What is Containerization?
Containerization is a modern software deployment technique that involves packaging an application’s code and all the necessary operating system libraries and dependencies into a single, lightweight executable unit known as a container.
This method ensures that the application runs consistently across different computing environments, eliminating the need to install different software versions for different operating systems.
Containers encapsulate everything the application needs to run, making them portable and enabling seamless deployment on any infrastructure, whether a developer’s laptop, a data center, or a cloud environment.
How Does Containerization Work?
Containerization works by packaging an application along with its dependencies into a standardized, self-sufficient unit called a container. This approach ensures that the application performs consistently across various environments.
Building Container Images
Containerization begins with creating container images, which are read-only files containing all the necessary components to run an application, including the application code, runtime, libraries, and configuration files.
These images are built based on the Open Container Initiative image specification, ensuring standardization and interoperability. Developers construct these images using various containerization tools, such as Docker, encapsulating everything the application needs into a single package.
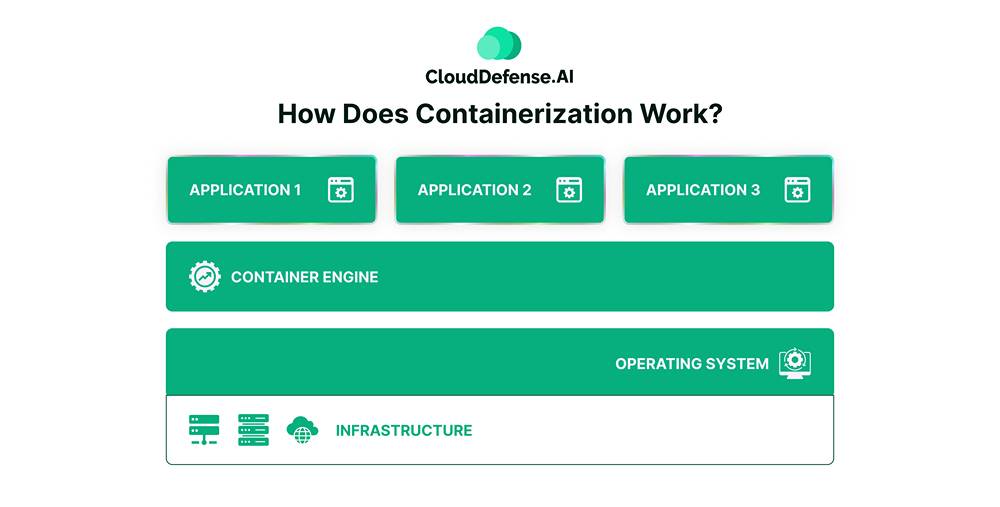
Containerization Architecture
A containerized system consists of several layers, including the infrastructure, the physical hardware, and bare-metal servers hosting the containers. The second layer is the operating system, with Linux being a popular choice due to its native support for containers, although cloud-based services like AWS EC2 are also commonly used.
Above the OS layer is the container engine, such as Docker Engine, which manages the creation and operation of containers, serving as an intermediary between the containers and the OS. The topmost layer includes the application code and its dependencies, such as libraries and configuration files, sometimes with a minimal guest OS layer installed over the host OS.
How Do Containers Operate?
Containers provide isolation by encapsulating applications within their environments, sharing the host OS kernel but maintaining separate user spaces. This isolation ensures that issues in one container do not affect others.
Containers also enhance efficiency by sharing common binaries and libraries, making them lighter and quicker to start than virtual machines that require a full OS boot. The abstraction from the host OS enables containers to run uniformly across different platforms, including local machines, VMs, cloud services, and various operating systems.
Benefits of Containerization
Containerization offers a range of significant benefits for developers and development teams, enhancing software deployment’s efficiency, portability, and reliability. Here are the key advantages:
Portability
Containers package software and its dependencies, enabling applications to run consistently across various environments. This means developers can build an application once and deploy it on multiple operating systems without rewriting the code. For instance, the same container can run on both Linux and Windows platforms. This portability simplifies deployment across different infrastructure types, including cloud and on-premises environments.
Scalability
Containers are lightweight and can be launched quickly, as they do not require booting an entire operating system. This efficiency allows developers to run multiple containers on a single machine, optimizing resource usage. Containers can be easily added or removed to handle varying loads, making it straightforward to scale applications up or down as needed.
Fault Tolerance
Containers provide fault isolation by running applications in separate, isolated environments. If one container fails, it does not impact the operation of other containers. This isolation increases the resilience and availability of applications, particularly those using a microservices architecture, where individual components run in separate containers.
Agility
Containerized applications operate in isolated environments, allowing developers to troubleshoot and update the application code without affecting the underlying operating system or other applications. This isolation facilitates faster development cycles, enabling teams to quickly implement changes and deploy updates.
Speed
Containers share the host machine’s operating system kernel, significantly reducing their size and start-up time compared to virtual machines (VMs). This lightweight nature leads to higher server efficiency and reduced server and licensing costs, as more containers can run on the same hardware as VMs.
Efficiency
By sharing the machine’s OS kernel, containers reduce resource overhead and start-up time. Application layers within containers can also be shared, further optimizing resource usage. This efficiency means more containers can run on the same hardware, enhancing server utilization and reducing costs.
Ease of Management
When used with container orchestration platforms like Kubernetes, containerization simplifies application provisioning, deployment, and management. Orchestration tools automate many tasks, such as load balancing and scaling, and ensure high availability, reducing the operational burden on development teams.
Security
Containers inherently isolate applications, preventing malicious code from spreading to other containers or the host system. Security permissions can be configured to block unwanted components and restrict unnecessary communications, enhancing the overall security of the application environment.
Types of Containerization
Containerization includes various technologies and platforms that enable the creation, deployment, and management of containerized applications. Here are some of the popular technologies used for containerization:
Docker
Docker is a widely used open-source container runtime that facilitates the building, deploying, and testing containerized applications. It allows developers to package applications and their dependencies into a single container, ensuring consistent behavior across different environments.
Linux Containers
Linux Containers, or LXC, are an open-source technology native to the Linux operating system. They provide a lightweight virtualization method for running multiple isolated Linux systems (containers) on a single host.
Kubernetes
Kubernetes is an open-source container orchestration platform designed to manage, scale, and deploy many containerized applications. It automates many aspects of container management, including deployment, scaling, and load balancing.
Microservices and Containerization
Microservices are a software design pattern that divides applications into small, independent services, each focused on a specific function. Microservices can be deployed across multiple containers when paired with containerization, enhancing resilience and flexibility. This setup allows for targeted scaling and updates to individual services without impacting the entire application.
Containers provide isolation, improving security by limiting the impact of potential breaches. Additionally, developers can write services in different programming languages, as containers support diverse environments. Combining microservices with containerization maximizes efficiency, as containers use fewer resources than virtual machines, and ensures consistent, reliable deployment across various platforms.
Specific Containerization Use Cases
Containerization offers various use cases across multiple domains, revolutionizing software deployment and management. Here are some prominent examples:
Cloud Migration:
Containerization facilitates the migration of legacy applications to cloud environments through the lift-and-shift approach. By encapsulating applications in containers, organizations can modernize their software infrastructure without requiring extensive code rewriting, ensuring compatibility and portability across different cloud platforms.
Adoption of Microservice Architecture:
Organizations using microservice architecture for building cloud-native applications benefit significantly from containerization. Microservices divide complex applications into smaller, independent components, each serving a specific function. Containerization enables developers to package these microservices into deployable units, promoting agility, scalability, and service isolation.
Internet of Things (IoT) Devices:
Containerization simplifies deploying and managing software applications on IoT devices, which often have limited computing resources. Using containers, developers can package and update applications seamlessly across diverse IoT devices, enhancing the development lifecycle, scalability, and efficiency.
Kubernetes and Containers
Kubernetes, commonly known as K8s, is a pivotal tool for scaling and managing container deployments. It fills the orchestration gaps left by containerization software like Docker or LXC.
Orchestration and Management
Kubernetes automates containers’ deployment, scaling, and operations across clusters of hosts, ensuring efficient large-scale management.
- Rollouts and Rollbacks: Kubernetes automates the deployment and updates of containers, enabling easy rollouts and rollbacks based on predefined resource utilization rules.
- Storage Mounting: Kubernetes allows automatic mounting of storage resources to containers, ensuring they have the necessary persistent storage.
- Resource Allocation: Kubernetes efficiently manages CPU and RAM requirements, deploying containers optimally within available resources.
Self-Healing and Load Balancing
- Self-Healing: Kubernetes performs health checks on containers, automatically restarting or replacing failed ones, ensuring high availability.
- Load Balancing: Kubernetes distributes traffic across multiple containers, maintaining efficient performance and resource utilization.
Security in Kubernetes
While containers provide isolation, they are not inherently secure. Kubernetes enhances security by enabling continuous monitoring for vulnerabilities and using container firewalls. Securing the host OS and container engine is crucial. Additionally, application security (appsec) must be integrated, using tools like Interactive Application Security Testing (IAST) and Web Application Firewalls (WAFs) to identify and mitigate threats holistically.
Containerization vs Virtualization
It’s easy for newcomers to confuse containerization (enabled by software like Docker) with traditional server virtualization (enabled by hypervisors like HyperV and VMware ESXi). In simple terms, the difference is:
Server virtualization abstracts the hardware and runs multiple operating systems on a single physical server. Containerization abstracts the operating system, allowing various applications to run in isolated environments on the same OS.
Both technologies abstract resources, but containerization operates at a higher level than server virtualization. They are not mutually exclusive; you can run containerized applications on a container engine deployed within a virtual machine. This allows for combining the benefits of both virtualization and containerization, optimizing resource utilization and flexibility.
Containerization Security with CloudDefense.AI
CloudDefense.AI is a leading Cloud-Native Application Protection Platform (CNAPP) designed to deliver comprehensive container security across every CI/CD pipeline stage. With a multi-layered security approach, it effectively mitigates risks in containerized environments, ensuring robust protection against evolving threats.
Key Security Features:
- Continuous Image Scanning: Detects vulnerabilities, misconfigurations, and unknown components before deployment.
- Runtime Protection: Shields running containers from security breaches and exploits in real-time.
- Repository Integration: Prevents unauthorized or non-compliant images from entering the pipeline, reducing the attack surface.
- Advanced Vulnerability Management: Utilizes an AI-powered detection engine and an up-to-date vulnerability database to minimize false positives and enhance accuracy.
- Shift-Left Security: Embeds security early in development, seamlessly integrating with DevSecOps workflows.
With its AI-enhanced insights and automated threat detection, CloudDefense.AI empowers security teams to prioritize and remediate critical vulnerabilities efficiently. Experience next-level container security—book a free demo today!







