizations: They’re in it for the money and might sell stolen data on the black market.
- Hacktivist groups: They attack for political or ideological reasons.
- Nation-states: They might use APTs for espionage or cyberwarfare.
3 Stages of an APT Attack
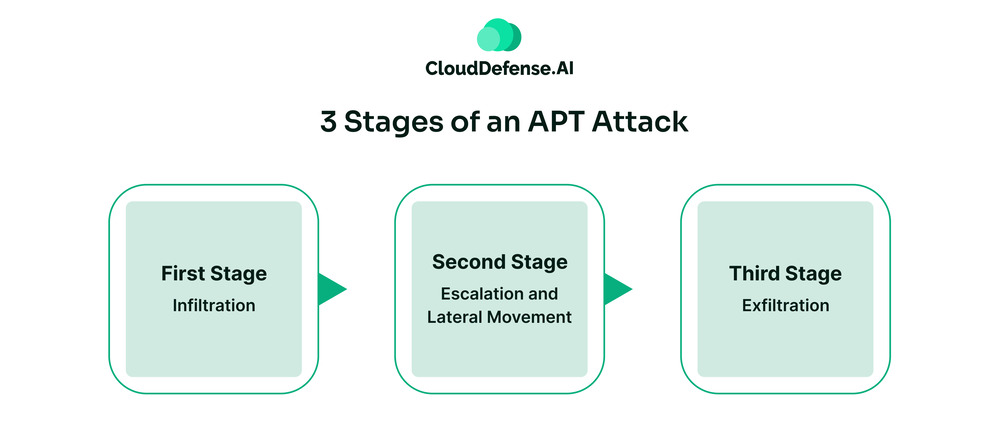
An APT attack unfolds in three main stages, each crucial for the attacker’s success:
First Stage: Infiltration
The first stage is recon. This is the initial phase where the attacker establishes a foothold within the target network. Social engineering tactics are a favorite tool here. Phishing emails designed to trick employees into clicking malicious links or opening infected attachments are common. Spear phishing emails, which impersonate legitimate sources and target specific individuals, are particularly dangerous in this stage. In some cases, attackers might exploit software vulnerabilities or even physical security weaknesses to gain initial access.
Second Stage: Escalation and Lateral Movement
Once they find a way in, the attacker doesn’t settle for just one compromised machine. This phase focuses on expanding their control within the network. They might install malware that grants them persistence within the system and establish backdoors for remote access. With a foothold, they can then move laterally across the network, hopping from one machine to another, often exploiting weak credentials or compromising accounts with low privileges to access more valuable systems and data.
Third Stage: Exfiltration
After establishing a presence and potentially gathering valuable information about the network, the attacker reaches the final stage – stealing the data they came for. This exfiltration can happen in various ways. Attackers might transfer data in small chunks over time to avoid detection or use covert channels specifically designed for this purpose. The stolen data could be intellectual property, financial records, or any other sensitive information the attacker deems valuable.
The whole process could drag on for months or even years in some cases. It’s like having a mole buried deep undercover, waiting to strike. These APTs are insanely patient and determined – that’s what makes them such nightmares to deal with.
Characteristics of an APT Attack
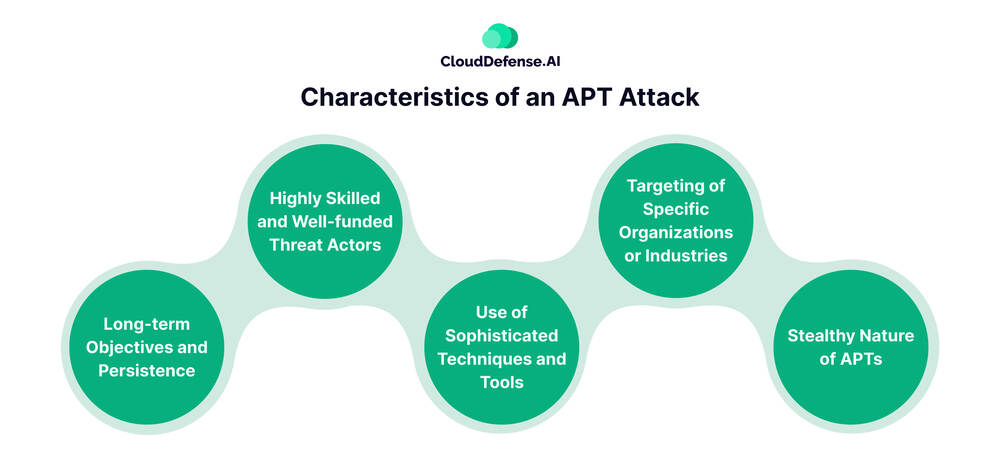
Advanced Persistent Threats (APTs) distinguish themselves from other cyberattacks through several key characteristics:
Long-term Objectives and Persistence: These threats are not brief encounters, but rather enduring campaigns. APT actors patiently pursue their objectives over extended periods, potentially spanning months or years. Their persistence allows them to methodically gather intelligence, laterally infiltrate systems, and carefully exfiltrate data while minimizing the risk of detection.
Highly Skilled and Well-funded Threat Actors: APT attacks are often carried out by well-resourced groups with advanced technical expertise. These actors can be state-sponsored hackers, cybercriminal organizations, or even hacktivist groups. Their significant resources allow them to develop sophisticated tools, exploit zero-day vulnerabilities (previously unknown flaws in software), and continuously adapt their tactics to bypass security defenses.
Use of Sophisticated Techniques and Tools: APT groups do not rely on simplistic exploits. Instead, they leverage a diverse array of sophisticated techniques, including social engineering, custom malware, zero-day exploits, and living-off-the-land attacks that abuse legitimate software. They continuously develop novel tools and identify new vulnerabilities to gain access and maintain a persistent presence within targeted networks.
Targeting of Specific Organizations or Industries: These threats are not indiscriminate; APT actors carefully plan their operations and target high-value organizations possessing sensitive data or critical infrastructure. Financial institutions, government agencies, defense contractors, and providers of essential services are common targets due to the value of the information they hold.
Stealthy Nature of APTs: Secrecy is paramount for APT attackers. They employ various techniques to evade detection, such as using low-and-slow tactics to avoid triggering alarms, covering their tracks by erasing logs, and developing custom malware that traditional security solutions might miss. This stealthy approach allows them to operate within the network for extended periods without raising suspicion.
Real-Time APT Attacks
Here are some examples of notable Advanced Persistent Threat (APT) attacks:
OPM Data Breach (2014-2015) – In one of the most significant data breaches impacting the U.S. government, Chinese state-sponsored hackers compromised the Office of Personnel Management network and stole sensitive personnel records of over 21 million federal employees and contractors.
SolarWinds Supply Chain Attack (2020) – A sophisticated Russian APT group compromised the software build system of SolarWinds’ Orion platform, allowing them to distribute malicious updates to thousands of public and private organizations worldwide. This supply chain attack provided the threat actors with a foothold into numerous high-value targets.
Equifax Data Breach (2017) – A Chinese state-sponsored APT group exploited a vulnerability in Equifax’s systems, resulting in the theft of personal data of approximately 147 million individuals. This massive data breach exposed highly sensitive information such as Social Security numbers, birth dates, and addresses.
Operation Cloud Hopper (2014-2017) – Attributed to Chinese threat actors, this multi-year campaign targeted managed service providers (MSPs) worldwide to gain access to the networks of their clients across various sectors, including healthcare, finance, and energy.
Stuxnet (2010) – One of the first publicly known APT attacks, Stuxnet was a highly sophisticated computer worm designed to target and sabotage Iran’s nuclear program by causing centrifuges to malfunction.
Shamoon (2012) – Carried out by an Iranian APT group, the Shamoon malware wiped data from over 30,000 workstations at Saudi Aramco, one of the world’s largest oil companies.
These examples highlight the global reach, diverse targets, and severe consequences of APT attacks, which can impact government agencies, critical infrastructure, and major corporations across various sectors.
Defending against APT attacks
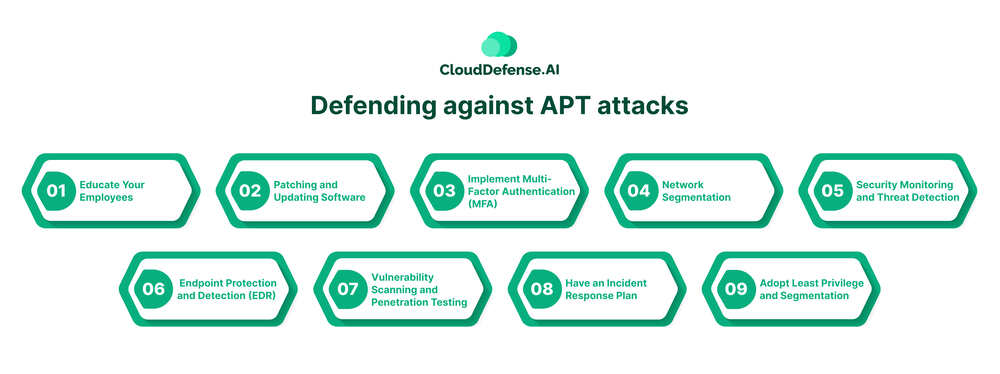
Being proactive against APT attacks requires a multi-layered approach, recognizing that there’s no single silver bullet. Here’s an arsenal of strategies to fortify your defenses:
1. Educate Your Employees: They are often the first line of defense. Regular security awareness training can equip employees to identify phishing attempts and social engineering tactics. Teach them to be cautious of suspicious emails, attachments, and unsolicited links.
2. Patching and Updating Software: Unpatched vulnerabilities are open doors for attackers. Make sure your systems, applications, and firmware are updated promptly. Prioritize patching critical systems and those facing the internet directly.
3. Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security beyond just passwords. It requires a second verification step, like a code from your phone, to access accounts. This makes it significantly harder for attackers to gain unauthorized access, even if they steal a password.
4. Network Segmentation: Dividing your network into smaller segments can limit the damage if a breach occurs. By compartmentalizing data and restricting access between segments, attackers can’t freely roam your entire network once they gain a foothold.
5. Security Monitoring and Threat Detection: Continuously monitor your network activity for suspicious behavior. Invest in Security Information and Event Management (SIEM) solutions that can collect data from various sources, analyze it for anomalies, and alert you to potential threats.
6. Endpoint Protection and Detection (EDR): EDR solutions go beyond traditional antivirus by monitoring endpoint devices (laptops, desktops, servers) for malicious activity. They can detect and respond to threats in real-time, offering another layer of defense.
7. Vulnerability Scanning and Penetration Testing: Proactively identify weaknesses in your systems and network by conducting regular vulnerability scans and penetration testing. This allows you to address security gaps before attackers exploit them.
8. Have an Incident Response Plan: Having a plan in place for when a security breach occurs is crucial. This plan should outline steps for detection, containment, eradication, and recovery. Regularly rehearse your incident response plan to ensure everyone knows their roles and responsibilities.
9. Adopt Least Privilege and Segmentation – Implementing the principle of least privilege, limiting user access rights, and segmenting networks can contain the lateral movement of APTs and reduce the potential impact of a compromise.
By implementing these security measures and fostering a culture of security awareness within your organization, you can significantly improve your ability to defend against APT attacks. Remember, constant vigilance and a layered security approach are essential in today’s ever-evolving threat landscape.
How CloudDefense.AI Can Help?
CloudDefense.AI positions itself as a powerful weapon in your fight against APT attacks, specifically by addressing some of the key challenges these attacks pose. Here’s how our Cloud Native Application Protection Platform (CNAPP) can potentially be helpful:
Unified Threat Detection and Management: APT attackers leverage various techniques. CloudDefense.AI, by aiming to be a one-stop shop for cloud security, could streamline threat detection by offering a central platform to monitor your cloud infrastructure and applications for suspicious activity. This can help reduce complexity and improve your ability to identify potential threats.
Automated Vulnerability Scanning: Keeping software up-to-date is critical against APTs that exploit vulnerabilities. CloudDefense.AI offers automated vulnerability scanning, which can help ensure your cloud environment is patched and secure.
Identity and Entitlement Management: Weak access controls are a common entry point for attackers. CloudDefense.AI, if it provides identity and access management features, can help strengthen your defenses by ensuring only authorized users have access to your cloud resources.
Continuous Monitoring: APT attacks are often stealthy. CloudDefense.AI’s continuous monitoring capabilities, coupled with threat intelligence feeds, can potentially help you identify and respond to suspicious activity faster.
DevSecOps Integration: Collaboration between development, security, and operations teams is vital for robust security. CloudDefense.AI integrates well with DevSecOps workflows and can streamline security practices throughout the software development lifecycle, potentially making it harder for attackers to exploit vulnerabilities introduced during development.
Bottom Line
Don’t be a victim! Stay vigilant against Advanced Persistent Threats (APTs). These cunning cyberattacks target high-value organizations, stealing sensitive data and remaining undetected for extended periods.
Understanding the hallmarks of APTs – their long-term goals, sophisticated tactics, and targeted approach – is crucial for defense. You build a strong foundation by educating employees, patching software religiously, and implementing multi-factor authentication. Advanced security solutions like CloudDefense.AI can further bolster your defenses with features like threat detection and automated patching. Remember, cybersecurity is an ongoing battle. A layered approach and constant vigilance are your best weapons against the ever-evolving threats posed by APTs.







