Nowadays, cybersecurity isn’t just about building walls anymore—it’s about questioning who gets in and why. And this is why two key strategies—Zero Trust and the Principle of Least Privilege—have emerged as cornerstones of modern security frameworks. Both emphasize restricting access, but they approach the problem differently.
Here, we’ll break down what these strategies mean, how they differ, and why combining them could be the key to staying one step ahead of threats.
Understanding the Concepts
Before we move on to learn about their differences…
What is Zero Trust?
Zero Trust is a security framework based on a simple idea: trust no one. It treats every user, device, or system as potentially compromised, whether they’re inside your network or accessing remotely. Instead of granting blanket trust, Zero Trust requires continuous verification at every step.
Here’s what it does:
- No blind trust: Every access attempt is validated, even from internal users.
- Continuous verification: Identity, device, and behavior are re-checked at every step.
- Dynamic decisions: Access is granted or blocked based on factors like location, device health, and behavior anomalies.
Let’s consider an example: imagine your company’s IT system. Even if an employee has access to internal tools, Zero Trust doesn’t assume they’re harmless. Before they can open sensitive files or use specific apps, the system verifies their identity, device health, and even their location. If something feels off—like someone logging in from a suspicious country—the access is blocked or flagged for review.
Zero Trust pushes businesses to move away from outdated “perimeter-based” security. It focuses on dynamic, granular control, ensuring no access is granted without a reason—and constant checks.
What is the Principle of Least Privilege (PoLP)?
The Principle of Least Privilege works differently but shares the goal of reducing risk. It’s about limiting access to exactly what someone needs—nothing more.
Here’s what PoLP implies:
- Role-based permissions: Access is tailored to an individual’s job responsibilities.
- Limits damage: If an account is compromised, the attacker can only access what’s strictly necessary for that role.
- Granular control: Even within their role, users might only have partial access to specific systems.
Take an employee working in finance. They might need access to payroll systems but shouldn’t be able to access customer databases or server configurations. Under PoLP, their permissions are tightly scoped to only what’s essential for their role. Even within payroll, they might only see data related to their team, not the entire organization.
This concept ensures that if an account is compromised, the attacker’s reach is limited. They won’t gain access to everything, just the minimal set of permissions tied to that account.
“So, the concept takeaway here is Zero Trust is a comprehensive strategy, whereas Least Privilege is a specific tactic or principle that can be a part of a Zero Trust implementation.”
The Evolution of Zero Trust and the Principle of Least Privilege
The development of Zero Trust and the Principle of Least Privilege didn’t happen by accident. Both emerged as solutions to clear and growing problems in cybersecurity, driven by changes in how we use technology and the increasing sophistication of threats. Let’s break it down.
1. Evolution of Zero Trust
- The Old Days of Perimeter Security: Early on, security was straightforward—keep everything inside a network “safe zone.” If you were in, you were trusted. This worked because most systems were centralized and employees worked from physical offices.
- What Changed: With cloud computing, remote work, and mobile devices becoming the norm, the “safe zone” concept fell apart. People and devices were connecting from everywhere, making perimeter security ineffective.
- Zero Trust Emerges: In response, experts realized trust shouldn’t be based on location. Around 2010, Zero Trust began to take shape, focusing on verifying every access attempt, every time. Companies like Google adopted this mindset with BeyondCorp, making it clear that trust had to be earned—not assumed.
2. Evolution of the Principle of Least Privilege (PoLP)
- The Problem with Over-Permissioned Accounts: In early IT setups, users often got broad access because it was easier to manage. This created massive vulnerabilities—if one account was compromised, it could expose entire systems.
- The Shift to Role-Based Access: Organizations began limiting permissions based on job roles. If you didn’t need access to a system, you simply didn’t get it. This was the beginning of PoLP as we know it.
- Fine-Tuning in Modern Environments: With today’s complex environments—spanning cloud platforms, on-premises systems, and SaaS apps—PoLP has evolved further. Tools now allow businesses to enforce permissions down to very specific actions, keeping risks tightly controlled.
Why Did These Models Evolve?
- Increased Attack Surface: As technology expanded, attackers had more ways to breach systems—remote logins, IoT devices, third-party vendors.
- Complex Threats: From ransomware to insider threats, risks grew more varied and harder to detect.
- Regulations: Compliance requirements forced organizations to take access control and monitoring seriously.
Zero Trust and PoLP evolved because the old ways just couldn’t keep up. They were built to solve real-world problems, and their importance has only grown as cybersecurity challenges have become more advanced.
Zero Trust vs. the Principle of Least Privilege: Key Differences
Zero Trust and the Principle of Least Privilege (PoLP) are two critical concepts in cybersecurity. While they overlap in some ways, they tackle security challenges from different angles. Let’s get straight into how they differ, their components, and why they matter.
Zero Trust: A Security Framework
Zero Trust is a full-scale security approach built around the idea of “never trust, always verify.” It operates on the assumption that no user, device, or system is trustworthy by default—whether inside or outside the network.
Core Components of Zero Trust:
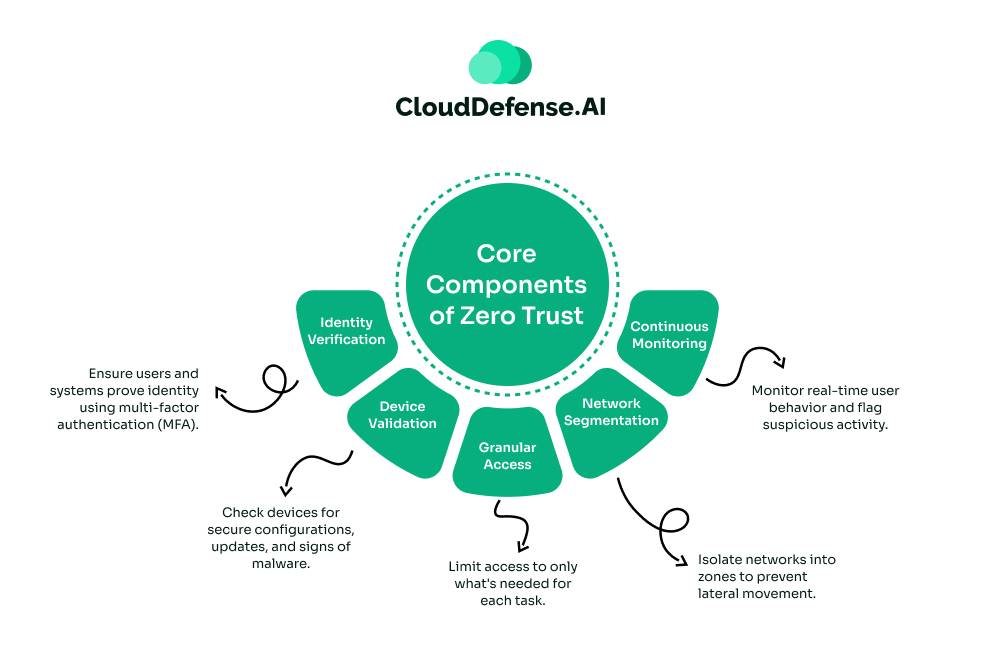
1. Identity Verification: Every user and system must prove their identity, often through multi-factor authentication (MFA). This ensures only verified entities can connect.
2. Device Validation: Devices are checked for compliance—things like up-to-date patches, secure configurations, and no signs of malware.
3. Granular Access (Built-In PoLP): Even within Zero Trust, access is strictly limited to what’s required for a task, integrating the PoLP principle.
4. Network Segmentation: Breaking the network into isolated zones (micro-segmentation) ensures that even if an attacker breaches one area, they can’t move freely.
5. Continuous Monitoring: Trust isn’t static. Zero Trust monitors user behavior and access patterns in real time, looking for anomalies or unauthorized actions.
Example of Zero Trust in Action:
Let’s say an employee is logging into the company’s HR system:
- The system verifies their identity using MFA.
- It checks their laptop for compliance, like whether it’s running updated software.
- The employee can only view their personal data, not payroll records for the entire company.
- If the system detects unusual behavior, like access from a new location or device, it denies entry or flags the activity for review.
Principle of Least Privilege (PoLP): A Targeted Security Approach
PoLP, unlike Zero Trust, focuses specifically on access control. The goal is simple—users, systems, or applications only get the bare minimum permissions required to complete their tasks. Nothing more.
Core Components of PoLP:
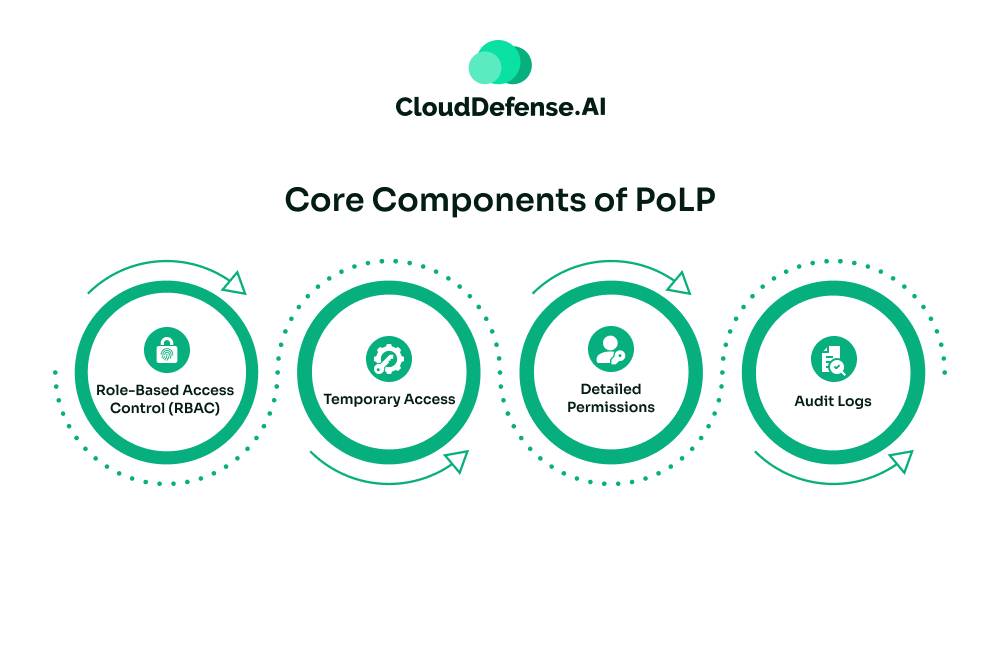
1. Role-Based Access Control (RBAC): Permissions are assigned based on job roles. For example, a financial analyst can access budget tools but not HR systems.
2. Temporary Access: Users are granted time-limited permissions for specific tasks. Once the task is complete, access is revoked.
3. Detailed Permissions: Access is granular—users can view or edit certain files, but not delete them, for example.
4. Audit Logs: All access activities are logged to ensure full visibility, helping identify and investigate potential misuse.
Example of PoLP in Action:
Imagine an intern working in a marketing department:
- They get access to social media dashboards but not to admin tools or customer databases.
- If they need access to additional tools for a project, it’s provided temporarily and removed afterward.
Here’s a detailed comparison to clarify how they differ and complement each other:
| Aspect | Zero Trust | Principle of Least Privilege (PoLP) |
| Scope | Comprehensive security framework. | Specific access control principle. |
| Focus | Continuously validates trust for every user, device, and action. | Limits access to the bare minimum required for a task. |
| Core Idea | “Never trust, always verify.” | “Grant only what is necessary.” |
| Implementation | Achieved through tools like multi-factor authentication (MFA), device validation, micro-segmentation, and real-time monitoring. | Uses access control policies like role-based access control (RBAC) and granular permissions. |
| Target | Holistic—addresses users, devices, applications, and network segments. | Specific—focuses on permissions for users, systems, or applications. |
| Examples | Requires identity verification, device compliance checks, and continuous monitoring. | Assigns permissions based on roles or tasks (e.g., temporary access for specific actions). |
| Granularity | Broad—includes network-wide protections and monitoring. | Granular—limits individual permissions to specific systems or data. |
| Use Case | Protects against insider threats, external attacks, and lateral movement within a network. | Minimizes damage if an account or system is compromised. |
| Dependency | Relies on PoLP as part of its broader strategy. | Can be applied independently without a Zero Trust framework. |
| Outcome | Holistic defense against unverified access and anomalies. | Prevents unnecessary access and reduces exposure to attacks. |
Are They Connected?
Yes, they are absolutely connected. The Principle of Least Privilege (PoLP) is a fundamental part of the Zero Trust framework. While Zero Trust is about verifying everything—users, devices, and applications—PoLP ensures that even after verification, access is limited strictly to what’s necessary.
How They Work Together
1. Least Privilege as a Building Block: In Zero Trust, verifying identity isn’t enough. Enforcing Least Privilege ensures users, systems, or applications don’t gain excessive access after verification. For example, even if a developer is authenticated through multi-factor authentication, they shouldn’t have admin access to production environments unless required for a specific task.
2. Granular Control: Zero Trust policies apply at every level—network, applications, data, and devices. Least Privilege complements this by setting fine-grained permissions to reduce overexposure. Think of it as limiting access to the right doors after someone is already inside the building.
3. Minimizing Damage: Even if an attacker bypasses identity verification, PoLP restricts the scope of potential damage. A compromised account with minimal permissions can’t do much harm, and Zero Trust’s monitoring can flag suspicious activity.
Real-Life Example:
Lets say an organization adopting Zero Trust for its IT infrastructure:
- Identity Verification: Employees log in with multi-factor authentication and biometrics.
- PoLP Enforcement: Each employee gets only the permissions they need. A marketing analyst can access campaign data but not the CRM’s admin dashboard.
- Continuous Monitoring: Any attempt to access unauthorized areas triggers alerts or blocks the action.
Together, these layers create a tightly integrated security posture. While Zero Trust is the overarching strategy, PoLP is a critical mechanism that ensures no one—legitimate user or attacker—gets more access than necessary.
In short, implementing Zero Trust without enforcing Least Privilege leaves gaps, and enforcing PoLP without Zero Trust’s broader protections limits its effectiveness. They are not just connected; they’re mutually reinforcing.
Wrapping Up
While Zero Trust and Least Privilege are often lumped together, they’re distinct yet complementary. Zero Trust questions trust at every step, while Least Privilege keeps access minimal and focused. Neither is a magic solution on its own, but together, they create a smart, layered approach to cybersecurity.
Integrating these approaches, organizations can tackle modern security challenges with precision rather than overcomplicating their defenses. Understanding their differences and synergy isn’t just theory—it’s the first step to building a security model that’s adaptive, scalable, and ready for the evolving digital threats of tomorrow.







