Almost every digital system hinges on two critical defenses: network security and application security. Network security focuses on securing the pathways where data moves, while application security secures the software people interact with daily.
Both address unique vulnerabilities, yet they’re interconnected in protecting modern systems. So, in order to truly understand cybersecurity, it’s essential to grasp the distinction and synergy between these two pillars. Here’s let’s break down the key differences between network security vs application security and discuss how they intersect and why each matters in its own right.
Understanding Network Security
Network security refers to the practice of protecting computer networks from unauthorized access, misuse, or attacks. Pause and think about the digital space you rely on every day—your work emails, online banking, virtual meetings. Behind the scenes, network security ensures that the pathways carrying this information remain protected.
But it’s not just about blocking hackers. It’s about control, visibility, and resilience. Let’s dig into the essentials:
Core Elements of Network Security
- Perimeter Defense: Tools like firewalls and intrusion detection systems act as sentries, deciding what gets in and out of your network. For example: a firewall might block traffic from a suspicious IP address trying to probe your systems.
- Network Segmentation: By dividing your network into smaller, isolated zones, you limit the damage a breach can cause.
- Access Control: Not everyone needs access to everything. By enforcing strict rules on who can access specific parts of your network, you reduce unnecessary exposure. Ask yourself: Does every device on your network truly need full access?
- Encryption in Transit: Data moving across the network is vulnerable to interception. Encrypting it ensures it’s unreadable even if intercepted.
Why Network Security Is Crucial
- Remote Work Challenges: Employees connect from home, cafes, or even airports—places that don’t have enterprise-level security. Your network must compensate for this unpredictability.
- Proliferation of Devices: IoT devices, smart gadgets, and mobile devices all increase potential weak points in your infrastructure.
- Sophisticated Attacks: From ransomware to man-in-the-middle attacks, adversaries are constantly finding new ways to exploit weak networks.
So, every time you connect to the internet, you’re taking a calculated risk. Network security is the measure that tips the balance in your favor. It’s not just about defense; it’s about ensuring continuity, trust, and confidence in your digital systems.
Now that we’ve laid the groundwork, let’s shift focus to application security—because securing the network is only half the battle.
Understanding Application Security
Application security refers to the process of identifying, fixing, and preventing vulnerabilities in software applications. Every application you use—be it your banking app, an online store, or a collaboration tool—holds sensitive information. This makes applications a goldmine for attackers. While we trust these tools to work seamlessly, they often have vulnerabilities hidden beneath the surface. Application security ensures that these tools remain safe, reliable, and trustworthy.
Core Principles of Application Security
- Input Validation: Applications must verify and sanitize any data users provide to prevent malicious actions. For instance, have you ever wondered how attackers exploit a simple login box? Without proper validation, it could open the door to attacks like SQL injection.
- Authentication and Authorization: Applications need robust mechanisms to confirm a user’s identity and limit their access. Why should every employee or user have the same permissions? Tailoring access levels reduces unnecessary exposure.
- Secure Code Practices: Applications must be built with security in mind, using regular testing to find and fix vulnerabilities in the code. Think about it: How often do businesses release apps quickly but overlook the importance of secure development?
- Patching and Updates: Threats evolve, and outdated applications are easy targets. Regular updates are non-negotiable to close security gaps.
Why Does It Matter?
More than just tools, applications are gateways to sensitive data. A single breach can compromise customer trust, corporate assets, and even reputations.
- Direct Interaction with Data: Applications handle critical information like payment details and personal records, making them high-value targets.
- Rapid Expansion: As businesses adopt cloud-native applications, APIs, and microservices, the attack surface grows, demanding stronger defenses.
- Real-World Consequences: From stolen data to service outages, weak application security can disrupt lives and businesses.
Every single time you log into an app, send a message, or make a payment, you’re trusting that application to keep your data safe. But ask yourself this: How many apps do you use daily? How many of them are truly secure? To ensure the peace of mind and safety, application security is about ensuring the systems you rely on work as intended, without hidden vulnerabilities.
Now that we’ve explored both network and application security, let’s see how they work together to create a comprehensive cybersecurity framework.
Network Security vs Application Security: Key Differences
Application security and network security are two distinct, yet equally important, layers of defense in cybersecurity. Both address unique challenges and require specific approaches. Here’s a clear breakdown of how they differ:
Focus Area
Network security focuses on securing the communication channels that connect systems and devices. For example, when employees access company resources remotely, tools like VPNs ensure the data traveling between their device and the company’s servers is encrypted and secure.
Application security, on the other hand, protects the software itself. Think of an online payment platform. Even if the network is secure, vulnerabilities in the application—such as weak input validation—can allow attackers to inject malicious code and steal sensitive data.
Types of Threats
Network security deals with threats like DDoS attacks, where an attacker floods a network with traffic to disrupt services. Imagine an online store going offline because its network couldn’t handle the surge of fake traffic.
Application security addresses risks specific to the software, such as broken authentication or API vulnerabilities. A real-world example is a poorly secured API in a financial app, allowing unauthorized access to user accounts.
Tools and Techniques
Network security uses tools like firewalls, intrusion detection systems, and traffic encryption. For instance, a firewall might block a suspicious IP address attempting to access sensitive systems.
Application security relies on practices like secure coding, vulnerability scans, and penetration testing. Developers regularly scan their applications for bugs or weaknesses, fixing issues before attackers can exploit them.
Impact on Users
For network security, users are usually unaware of its operation. When you access a corporate network, the firewalls and monitoring tools in the background ensure a secure connection without you noticing.
Application security is more visible to users. For example, multi-factor authentication (MFA) prompts on a banking app directly involve users by requiring them to verify their identity.
Layer of Operation
Network security protects the infrastructure—everything from servers to IoT devices. For instance, it ensures that an organization’s internal systems can communicate securely without external interference.
Application security focuses on securing specific software functionalities. For example, it ensures that users of an e-commerce platform can only access their own account information and not anyone else’s.
Response to Attacks
When a network breach occurs, network security tools isolate the affected area to stop the threat from spreading. If an IoT device is compromised, the network segmentation ensures it doesn’t impact critical systems.
With application security, the response often involves fixing the vulnerability that allowed the breach. For instance, if attackers exploit a flaw in an application to access a database, the development team updates the application code to prevent future incidents.
Proactive vs. Reactive
Network security is heavily prevention-focused. Systems like intrusion detection tools actively monitor traffic for anomalies, stopping potential attacks before they can cause damage.
Application security tends to involve more reactive measures, such as patching vulnerabilities after they’re discovered. Bug bounty programs are a good example—ethical hackers find flaws, and developers fix them to improve security.
Tools Used
Network security tools include firewalls, VPNs, intrusion detection/prevention systems (IDS/IPS), and endpoint detection and response (EDR) systems. These tools focus on securing data flow and detecting anomalies across the network.
Application security tools, on the other hand, are tailored to securing the software. Examples include:
- Static Application Security Testing (SAST): Used to analyze source code for vulnerabilities during development.
- Dynamic Application Security Testing (DAST): Tests applications in runtime to identify flaws.
- Software Composition Analysis (SCA): Tracks vulnerabilities in the software’s components to ensure no outdated or insecure packages are used.
- Web Application Firewalls (WAF): Protects web applications from threats like cross-site scripting (XSS) and SQL injection.
For example, a software team might use SCA to analyze open-source libraries for vulnerabilities, secure the codebase with SAST during development, and deploy a WAF to protect the application against live attacks in production.
Now that we discussed the key differences between network security and application security in detail, below is a clear and structured table outlining the key differences between application security and network security:
| Aspect | Network Security | Application Security |
| Focus Area | Secures communication channels and infrastructure connecting systems and devices. | Protects the software itself, including its functionality and user data. |
| Types of Threats | Defends against external attacks like DDoS or malware targeting the network infrastructure. | Mitigates vulnerabilities like SQL injection, insecure APIs, and poor authentication mechanisms. |
| Tools and Techniques | Firewalls, VPNs, intrusion prevention systems, and traffic encryption. | Secure coding, vulnerability scanning, penetration testing, and runtime protection tools. |
| Impact on Users | Operates behind the scenes with minimal visibility to users (e.g., VPNs securing remote connections). | Visible to users through measures like multi-factor authentication or security warnings. |
| Layer of Operation | Works at the network layer, safeguarding routers, switches, and servers. | Operates at the application layer, securing specific functionalities within the software. |
| Response to Attacks | Contains and isolates attacks quickly to prevent escalation (e.g., network segmentation). | Identifies and patches vulnerabilities to prevent recurrence (e.g., software updates). |
| Proactive vs. Reactive | Prevents attacks using tools like intrusion detection systems to monitor network traffic. | Addresses vulnerabilities proactively with scans and reactively by fixing bugs post-deployment. |
| Tools Used | Firewalls, IDS/IPS, VPNs, endpoint detection and response (EDR). | SAST, DAST, SCA, WAF, dependency scanners, and runtime protection tools. |
Comprehensive Checklist: What Comes Under Network Security vs. Application Security
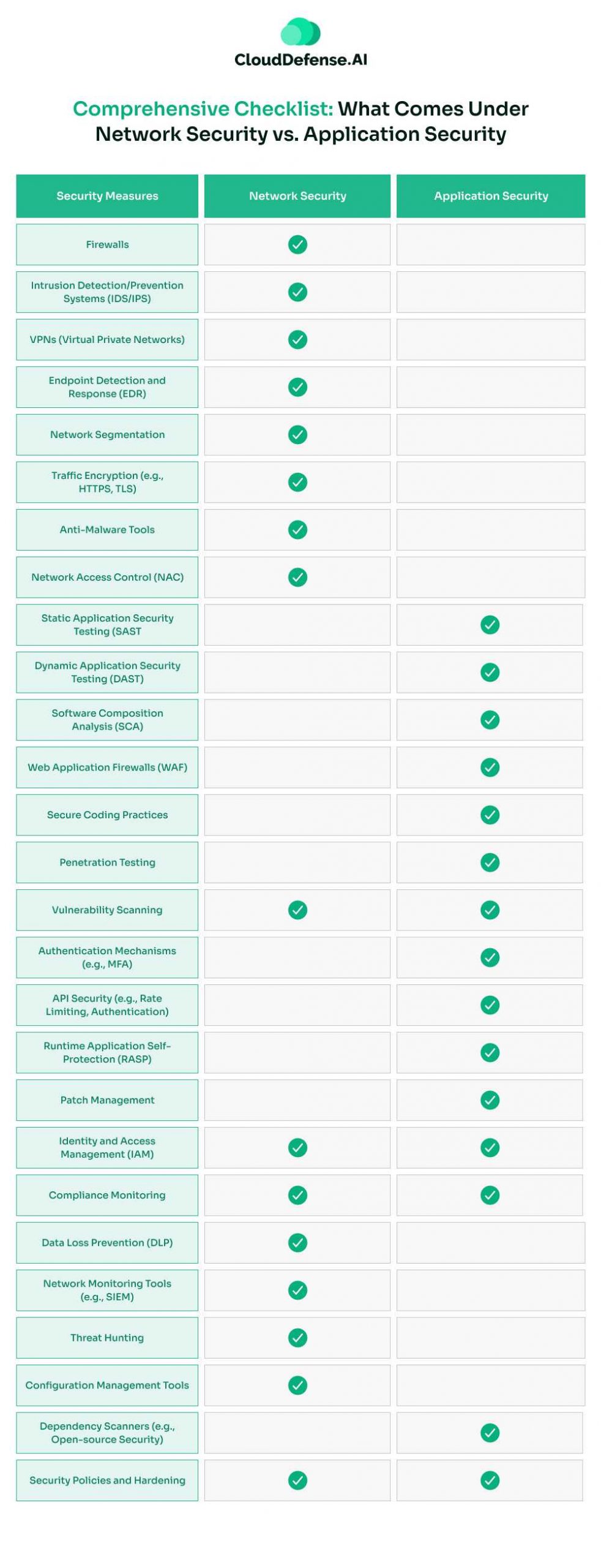
The detailed checklist gives a granular breakdown of tools, techniques, and practices across both domains, helping readers clearly understand the distinctions and overlaps.
The above-given detailed checklist gives a granular breakdown of tools, techniques, and practices across both domains, helping readers clearly understand the distinctions and overlaps.
Wrapping Up
Securing your business isn’t just about locking down networks or scanning for threats—it’s about understanding where the real risks are. Network security keeps attackers from breaching your infrastructure, but that’s not enough. If your applications have vulnerabilities, they become an open door for exploits. Both need equal attention, and ignoring one puts everything at risk.
At CloudDefense.AI, we provide industry-leading application security solutions designed to help businesses stay ahead of vulnerabilities. Our SAST, DAST, and SCA tools give you deep visibility into your code, detect security flaws early, and safeguard against attacks before they happen.
Whether you’re securing a cloud-native application, APIs, or legacy software, our solutions integrate seamlessly into your development pipeline without slowing you down. Our solutions integrate seamlessly into your development pipeline, regardless of whether you are securing a cloud-native application, APIs, or legacy software.
Book a free demo today and see how CloudDefense.AI can help you build secure applications from the ground up!







