What is a Network Firewall?
A network firewall acts as a critical security barrier, monitoring and controlling incoming and outgoing network traffic based on a set of security rules.
It evaluates data packets attempting to enter or leave your network, ensuring only authorized traffic passes through.
Firewalls enforce these rules by considering key factors:
- Port Numbers: Think of ports as unique doorways to your network. Firewalls can restrict or allow traffic based on the specific port being accessed.
- IP Addresses: Like digital street addresses, IP addresses identify devices on a network. Firewalls block untrusted or malicious IP addresses while permitting trusted ones.
- Protocols: Protocols dictate how devices communicate (e.g., HTTP for browsing, FTP for file transfers). Firewalls can allow or deny traffic, depending on the protocol.
This packet inspection enables firewalls to filter out malicious traffic, such as malware or hacking attempts while allowing legitimate activities like emails and web browsing to flow freely. By functioning as your network’s vigilant traffic cop, firewalls ensure that your systems remain secure and operational.
Benefits of a Network Firewall
Let’s explore the compelling benefits that make firewalls irreplaceable in protecting your digital environment.
- Prevents Unauthorized Access: Controls and restricts unauthorized entry to network resources, ensuring only trusted users can access sensitive systems.
- Blocks Malicious Traffic: Detects and halts threats such as viruses, worms, and cyberattacks before they penetrate your network.
- Segmentation and Isolation: Separates network segments to limit lateral movement of threats, providing enhanced containment and control.
- Centralized Security Management: Allows consistent enforcement of security rules and policies across the network, simplifying management.
- Activity Logging and Monitoring: Tracks and audits network activity to identify anomalies and conduct thorough security reviews.
- Application and Service Filtering: Inspects traffic based on applications or services, allowing fine-tuned control over network behavior.
- Secures Remote Access: Facilitates safe access for remote users through authentication protocols and encryption mechanisms.
- Compliance Enforcement: Ensures alignment with organizational security and regulatory requirements, reducing the risk of non-compliance penalties.
- First Line of Defense: Acts as a primary shield against external threats, minimizing exposure to malicious entities.
- Maintains Integrity and Confidentiality: Protects data and network operations by preventing tampering or unauthorized disclosure of sensitive information.
Key Features of a Network Firewall:
A firewall acts as your network’s vigilant guard, ensuring that only trusted traffic gets through while blocking potential threats. Here’s how they perform this critical role:
- Traffic Inspection Firewalls inspect every piece of data—every packet—that tries to enter or exit the network. They don’t just check the surface but analyze detailed metadata, including the origin, destination, service types, and other characteristics, ensuring that only authorized data is allowed.
- Policy Enforcement Firewalls operate based on pre-configured security policies that define which activities and transfers are permitted. The network administrator customizes these rules, which are then enforced consistently, ensuring compliance with your network’s standards.
- Access Control Firewalls act as a boundary, controlling traffic between trusted internal networks and untrusted external ones, such as the Internet. They restrict unauthorized access while enabling legitimate communication and maintaining a secure perimeter for your network.
- Application Filtering Firewalls provide granular control over applications and services. This feature allows you to block or allow specific IP addresses, ports, or applications. Additionally, when combined with tools like VPNs and antivirus software, firewalls enhance your network’s ability to prevent attacks and unauthorized access.
- Network Segmentation By segmenting the network into isolated zones, firewalls limit the damage an attacker can do if they manage to breach one section. This creates security barriers that contain any potential threats, preventing them from spreading across the network and protecting your sensitive data.
These core features make firewalls indispensable for protecting your network. They ensure safe data traffic while maintaining control and compliance.
How Does a Firewall Work?
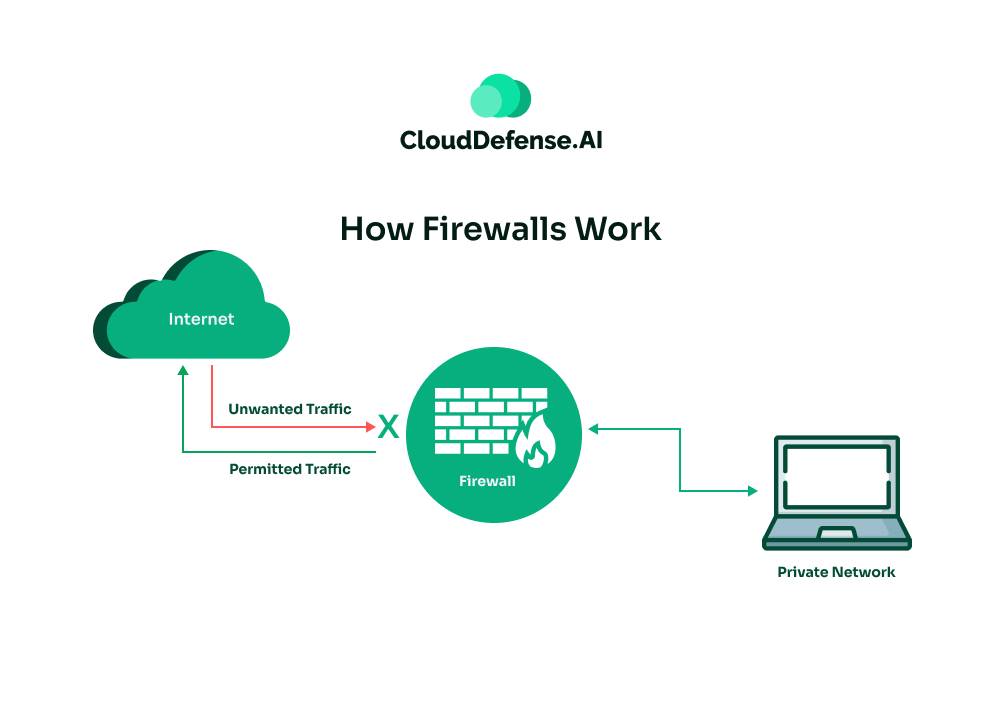
Here’s a breakdown of how a network firewall operates, keeping the technical jargon to a minimum:
1. Inspecting Traffic Flow: Metric packet inspection is at the core of a firewall’s functionality. All incoming and outgoing data traffic on the network is meticulously examined. This data traffic is comprised of individual units called packets, which carry information like source and destination addresses along with the actual data payload.
2. Security Rule Matching: The firewall has a pre-defined set of security rules, like a rulebook for the inspector. These rules specify which types of data packets are allowed to enter or leave the network (think of them as guidelines for what can be brought in or out).
3. Scrutinizing the Data: The firewall analyzes each data packet based on factors like:
- Source IP Address: The IP address of the device sending the data packet. Firewalls can block traffic originating from untrusted or unauthorized sources.
- Destination IP Address: The IP address of the intended recipient of the data packet.
- Port Numbers: Ports function as specific communication channels on a device. Firewalls can restrict traffic based on the port it’s trying to access.
- Protocol: The protocol defines the language used for communication between devices. Firewalls can allow or deny traffic based on the protocol used (e.g., HTTP for web browsing and FTP for file transfers).
4. Granting or Denying Access: Based on the analysis, the firewall makes a split-second decision. If the data packet aligns with the allowed criteria, it’s waved through like a passenger with proper documentation. However, suppose the packet raises any red flags or violates the rules (like containing suspicious content or originating from an untrusted source). In that case, it’s blocked, much like how security might stop a passenger with prohibited items.
5. Logging Activity: The firewall keeps a log of its activity, recording details about allowed and blocked traffic. This log serves as a valuable record for security audits and helps identify potential threats.
6. Constant Vigilance: This inspection process happens continuously, ensuring a constant flow of safe and authorized traffic while keeping malicious activity at bay.
A Look at Different Firewall Types
Network firewalls come in various forms, each offering distinct functionalities and deployment strategies. Here’s a breakdown of the most common types of network firewalls:
By Deployment:
- Network Firewall: The quintessential firewall, it resides at the perimeter of a network, typically between a private network and the public internet. This strategic placement allows it to monitor and filter all incoming and outgoing traffic.
- Host-based Firewall: Unlike its network counterpart, this firewall resides directly on individual devices, such as computers or servers, providing granular control over traffic flow for each system – an additional layer of security for discerning digital fortification.
By Form Factor:
- Hardware Firewall: A dedicated physical appliance specifically designed for firewall functionality. These appliances offer robust performance and centralized management.
- Software Firewall: A software program installed on a device, offering a cost-effective solution for basic network protection. However, they may not provide the same level of performance or security features as hardware firewalls.
By Functionality:
- Internal Firewall: Strategically deployed within a network, this firewall segments the domain into distinct security zones, limiting the potential damage of a breach by restricting an attacker’s lateral movement.
- Distributed Firewall: A collection of firewalls strategically distributed across a network, offering scalability and redundancy for larger networks.
- Perimeter Firewall: As the name suggests, this firewall is located at the network’s outer edge and functions as the first line of defense against external threats.
- Next-generation Firewall (NGFW): These advanced firewalls go beyond basic packet filtering. They offer deep packet inspection capabilities, application awareness, and intrusion prevention functionalities for comprehensive network security.
By Inspection Method:
- Packet Filtering Firewall: The most basic type of firewall. It examines individual data packets based on factors like source IP address, destination IP address, and port number.
- Circuit-level Gateway: Focused on managing connections between devices rather than individual data packets, this firewall provides an additional layer of security for network communication protocols.
- Stateful Inspection Firewall: This is an evolution of packet filtering. It keeps track of the state of network connections, allowing for more sophisticated traffic filtering decisions.
- Web Application Firewall (WAF): Specifically designed to protect web applications from security vulnerabilities and attacks.
- Proxy Firewall: Acts as an intermediary between a device and the internet, filtering and potentially modifying traffic to enhance security.
How to Choose the Right Network Firewall?
Selecting the most suitable network firewall for your needs requires careful consideration of several factors. Here’s a series of questions to ask yourself, followed by suggestions to guide you toward the optimal solution:
Network Needs:
- What size is your network? (Number of devices)
- What is your typical internet usage? (High-bandwidth activities like streaming?)
- Do you need to manage remote users?
Security Features:
- What level of threat protection do you need? (Basic filtering vs. advanced intrusion prevention)
- Does the firewall offer deep packet inspection for application control?
- Does it integrate with other security solutions like anti-virus software?
Management and Usability:
- Is the firewall easy to set up and manage? (Consider your IT expertise)
- Does it offer remote management capabilities?
- Does the vendor provide ongoing support and updates?
Budget:
- What is your budget for a network firewall? (Hardware vs. software options)
- Are there any ongoing subscription costs for updates or support?
Here are some suggestions:
- For small home networks: A software firewall or a basic hardware firewall with user-friendly features might be sufficient.
- For businesses with moderate network traffic: Consider a hardware firewall with features like application control and basic threat protection.
- For large enterprises with complex security needs: A next-generation firewall (NGFW) offering deep packet inspection, intrusion prevention, and advanced threat detection capabilities would be ideal.
Additional Considerations:
- Ease of use: Consider the firewall’s user interface and manageability for your IT team.
- Scalability: If your network is expected to grow, choose a firewall that can scale to meet future demands.
- Vendor reputation: Opt for a reputable vendor with a strong track record in security solutions and customer support.
Can a network firewall truly stop every single cyberthreat?
No, a network firewall cannot protect against all types of threats. While they are a crucial security measure, they have limitations. Here’s why:
- Evolving Threats: Cybercriminals are constantly developing new attack methods. Firewalls rely on predefined security rules, and entirely new threats might slip through undetected.
- Social Engineering: Firewalls can’t protect against attacks that trick users into giving away sensitive information or clicking malicious links.
- Zero-Day Attacks: These are new, unknown vulnerabilities that software vendors haven’t yet patched. Firewalls may not be able to identify and block them immediately.
However, firewalls are highly effective against many common threats, including:
- Malware: They can block malicious software downloads and prevent them from infecting your devices.
- Hacking Attempts: Firewalls can restrict unauthorized access attempts to your network.
- Denial-of-Service Attacks: They can help mitigate these attacks by filtering out excessive traffic.
In summary, firewalls are a vital first line of defense, but they should be used in conjunction with other security measures like antivirus software, user education, and keeping software updated.
Will a network firewall slow down the internet connection?
Yes, a network firewall can slow down your network performance. Here’s why:
- Traffic Inspection: Firewalls meticulously examine all incoming and outgoing data packets. This inspection process can take time, especially for complex firewalls with deep packet inspection capabilities.
- Filtering and Blocking: If a firewall actively blocks a lot of malicious traffic, it can slightly slow down the overall network speed.
However, a firewall’s performance impact is usually negligible for most users. Modern firewalls are optimized for efficiency, and the security benefits they offer far outweigh any potential slowdown, especially for critical data or business operations.
How to set up a network firewall?
Setting up a network firewall can vary depending on the type you choose. Here’s a general breakdown:
- Software Firewall: A software firewall might come pre-installed on your operating system or require a separate installation. You’ll typically need to configure the firewall settings to define allowed applications and protocols.
- Hardware Firewall: To set up a dedicated hardware firewall, you might need to connect it to your network router and configure its settings through a web interface. This process might require some technical knowledge.
- Router with Built-in Firewall: Many routers come with basic firewall functionality. You can usually access the router’s settings page (often through a web browser) to configure its firewall options.
It’s always recommended to consult your firewall’s documentation or the manufacturer’s website for specific setup instructions. If you need to be more comfortable configuring a firewall yourself, consider seeking assistance from a network administrator or IT professional.
Final Words
In this article, we have seen in detail what is a network firewall, explored the various types suited for different needs, and unraveled the questions surrounding their effectiveness and implementation
Remember, for maximum protection, firewalls should be complemented by other security measures like user awareness and software updates. So, take charge of your network’s security—deploy a firewall today and venture forth into the digital realm with peace of mind.







